Mobile Infosec Challenge Walkthrough
Infosec Mobile CTF - The goal of this challenge is to extract encrypted data plus its secret from a database embedded inside the application.

This article aims to briefly document some techniques and tools involved in the vulnerability assessment process of android applications. For such purpose, we will solve the 2nd CTF challenge of Infosec institute (please, get the apk from here).
" The goal of this challenge is to extract encrypted data plus its secret from a database embedded inside the application. Successfully decrypting the data reveals the flag."
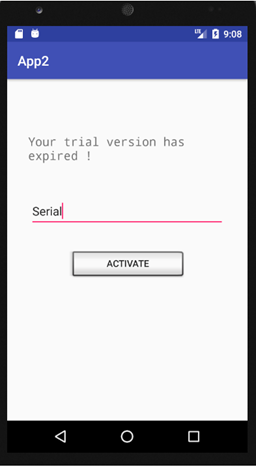
First of all, we simply launch the app in the android emulator.
Here are the standard steps we will perform to understand the inner working of the application:
- Decompiling the apk
- Retrieving the source code
- Crafting the solution with a PoC
1) Decompiling the apk
We use apktool to decompile the resources and the bytecode.
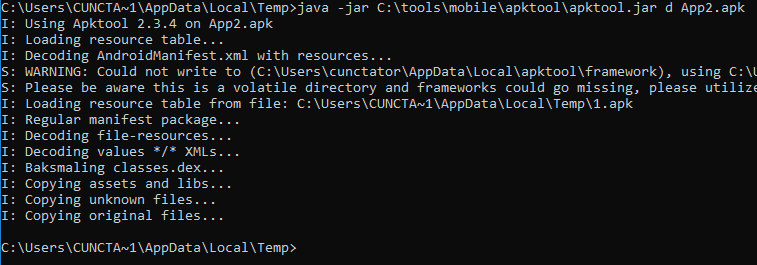
We have a look at the android manifest, to have an overview of the components exported by the application.
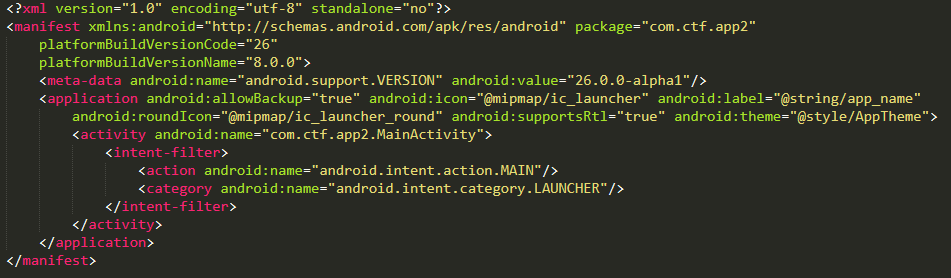
Nothing interesting for now, only one activity is exported in this app. Obviously, this activity is the main activity itself.
2) Retrieving the source code
Note that we have not retrieved the source code with Apktool, but just the smali code (that is the assembler of the bytecode). For obtaining something similar to the source code, we will use jadx, as shown in the image below.
