TryHackMe: KaffeeSec - SoMeSINT
TryHackMe's KaffeeSec SoMeSINT box teaches you how to gather social media intelligence on your targets.

Social media intelligence plays a vital role during investigations. We are all connected via different social media applications and forums one way or another. The digital footprint of a target that is left on the internet can lead to uncovering interesting facts and information which helps in active intelligence gathering, analysis, and forensics.
To better understand the concept of Social Media Intelligence/Investigation and how it works let’s try to solve a case presented in this awesome room "KaffeeSec - SoMeSINT" by Hothotcoffee on tryhackme.
Objectives
- Investigate and analyze the person of interest to uncover facts and information.
- Learn to use OSINT tools and techniques such as Google Dorking, website archiving, social media information gathering/enumeration & Analysis.
- Apply the skills that you have learned throughout this write-up while attempting CTFs and while addressing real-world investigations related to social media.
Scope
The scope of this case revolves around two social media account/forum. Considering this limitation, we will have to narrow down our investigation.
Lets Get Started
The room contains series of challenges that have to be solved using various open-source tools and techniques related to Social Media Investigations.
Our Challenge Case
You are Aleks Juulut, a private eye based out of Greenland. You don't usually work digitally, but have recently discovered OSINT techniques to make that aspect of your job much easier. You were recently hired by a mysterious person under the moniker "H" to investigate a suspected cheater, named Thomas Straussman. After a brief phone-call with his wife, Francesca Hodgerint, you've learned that he's been acting suspicious lately, but she isn't sure exactly what he could be doing wrong. She wants you to investigate him and report back anything you find. Unfortunately, you're out of the country on a family emergency and cannot get back to Greenland to meet the deadline of the investigation, so you're going to have to do all of it digitally.
Now that we exactly know, who is our suspect? Who has hired us to investigate? What the suspect is being investigated for? Let’s try to solve the challenge questions below.
Challenge Task 1 :
Who hired you and Who are you investigating?
It is evident from the case stated above that we have been hired by a mysterious person known by a nickname. The person who has hired us has stated the name of the person who has to be investigated.
Challenge Task 2 :
During the initial investigation, we found that our target goes by the name of “tstraussman" on two different social media platforms which are going to be revealed soon.
The initial investigation kicks in using enumeration of social media accounts that lead to uncovering various links between the target and its connections. Let’s see what we can find about our suspect over the internet. A simple Google search will do the thing.
P.S: Limit your investigation circle around the two social media accounts of our suspect.
Looks like we have found some information.
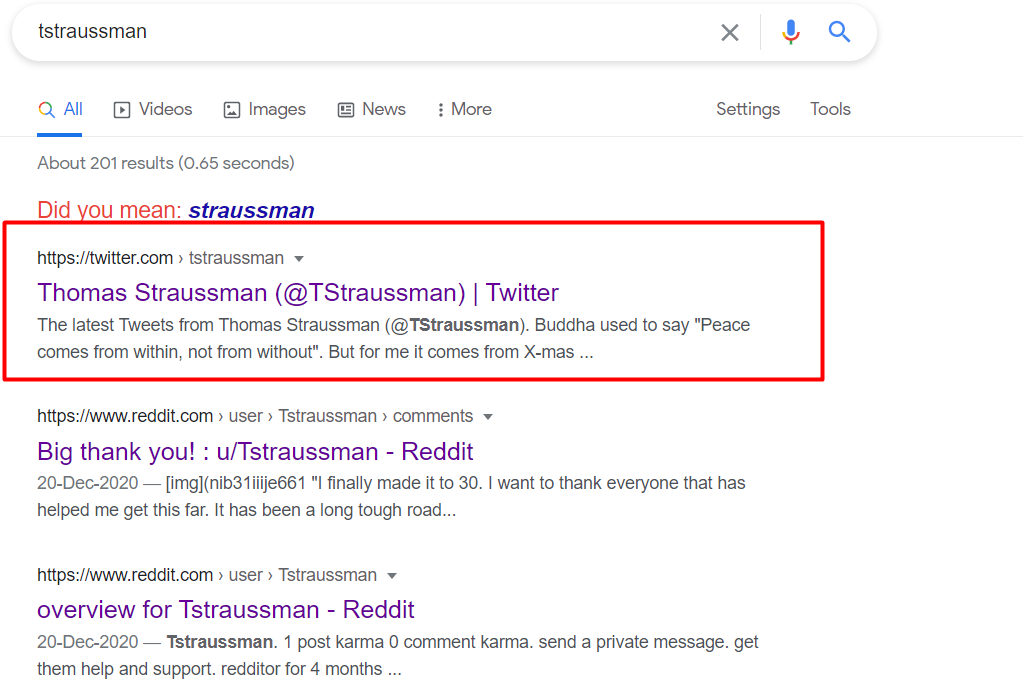
Let’s try to answer the following questions
What is Thomas's favorite holiday?
