Power Grid Vulnerabilities
Smart grid technology presents an opportunity for threat actors seeking to disrupt the power grid.

Our current electric grid was built in the 1890s and improved upon as technology advanced through each decade, today a new form of technology is being tested called the smart grid. This type of power grid provides the opportunity for two-way communication between the consumers and electricity producers and providers.
However, using smart grids in this way, presents an opportunity for cyber criminals to exploit the numerous security vulnerabilities that are inherently available. Hackers can do unprecedented damage in the form of causing widespread blackouts, stealing customer data, and destroying industrial control system (ICS) equipment, ultimately costing utility companies hundreds of millions of dollars in damages.
I propose three solutions to mitigate the opportunity for hackers to exploit vulnerabilities: ranking interdiction surfaces, implementing a threat hunting framework, and implementing in-network deception technology. Ranking interdiction surfaces will allow security professionals to accurately identify vulnerabilities and rank them with a priority. This could be compared to triage in medicine. Implementing a threat hunting framework will promote prevention of cyber-attacks through early detection. Finally, the implementation of in-network deception technology is vital as a defender with technology that is already infested with potential attack vectors.
Problems
Liu defines industrial control systems (ICS) as, “a general term that covers several types of control systems and related instruments for industrial process control” (2021). In recent years, municipalities have merged the ICS technology with information and communication technology (ICT) which has opened the flood gates for hackers to exploit vulnerabilities. However, using smart grids in this way, presents an opportunity for cyber criminals to exploit the numerous security vulnerabilities that are inherently available.
The nascent technology of smart grids is a clear step in the right direction for efficient energy consumption. However, hackers can do unprecedented damage in the form of causing widespread blackouts, stealing customer data, and destroying industrial control system equipment, ultimately costing utility companies hundreds of millions of dollars in damages.
According to a research paper by Adepu, there has been a realization of substantial risk to society in the wake of the Ukrainian power outage caused by the cyber-attack Black-Energy. He also highlighted that in a conventional power grid the only way to manage the power supply during peak demands, is to increase the power, which in turn, causes greater losses of energy when it is not fully utilized. He made clear that smart grids, coupled with information and communication technologies (ICT), can be used to reduce energy losses. (2019, p. 191).
Moreover, research article that Al-Abassi authored explains that “the security concerns of critical infrastructure facilities are already considered in the IT community, limited efforts have been made to develop security solutions that are specific to ICSs and OT environments” (2020, p. 83965). His research underscores the potential dangers of cyber-attacks on critical infrastructure. He highlights semi-recent global attacks: in 2015 the Black-Energy cyber-attack cause a massive power grid outage in Ukraine, in February 2020 the U.S. Colonial pipeline, and the 2010 Stuxnet attack on the Iranian nuclear development facility. These industrial control system cyber-attack examples do not all relate to smart grids, however, they do demonstrate the rising development of never-seen-before cyber-attacks on industrial control systems globally and at all levels: nation state and hacktivist alike.
Figure 1 shows what a smart grid looks like. Illustrated is the electricity flow, the different stakeholders involved, and where the secure communications are flowing. Imagine all the attack vectors baked into this representation of our modern-day electrical grid since the infusion of information and communication technologies into industrial control systems.
