Rise of the Nigerian Cybercrime Princes
The complexity of these scams is dependent on the duration of operation, the targets, the potential proceeds, and the versatility of the format.

As a Nigerian, I was sentimental about including my country’s name in the article. Afterall, there are other countries notorious for cybercrime, however, it is sickening to see how cybercrime has gone from being seen as one of the most repulsive practices to one of the trendiest in the eyes of Nigerias youth. exposing these cybercrime schemes is something I'd gladly do as an Infosec writer.
Nigeria is highly recognised for its innovative brains, owning the largest tech ecosystem in Africa and the most tech investments in Africa, generating a total of US$2,068,709,445 over seven years. Unfortunately, not all of these technologically savvy brains believe in investing their knowledge in noble causes.
You must have heard the story of Ray Hushpuppi, the Nigerian internet scammer alleged to have laundered tens of millions of dollars. He convinced people that he funded his extravagant lifestyle with his "Instagram influencer and Real estate dealer" alias.
But this article isn’t about Hushpuppi. Instead, it is about exposing the schemes and tricks of the Hushpuppies out there still in operation; how they corporately extort and launder money from individuals and cooperation.
Drivers Beyond Getting Rich Quick
Let’s do a quick review of the factors that motivate Nigerian youths to venture into cybercrime:
1. Economic stress:
Despite having the largest economy in Africa, millions of Nigerians live in poverty due to income inequality coupled with factors like unemployment and inflation. These factors frustrate many Nigerians from carrying out their financial responsibilities and are motivated to venture into cybercrime.
2. Peer pressure:
Just like Ray Hushpuppi, cybercriminals live a lavish lifestyle, show off their ill-gotten wealth, and make condescending comments to fellow youths who are hustling legitimately. This peer pressure eats into some and convinces them to explore cybercrime.
3. Personal vendetta
For some yahoo boys, their targets are individuals from countries that participated in the colonization and exploitation of Africa. They convince themselves that their in the right with the “we’re taking back our forefathers’ money’ saying.
Just take a look at the comment in the picture below.
Justifiable or not, what’s certain is that these drivers have branded the cybercrime to be more acceptable by the youths and have had some lose their integrity.
7 Most Sophisticated Nigerian Cybercriminals Schemes
Even though you may berate scamming, it is equally important to acknowledge the intellect used to plan such an act. Recognizing the art and its complexities does not just help you understand these scams but also helps to develop preventive measures.
When you mention the word “cybercriminal,” one of the first thoughts that come to mind is a black hat hacker. Well, think again because Nigerian cybercriminals do not only employ hacking techniques but prey characteristics that make their victims human.
The complexity of these scams is dependent on the duration of operation, the targets, the potential proceeds, and the versatility of the format. Some of these scams are very effective independently and can also facilitate more complex scams. Let us review some of them together:
1. Dating:
Yes! You may want to double check that match you just made on Tinder. The pretty girl, 5 miles away that is interested in you might be a dude in Ikorodu, Lagos.
People join dating sites and get the perfect love story, but some are not so lucky. But hey! Oscar Wilde warned you already – "life is never fair”.
Popularly known as catfishing, the dating scams is one of the most common cyber scams performed in Nigeria. Nigeria reportedly has the second-highest rate of romance frauds, according to Techsider.
How does it work?
Here, people are being nurtured online by fraudsters who pose as the gender their targets are attracted to and declare their love for them. In this context, “nurture” is the act of treating a target with affection to create an emotional bond leading to the targets falling in love.
After this point, the thieves start to “bill” their victims and request money be transferred through obscure methods. Like the use of gift cards, cryptocurrency, or any other untraceable method.
Dating is quite common and despite being straightforward, scammers call it “the mother format” because it is the foundation for many other formats which makes it versatile.
How to prevent:
· Don't use mediocre dating sites. Some of them are developed by these cybercriminals who want to exploit you. Even if they are legitimate, there is a good probability that you may run into many con artists because the security procedures are poor.
· Do not reply to accounts that are not verified. Verification features are offered by reputable dating sites like Tinder to enable you to determine whether the person you are conversing with is actually a real person or not.
· If someone starts the chat by asking for favors or if they ask for so many favors later, flag them.
2. Sugar mummy/daddy:
A brutal con artist comes along when you think you have found the perfect middle-aged person to help you with your finances.
