An OSINT Script For Scanning Multiple Organizations Using Shodan and Golang
Security researcher Wojciech created a great OSINT script to scan multiple organizations using Shodan & Golang.

I wrote a script in Go which queries the Shodan database based on a list of organizations that you feed into it. Then it retrieves all the bug bounty participants from the Bugcrowd website and connects these two things.
INTRODUCTION
Everything began when I wanted to learn a new programming language and start on projects related to security in some way. I decided to start with Go (Golang) and Shodan. I thought to myself, why scan one organization with multiple tools when I can scan multiple organization with one tool?
For those, who doesn’t know what Shodan is, here is their main page.
Besides webcams, refrigerators, SCADA systems, MMQT, external disks, Shodan can help with subdomain enumeration and it’s very helpful in reconnaissance.
The scariest search engine on the Internet can operate on filters like: “port”, “city”, “hostname” or “org” for organization and by now I think you know where this is going.
A Few Notes On Script
That was my first contact with Golang ever. I quickly have got acquainted with this language (A Tour of Go was very helpful) and just start writing. It wasn’t easy at the beginning but StackOverflow did his job. I realize, this is not a masterpiece but I’m proud that it worked at all.
Script gets file including organization names separated by newline and next makes query to Shodan’s database.
Example usage:
./shodan hosts.txt
Content of hosts.txt
Sony Facebook Dropbox
Counter of founded results is broken, so do not count on them ;)
Additionally, we are not interested in smb, smtp or dns services, so I added most used HTTP ports to request. The final query can look like this:
org:’Sony’ port:’80, 81, 443, 8000, 8001, 8008, 8080, 8083, 8443, 8834, 8888'
Sony is not an accurate request at all. This includes:
Sony Network Communications Sony Computer Entertainment America LLC Sony Network Taiwan Limited Sony Communication Network Corporation Sony Pictures Entertainment Sony Media Software and Services
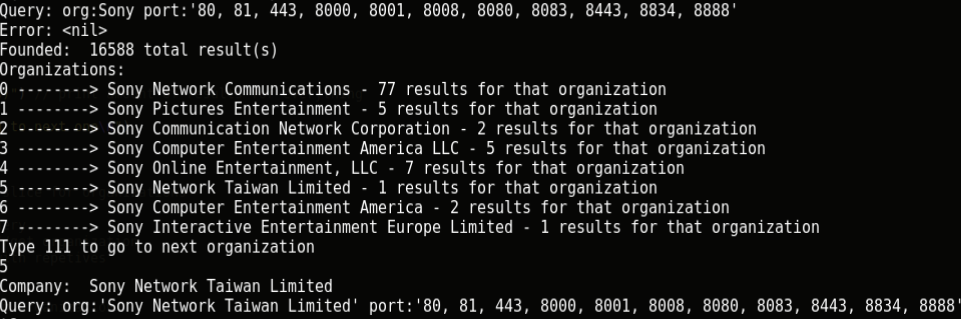
The script will ask you exactly which companies you want to scan. It’s extremely important that you shouldn’t test any domains, which are out of scope or do not participate in bug bounty program.
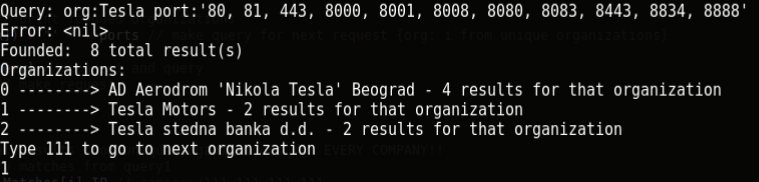
An excellent example is in this screenshot:
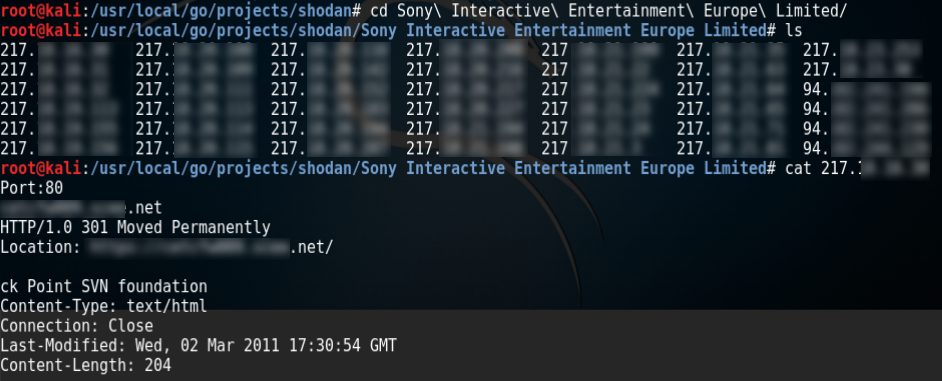
As output, script makes directory with same name as scanned organization and HTTP responses are saved into file named with corresponding IP. I added also port number and hostname (if exists).
Example output can look like below:
What Is This Script For?
This script is of course for finding vulnerabilities, which often exist in old, forgotten or subdomains that have not been updated. Shodan can find interesting (from security perspective) web applications which can lead to information disclosure on other more or less dangerous vulnerabilities. To proof my words, I obtained all organizations from official Bug Bounty list (https://bugcrowd.com/list-of-bug-bounty-programs) with help of goquery (below function) and next of course I passed it to my script.
func bugcrowd() []string{
doc, err := goquery.NewDocument("https://www.bugcrowd.com/bug-bounty-list/")
if err != nil { // if cant connect
log.Fatal(err)
}
s := make([]string, 455 ) //slice of strings
doc.Find("td a").Each(func(index int, item *goquery.Selection) { //for every organization in "td a" (table)
linkTag := item.Text() // get text
s[index] = linkTag //put in to map
})
return s // return slice of organizations
}
I had to be cautious and paid close attention to scope of the programs. When only one domain is in scope, there is no need for scanning and we need to go to the next one. Only organizations, which allow us to test all of their infrastructure or have *.domain in scope are our potential targets.
What can be found?
After scanning all of the companies and digging a while, I found local file inclusion vulnerability on of the scanned websites. It did not even take too long. I reported it and possible will update this article with more info when it will be fixed.
Additionally is great source of information, from link to link, I stumbled upon path disclosures, internal addresses and hostnames and a lot more. Also some of the websites look like from 10 years ago, so it’s good start to look closer and try known tricks.
There are also plenty of 403, 404 or 401 errors but it’s not a problem to remove them in bash.
find -exec grep -l ‘404’ {} \;| xargs rm
Conclusion
This script was written as a tool to find vulnerabilities in companies who are currently offering bug bounties. I remember a guy who found an open redirect vulnerability in Apache, scanned all in-scope domains of bug bounty programs and reported them all.
My approach is “quantity over quality” and you need to dig a little to find something interesting, but it’s good place to start. I have not looked through all files yet but I feel that previously mentioned Local File Inclusion won’t be the only one.
You can find the full script here.
Header Image by Vic Bell
