Modern Wardriving: An Analysis
Security researcher Max Bishop performs an evaluation of the state of modern urban networking as it relates to WEP/WPA2 cracking & wardriving in Grand Rapids, MI.

Introduction
There’s something that just feels right about being an information security professional in a large urban city. Considering the mess of unsecured IoT devices, sloppily configured home networks, and bad business practices, a pentester with authorization might just be the king of the jungle. On days like this, I feel a calling…a calling for wardriving. What is wardriving? Wikipedia defines it as, “the act of searching for Wi-Fi wireless networks by a person usually in a moving vehicle, using a laptop or smartphone.” I call it "mobile hunting".
Back in the days of yore, there were far more WEP access points out there in the wild. In Seattle, Washington in 2004, a weeks-long analysis of the city found 5,225 access points, and of those 5,255, only 44% of the routers were secured with WEP encryption. (http://old.seattletimes.com/html/businesstechnology/2002183464_wifimap18.html)
(https://en.wikipedia.org/wiki/Wardriving)
To compare, I did the same thing in Grand Rapids, Michigan in May 2018. I found roughly 3,000 access points, only two of which used WEP encryption. While this is a good sign for the state of information security, it’s frustrating for us blackhat wardrivers.
So what does this mean? Well, largely it means we’ve progressed to more secure standards like WPA2, but could those be cracked? Or, alternatively, are the seldom pickings of WEP networks plentiful enough nowadays to sustain a wardriving habit?
In short, yes, and yes. We’ll be addressing the cracking of WPA2 a little later, but as far as cracking WEP goes, it’s still definitely worthwhile to have in one’s pentesting repertoire. Plus, if you get some practice wardriving for WEP, you can easily adapt that skillset to progress into WPA2 cracking.
Tools
To prepare for our warpath, we’ll only need one thing: a wardriving application. The point of any wardriving application is to continually scan for networks on a given channel and then log the encryption standard, location, and MAC & SSID for later use.
That’s not actually a terribly demanding list of features, so there’s plenty of open-source applications ready to choose from that come equipped. My personal favorites as an Android user are WiGLE WiFi and GMON, but WiGLE gets precedence and all of my respect for running https://wigle.net/, a crowdsourced map of wifi access points (which some might argue is the terminal goal of wardriving).
Once I installed WiGLE WiFi on my Android, I opened up the app and immediately got hits. I wouldn’t even be off work yet for a few hours; but I was itching to roam and collect more networks for my log.
You’ll immediately see a nice enough (free!) interface which displays the SSID (Router Name), MAC Address, Signal Strength, and Encryption Standard.
Exporting
One of the features any wardriving app worth half it’s salt will have is an Export to File option; probably in CSV or KML format.
Personally, I think it’s amazing to be able to build a database of access points, or “APs,” and view them easily by location. Sites like http://kmlviewer.nsspot.net/ can provide a quick and free way to browse a collection, though there are plenty of alternatives. I like KMLViewer because it visualizes with color coding the encryption standard present - which makes parsing through data in a big city much easier.
Once accumulating APs with WEP, WPS or WPA/WPA2 encryption, it’s easy to recall / view the location later; and if authorization from the owner is negotiated, return later in a clandestine operation to perform a realistic curbside security audit.
Over time, as WPA and WPA2 replaced the deprecated and insecure WEP standard, home networks for computer users with little to no expertise in the field were automatically secured by the default WPA2 configuration on nearly all routers available for purchase. While this is good for the average home user, it’s less than ideal for people who make their livings on poorly secured technology.
That being said, the art of wardriving truly is a joyful, lighthearted and fun activity that I strongly encourage anyone interested in cybersecurity to experience firsthand. As mentioned previously, not only will this hone a useful skill, but it will also posture anyone to transition into WPA2 handshake capturing and cracking with a comprehensive understanding.