The number of young men and women on the internet willing to provide sexual pleasures to older people in exchange for money, gifts and other favors makes it possible for scammers to operate.
How can I get scammed?
These swindlers pose as older adults who are financially capable of meeting the economic demands of young people. They locate naïve teens and youths wherever they want to operate. Contrary to what you may presume, they don’t always look for wealthy individuals because they aim to use their victims as pawns in other con games. Sometimes they prefer to target people with financial difficulties because they are often more desperate.
They pose as sugar mummies/daddies on social media platforms and send messages to younger people, saying they are looking for reliable young men or women they could take care of in exchange for them satisfying their sexual needs. Once they are certain their targets are convinced, they move on to the next stage.
But how do you get money from broke people?
They send their victims on errands. For example, they could give their sugar boy/girl a fake check, asking them to cash it out, or they could ask them to help ship some illegitimately bought goods (see format number 6)
The cybercriminals convince their victims that their regular pay comes from the proceeds of the errands they run. The latter believe they are just assisting their sugar mummy/daddy run errands for a cut.
In the instance of a fake check errand, once the targets receive the check and deposit it into their accounts, it initially appears legitimate until the bank starts their audit which is often too late. At that time, the victims must have withdrawn the money as advised by their sugar mummy/daddy, using them to purchase gift cards, cryptocurrency, or other untraceable items, and sent the rest after retaining their share as promised.
The victims realize they were scammed after the bank effects a charge back on their accounts upon discovering the phony check.
Does it end there? It could only be the beginning of the victim’s misery as scammers can use bank details obtained to operate unemployment scams (see format number 5) or use other personal information from their victims, such as their social security numbers ,etc. as their fake identity thereby implicating them as co conspirators (see format 3).
How to prevent:
· Flag accounts that hint on you running errands for them, especially if your remuneration depends on it.
· Do not share your personal details online.
Bonus:
Hookup:
Cybercriminals say the hookup scam is the easiest to pull off. Swindlers pose as strippers and sex workers on dating sites to find leads through illegal adverts. Their use of VPNs makes it difficult for them to be flagged and banned from the sites.
Once they get a lead, they demand a deposit, a percentage of their service rate through untraceable platforms or the details of some unsuspecting pawn. As soon as they receive a payment, they block you on that account before you suspect it.
3. BEC scams:
As if the difficulties that come with running a business are not enough to tempt you to give up, cybercriminals come along.
Fully known as "business email compromise", BEC is one of the most complicated scam formats. Scammers also regard it as the safest and biggest, thanks to its nature – the targets, and the proceeds.
How is it safe?
Fraudsters target reputable companies. Large corporations that would rather let scammers walk away because they do not want the public outcry and panic. Or any complication that would cause them to lose value in the stock market because they are thought unsafe. Hence, they refuse to disclose such information and even actively work to have the FBI avoid looking into such frauds to maintain their clients' trust. Therefore, giving con artists an easy escape route if they are clever enough.
These businesses occasionally use private investigators, but due to confidentiality restrictions, they are rarely successful.
For example, the “billionaire Gucci master”, Hushpuppi, successfully carried out BEC scams before he was caught. When he was being tried, some of these successful schemes were reviewed due to probable cause. However, the names of the victims were still not revealed. Page 14 of the criminal complaint:
“FBI employee saw messages reflecting that, in or around October 2019, ABBAS had conspired with Coconspirator 1 and Coconspirator 2 to commit a fraudulent wire transfer and money-laundering scheme, in which a U.S. victim (the “Victim Law Firm”) lost approximately $922,857.76”
How do they work?
As the name of the scam implies, if one email is compromised, it may impact many others and harm a firm.
After a while of monitoring the company, scammers target the finance unit of the companies and individuals that handle the company's finances. Their first step is to send phishing attacks, sometimes through the email of an already compromised department of the same company. Perpetrators study the email pattern of the company and structure theirs in the same manner so that they are unsuspicious enough to be clicked on. Once they click on these links, the scammers get confidential information about the company's emails needed to commence the next stage of the scam.
Hackers gain login access to these emails to keep tabs on the flow of messages, frequency of payments, and identity of those handling payments. Suppose the compromised email is not that of the person in charge. In that case, they can use the access they already have to look up the correct address and send another phishing message using the compromised account, which would be simple because they are thought to be employees of the organization. After gaining access to the appropriate account, they attempt to intercept due payments. They resend invoices with their payment information included, denying the validity of the initial ones sent by the compromised companies and claiming that they were a mistake.
