My First Foray Into Software Reverse Engineering
Security researcher Alessandro Innocenzi is dipping his toe into reverse engineering, join him on his journey and find our what he learned.

I’m beginner to software reverse engineering, so this article isn’t for experts. I’ll be describing my personal approach to starting in this field. Feel free to comment with your own approach, tools, tips and tricks to make it stronger!
Reverse engineering is really cool. This is what I think about it after one week on reversing challenges of HackTheBox (link is only for registered users on that platform).
A Simple Newbie Story
I wanted to start with reverse engineering challenges on HackTheBox, so I’ve downloaded the first executable file to reverse and…
Ok, now? I have absolutely no idea what to do. Really.
So I thought: I know that I know nothing (Socrate docet).
Starting from this assumption, I looked for some courses about reverse engineering. I found and completed Security for Hackers and Developers, an interesting PluralSight path to reverse engineering malware, that introduced me to various methodologies and tools.
Although knowing Assembly wasn’t a necessary prerequisite, in the middle of the course I realized that it would be better to know it. So I looked for some guides or tutorials for beginners.
I read several forums and Q&A, such as Reverse Engineering on Reddit or Reverse Engineering Stack Exchange. I found a crash course in x86 Assembly to give me a general idea, then I found Reverse Engineering for Beginners from Dennis Yurichev, a very impressive free ebook about reverse engineering. Check it out!
I also followed tutorials on how to reverse some famous programs to remove protections. Obviously only for study purposes.
Remember that cracking is illegal in most countries.
Cybersecurity guys use reverse engineering mainly to study malware to find a patch or to block them.
Anyway, I learned the initial steps to take and some simple techniques.
Some Steps Towards The Goal
First of all, check what type of file you’re working on to figure out how to continue. On Linux, you can use file command or binwalk. On Windows, there is Detect It Easy (also available for Mac OS X and Linux).
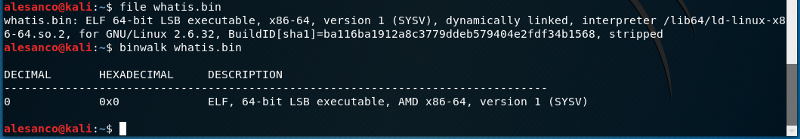 file command and binwalk outputs.
file command and binwalk outputs.
When you know the type, you can decide what to do.
For example, you can try to decompile a .NET file with dotPeek, a JAVA file with Bytecode Viewer, a FLASH file with JPEXS Decompiler, and so on. When you have the code and you can run it in debugging, everything is easier.
But what if you cannot? In some cases the code generated by decompilers isn’t very clear (for example sometimes with snowman) or doesn’t work at all.
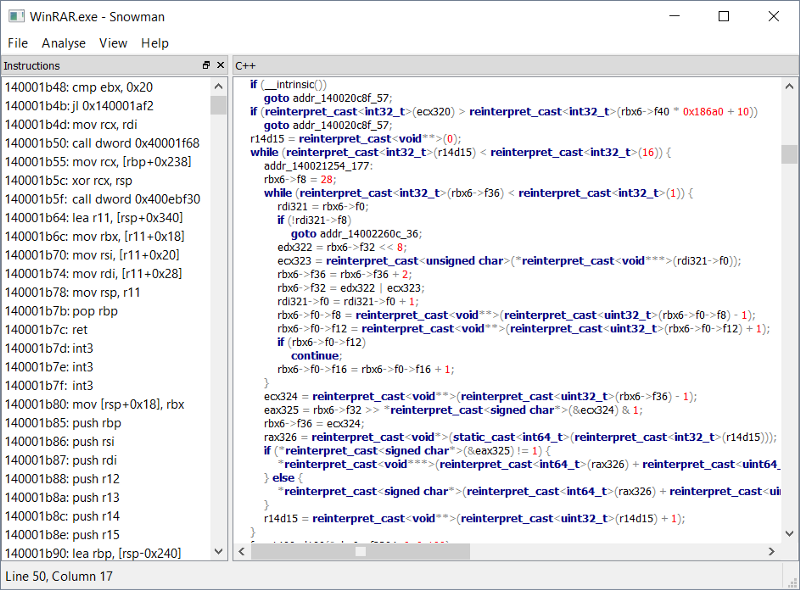 An example of decompilation with snowman.
An example of decompilation with snowman.
I understood that disassemblers (especially those with the debugging function) are the best friends of a reverse engineer.
In the HackTheBox challenges, I found myself comfortable with objdump and edb-debugger, while on Windows I use x64dbg.
Obviously there are many other disassemblers, more or less famous, including also Immunity Debugger, OllyDbg, WinDbg, Radare2, and so on… But the most famous in the world is undoubtedly IDA Pro. It’s expensive but if you want to work in this field, it’s worth it.
Anyway, after studying all these things, at one point I thought I was ready.
 Neo also thought he was ready.
Neo also thought he was ready.
Time To Prove It (And Improve Me)
Ok, after all my goal was to start HackTheBox challenges.
I reopened the downloaded executable file to reverse and I knew very well what to do… almost.
In one week I solved the first four challenges in my spare time! Ok, I know these challenges are very easy, but I’m really happy to have them solved, especially because I started this adventure three weeks ago without having an idea to what to do at all!
 Ok, these challenges are very easy in general, but in this moment, I feel like a boss.
Ok, these challenges are very easy in general, but in this moment, I feel like a boss.
Working on these challenges I’m learning more about software reverse engineering, of course, and I know I’ve a lot more to learn in this field, like reversing on encrypted and obfuscated codes, bypassing anti-debugging protections, and much more!
But, as I said, reverse engineering is really cool! Try it!
Here a huge list of reverse engineering resources. Happy crackin… oh, no, wait: happy reversing!