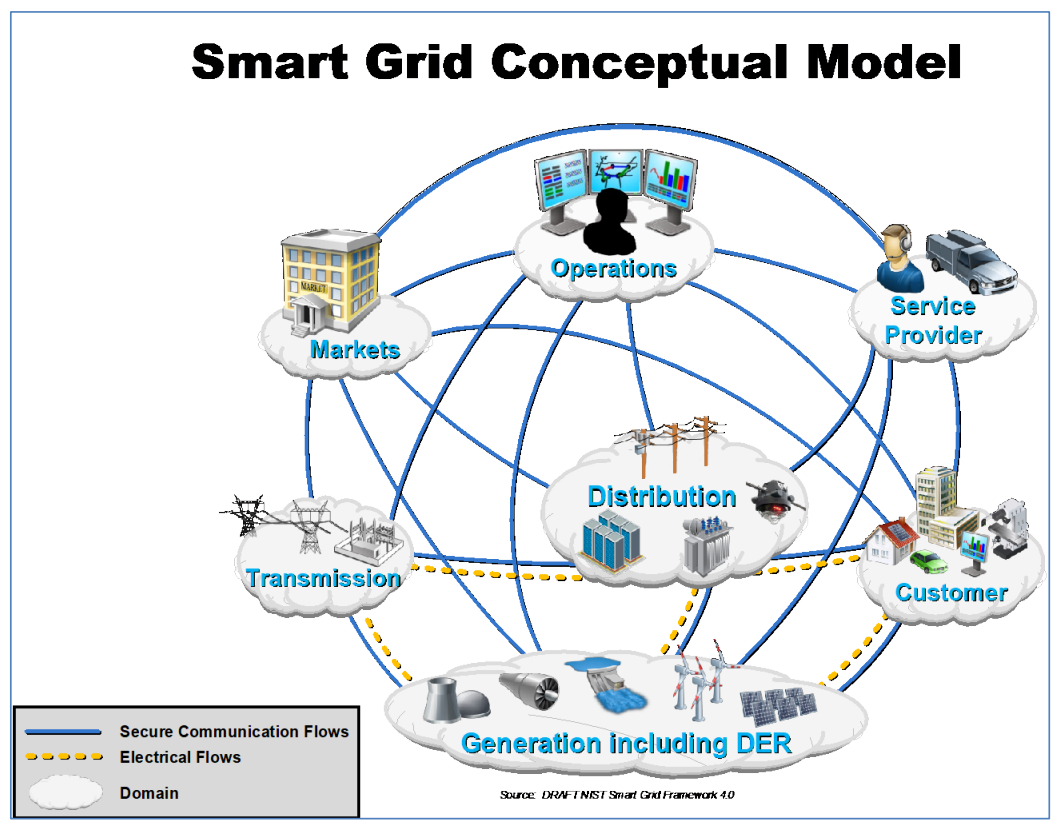
Figure 1. A Smart Grid Conceptual Model
A Potential Solution:
I have promulgated three solutions to mitigate the opportunity for hackers to exploit vulnerabilities: ranking interdiction surfaces, implementing a threat hunting framework, and implementing in-network deception technology. Ranking interdiction surfaces will allow security professionals to accurately identify vulnerabilities and rank them with a priority. This could be compared to triage in medicine. Implementing a threat hunting framework will promote prevention of cyber-attacks through early detection. Finally, the implementation of in-network deception technology is vital as a defender with technology that is already infested with potential attack vectors.
Ranking Interdiction Surfaces
A proposed solution to the myriad of challenges in the cybersecurity side of ICS is to remove as many vulnerabilities as possible thereby reducing the attack surface. How this gets accomplished is through a systemic process called prioritizing interdiction surface-based vulnerability remediation. Wang et al. stated in his research article, “As a side effect of such technologies, more and more vulnerabilities in hardware, software, or policies are brought into the ICS, which allows attacker to gain unauthorized access to the system. However, sophisticated attackers are not satisfied to exploit single vulnerability any longer, and they instead launch multi-step and multi-host attacks with multiple vulnerabilities, posing a greater threat.” (2022 p. 1).
The first proposed solution works to mitigate the vulnerabilities through a process of three steps. The first phase is to prioritize interdiction surfaces. Second phase consists of ranking vulnerability remediations. Lastly, calculate composite metrics. Ultimately this solution is a way to triage the current landscape of vulnerabilities and remove as many attack vectors as possible.
