Infostealers: An Overview
We’ll dive into the sneaky world of infostealers, malware that steals your secrets like a ninja!

What are Infostealers?
An infostealer is malicious software designed to infiltrate computer systems and extract valuable information from compromised devices. These malware programs operate covertly (not like some malware that perhaps gives pop-ups or noticeably hamper system performance) to collect sensitive data.
For a shorter description, an infostealer is malware that covertly steals secret information from a computer.
Our computers have tons of sensitive information tucked away – passwords in the browser, cookies with connection tokens, files with sensitive information saved (how many people do you think have a text file saved with a name like “passwords” or “private”?), PDFs with their recovery key codes, Word documents with their banking information – to name a few.
And in every operating system, there are typical “hidden” places with loads of information about that computer (e.g., Windows registry, Linux /etc, /usr, /bin).
Those are the items that infostealers are after.
Typical Techniques
Infostealers use varied techniques for system infiltration and data extraction. These techniques include but aren’t limited to phishing, infected websites, malicious software downloads (e.g., video game mods, pirated software), and exploiting system vulns.
Once installed, infostealers harvest data via methods like browser hooking, web injection scripts, form grabbing, keylogging, clipboard hijacking, screen capturing (ironically, this sounds like Microsoft’s recent Recall feature), and browser session hijacking.
Some more specific information
After infecting a computer, infostealers use various the following techniques (including, but not limited to) to acquire data. These include:
- Credentials: Credentials are a significant target, providing the quickest and easiest way for the criminal element to access computers. These stolen creds are used to collect login links, usernames, and even passwords stored in the browser.
- Cookies: Cookies enable malicious actors to access a logged-in session, bypassing security measures like MFA/2FA.
- Documents and text files: Infostealers discover and target high-risk files containing confidential information such as financial, intellectual property, server passwords, and crypto private keys.
- Machine-specific properties: These properties include computer name, operating system, IP address, date and pathway of infection, as well as existing antivirus and installed applications. It’s their way of doing recon!
Anatomy of an Infostealer
Bot Framework
The bot framework is an essential component of many infostealers, designed to operate on many victim machines for infection distribution. Here are key aspects of the Bot Framework:
1. Configurability: The framework includes a builder allowing attackers to customize the infostealer's behavior on the target computer. This enables them to specify the data to collect and how the malware should operate.
2. Data collection capabilities: Bot frameworks typically include modules for:
· Harvesting browser data (passwords, cookies, autofill information)
· Extracting credentials from various applications
· Capturing keystrokes
· Taking screenshots
· Gathering system information
3. Stealth: Infostealers are designed to be lightweight and stealthy, leaving a minimal footprint on the infected system.
4. Exfiltration: The bot framework is responsible for sending the collected data back to the attacker's command and control (C2) server.
5. Versioning: Some sophisticated bot frameworks, like the one used in the Jupyter infostealer, implement a versioning matrix to manage different malware versions.
6. More advanced Bot frameworks may include capabilities for:
· Downloading and executing additional malware
· Running PowerShell scripts and commands
· Process hollowing (for injecting malicious code into apps)
7. Compatibility: Bot frameworks are often designed to work across multiple Windows versions and system architectures. For example, the Continental Stealer is compatible with systems from Windows 7 (x32) to Windows 11 (x64) and supports both ARM and x86-x64 architectures.
8. Anti-detection features: Some bot frameworks incorporate anti-VM capabilities to evade detection when running in virtual environments and self-destruct mechanisms to remove traces after execution.
Here’s a pictorial and general overview of a bot framework:
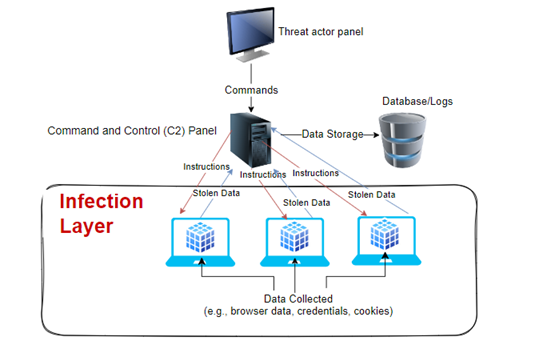
And of the attack lifecycle:
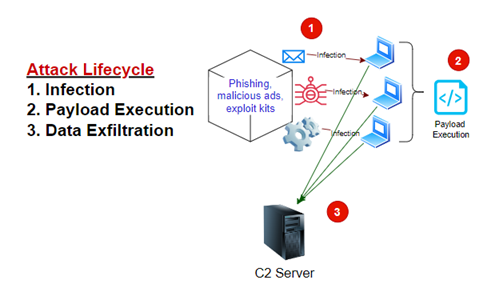
All in the Family
Infostealers are technically malware, which we often think of as a product – like buying an office suite or photo editing program - and is, more technically, Malware-as-a-Service (MaaS) because one can pay $130-$750 for Vidar infostealer, for example – depending on the license - to get it from a vendor. But it’s often also referred to as if certain ones are their own entity, family, distributor, reseller, market, campaign, and threat actor. Here, I’ll talk about infostealers in both ways, not focusing on whether or not it’s the malware or threat actor.