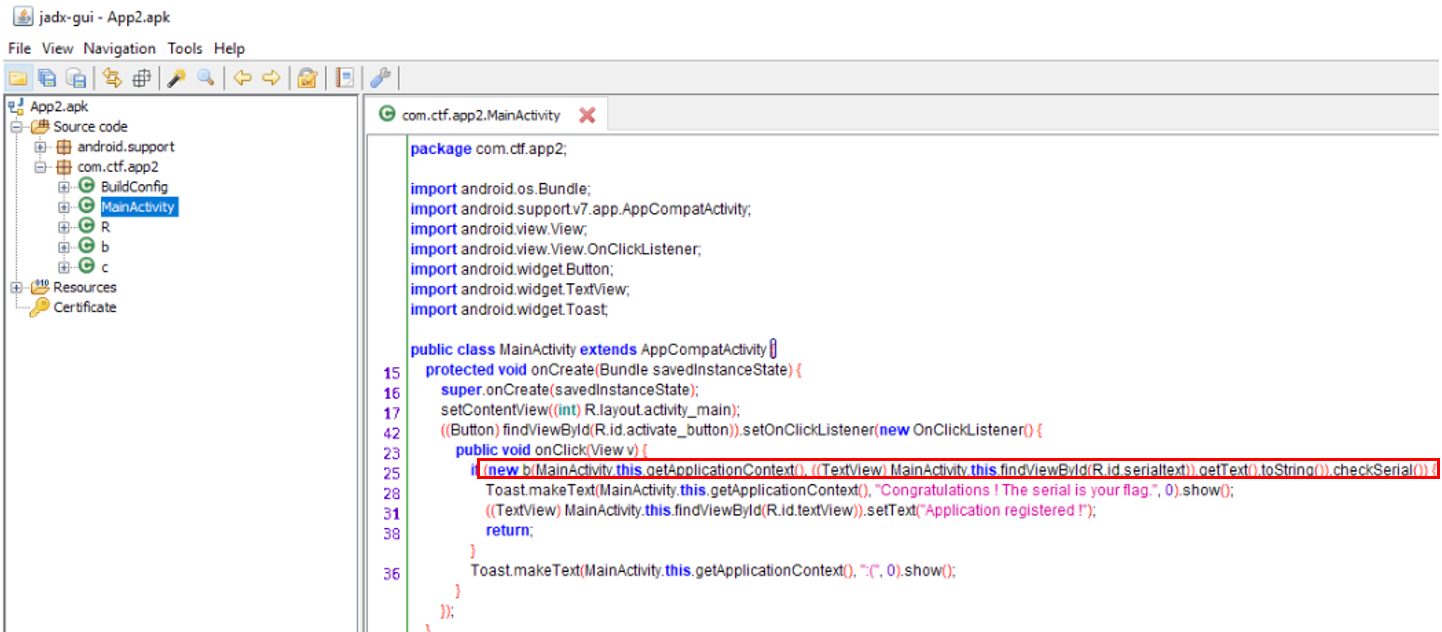
Ok, now we focus on the code reviewing step, looking at the implementation of class 'b' and 'c'.
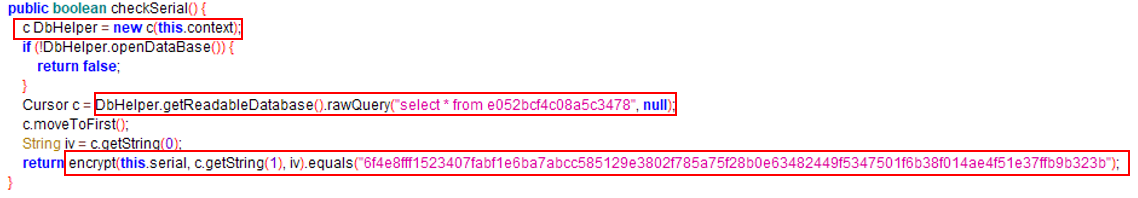

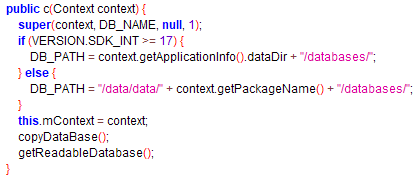
We now have a clear picture of the inner working of the app: the flag is the "Serial" value we input in the app.
We also see that all the necessary information we need to solve the challenge are listed in the method 'checkSerial'.
In fact, the flag is used as the plaintext in the symmetric encryption, the key and IV are stored in cleartext in a database, the ciphertext is the string "6f4e8fff1523407fabf1e6ba7abcc585129e3802f785a75f28b0e63482449f5347501f6b38f014ae4f51e37ffb9b323b".
Therefore, all we have to do is to extract key and IV values from the database and to correctly craft the decrypting function.
Firstly, we need to identify the location of the database. This task is achievable in multiple ways.
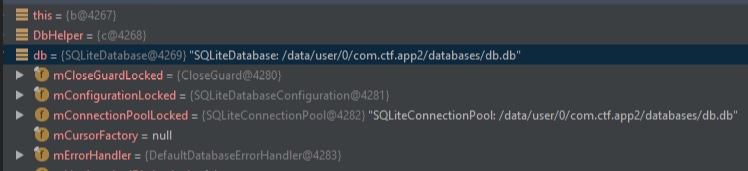
For example, we can set the 'android:debuggable' attribute in the AndroidManifest, recompile, sign, zipalign the apk and then debugging the smali code via Android Studio (below image).