After checking our suspect Twitter account, the target has not explicitly tweeted about his favorite holiday, but if we look a little closer towards his bio we find the answer i.e. "Ch****as"
What is Thomas's birth date? (Format is MM-DD-YYYY)
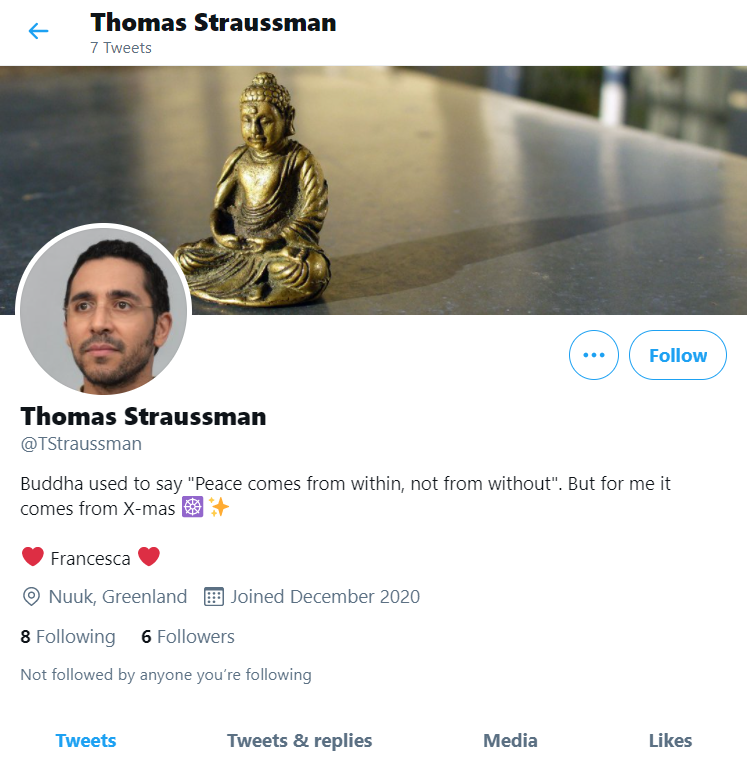
We don’t find any birth date of our suspect on his Twitter bio, but remember we found one more link to a social media forum "Reddit".