Some of the most prevalent infostealer families include Raccoon, RedLine, AgentTesla, Vidar, and AZOrult.
One example of the sophistication of MaaS is the stealer Rhadamanthys (here’s quick overview of it, with Yara rules at the bottom of the page if you need that to search for activity).
Rhadamanthys has instructional videos on Vimeo about how to use it.
The Top 3?
What are the main ones to be aware of and protect against? There’s no way to determine “Who’s or What’s the most dangerous?” It’s like asking, “What’s the best band?” or “What’s the worst company?” There are so many technical details and subjective experiences that calling something “worst” or best” is not quantifiable. For infostealers, some are spun up and then dismantled, others are used prominently for a while and then placed in the malware junk drawer; some are for mobile, some for specific industries, and others are OS-specfic.
But to focus a little, 3 of the top infostealers are:
1. Raccoon
2. Redline
3. Vidar
Raccoon
Raccoon Infostealer, first observed in April 2019, is a popular and effective Malware-as-a-Service (MaaS). Raccoon targets a wide range of sensitive information – such as login credentials, credit card details, cookies, browser history, and autofill information. Written in C++, Raccoon employs a modular approach to infect both 32-bit and 64-bit Windows-based systems, using process injection techniques to hijack legitimate processes like explorer.exe and gain elevated privileges.
What makes Raccoon particularly dangerous is its comprehensive data collection capabilities. The malware gathers detailed system information, including operating system architecture, version, system language, hardware details, and installed applications. It can also capture screenshots if enabled by the attacker's configuration. Raccoon follows a standard procedure for each targeted application: locating and copying cache files containing sensitive data, extracting and encrypting the information, and storing it in its main operating directory. After collecting data, Raccoon compresses all stolen information into a single zip file and exfiltrates it to its command-and-control (C2) server, typically using Telegraph or Discord for C2 operations.
Monitoring for Raccoon Stealer
To identify and mitigate the threat of Raccoon Infostealer, several indicators and behaviors can be monitored:
Raccoon Stealer v2 infections are characterized by unusual HTTP requests with empty Host headers and abnormal User Agent headers. The malware frequently changes its User Agent strings to evade detection, making anomaly-based detection methods crucial.
The malware contacts its command-and-control (C2) server using HTTP GET and POST requests, often to highly unusual IP addresses. These requests can include downloading DLL libraries and exfiltrating stolen data.
Upon infection, Raccoon Stealer fingerprints the target system, gathering information such as the operating system architecture, version, system language, hardware details, and installed applications. It uses functions like `RegQueryValueExW` and `GetUserNameW` to retrieve machine IDs and usernames.
The malware collects sensitive data, including browser autofill passwords, history, cookies, credit card details, usernames, passwords, and data from cryptocurrency wallets. It then compresses this data into a zip file (often named `Log.zip`) and sends it to the C2 server via an HTTP POST request.
Raccoon Stealer uses process injection techniques to hijack legitimate processes like `explorer.exe` and gain elevated privileges.
Raccoon Stealer was hampered in 2022 with the arrest of one of its main developers, who then pleaded guilty in 2024. But it’s still active.
Redline
RedLine Stealer, first discovered in 2020, has become one of the most notorious and widely used information-stealing malware in recent years. Operating on a Malware-as-a-Service (MaaS) model, RedLine allows cybercriminals to purchase a turnkey solution for stealing sensitive data from infected systems. This infostealer is capable of harvesting a wide range of information, including saved credentials, autocomplete data, and credit card details from web browsers, as well as data from cryptocurrency wallets, FTP clients, and popular messaging applications like Discord and Telegram.
