Privacy And The Trail You Leave Behind
In a world where everyone is over exposed in the context of privacy the, coolest thing you can do is maintain your mystery argues Shivam Singh Sengar.

All of us, as active users of internet specially the social media, are always concerned about our privacy and our data that is processed by the giant organizations. The recent Facebook privacy breach incident has significantly escalated things in this domain.
In a world where everyone is over exposed the coolest thing you can do is maintain your mystery. (~Unknown)
A while ago, a blog drove my attention towards the privacy issues we deal nowadays, especially over the internet. World Wide Web is a very complex human invention and thus, technically very less understood by humans. The blog talked about how even TOR is compromised with honeypots. A decent explanation and working of honeypot will require a whole different article and I won’t try it here.
As Wikipedia stated, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data that appears to be a legitimate part of a website but is actually an isolated and monitored, and that seems to contain information or a resource of a value of attackers, which are then blocked. They are often used as baits for criminals, by legal authorities for undercover surveillance on various platforms like TOR.
The key thing is to minimize (or eliminate) your digital footprint while surfing the web. Webopedia defines digital footprint as a trail that people leave online. It is information transmitted online, such as forums registration, emails and attachments. This even includes your comments, likes and shares over different social media platforms.
The extent to which you want to minimize this footprint depends whether you are a hacker, a student (or employee) using an institutional network, or just a person sitting in front of your desktop at home. The important thing is to have control over your digital footprint. Make sure, what you want is only being shared online, or is available over the internet for others to see.
We usually switch our browser to incognito mode while surfing privately and thinks that we are doing fine in protecting our privacy. Browsing using private mode is not 100% private. The only thing that this mode does is stop storing history, cookies and temporary files on the client side. What about over the server side? In short, the answer is — nothing. Websites (on the server side) keep information about your IP and other data during the session.
This stored data can be stored in non-encrypted form. So, here much is left on the developer of the application you are using. Also, the use of incognito mode doesn’t restrict the sniffers from viewing the data that enters or leaves your device. I will recommend the use of TOR browser if you want to extend your anonymity from what general browsers provide.
Websites we are surfing shares our data with other websites and keep track of our browsing. These trackers include advertisements, social media and site analysis sites and plugins. The collected data provides important input to the machine learning algorithms running on various servers.
They help to generate nice predicted options of what we might need or wishes to see. An advertisement on our visiting page is a product (to a great extent) of your previous searches. Organizations often sell this information to other organizations. The problem arises when the information is misused or it is stored in an unsecured (non-encrypted) manner.
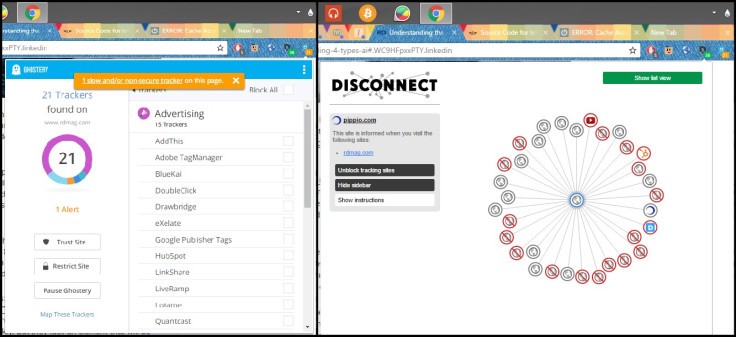
To get the feel of who is keeping track of your browsing and who is getting your data via a website, you can use browser add-ons. Two of my favorite ones are ghostery and disconnect. The cool thing about them is that they allow us to have control over who can keep track of us and who can get our data.
Ghostery tells about the trackers on the website, while disconnect shows the list (and graph) of the websites which might be receiving information about us. The image below shows their interfaces.
Another common mistake that people make is the improper deletion of files. We often sell (or dump them into dustbins) our used electronic devices like mobiles, laptops, printers, pen drives and external hard disks to others. Before that, we simply delete our important files, pictures or format the device.
Deleting a file only removes the reference to file objects, while actual data still resides in the memory. Anyone having access to the device can easily recover the data using any third-party software. There are many software available which securely clear data by overwriting them in multiple turns. CCleaner is a very good tool to perform the secure deletion. In case you are using Linux, commands like the ones below can come to your rescue.
shred /dev/sda
dd if=/dev/random of=/dev/sda
I will recommend you to go through the use of these commands by googling them. They are very good commands and will come in handy. You can find more about about the traces left behind in hard disks even after deletion here.
The Internet is the home of many viruses, Trojans, malware and worms. One must make sure about what websites are writing on your disks, especially on your C drive. Be cautious while downloading files from the internet. And keep an eye on the extension of the downloaded files, before opening them. Make sure that you have blocked pop-ups by going in the browser’s settings.
The most important thing is to be always alert and pay attention to what the websites are trying to do. Don’t open the links, unless you are sure, that are forwarded to you in group chats as they might hold malicious stuff.
You can check for malicious links at VirusTotal.
After a virus is planted on the device then it will start sending your sensitive data to its creator by creating a TCP connection. This is basically what Trojans do. One way of detecting a Trojan is using typing netstat (in windows). Any odd looking connection is possibly a Trojan.
In the end, I will say, keep learning how things work and don’t be easy targets for hackers (or hackers who are better than you). The primary weapon that any hacker has is carelessness and ignorance of the victim. By increasing your knowledge and understanding about the networks and applications running over internet will greatly increase the amount of work hacker need to do before tricking you into a trap.
Author: Shivam Singh Sengar
Image by Jack Teagle