We find our suspect cake day on his Reddit profile. A little math and we have the suspect birthday i.e. 1*-2*-1***
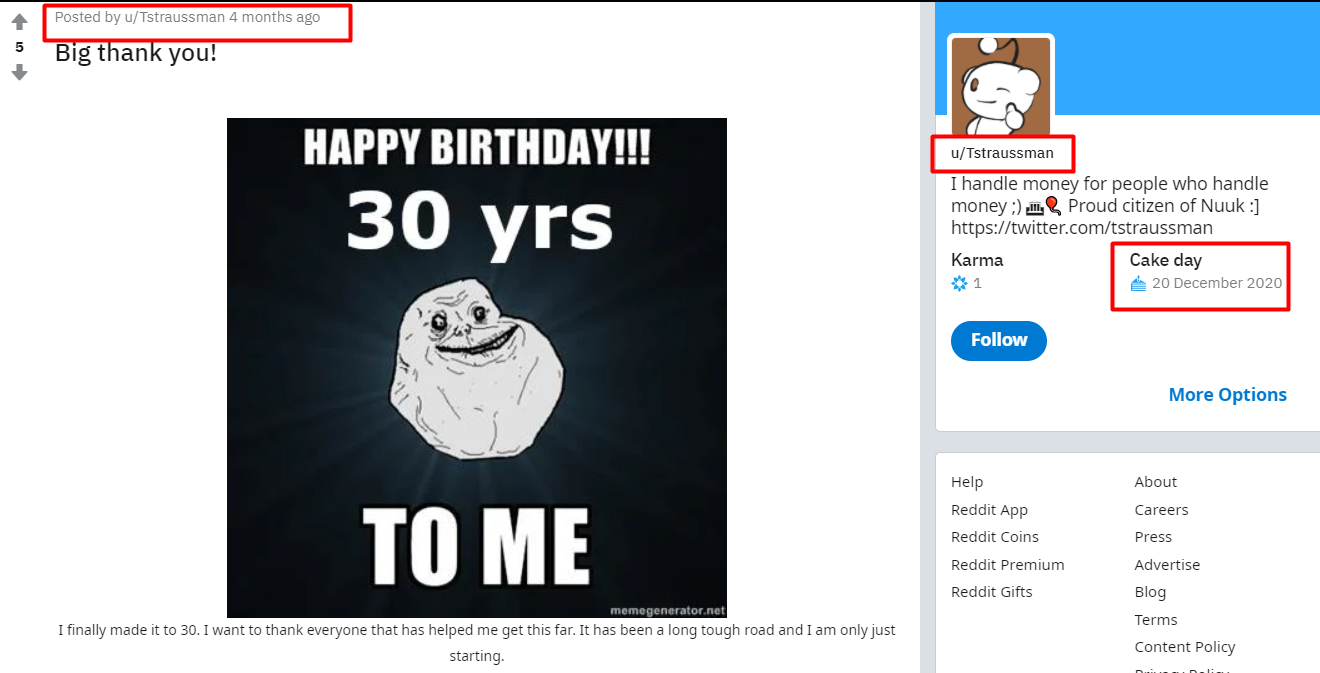
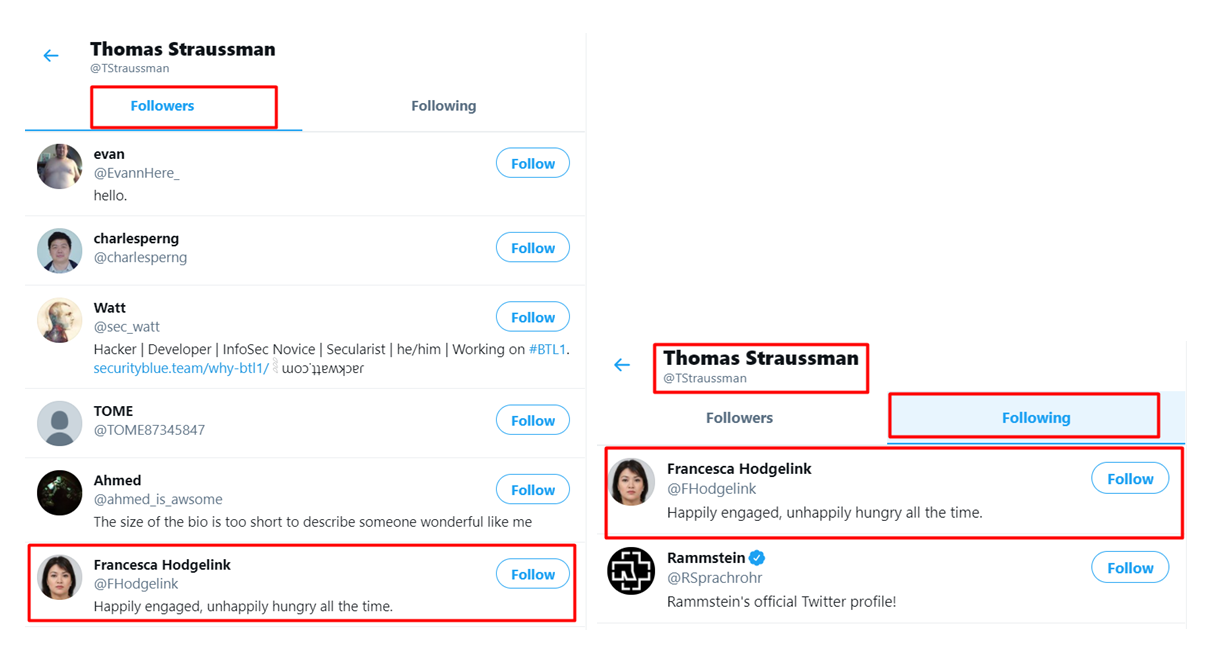
What is Thomas' fiancée’s Twitter handle?
Looking at the followers of our suspect, we find only one female named "Francesca Hodgelink" who follows our suspect Thomas and he too follows back. The status in bio also confirms that the lady is Thomas's fiancée’s whose Twitter handle is @*Ho*g*l*n*.