What makes RedLine particularly dangerous is its ability to gather detailed system information, such as the victim's IP address, operating system details, installed antivirus software, and hardware configuration. This comprehensive data collection allows attackers to build detailed profiles of their victims and potentially use the stolen information for further malicious activities, including identity theft, financial fraud, or as a stepping stone for more sophisticated attacks like ransomware. The effectiveness and relatively low cost of RedLine have contributed to its popularity among cybercriminals, making it a significant threat in the current cybersecurity landscape.
Redline TTPs
More details on these TTPs can be found at Infostealers.com https://www.infostealers.com/technique/redline-stealer/
T1087, T1071, T1020, T1059, T1555.003, T1132, T1005, T1140, T1573, T1041, T1083, T1562, T1105, T1056, T1095, T1571, T1003, T1120, T1566, T1057, T1055, T1012, T1113, T1518, T1528, T1539, T1082, T1614, T1007, T1124, T1552, T1204
Vidar
First noticed in 2018, Vidar infostealer is a versatile malware that gained prominence in the cybercriminal ecosystem due to its efficiency in harvesting sensitive data. Initially marketed on underground forums as a Malware-as-a-Service (MaaS), Vidar is favored for its ease of use and ability to target a wide range of information, including login credentials, financial data, cryptocurrency wallets, and autofill information from browsers. The malware typically spreads through phishing campaigns, malicious advertising, or exploit kits, making it a persistent threat across multiple industries. Once deployed, Vidar operates silently, exfiltrating data to its command-and-control (C2) server while leaving minimal traces on the infected system.
One of Vidar's most troublesome attributes is its modular architecture, allowing customization of its functionality. This adaptability lets threat actors use Vidar for reconnaissance, credential theft, or even as a precursor to more devastating attacks like ransomware. The malware is also equipped with anti-analysis techniques, such as virtual machine detection and sandbox evasion, making it challenging for security researchers to dissect its operations. Over time, Vidar has been associated with various campaigns targeting organizations globally, highlighting the growing need for robust endpoint protection, phishing awareness training, and network monitoring to counteract its impact.
Related to Arkei trojan, Vidar can even receive updates!
For additional information, here’s an interview between g0njxa and Vidar staff: https://g0njxa.medium.com/approaching-stealers-devs-a-brief-interview-with-vidar-2c0a62a73087
For those looking to protect their network, here are some defanged IoCs (Indicators of Compromise) - IP Addresses, Domains, and Social Media. Plus some MITRE ATT&CK TTPs. This is just a sampling; much more can be found in the links in this section and the Resources at the end.
IP Addresses
162[.]241[.]225[.]237
- 5[.]79[.]66[.]145
- 104[.]21[.]45[.]70
- 193[.]29[.]187[.]162
- 104[.]18[.]5[.]149
- 45[.]151[.]144[.]128
- 18[.]205[.]93[.]2
Domains
- notepadplusplus[.]site
- download-notepad-plus-plus[.]duckdns[.]org
- download-obsstudio[.]duckdns[.]org
- dowbload-notepadd[.]duckdns[.]org
- dowbload-notepad1[.]duckdns[.]org
- download-davinci-resolve[.]duckdns[.]org
- download-davinci[.]duckdns[.]org
- download-sqlite[.]duckdns[.]org
Social Media
- hxxp://www[.]tiktok[.]com/@user6068972597711
- hxxps://t[.]me/mantarlars
- mas[.]to/@zara99
- ioc[.]exchange/@zebra54
- nerdculture[.]de/@yoxhyp
- hxxp://www[.]ultimate-guitar[.]com/u/smbfupkuhrgc1
- mas[.]to/@kyriazhs1975
- mastodon[.]online/@olegf9844g
- steamcommunity[.]com/profiles/76561199436777531
Vidar Malware MITRE ATT&CK Tactics, Techniques, & Procedures (TTPs)
Technique ID, Description
T1204 - User Execution
T1555 - Credentials from Password Stores
T1539 - Steal Web Session Cookie
T1614 - System Location Discovery
T1518 - Software Discovery
T1007 - System Service Discovery
T1095 - Non-Application Layer Protocol
T1566 - Phishing
T1552 - Unsecured Credentials
T1113 - Screen Capture
T1057 - Process Discovery
T1087 - Account Discovery
T1041 - Exfiltration Over C&C Channel
Protection
It’s never good to present all the things to be afraid of yet not show people how to protect against those fearful apparitions.
There’s a lot of information to sift through. How can we protect ourselves against all of these malicious actors? No report can provide all the ways – too many factors, and many are highly technical. But here are several ways that anybody can use, professional/technical or not.