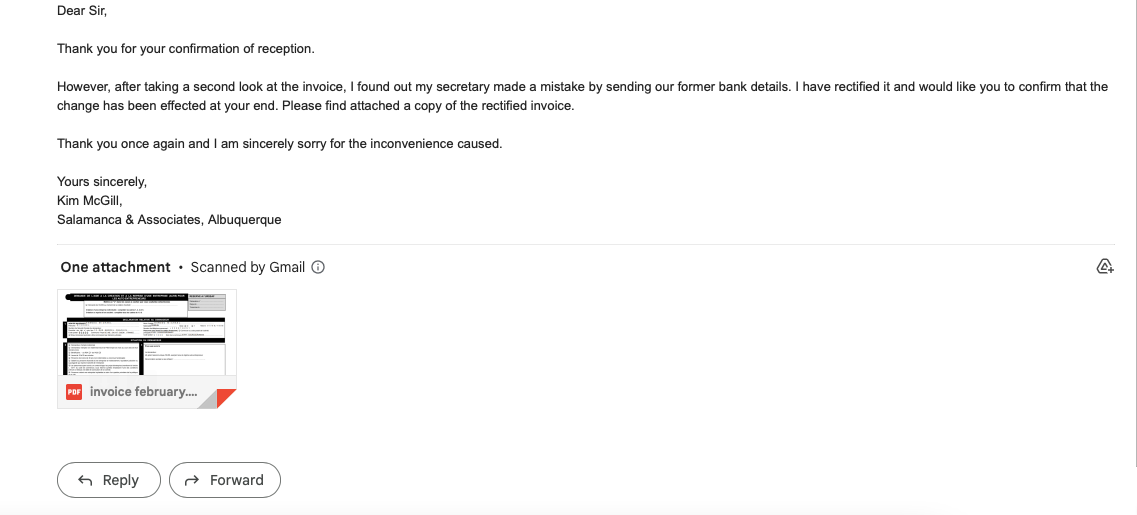
Now, company A transfers the funds to company B without realizing that B has been hacked and used the incorrect account information.
Even though the bank accounts can be tracked, this scam typically involves large sums of money, and the accounts don't belong to the con artists. They are from the details obtained through other scams. The con artists make sure they have many of these accounts available, distribute the huge sum through them, exploit them to purchase cryptocurrencies, and the money gets lost in the system.
For some cybercriminals, this is the ultimate challenge, and some swear to retire if they can pull off a BEC scam.
How to prevent:
· If someone contacts you or your company to alter payment information on an already-confirmed invoice, you should ask that any clarifications be presented at a face-to-face or online meeting.
· Whenever a department in your company sends you an email containing a link that requires you to take an immediate decision, make sure to call to confirm before clicking.
4. Unemployment benefits:
While governments and humanitarian organizations assist people with financial difficulties, scammers do the opposite.
Yahoo boys claim that this is an old scam format that only gained popularity during the covid 19 era, a period characterized by financial distress and economic hardship. It was, however, this scheme that made a lot of cybercriminals in Nigeria rich. This scheme even gained more popularity thanks to a trend called “benefit boys”.
The benefit boys trend started after a viral video showed that some high school teenagers showed up to school in a brand-new Mercedes Benz, the latest iPhones, humiliated their school teachers and tagged themselves benefit boys. “Benefit” alluding to the siphoned relief funds allocated to help unemployed people in the United States.
The Secret Service looked into this fraud in May 2020 and found that a significant portion of it was connected to a group of alleged Nigerian cybercriminals.
How does it work?
Perpetrators of the unemployment scam are scammers who already had access to the personal information and banking information of victims of scams like dating, sugar mummy/daddy (see format 1 & 2).
They continue to exploit these victims by using their identities to apply for relief funds. Afterward, they transport substantial quantities of money using untraceable methods.
How to prevent:
· Do not share personal information with strangers online
· Once you suspect any foul play with any personal details report to the constituted authority
5. Crypto scams:
According to Reuters, the majority of US customer dissatisfaction about cryptocurrencies are due to scams.
Scammers claim that this format is a recent, safe method, and it works in many different ways.
How does it work?
