Researcher Assaulted By A Vendor After Disclosing A Vulnerability
Following a serious vulnerability disclosure affecting casinos globally, an executive at Atrient has allegedly assaulted the researcher who first disclosed the vulnerability.

Following a serious vulnerability disclosure affecting casinos globally, an executive of casino technology vendor Atrient has allegedly assaulted the security researcher who disclosed the vulnerability at the ICE conference in London. This is the story of a vulnerability disclosure gone bad, one involving the FBI, a vendor with a global customer base of casinos and a severe security vulnerability which has gone unresolved for four months without being properly addressed.
Our story begins with two white-hat security researchers, Dylan and Me9187, who were on a Shodan safari back in September when they noticed what looked like a casinos player reward server (with no authentication) exposed to the public internet. After a little more investigation by the researchers, it became obvious that the server was supporting player reward kiosks in different casinos all over Las Vegas.
These kiosks are made by a vendor called Atrient who market them as a 'PowerKiosk Marketing Platform' and sell them to casinos globally who then use these kiosks to engage their casino customers with a loyalty reward program.
The kiosks provide loyal casino customers with a user interface they can use to register their purchases and spending at the casino, receiving loyalty bonuses in return. Bonuses can include theatre and show tickets, comped hotel rooms, entries into cash prize draws and anything the casino wants to use as part of their reward program, including offering cash back on purchases in some casino locations.
Casinos who use these kiosks include Hard Rock and Caesars, the researchers told me that these kiosks are deployed in casinos all across the country.
These kiosks and the back end server communicate the personal details of their users and send data like drivers license scans (used for enrollment), user home addresses and contact details, as well as details about user activity, unencrypted over publicly accessible internet. When the researcher discovered that the unauthenticated reward server was directly connected to the kiosks on the casino floor they realized that the API the kiosks used was wide open and extremely vulnerable to criminal abuse.
The researchers told me that every single kiosk was calling home to the server in plain text and all data sent from the kiosks to the server clearly visible on the network. There was no SSL protection, the API is wide open and vulnerable to abuse and it is possible to identify kiosks by their MAC address and use the unsecured API to change details, track users and add credit to user accounts and even spin up a kiosk on a virtual machine in order to have your own personal kiosk at home.
Atrient were not segregating these kiosks into vlans, their FTP access was wide open and unencrypted, and all of this was discovered using the Shodan search engine, all of it was publicly visible to anyone on the internet who knew where to look.
Atrient is a market leader in selling these loyalty kiosks to casinos and because these kiosks have been sold to casinos all over Las Vegas, the United States and (via their partnership with Konami) to casinos all over the world. Considering that Atrient COO Jessie Gill said in the media recently that they "don’t have a different version for different operators; we integrate all functions in a single product", there is a very high likelihood that this vulnerability affects all of their customers, including their white label partners Konami who rebranded Atrient's tech for sale to their own customers.
The security researchers who first discovered this vulnerability, Dylan and Me9187, told me that the vulnerability was just the tip of the iceberg when it came to sloppy security practices at Atrient. They saw casino WiFi network passwords stored in plaintext, user personal data stored in plaintext and no attempt to secure anything.
They even found Atrient's third party contractors (based in India) posting Atrient's source code on Github and asking stack overflow questions about it, an indicator which made it obvious to the researchers that security was not being taken seriously. They probably were not even using a remote browser either.
It was clear to the security researchers that Atrient had outsourced their development to India where a significant amount of their services were being hosted, including their FTP, kiosk management services and the development servers. It was obvious to the security researchers that the subcontractors were not taking even basic security steps to secure any of this infrastructure from being discovered on the open internet.
Reporting The Vulnerability
The security researchers acted in good faith, followed responsible disclosure best practices and tried to directly contact Atrient to report the vulnerability and make them aware of how serious a problem this was. For a company like Atrient with a global customer base and a record of talking about how secure their systems were, you would expect them to respond immediately. Unfortunately Atrient completely ignored repeated emails to multiple executives and members of the Atrient team.
The researchers even left messages with their contact details on the FTP server for the admins to see, warning them about the vulnerability. The made every effort to get in touch with the vendor and responsibly disclose but they were ignored.
