Hiding In Plain Sight With NTFS Steganography
Steganography is the art of hiding data in plain sight, in this article Nihad Hassan takes a closer look at hiding data using the NTFS file system.

The art of data hiding (also known as steganography) is basically storing data in a place where it is not supposed to go. There are numerous techniques to conceal data in different digital file types like Text documents, images, audio and video files. The underlying file system that is used to host operating system files also can be exploited to conceal secret data and other executable files.
In this article, we will investigate advanced data concealment technique inside Microsoft Windows NTFS file system by talking about how the ADS feature of NTFS file system can be exploited to conceal secret data stealthy inside it. The same feature can be exploited to conceal malware and launch deadly attacks against target Windows machines, but of course you should never do that, its illegal.
What is the NTFS file system?
NTFS (New Technology File System) is a proprietary file system developed by Microsoft Corporation for its newer Windows operating systems beginning from Windows 3.1 and all their successors to date. NTFS has many enhanced features compared with FAT, making it the ultimate choice for all computers running modern Windows versions (+ Windows7).
In NTFS, a file consists of different data streams (See Figure 1). One stream is the primary unnamed stream that contains the actual data of the file that we are going to see after opening it normally. This unnamed stream also called the default or primary stream and is referenced when no stream name component specified as a part of the pathname.
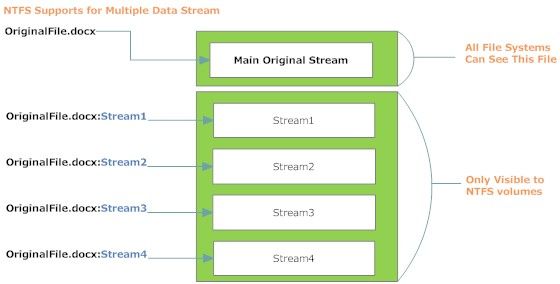
The second stream is the ADS. A file can have more than one ADS (Microsoft does not supply the number of allowed ADS files per a single file, but a test conducted by Jason Fossen suggests that the maximum is 4106 regardless of the size of the ADSs themselves [1].
An ADS feature has a number of interesting characteristics, as we can append it to existing files and folders without affecting their size on disk. ADS also are invisible in Windows file explorer and to the DIR command (using command prompt) unless we combine it with the /R switch. Besides, most anti-virus software will not scan ADS files for malicious code as this will increase the scan time significantly. All these features make ADS files a preferred location for intruders to conceal malicious code and later executing it silently using the START command (supported on Win® XP) or by using the WMIC command (supported on modern Windows® versions). Once executed by the intruder, it can carry out a silent installation of the malicious software on the victim’s PC. No process will appear in the process list of Windows® task manager; the program used to open the original file (default stream) will appear in the process list but no sign of the malicious program will be visible. Furthermore, we can attach the malicious program to a legitimate process, which will make detection of the code much more difficult.
How Can We Use Alternate Data Streams to Hide Files?
Now, let us begin concealing secret data in ADS stream files. We will experiment to hide a video file in the ADS stream of a text file.
- Create a new folder on the C:\ drive and call it secret.
- Open the command prompt window and change your working directory to C:\secret using the CD command.
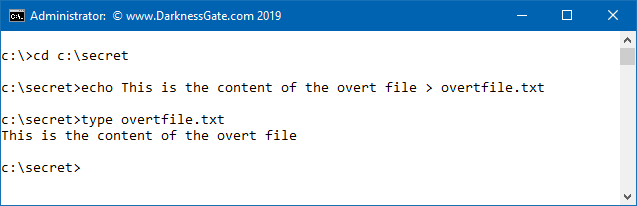
- Create a text file called overtfile.txt using DOS as shown in the following code snippet (See Figure 2). Use the TYPE command to read its contents and make sure it has been created successfully.
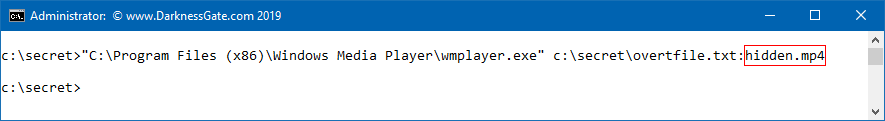
- Now we want to conceal our secret video file in the hidden ADS stream of overfile.txt using the commands appeared in (Figure 3)
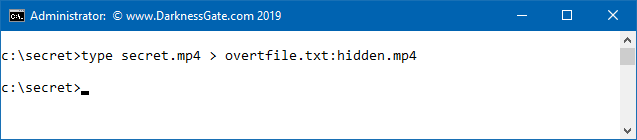
The Type command is used to copy the secret.mp4 content to be included in the alternative stream of overtfile.txt under the name hidden.mp4. The colon is the syntax used to create an ADS file. Please note that concealing videos in ADS streams will make them difficult to play and extract, later I will show you different ways to easily extract any file type hidden in the ADS.
