Investigation - A Fraudulent App With Some Dangerous Permissions
A security researcher is hot on the trail of the creators of a fraudulent Android app with some dangerous permissions, in this ongoing investigation and analysis.

I have been following an Instagram meme page with about 150K followers for a while now and the page posts advertisements sometimes when they can get paid for them. One such ad promised “10GB Data Everyday for Free for 3 Months for Jio Prime Users”, Jio is one of the largest telco's in India and as I am a Jio user I got curious enough to look into this. I was sure that there was some kind of fraud going on, and that this advert was not paid for by Jio.
My theory was that scammers were using the name of Jio to milk the followers of the meme page, since many of their followers also use Jio for their data.
I visited the URL (link) and downloaded the mentioned APK (JioPrime.apk), which was hosted on Google Drive. Turned-on the emulator (Genymotion here!) and loaded this APK – yes, the icon was same as Jio’s logo (spot the app named Jio Prime in screenshot below). On opening the APK, it gives look-n-feel similar to the MyJio app (the self-service app for Jio customers):

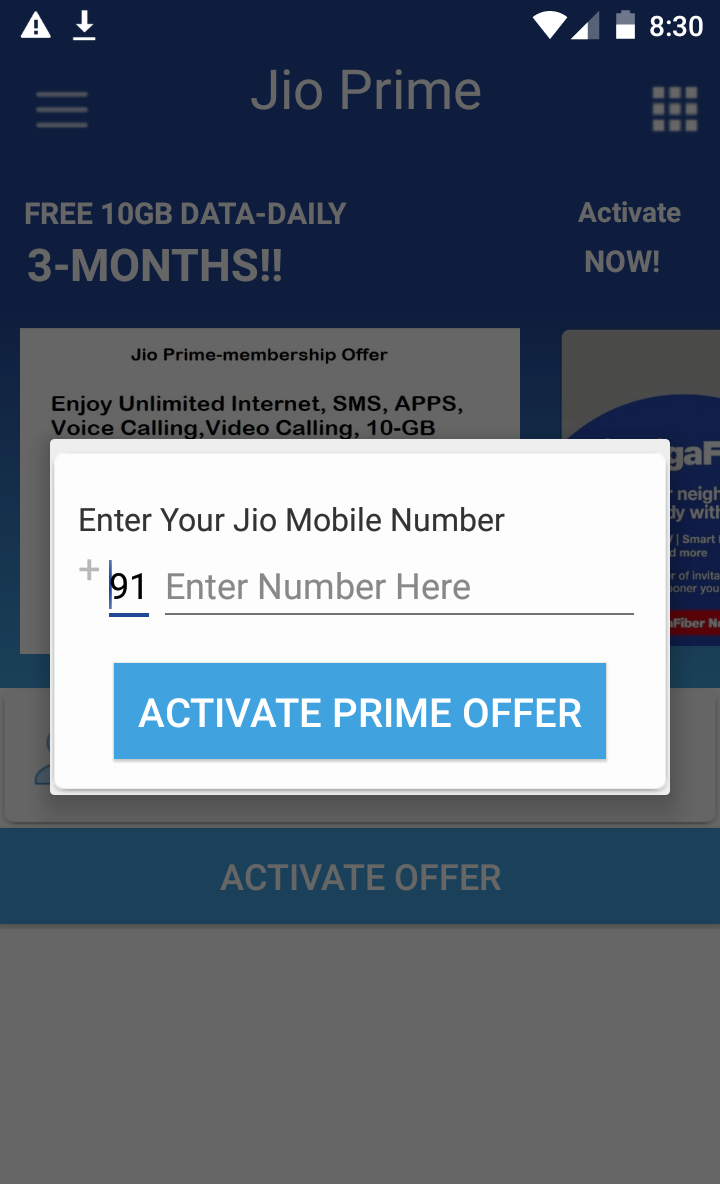
I started capturing the requests and responses with Burpsuite to look for anything malicious, it asked me to provide my phone number so I entered my mobile number and it gave me the 'loading screen', saying that something is happening in the back-end. Any user will be convinced by the different pop-ups sequentially saying: ‘Connecting to Sever…’, ‘Connected’, ‘Activating Offer’. Next it took me to “Share with Whatsapp” screen, where it asked me to share it with 10 users on Whatsapp.