Atrient completely ignored the researchers, but despite following them on Linkedin and Twitter they clearly had no interest in communicating with the researchers.
The researchers then reached out to me, asked for my help in contacting Atrient and asked me to tweet out about the vulnerability on Twitter, so I helped them.
Enter The FBI
When I sent out the tweet reporting that I was working on a story about the vulnerability, one which affected casinos all over Las Vegas, the tweet was noticed by the FBI's Cyber Fusion Unit who then reached out to me for a conversation.
This particular FBI division worked towards connecting security researchers to vendors when vulnerabilities had been discovered, particularly in cases where the vulnerability is serious and the researchers are being ignored by the vendors.
I was asked by the FBI to put together a call with the researchers who, wanting to act in good faith, agreed to join the call. They were scared, it was the FBI after all, in general security researchers tend to be wary of the feds, but they agreed to talk to them.
On that the call the researchers thoroughly briefed the FBI on what they had found and the attempts they had made to contact Atrient. The FBI sprung into action and set up a call for the next day between Atrient and the security researchers so we could all get on the phone together and make sure Atrient properly understood how serious the vulnerability was, everyone involved was focused on remediation.
Now the FBI was involved Atrient would have to take the vulnerability disclosure seriously, it gave us hope that the vulnerability would be quickly remediated.
I am pleased to report that the FBI did the right thing, their sole interest was resolving what they considered to be a serious vulnerability and at no time did the FBI lay any blame at the feet of the researchers or accuse them of anything. There is a lot of mistrust in the infosec space when it comes to the FBI, but this particular unit had the right attitude, knew their infosec and wanted to help the researchers.
** UPDATE Call recording : https://dayafterexploit.com/Skype1.mp4
The above call recording of the initial FBI conversation was added to this article on Feb 7th 2019 after it became available in this article from CBR Online.
The Vendor Call
The next day I joined the vendor call with the FBI and the security researchers, Atrient was represented by Jessie Gill, their COO and another member of staff. When the call started and everyone had been introduced the floor was handed over to the security researchers. The researchers explained in simple terms that the kiosks and supporting infrastructure was wide open, that players credit could be manipulated, that users personal data (including drivers license scans) was exposed to the public internet and that you could enter casino cash prize draws with as many entries as you wanted in order to win them, all without Atrient or their developers and subcontractors noticing.
They clearly explained to Atrient how the risk of abuse was extremely high because there is no way to differentiate the legit calls from the malicious api calls in the Atrient back end system, leaving it wide open to malicious exploitation by criminals.
Atrient's COO Jessie Gill asked what steps they could take to secure these services and the researchers advised them of the urgent actions they needed to take to secure their infrastructure. in response to this Jessie said "The information you have shared with us is fantastic, we're really impressed by what you have done here and we would like to actually own this information. How do we make that happen?" and invited the researchers to a private conversation to discuss that with them.
At the end of the call the FBI asked Atrient if they had properly notified their customers of this breach and vulnerability in their systems, their COO Jessie quickly replied "lets talk about this offline", immediately closing down the question.
** UPDATE Call Recording: https://dayafterexploit.com/Skype2.mp4
The above call recording of the initial vendor conversation was added to this article on Feb 7th 2019 after it became available in this article from CBR Online.
The Bug Bounty Call
I was not privy to this call, but I have been told by the researchers that Jessie Gill promised them a bug bounty of $60,000 and asked them to keep the incident quiet until their lawyers could draw up an NDA and legal agreement for them to sign.
As far as the researchers were concerned Atrient was dealing with this in the right way, moving to secure their services, reward the researchers who reported the vulnerability with a bounty and instructing their legal team to draw up the paperwork to cover the engagement. The researchers of course were absolutely thrilled by this, they are both young and it is a lot of money.
Jessie Gill promised the researchers that lawyers would be in touch and send them those agreements, a promise that he made again and again for months.
The Run Around
From that point on Atrient led the researches around by the nose with the promise of money and gave them the run around. The researchers also tell me that Atrient have made no real effort to secure their services, but did hide some servers from Shodan's view and take the dev servers in India offline for a short time.