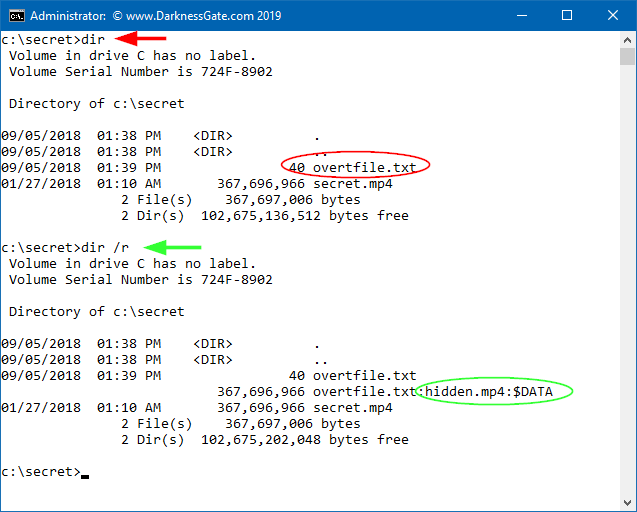
Use the DIR command to check all files displayed in the test folder as shown in (Figure 4). We see only one file, called overtfile.txt, while the other file (ADS file) is hidden. The hidden file in the ADS cannot be seen using DIR or Windows Explorer. However, if we use the DIR command combined with the /R switch we can see the hidden ADS file (Figure 4).
How To Retrieve Hidden Data Concealed In ADS Stream Files?
In our experiment, we demonstrated how to conceal a video file, to play this file we need to supply the path of the program which is going to open this video. I’ll use Windows Media Player as it is already available freely in all Windows versions (See Figure 5). Please note you must enclose the path to Media Player with quotations as it contains spaces.
If all worked well, your secret video should be playing now. If you prefer to use a tool to simplify the process of extracting different file types concealed inside the ADS streams, there is one great tool from NirSoft to perform this action automatically. It’s called lternateStreamView and can be found at http://www.nirsoft.net/utils/alternate_data_streams.html.
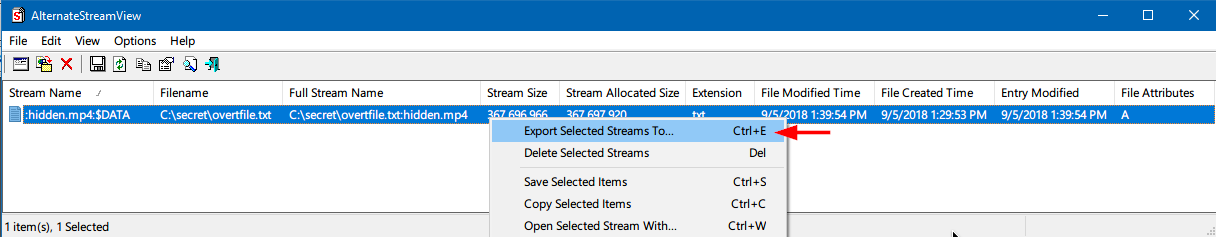
This tool allows you to scan your NTFS drive, and find all hidden alternate streams stored in the file system. After scanning and finding the alternate streams, you can extract these streams into the specified folder, delete unwanted streams, or save the streams list into a text/html/csv/xml file. After executing this tool, go to the File menu > Scan Options > specify the folder where you want this tool to scan for ADS streams then click the “Scan” button. A list of files which have an ADS stream appended to it appears, to extract the hidden stream of any file, right click over it and select “Export Selected Streams To...” and finally select the location where you want to save the extracted stream files (See Figure 6).
More Info
You can find more examples about concealing executable code in NTFS file system in the following locations:
1. Data Hiding Techniques in Windows OS: A Practical Approach to Investigation and Defense 1st Edition, Publisher: Syngress; 1 edition, ISBN-13: 978-0128044490, ISBN-10: 0128044497 | https://www.amazon.com/Data-Hiding-Techniques-Windows-Investigation/dp/0128044497/
2. Author InfoSec portal: http://www.darknessgate.com/security-tutorials/date-hiding/
References
- Data Hiding Tactics for Windows and Unix File Systems [Online]. Available from: http://www.berghel.net/publications/data_hiding/data_hiding.php (accessed 2018.09.05)