But there were no network connections up until that point and then it started sending some data to Google Adwords URL. I entered mobile number as 0000000000, and it still accepted my mobile number as a valid Jio number and showed me the loading pop-ups, next with the Share on Whatsapp screen. Since I don’t have Whatsapp installed on the emulator, I was not able to test further, but I worked out that they were sending user clicks to Google Adwords.
The MobSF analysis results are here:
1. Some of the dangerous Android permissions asked by the app:
a. READ_EXTERNAL_STORAGE
b. WRITE_EXTERNAL_STORAGE
c. READ_SMS
d. ACCESS_FINE_LOCATION
e. SYSTEM_ALERT_WINDOW
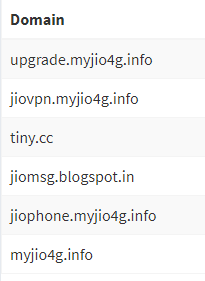
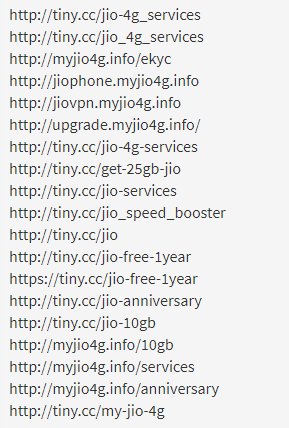
2. Below is the list of malicious URLs and Domains contained in the APK. When you “Share via Whatsapp”, your contact will receive the link like “Activate this service before*\n*12:00AM Tonight to Enjoy*\n*25GB/Per Day!!*\n\n*Team Jio.*\n\n*Link* : http://tiny.cc/Jio-Free-1Year“;“
Later I uploaded the APK to VirusTotal for their analysis. One thing that attracted my attention was a Service named “er.upgrad.jio.jioupgrader.Coinhive“. While Coinhive (link to KrebsonSecurity article) is a cryptocurrency mining service, this app could be a miner masquerading as Jio to eat the process of the user device in order to mine cryptocurrency and earn money for the APK owner.
I reverse-engineered the APK with dex2jar and Jd-Gui to check what exactly is contained in the Coinhive part, but most of the code was obfuscated and I was unable to get much meaningful data from the single class.
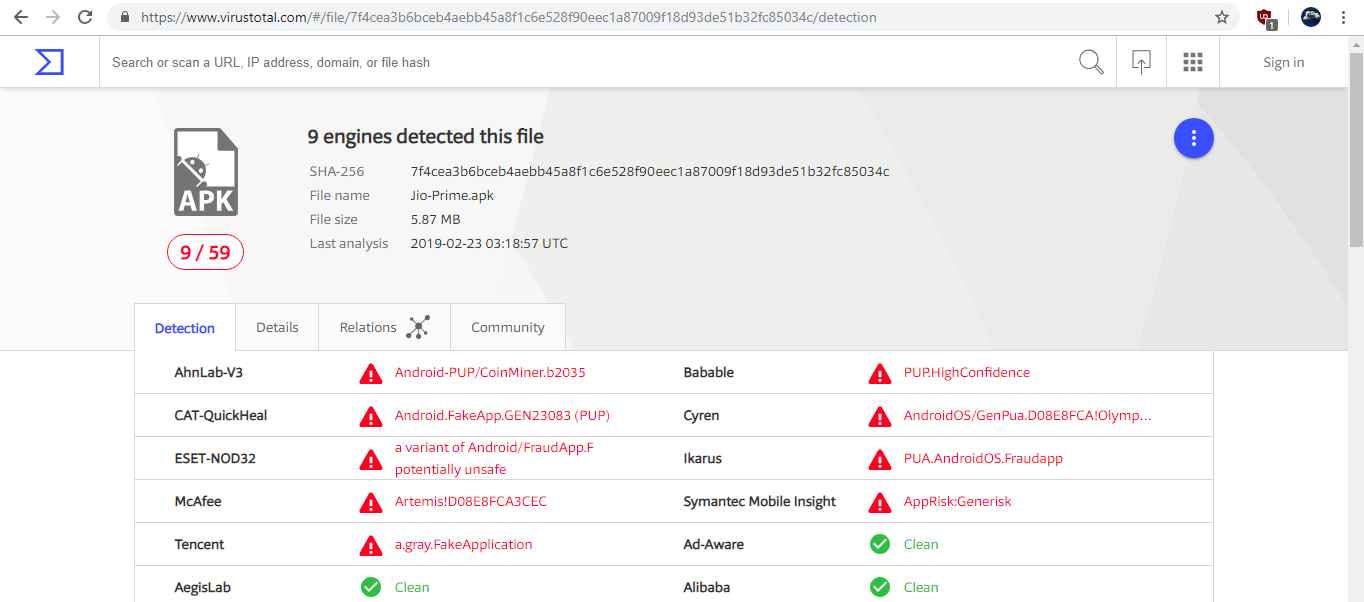
Nine (9) Engines at VirusTotal also marked this app as malicious/fake, screenshot here:
Takeaways:
I could just see their JioPrime ad on 1 page on Instagram, but not sure where else they have posted their ads and how many victims have installed their APK. Also, since the app is having dangerous permissions (like Read & write external storage, read SMS), I am sure they would be accessing and sending this data somewhere.
I highly recommended you do not install APKs from unknown sources, even some of the Google Playstore apps have malware in them, but that’s a totally different topic.
Remaining On My To-Do List:
– Check if it is actually mining any cryptocurrency.
– Reverse engineer the APK to reveal its creator and the Adwords account
– Check the network connections it creates other than the Adwords connection.
– Find out exactly what data from user device is being accessed and determine whether that data it is being sent anywhere else by the app.
I will update this article as I progress down my to do list, but if you do have some free time and want to help me out, please do feel free to perform your own further analysis of the APK and help me find any more malicious vectors.
- You can download the APK from this blog: http://jiodatapack.blogspot.com/
- VirusTotal report available here: https://www.virustotal.com/#/file/7f4cea3b6bceb4aebb45a8f1c6e528f90eec1a87009f18d93de51b32fc85034c/detection
You can reach me on Twitter here if you wanted to ask me about this, thank you for reading about my work so far and happy hunting!