It became clear over four months that no legal paperwork or bug bounty was forthcoming and Atrient did not at any time ask the researchers to sign an NDA. It also became clear to the researchers that Atrient had made no significant changes to their security policies or the security of their services in that time frame. The security researchers were given the run around for four months, during which time they were promised a bug bounty and that the vulnerability would be resolved.
The ICE Conference Assault
Almost four months after the initial disclosure to Atrient, the security researchers learned that the Atrient CEO Sam Attisha had big plans for the ICE Conference in London where the security researchers are based. Sam Attisha had planned to speak at the conference about the new facial recognition feature in their kiosks that scanned users faces, uploaded the biometric data to their servers, allowing casino customers to use their kiosks without swiping their membership cards.
This alarmed the researchers who quite rightly identified the facial scans as a serious privacy risk for the users, especially if the back end infrastructure was not properly secured, further compounding the existing security problems Atrient had.
They went along to ICE as registered attendees to try and meet with Atrient COO Jessie Gill who they had been talking to for the previous four months and Atrient CEO Sam Attisha in order to raise these concerns and look at them in the eye.
When one of the security researchers, Dylan Wheeler, approached COO Jessie Gill and introduced himself as the researcher who Jessie had been dealing with, Jessie suddenly lunged at the researcher and violently grabbed him by his clothes on his chest before then tearing his attendee badge away from him, telling the researcher that he didn't need it anymore and that he would keep hold of it.
This whole incident was witnessed by multiple people, including Atrient CEO Sam Attisha who said nothing throughout the whole incident. The researcher started to video the incident on his phone as soon as Jessie released him. You can see in the video below Jessie threatening the researcher with Scotland Yard before then denying that he knew him, when he knew exactly who the security researcher was.
We have partial video of the incident below and I have requested the CCTV video recordings of the exhibition hall from the ICE conference organizers. The security researcher has since reported the assault to the London Metropolitan Police who are working with conference organizers on this incident. Dan Stone the Head of Marketing for the ICE conference told me "we take the safety of all of our visitors to ICE extremely seriously. We have reported the matter to the on-site security team and they are looking into the incident and will liaise with the police as required".
A security researcher (@degenerateDaE) was just assaulted by a vendor (@atrient) for trying to introduce himself after being engaged with the vendor for three months after reporting a serious vulnerability that they have ignored. Police are involved, full story coming shortly! pic.twitter.com/jK42iqcXV1
— Secjuice (@Secjuice) February 5, 2019
The Aftermath
I have reached out to Atrient, calling COO Jessie Gill personally to invite him to comment on the unresolved security vulnerabilities at Atrient, his assault on the security researcher, or anything else he wanted to say but he hung up the phone on me.
I am reaching out to a number of Atrient customers (Caesars Entertainment and Hard Rock International) to see if they have been notified of this security vulnerability.
UPDATE - Legal Threats Possibly Issued
I received a strange email from Jessie Gill in response to publishing this story, I have pasted it below so you can see it. Am not entirely sure if they are naming me a co-conspirator, it looks like it was CC'd and not really addressed to me directly.
The email is not actually addressed to either of the security researchers and does not name them, the source of this text is unclear but it appears to have been cut and pasted from somewhere and had the customary 'Dear John' part excluded.
