Simple Protection Against Ransomware (Ryuk)
In recent weeks ransomware hysteria has been sweeping the press thanks to a fresh wave of high profile infections.

In recent weeks ransomware hysteria has been sweeping the press once again thanks to a fresh wave of high profile infections. Businesses from all over the world have been reporting outbreaks of a ransomware strain known as Ryuk.
Searching for “Ryuk Ransomware” on Twitter yields many results across firms big and small, even a handful of tweets from IT folks reaching out to the security community looking for a decrypter. Sadly, no such tool exists at the time of print.
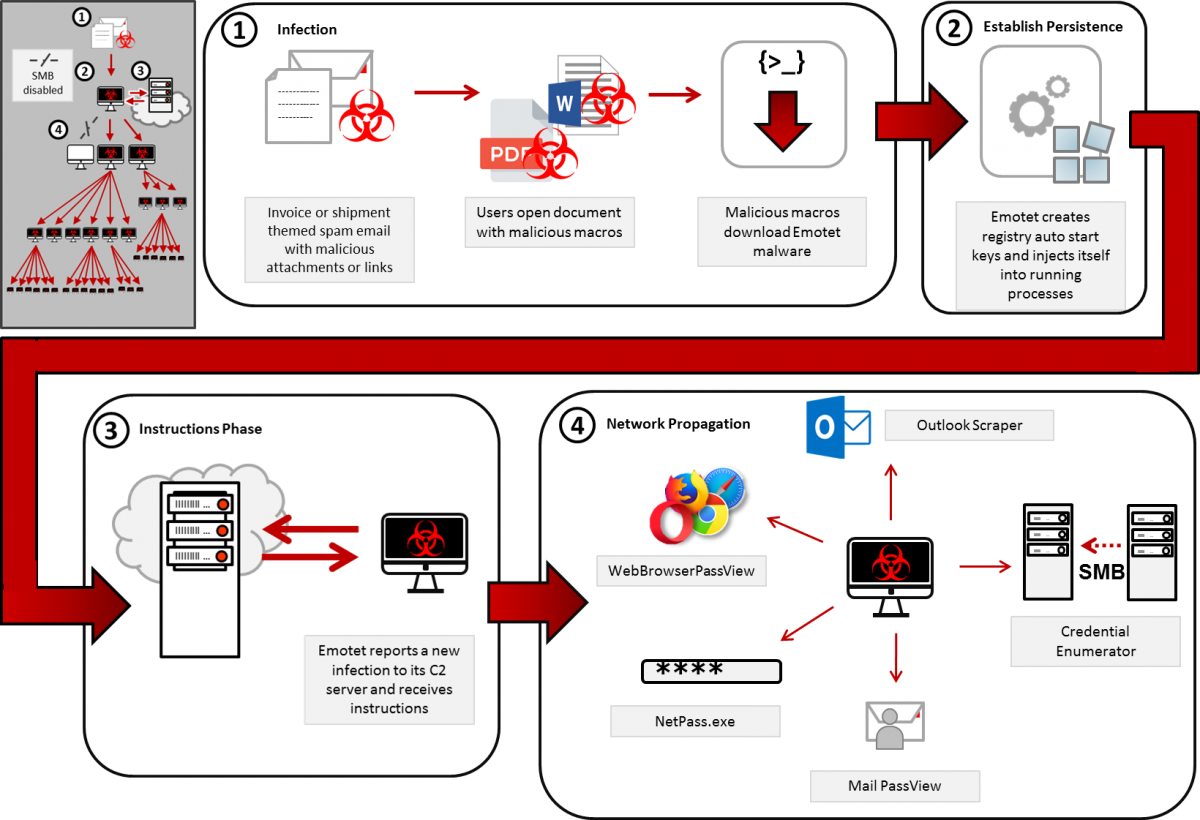
This particular strain seems shrouded in a cloud of mystery as details of its methodology are sparse. We do know the initial foothold is gained via an Emotet and or Trickbot infection, which lead to delivery of Ryuk. But this isn't an ordinary ransomware infection.
After a successful Emotet infection the Ryuk attackers will lurk on your network, learning and embedding themselves before manually deploying the ransomware with a variation of tactics which include group policy abuse and disabling anti-malware software. This methodology allows the attackers to grow a deep, hard-to-remove foothold into your network. This new and very invasive tactic has the cyber security news room churning and rumour wheel turning.
I'd like to demystify the rumors to help blue teams understand that this ransomware and others like it do not require million-dollar fusion centers with world class security experts. In fact, essential enterprise security tooling and hygiene should be enough to keep Emotet, Trickbot, Ryuk and their friends away (!)
It's widely known that Ryuk is delivered by Emotet and Trickbot. It's also known that these attackers will lay low on the network for weeks or months before springing their trap but what is not known is the ransomware itself. So instead of focusing on detecting the ransomware we will focus on detecting the already well known malicious behaviour that preludes it.