Threat Hunting Framework
In addition to ranking interdiction surfaces, establishing a threat hunting framework (THF) will support the reduction in possible attacks through prevention. According to Jadidi and Lu’s research, “Existing security mechanisms like firewalls, anti-malware, and security information and event management (SIEM) are reactive methods. Reactive security mechanisms can help networks to detect attacks and prevent repeat attacks by improving their protection strategies” (2021 p. 164118). Therefore, establishing a THF is critical for the prevention of cyber-attacks. The proposed industrial control system threat hunting framework (ICS-THF) consists of three phase, triggers, threat hunting, and cyber threat intelligence. This framework uses the MITRE ATT&CK and the Diamond model of intrusion analysis to detect threats inside an ICS network. Figure 2 illustrates a threat hunting framework model proposed for ICS.
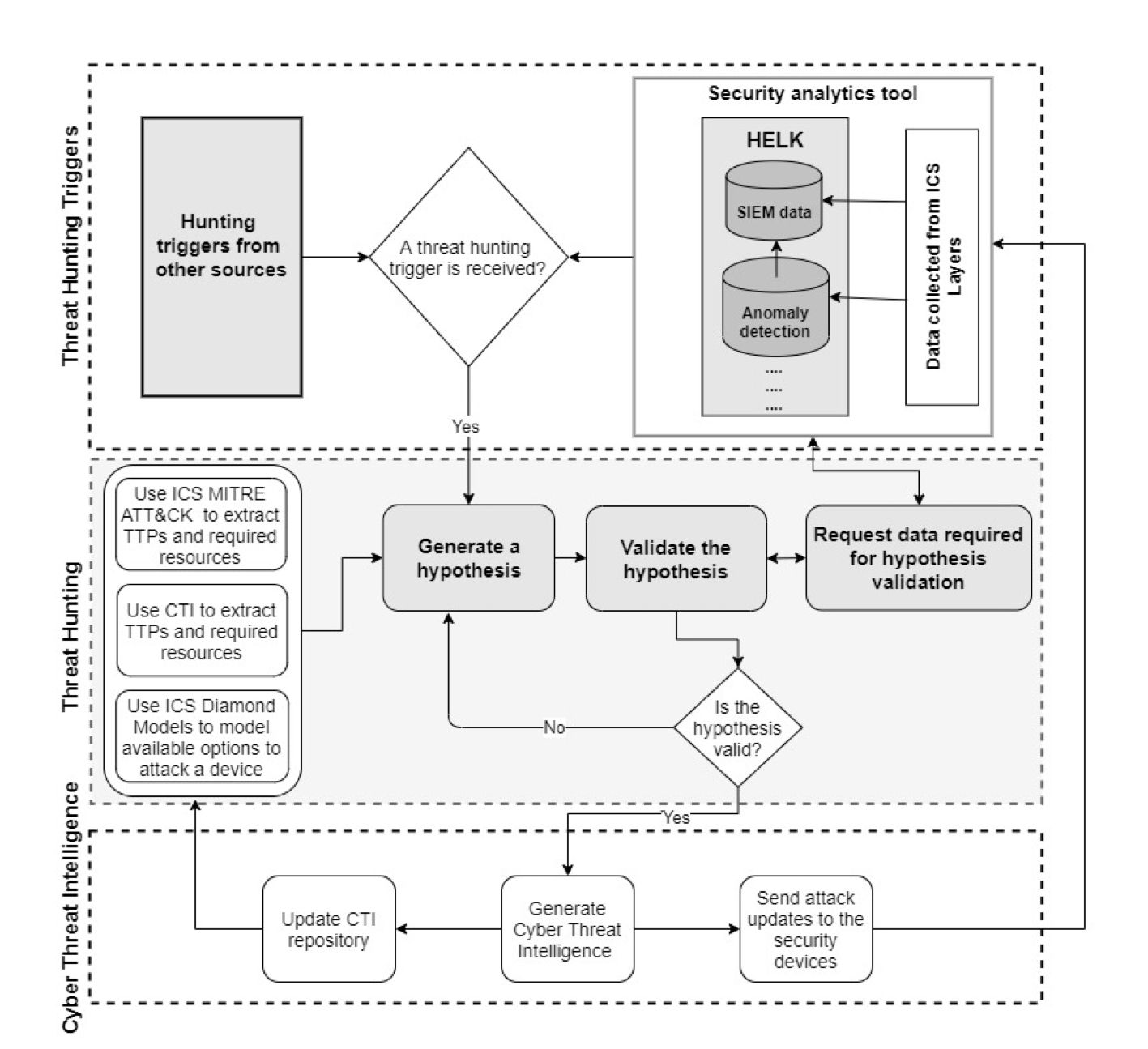
Figure 2. Threat Hunting Framework for Industrial Control Systems
In-Network Deception Technology
Finally, the last solution is what cyber security experts call the In-Network Deception Technology. In-network deception technology can be categorized into two types: honeypot and in-network deception. A honeypot is where a realistic device is intentionally exposed outside the network to fool attackers to collect intelligence. The in-network deception technology is nascent and has not been studied by academia to the extent that is required to be fully supported by the industry. However, setting traps for criminals is not a new