1. Multi-Factor Authentication (MFA/2FA): For infostealers, user credentials are a major target. Deploying MFA makes it more difficult for an attacker to use the stolen credentials.
2. Use strong anti-malware software
a. New to buying antimalware/antivirus? Search online for top antimalware or best antivirus suites or top 10 AV for 2025
3. Keep systems and software up-to-date
a. For home use and personal devices, select automatic download and then install when ready.
b. For corporate users, automatic updates can cause big trouble for critical systems, so ensure proper testing, but update (or upgrade) when you can. I know…easier said than done.
4. Use caution with attachments and downloads
a. If you can slow down to think about what you’re sending or downloading, that’s a great start.
b. Because many infostealer campaigns deliver malicious files via a phishing email, it’s great to have security solutions that can inspect email attachments for malicious content and provide the ability to rip them out before people can get to them.
5. Implement strong password policies
a. Typical home use of computers doesn’t require official policies, but at least keep in mind that the better your password, the better.
6. Regularly monitor for suspicious activities
a. Don’t click on those pop-ups on your computer, except to click on the X or Close. Even at that, those are simply buttons that could be tied to actions. So, if at all possible, close the entire browser (at least the tab) instead of clicking on the pop-up.
b. Set a regular time to review your bank transactions. That doesn’t prevent crime, but at least a long time won’t pass without you knowing about it.
7. Educate colleagues about social engineering
a. Professionals – help people out. Non-professionals – ask for help. Security professionals love to help people (we might not fix things or give hour-long seminars for free, but an email now and then is possible).
There are dangers out there, and with the right knowledge – which is readily available but often either hard to find or overabundant - you can stay safe. Go safely into and through 2025!
Sources, Resources, and More Information
Raccoon
https://www.cyberark.com/resources/threat-research-blog/raccoon-the-story-of-a-typical-infostealer
https://cyberint.com/blog/financial-services/raccoon-stealer/
https://www.justice.gov/usao-wdtx/victim-assistance-raccoon-infostealer
https://www.linkedin.com/pulse/raccoon-stealer-announces-return-new-features-tools-mihir-bagwe
https://www.cyber.nj.gov/threat-landscape/malware/trojans/raccoon
https://www.infostealers.com/article/approaching-stealers-devs-a-brief-interview-with-recordbreaker/
https://www.kelacyber.com/wp-content/uploads/2023/05/KELA_Research_Infostealers_2023_full-report.pdf
Redline
Good and detailed summary: https://cyberflorida.org/redline-stealer-malware-analysis/
2024 discruption: https://www.bankinfosecurity.com/dutch-police-fbi-infiltrate-info-stealer-infrastructure-a-26643
https://www.kroll.com/en/insights/publications/cyber/redlinestealer-malware
https://proton.me/blog/infostealers
https://www.threatspike.com/blogs/redline-part-1
https://nordvpn.com/blog/redline-stealer-malware/
https://www.linkedin.com/directory/articles/t-402
https://flare.io/learn/resources/blog/redline-stealer-malware/
https://www.csk.gov.in/alerts/RedLine_infostealer_malware.html
https://securityscorecard.com/research/detailed-analysis-redline-stealer/
https://www.cloudsek.com/blog/technical-analysis-of-the-redline-stealer
https://www.infostealers.com/technique/redline-stealer/
https://www.esentire.com/blog/esentire-threat-intelligence-malware-analysis-redline-stealer
https://malpedia.caad.fkie.fraunhofer.de/details/win.redline_stealer
https://flashpoint.io/blog/redline-meta-takedown-infostealer/
https://intel471.com/blog/redline-and-meta-the-story-of-two-disrupted-infostealers
Vidar
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-malware/what-is-vidar-malware/
https://www.hhs.gov/sites/default/files/vidar-malware-analyst-note-tlpclear.pdf
https://wazuh.com/blog/detecting-vidar-infostealer-with-wazuh/
https://darktrace.com/blog/a-surge-of-vidar-network-based-details-of-a-prolific-info-stealer
Bot Framework
https://en.wikipedia.org/wiki/Infostealer
https://blog.morphisec.com/jupyter-infostealer-backdoor-introduction
https://lumu.io/blog/infostealers-silent-threat-compromising-world/
https://cyberint.com/blog/research/the-new-infostealer-in-town-the-continental-stealer/
https://flashpoint.io/blog/protecting-against-infostealer-malware/
https://www.cyberark.com/resources/threat-research-blog/raccoon-the-story-of-a-typical-infostealer
https://flashpoint.io/blog/understanding-seidr-infostealer-malware/