Prevention
Threat feeds
There's an ecosystem of security researchers out there squirreling away at malware samples from across the net. Most of these people are hobbyists who may or may not be getting paid for their work. These researchers kindly publish their work for blue teamers and these publications are often pushed to aggregators some of which are free!
Services like https://abuse.ch/ offer a free plain text feed of IOCs like hashes, urls and IPs which should not be trusted. Feeding these IOCs into your Firewalls, AV, SIEM, EDR and whatever other tools you can will help you detect certain malware stains early on. If you're brave enough you could even preemptively block the IOCs from the feed.
Group Policy Hardening
Blue teams should consider using Windows Group Policy to block the execution of external macros which will halt an initial infection altogether. Users will not be able to execute macros that are from outside the organisation however it's possible for the macro to be manually unblocked with PowerShell.
Caveat: this should be reserved for IT admins once the macro in question has been checked with a sandbox or AMSI enabled AV.
User training
Running in person or even online training about the dangers of phishing is a worthwhile endeavour, some geographies or business sectors even require it by law. Keep user training simple by removing technical jargon and presenting information in clear digestible chunks. Long and complex training will be ineffective because it's hard for regular non technical people to follow along, let alone remember what you might be trying to teach them. Also you should work to make your phishing email reporting system simple for users to encourage reporting. Also - reward and celebrate every small success!
Hygiene
Basic cyber hygiene is essential to warding off the bad guys and is often overlooked for more exciting, challenging work. Checking off the following on a weekly basis has no harm and might be a good chunk of work to automate or train a junior member on:
- Ensure DMZ system ports are locked down. Do not expose RDP to the internet.
- Health check your security software. Perhaps use EICAR against your AV?
- Keep SIEM and EDR use cases current and relevant to today's threats.
- Implement a good password policy. Complex isn't always better!
- Ensure all systems are patched regularly and verified.
- Egress ports and firewall rules regularly verified.
Detection
Suspicious process behavior
Monitoring for indicators of compromise like hashes is becoming slightly redundant because malware changes so quickly. It's easy for attackers to deliver something almost completely new to every victim. We should focus more effort into monitoring for malicious behaviour instead. Dont worry IOCs, there's still room for you!
Firstly use your endpoint monitoring or EDR to look for suspicious process parent/child relationships.
Winword.exe spawning PowerShell.exe or CMD.exe is a positive sign of successful phishing. This can be expanded to look at the entire office suite spawning suspicious processes.

We should also monitor use of vssadmin. Ryuk and many other ransomware strains will attempt to hamper recovery efforts by deleting backups with Windows utility vssadmin.exe
We should look sharp also for unauthorised use of: vssadmin.exe delete shadows /all /quiet
Emotet and other kits will often try to persist on a victim system by abusing Windows functionality. This is commonly known as Living Off The Land.
You should specifically monitor for modifications to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
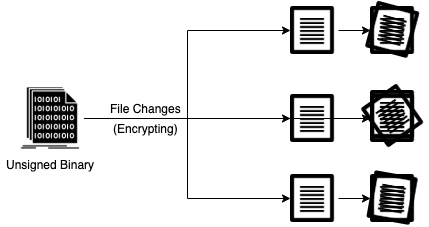
Furthermore if you are running a decent EDR tool watching out for mass file modifications by an unsigned binary may help detect some ransomware strains.
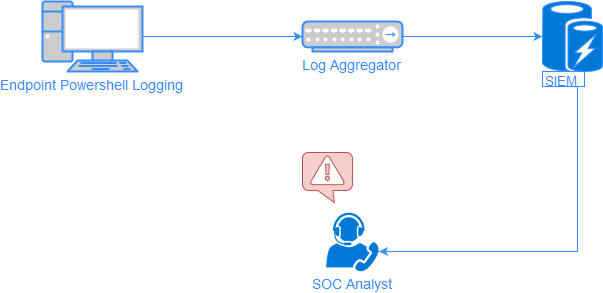
PowerShell logging
Emotet and many other malware just like it abuse Windows PowerShell to take hold of their victims. To detect the attack at this stage you should enable Windows PowerShell logging (which isn't enabled by default) and pass the logs off to your SIEM for analysis. An in depth guide on this subject can be found here.
I bang this drum so regularly because PowerShell is being used for all kinds of malware attacks world over. It's such a valuable solution that I think is being overlooked.
Ryuk seems very mysterious, but in reality it's just another strain of ransomware that we are already used to dealing with. To my mind the only difference here is the manual delivery by Ryuk operators.
I regularly post threat detection tactics just like this on my Twitter feed.
The awesome gif in this post is called Cyber Threats by Mike Mirandi.