idea and has been working since the beginning of time. Mashima highlighted in his research paper, “each technology has advantages and disadvantages, and no single solution is perfect. Thus, it is desired to combine multiple, heterogeneous cybersecurity solutions that are complementary to each other, realizing defense in depth” (2022, p. 1). Figure 3 illustrates what in-network deception technology might look like when integrated with a smart gird.
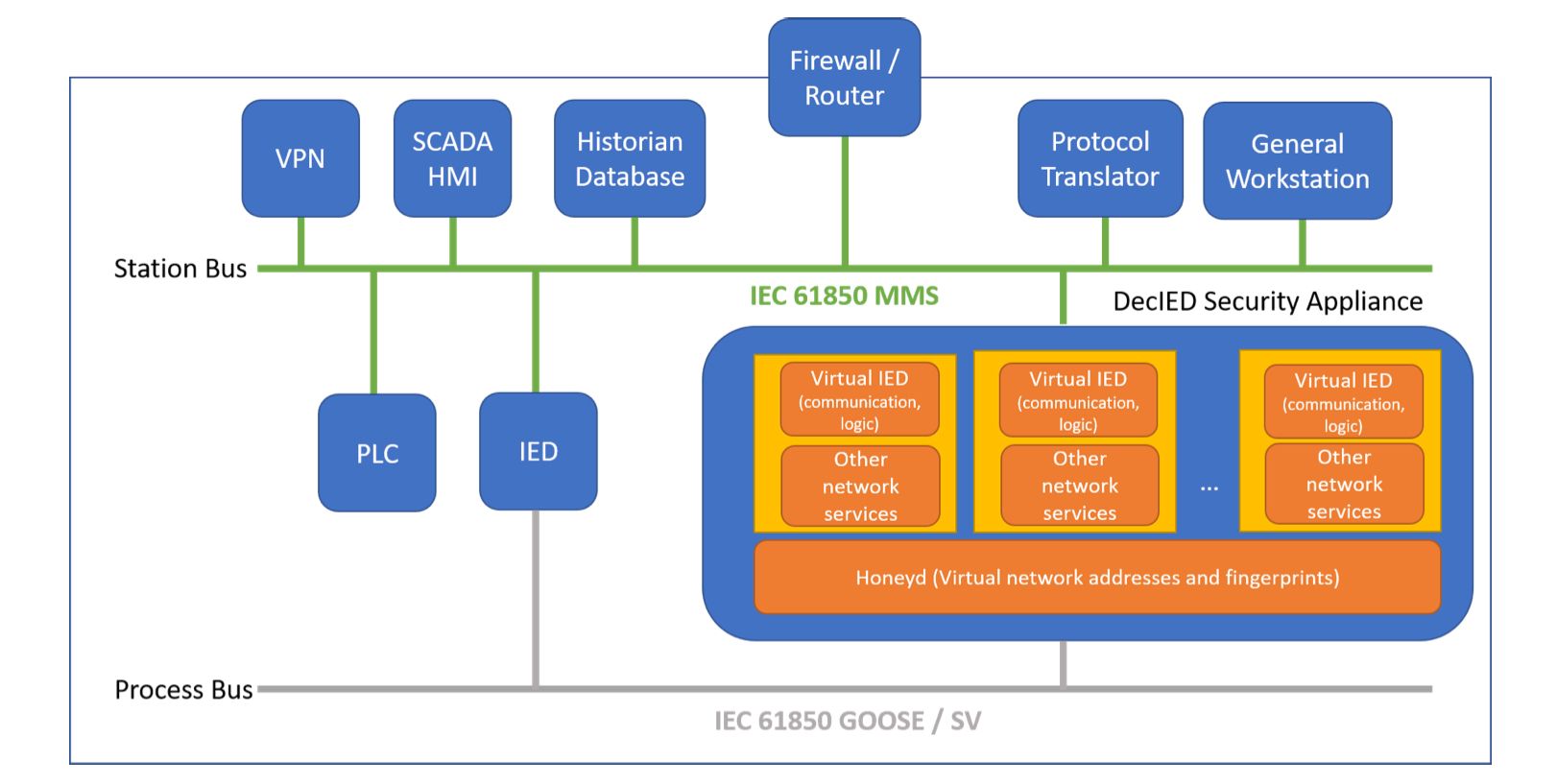
Figure 3. In-Network Deception Technology
Mashima concluded, “deception technologies are promising solutions that can provide an additional layer of security for protecting modernized industrial control systems, including smart power grid systems” (2022 p.11). It is in every municipality’s best interest to integrate this solution as an additive to their defense mechanisms to protect against the current threat landscape in 2022.
Summary
In summary, smart grids are only going to become increasingly integrated with our nation’s current industrial control system landscape. It is crucial that we implement the most up to date defense solutions and research out there, to better defend our critical infrastructure. Through the compound use of ranking interdiction surfaces for vulnerability assessment, standing up threat hunting frameworks, and utilizing in-network deception technologies we can better secure industrial control systems and keep innovating with technologies like smart grids.
References