It’s also well worth noting that wardriving for WEPs is not without benefit to a true threat actor. The act of “warkitting” refers to roaming in a wardriving style, but upon completion of the WEP crack, using the key to access the AP without authorization and proceeding to “update” the AP to use malicious firmware that rootkits the router, to add it to a botnet.
WEP Cracking
Alright, we’re finally ready to perform a WEP cracking attack, which should obviously only be performed on a computer system the cracker is authorized to pentest. There’s a wide range of tools for a crack on this encryption type, one consequence of the standard’s deprecation. I prefer Aircrack-ng, since I’m already used to the syntax of Airmon and Airodump from my blackhat Pi build.
Honorable mentions: Reaver (WPA), FERN Wifi Cracker (WEP/WPA), Cain & Abel (WEP), and Wifiphisher (not technically a “cracker”, but still worth mentioning; (WEP/WPA/WPA2)).
First we’ll need to get the name of our wireless adapter (or interface, in Linux terminology). In Linux, this is as simple as checking the “iwconfig” command output.
It should return something like:
wlan0:
with a ton of useful text about this interface’s characteristics to the right of it. Sometimes it’ll be wlan1, or a different name altogether, so this might take a bit of trial and error.
Next, we need to start our interface in monitor mode; which is when the adapter will constantly scan a channel with packet capturing capability. The command to do that should look like this
sudo airmon-ng start [interface name from above] [channel number]
Most of the time the channel will be 11 in my experience; but again, this may vary.
It’s good practice to check that this change succeeded by again using the “iwconfig” command. If successful, you should have a new interface on monitor mode; which usually looks like:
mon0
Awesome! Next we’ll want to start capturing traffic. That’s as easy as entering:
sudo airodump-ng [interface name, seen above]
The screen will start to populate with the APs, including the SSID, PWR (Signal Strength), CH (Channel), ENC (Encryption Type), and MAC Address.
Next we’ll want to specifically target our dummy WEP encrypted AP and capture some packets.
sudo airodump-ng -bssid [MAC Address] -c [channel number] -w [filename] [monitor interface again]
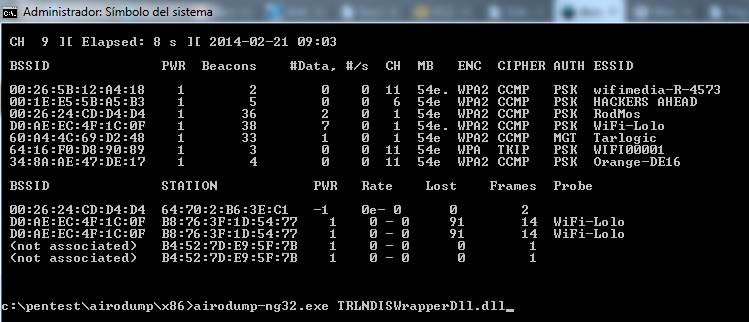
Name the file something memorable, because we’ll need to access this later to actually run the cracking half of the lab.
This will begin our packet capturing process. Now we wait to see if anyone connects to the AP while we’re actively capturing packets from it. Some of these packets will include a “networking handshake” to establish a new device and introduce it to the access point. By spying on packets, we’ll easily tell when someone does this.
Once you see a second BSSID populate below the first, which depicts the AP, that's a sure sign of somebody connecting to the AP. (Our screen will look a little different than the screenshot, which appears to be running with a slightly different configuration.)
Initialization Vectors & You
From here, we could just let our packet capturing naturally, over a long slow period of time, collect samples of initialization vectors, or IVs, and analyze them in order to accurately guess the key.
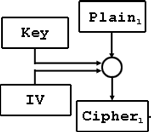
Each time a packet is sent; it requires a new IV be sent along with it, which is used like a salt would be used to add complexity to a password hash -- that is, the secret key of the WEP network is made more complex by adding a random, new, IV with each transmission of a packet. The intended effect of this is to prevent us from succeeding in guessing the secret key by examining a single IV.