However, the shortest path is to look carefully at the 'c' class constructor and to execute in a new Android Project the instruction:
getBaseContext().getApplicationInfo().dataDir + "/databases"
Lastly, we dump the database with adb and read its content with sqlite3.
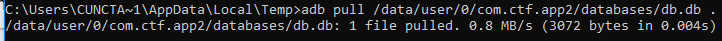
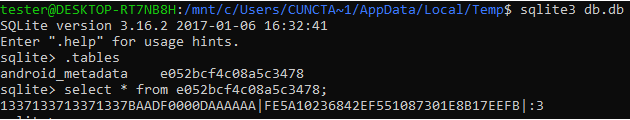
We now have the value of the key and the IV. We already have the ciphertext... we just need to use this data to get the plaintext (the flag) back.
3) Crafting the solution with a PoC
To code the few lines of the decrypting function, we have to consider the implementation of the 'encrypt' method in use by class 'b'.
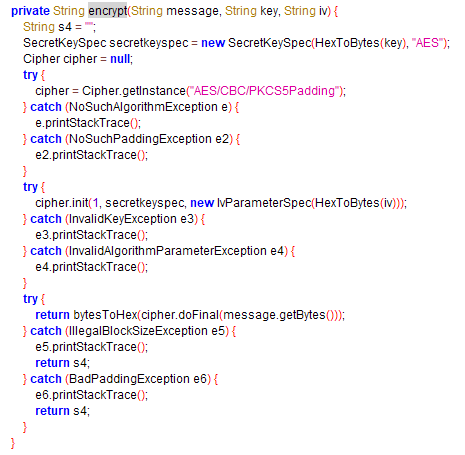
Here is our Proof of Concept, that is a simple application that just performs the decrypting process and displays the flag.
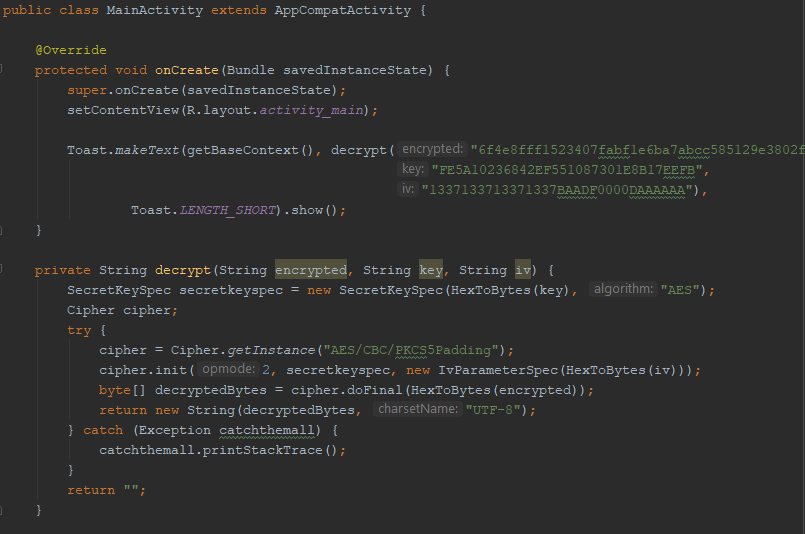
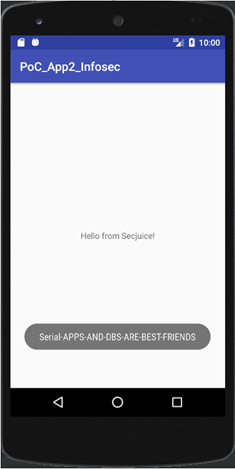
Conclusion
Android vulnerability assessment requires specific tools and techniques.
If you would like to start testing mobile apps, a good methodology has been recently created by OWASP and is available for free here.
This article only scratched the surface of testing mobile apps. In fact, due to the CTF app peculiarities, we did not cover tools like Drozer and Frida, that are the defacto standard for a professional assessment on Android applications.
Keep on studying!