Adepu, S., Kandasamy, N. K., Zhou, J., & Mathur, A. (2019). Attacks on smart grid: Power supply interruption and malicious power generation. International Journal of Information Security, 19(2), 189-211. https://doi.org/10.1007/s10207-019-00452-z
Al-Abassi, A., Karimipour, H., Dehghantanha, A., & Parizi, R. M. (2020). An ensemble deep learning-based cyber-attack detection in industrial control system. IEEE Access, 8, 83965-83973. https://doi.org/10.1109/access.2020.2992249
Gopstein, A., Nguyen, C., O'Fallon, C., & Wollman, D. (2021). [Journal Image] NIST framework and roadmap for smart grid interoperability standards, release 4.0. National Institute of Standards and Technology. https://www.nist.gov/ctl/smart-connected-systems-division/smart-grid-group/smart-grid-framework
Jadidi, Z., & Lu, Y. (2021). A threat hunting framework for industrial control systems. IEEE Access, 9, 164118-164130. https://doi.org/10.1109/access.2021.3133260
Jadidi, Z., & Lu, Y. (2021). [Journal Image] A threat hunting framework for industrial control systems. IEEE Access, 9, 164118-164130. https://doi.org/10.1109/access.2021.3133260
Liu, C., Alrowaili, Y., Saxena, N., & Konstantinou, C. (2021). Cyber risks to critical smart grid assets of industrial control systems. Energies, 14(17), 5501. https://doi.org/10.3390/en14175501
Mashima, D. (2022). [Journal Image] MITRE ATT&CK based evaluation on in-network deception technology for modernized electrical substation systems. Sustainability, 14(3), 1256. https://doi.org/10.3390/su14031256
Mashima, D. (2022). MITRE ATT&CK based evaluation on in-network deception technology for modernized electrical substation systems. Sustainability, 14(3), 1256. https://doi.org/10.3390/su14031256