In practice, that means a key like “bo0kw0rm” might be “salted” so to speak with an IV of “rld” or “vbn”, just a random 3 byte string; and end up looking more like “rldbo0kw0rm” or “vbnbo0kw0rm”.
While the original key, or “pre-shared key (PSK)” is the original word input (bo0kw0rm), the “secret key”, or string used to encrypt a communication via packets, is the concatenated version, “vbnbo0kw0rm”.
The flaw with WEP initialization vectors is that each IV is only 3 bytes long; which means the list of possible IVs is actually quite small considering the traffic that a busy network might undergo and the ability of threat actors to examine IV usage.
As a result, when you have enough time to sniff packets until an IV is inevitably re-used; then it becomes quite simple to segregate the IV from the key, based on probability that segment A of the full string (which is the IV plus key) is an IV, and segment B is the key.
When we have a good guess for what the key might be; we check it against the list of IVs captured and see if concating our guessed key with any or all of the historical IVs results in a previously used string in the list. If so, that means we’ve successfully “cracked” the key.
As a side note here; we’re able to initially obtain the MAC Address of the device we’re posing as to the router because the header and footers in a packet are NOT encrypted; and the header will always contain the MAC address of the device the packet originated from.
A Little Bit of History
The only problem with this technique as it stands is that a typical passive WEP key sniffing attack would take 5-6 hours on a very busy network for enough packets to be communicated to in turn generate the necessary amount of IVs to analyze in order for Aircrack to properly guess the key.
Enter “Korek,” a gifted hacker who devised a revolutionary method of WEP cracking, which at its core relies on injecting packets into the access point arbitrarily and rapidly, to generate packet noise and in turn generate far more IVs to be analyzed. This immediately broke the security of WEP, as now the same attack, with Korek’s method applied, would typically crack the same complexity of key in a matter of minutes.
Korek’s method is now immortalized, probably, in the aireplay-ng module of Aircrack-ng, which does exactly as he intended and injects packets into the router until we have enough IVs to get the key.
WEP Cracking, the Finale
To use the airplay-ng module; use the following command:
sudo aireplay-ng -3 -b [source MAC address] -h [access point] [monitor interface]
The -b and -h options are commanding aireplay-ng to use the given MAC address as our source MAC address, effectively spoofing it during/for the injection.
For the curious, the -3 option specifies our attack mode; which is ARP request replay. I think aircrack-ng’s own website, https://www.aircrack-ng.org explains better than I could:
The program listens for an ARP packet then retransmits it back to the access point. This, in turn, causes the access point to repeat the ARP packet with a new IV. The program retransmits the same ARP packet over and over. However, each ARP packet repeated by the access point has a new IVs. It is all these new IVs which allow you to determine the WEP key.
Now all we have to do is wait until we’ve collected a few thousands IVs in our crack file from earlier. So do so; just use the command:
sudo aircrack-ng [filename]
Finding Keys
If we recovered enough IV samples; aircrack should print, “Key found” or something to that effect, along with the key. If not, you’ll want to return to the earlier steps and collect more IVs, retrying the crack in increments.
The key will appear in hexdecimal format, so you can use the key as it is, but also convert it from hexdecimal to text with an online converter like http://www.unit-conversion.info/texttools/hexadecimal/. This should yield a passphrase in plain text, which may be useful for further pentesting.
Well, that’s pretty much it. We’ve covered wardriving as a concept, how to put that concept into practice today, and why you should. We’ve addressed why identifying WEP networks as vulnerable is useful and even benevolent, as well as demonstrated how to perform an actual WEP security audit with some lightweight, open source Linux tools (-- the best kind!).
This is part one of a two-part series on wardriving’s evolution. We touched briefly on the WPA2 wireless security encryption standard in this paper, but next I’ll be delving deep into how to capture an encrypted WPA2 “handshake” and use it to gain access to a modern, secure network.
Stay tuned!