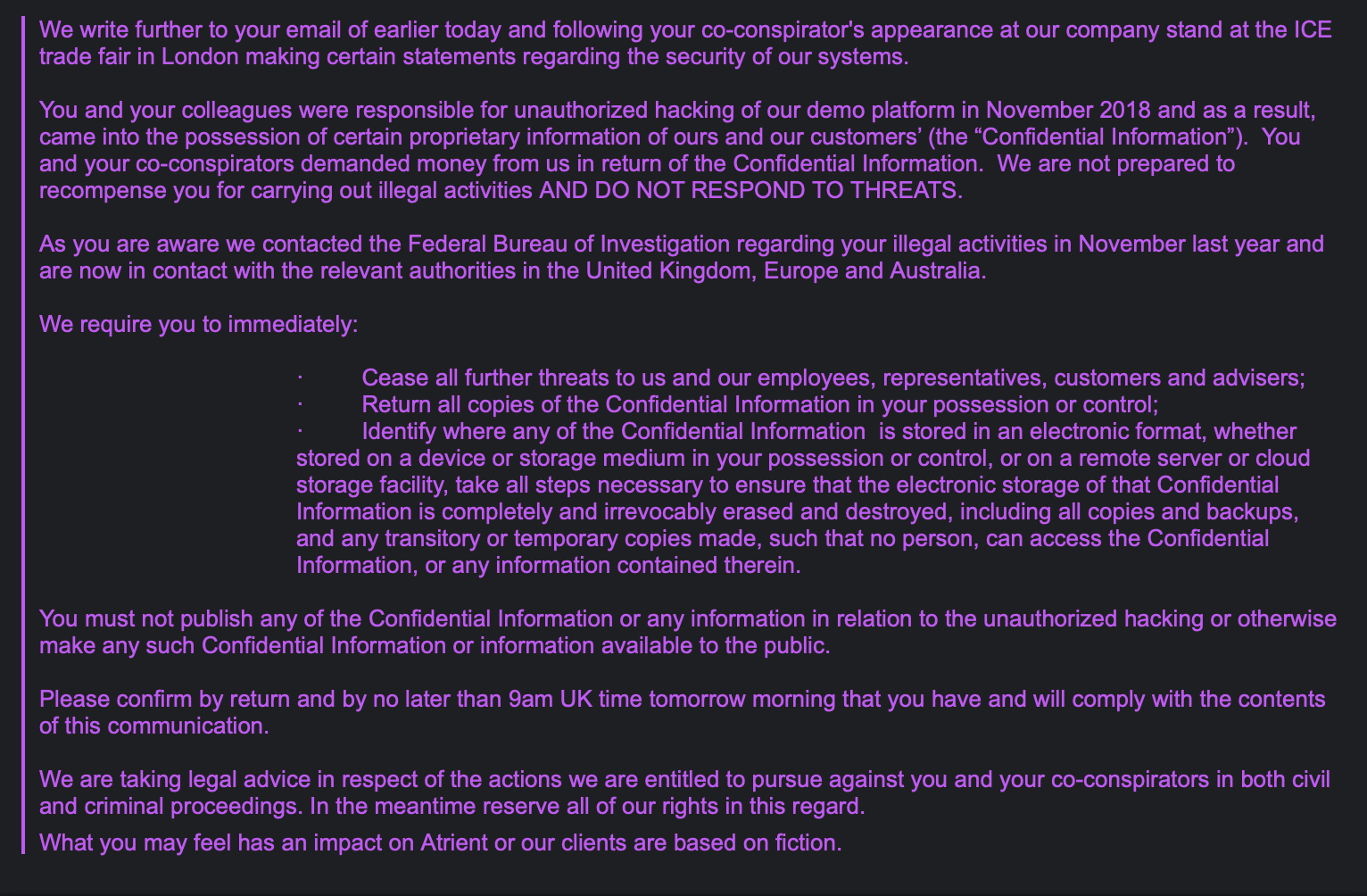
Now this has been exposed to the cold hard light of day they seem to have knee jerked out a blustery legal threat. Rest assured dear reader, your writer was nowhere near any of this technically, I recorded the story as it unfolded and truthfully told it.
The security researchers tell me that they have recorded every conversation and kept an accurate timeline of events pegged to specific communications. You can stand on my word when I tell you there are no bad actors at Secjuice and that the security researchers acted in good faith throughout the last few months.
Neither Secjuice nor the security researchers have received a formal legal notice from anyone who looks like a legal representative of Atrient or a lawyer.
UPDATE - Atrient Issued A Statement and Quickly Withdrew It
Following the furor on social media, Atrient tweeted out a statement that they have since deleted when new evidence in this article came to light contradicting their claims, journalist Dan Goodin asked them why they deleted their statement.
Their statement was online until this article from Ed Targett of CBR Online was published containing audio recordings of the calls with the FBI and Atrient which contradicted the claims made by Atrient in their statement. Below is a screenshot of the statement that Atrient deleted shortly after posting them on Twitter.