For the easiest of the crypto formats, all the scammers have to do is find a target on social media or dating sites, not necessarily someone to start a romantic relationship with but someone gullible enough to help a total stranger make cryptocurrency transactions for a percentage. The scammers claim to have made a sizable investment in cryptocurrency and have even earned a great amount of interest but however cannot withdraw it because they don’t have the amount required to activate the withdrawal. Unsuspecting victims agree to help and transfer funds to the wallets of their scammers awaiting confirmation and their percentage oblivious they have been scammed and probably blocked once the transaction has been confirmed.
Another format of the crypto scam involves investing in some digital token. Scammers create fake websites and lure people with very high ROIs. Once victims create an account and transfer funds into their wallets, they get locked out and can neither withdraw nor access the account.
My personal experience came in another format. A client messaged me on Freelancer and asked me if I could write some articles within a given timeframe, offered a fat pay and went on to share with me their Telegram contact, asking me to contact them there. I texted them on Telegram and they asked if I accepted crypto for payments that they wanted to make a deposit so I’d be eager to do the job and I answered positively. Then they told me they had issues with their Trust Wallet but have this crypto token that is really prolific.
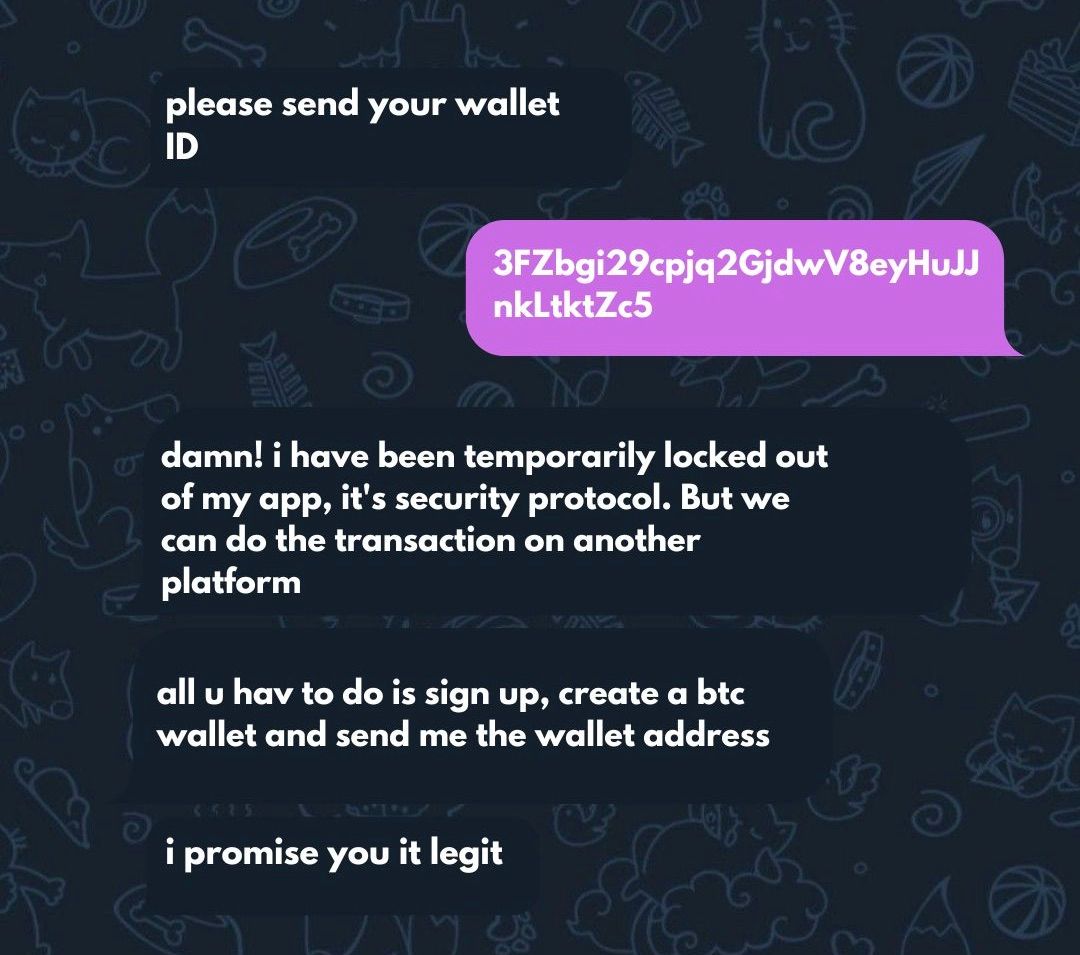
Since the switch from Freelancer to Telegram, I already suspected it was a scam but was desperate to see if it’ll bring any good. I created an account with fake details and was transferred $1,200 but needed to deposit money to activate the account and withdraw. Then I confirmed that it was a scam, I reached out to a friend who creates websites and he confirmed that it was only a fake flash from the endpoint.
