A Journalist's Guide to Online Anonymity and Secure Communications
It’s important for a journalist to be able to protect the confidentiality of their sources as well as their own online presence at times. In many cases, you will be publishing information that other people don’t want to be public.

It's important for a journalist to be able to protect the confidentiality of their sources as well as their own online presence at times. In many cases, you will be publishing information that other people don't want to be public. Also, your sources will want to make sure that they can't be traced back to the information that they are disclosing. To assist with this problem, I'm putting together some tips that a journalist can use to protect their online identity, the identity of their sources, and protect their communications from eavesdropping.
Online Anonymity
As the internet of things (IoT) continues to grow, companies are collecting more and more information from consumers. Modern-day conveniences like GPS, Siri, search engines, or smartphones all collect information about us that can be linked back to us as individuals. While it has not been publicly admitted, many people suspect that companies sell this information to invested parties, which further increases people's concerns. However, there are steps you can take to remain anonymous online. While none of these are full-proof methods, they significantly decrease the likelihood of someone being able to track your identity online.
Use secure browsers: Google, Apple, and Microsoft take part in a program called PRISM, which allows the NSA to access user data from them. Therefore, browsers like google chrome, safari, and Microsoft edge that are all owned by private companies who are well known for disclosing their customers' information are not seen as secure. You want to use an anonymous browser such as TOR, idyll, or Waterfox/Firefox. These browsers don't record or report your browsing information by default and offer other security advantages over the browsers provided by larger companies. At the very least, if you're going to use a mainstream browser, you should use the private browsing mode. For example, in google chrome, you can right click the browser and select incognito. In this mode, your browser won't store cookies or internet history on your computer. However, incognito mode doesn't do anything to protect your identity, as your IP address can still be easily found.
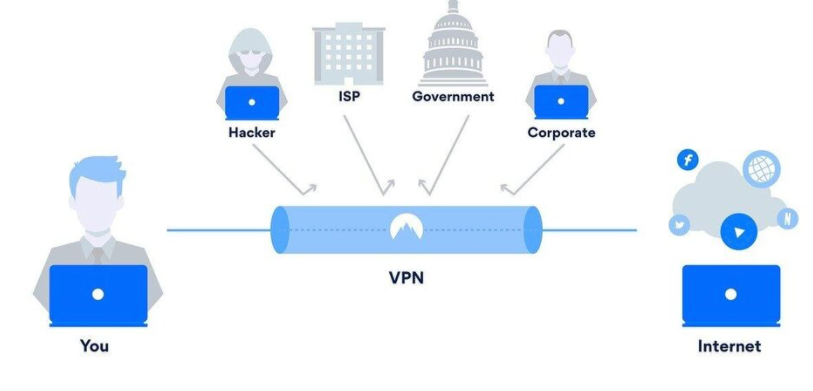
Use VPNs: This stands for virtual private networks, and this helps in protecting your identity online. The way it works is, rather than your computer sending a request directly to a website or another computer. Your computer connects to the VPN network, and the network sends the request on your computer's behalf. This way, if anyone is trying to find the IP address of the sender, they will see the VPN provider's IP address instead of your IP address. Many VPNs also allow for an end to end encryption, which protects the content of your message. This way, anyone that is eavesdropping, for example, maybe your Internet Service Provider, would not see your true message only ciphertext (the encrypted form of a message).
Use secure search engines: Search engines like google track your search history, typically using it to provide personalized search, which is why you are recommended things based on your past search history. This can be turned off to prevent google from obtaining your search information. Ideally, you use alternative search engines like duckduckgo, which are well regarded as one of the few search engines that do not track user's searches and "emphasizes protecting searcher's privacy and avoiding the filter bubble of personalized search results."
Use a VM: This stands for a virtual machine, and it's essentially a computer within a computer. The way it works is that once you download the software, such as VirtualBox, you can open a window, and within that browser, you will have a desktop with applications just like your main computer screen. This VM is isolated from your main machine and keeps viruses or malware contained. Therefore, if you ever have to work with a suspicious file that might be malware, work on it within the VM, and then you can delete the File and the VM, and it doesn't pose the risk of infecting your machine.
Secure Communication
While being anonymous is good at protecting the identity of you and your sources, you also need to protect the content of your discussions. Here are some ways you can do that:
Secure Email
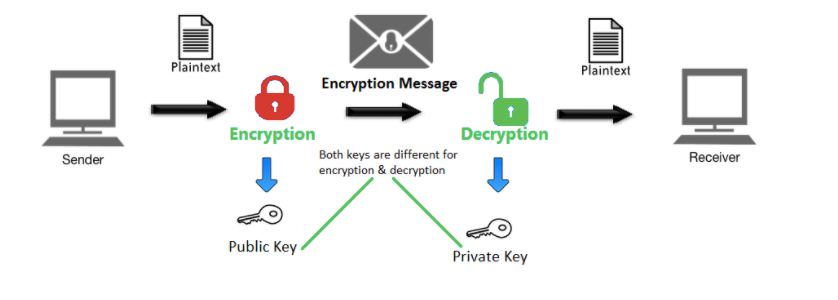
If you're using a popular email service like Gmail or Yahoo, you can combine this with end-to-end encryption. You can do this by using browser extensions like SecureGmail or Mailvelope, which can be used on google chrome and other popular browsers. These will ensure that all emails you send will be encrypted, so if anyone is able to capture them during transmission, they won't know the contents of your message. The recipient of the emails will need to have the same extension installed to decrypt the message. You can also make a full switch to a more secure email platform such as hushmail or kolabnow.
Lastly, you can use Disposable Email Addresses(DES). These allow users to quickly create and dispose of email addresses. They are not especially secure but are good if you need quick throwaway email addresses. Some providers for this are Guerilla Mail and Mailinator. You can also use email aliases with these solutions to mask your real email address if you want that to remain hidden.
Use a Throwaway Phone or Phone Number
Have a phone dedicated to contacting confidential sources and signing up for messaging apps so that the number associated with the account isn't directly related to you. Blackberries were always considered to be very secure, but there are plenty of other options you can use. The main thing is you don't want the number directly associated with you.
Secure Messaging Apps
If you're going to be messaging people from your phone, it's important to use a messaging service that provides end to end encryption. You also want to do some research to ensure that the company controlling that platform is someone that you are willing to trust. Some messaging apps that are known for good security and encryption are chat secure, silent phone, and WhatsApp.
Recap
As a journalist, the two things you should be concerned about when it comes to online security is online anonymity and secure communications. To be anonymous online, you need to hide your IP address and your online activity whenever you're going online. For this, you need resources like a VPN, secure browsers, anonymous search engines, and virtual machines (if you're working with suspicious files). Second, you want to secure your communication. This means ensuring that whatever application or email you are using has to end to end encryption. This protects the content of your message and makes sure no one eavesdropping can read it.