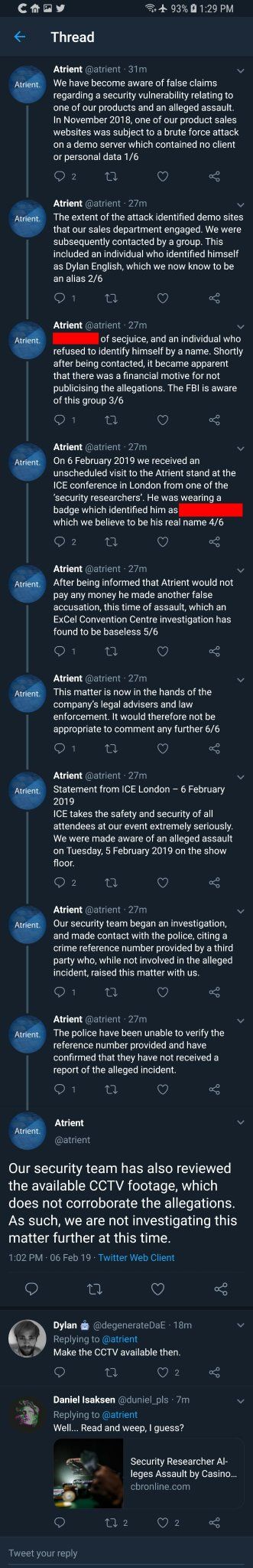
Atrient deleted the tweets after the CBR Online article and its recordings of the conversations contradicted their claims in four ways. The first Atrient claim to be contradicted was their initial claim about a brute force attack on a demo server, it is clear from the conversation recordings with the FBI and researchers that this was false and that they were very aware of the extent of the security vulnerability.
The second Atrient claim to be contradicted was their claim that they FBI were aware of the group, although I think perhaps that they were being deliberately misleading with their words rather than untruthful. The FBI are indeed aware of the group, primarily because, as the recorded conversations show, the FBI and the security researchers had engaged with each other before Atrient spoke to them.
The third Atrient claim to be contradicted was their claim that the police had been unable to verify the incident and confirmed that they had not received a report of the incident. This claim proved to be false when a Metropolitan Police spokesman said by email to journalist Ed Targett: “[We] can confirm that police received a telephone report of an altercation at Excel, Western Gateway, Newham, where a 23-year-old male was allegedly assaulted by a second male who took the victim’s event lanyard. No injuries. No arrests. Officers from Newham Police investigate. Enquiries continue.”
The fourth and final Atrient claim to be contradicted was that they had reviewed the CCTV footage and deemed that it does not corroborate the allegations. I have written to the ICE team for clarification on this CCTV footage because it is unknown if this footage even exists and if they have indeed provided this footage to Atrient.
I have been told by other journalists that ICE has told them that there was no CCTV footage of the part of the exhibition hall where the Atrient stand was located, in order to confirm that this is true I have asked a few people to head down to the conference and scout out the CCTV field of vision in that area and will report back on that. Undoubtedly footage of the incident is hugely important to this story, the original video footage recorded by Dylan Wheeler does not begin until after the alleged assault, so ICE releasing the footage would be helpful in establishing the truth.
I asked security researcher Dylan Wheeler to comment on the claims made by Atrient in their now deleted tweets and he replied "I'm unable to comment on their deleted statement posted on Twitter at this time, as we are openly engaged with our legal team regarding this incident." The security researchers involved in this incident are working with lawyers on the potentially libelous claims Atrient has made and deleted.
It is worth noting that despite the strange legal notice Jessie sent to Secjuice and the researchers by email (which did not address or name anyone specifically) and the bizarre claims Atrient made in their twitter statement, neither Secjuice nor the researchers have seen any official legal communication from Atrient's legal team.
I have been using a remote browser to research this story. If the endpoint is the new perimeter, then remote browser isolation is the future of endpoint security.
UPDATE - Original Call Recordings
Below are the original call recordings taken from this CBR Online article of the initial call myself and the security researchers had with the FBI and the second call that the FBI set up the next day for the researchers to talk to Atrient.
Call 1: https://dayafterexploit.com/Skype1.mp4
Call 2: https://dayafterexploit.com/Skype2.mp4
I did not originally publish these call recordings to protect the privacy of those involved in the conversations, but when it became clear that Atrient were doubling down on their efforts to condemn the researchers and CBR published them first it became a moot point and so I have included them here in article for your convenience.
I will keep you updated as this story progresses and update this article with any news.