How to prevent:
· No legit cryptocurrency trading platform requires you to deposit money in order to activate your account.
. Watch out for the tone of desperation in their messages, like the picture above, "i promise you it's legit".
· When the returns sounds too good to be true, they usually are.
· If they ask you to send a message on a different platform, it probably a scammer avoiding the security measures.
6. Credit card:
Imagine this! You are chilling at home and suddenly receive a message that you just purchased something online.
How does it work?
Scammers use phishing attempts to access companies' payment websites, where they can download and access account information from clients who have made payments. They then sell this information on their websites. Cheap fraudsters then go to the sites and purchase these card details for as little as $2 in the hopes of finding money in them. It hence, turns into a game of chance for the buyers; while some get to make purchases for millions of dollars with these cards, others are only able to make a few hundred or less. After making purchases, they use other schemes like sugar mummies, dating, etc., to cover their tracks. They send their accomplice victims on errands to help sell the items, collect their cut, transfer the remaining money, or even ship them to their home country. The funds vanish during this procedure into thin air.
Many of these cards are old and have been blocked or suspended, which is the sole drawback for purchasers, but some of these websites take fraud to a new level by offering customer support. They allow customers to test the cards to see whether there is money on them and assist in changing the cards till a valid one is found. Some others even charge their cards to find a working one.
How to prevent:
· Do not save your card details for future transactions on untrusted websites
· Call your banks to block your card if you have your phone stolen and have your card details on it.
· If you receive an unexpected debit, request that your account be freezed.
7. Inheritance scam
Internationally recognized as the “Nigerian prince scam” and locally called the “419 scam”. Have you ever heard someone excitedly talk about how they will be rich from the billion-dollar inheritance some Nigerian prince promised to share with them because they lent them some money?
Fun fact: The Nigerian Prince scam does not originate from Nigeria. In fact, it was formerly called the “Spanish prisoner scam” and has been around for so long that it predates the invention of devices that facilitate communication. However, cybercriminals from Nigeria have their reputation as the most popular perpetrators of the scam, hence, the renaming.
How does it work?
Scammers exploit human weaknesses rather than technological, appealing to emotions and psychologically manipulating their victims.
All the con artists need is a prey and they often kick back by dating their victims. They assert that they are the children of wealthy Nigerian families, and some even claim they are the heirs of a great kingdom (thus the origin of the phrase “Nigerian prince”). However, they cannot receive their inheritance because they have yet to fulfil certain requirements.
Here’s a perfect scenario:
After a period of dating, a self-acclaimed Nigerian prince contacts his online partner or acquaintance and tells his secret of how wealthy their family is. The prince goes on to tell how much wealth he would receive from the inheritance. However, there are some requirements to be met to be a beneficiary.
After successfully convincing their targets that they are wealthy, they invent a personal problem that needs to be resolved financially and complain that they cannot do so because they are poor. They request the help of their oblivious partners and friends, promising to marry them (which makes sense since it is a prerequisite for them to get their share of the fortune) and to give them a sizable portion of their inheritance once they are eligible to do so.

How to prevent:
· Be at alert for signs: the messages are often sent by anonymous people posing as members of a royal family or a dignitary from Nigeria. Another red flag is lack of coherence in language; this is intentional, because sometimes these scammers claim to be foreigners from non-anglophone countries. Also watch out when they promise a reward too good to be true.
· Once the message has any of these signs, it is best not to reply.
· Filter your emails by marking such messages as spam, that way future scam emails automatically go into the spam section.
Conclusion
While attempts are being made to make the internet a safe place, cybercriminals are also looking for new points of vulnerability and even preying on the psychology of people, which makes it particularly susceptible.
Even if you avoid having your hard-earned money stolen, you could still be involved in a complex network of schemes that scam a poor victim. Therefore, it is important to be cautious; look out for red flags and act appropriately if you suspect fraudulent activity.