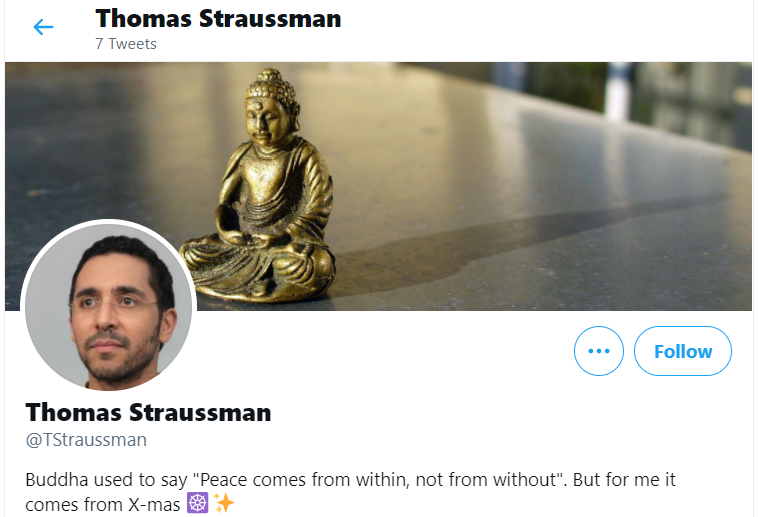
What is Thomas' background picture of?
Well the Bio of our suspect says it all !! (*u**h*)
Challenge Task 3
We were able to obtain the information of our suspect by simply using a Google search. Another approach of investigation is the use of an awesome open-source tool known as spider foot that collects information from various publicly available data sources.
You can use spider foot on different Operating systems. A detailed guide to set up this tool can be found here. Make sure you follow the guide completely and install the latest version of Python on your desired operating system.
Once properly installed, you can access spider foot using "localhost: 5001" from your browser.
Initiate a new scan and search for our suspect username "TStraussman" or "Thomas Straussman". Make sure to select "By Use Case" and check the radio button that says "All" and initiate the scan.
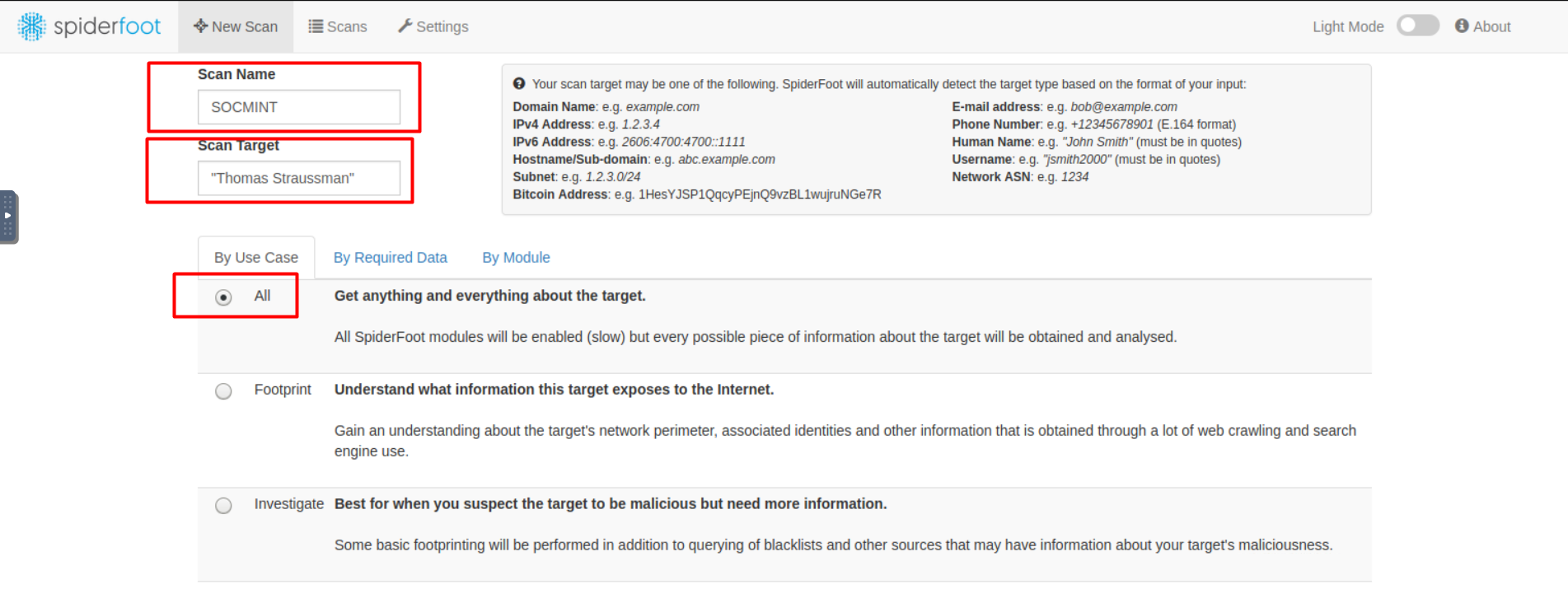
Note that our investigation scope is limited to the suspect accounts that are on Twitter & Reddit, anything other than these will be flagged as false positives.
We see the following spider foot results once the scan ends.
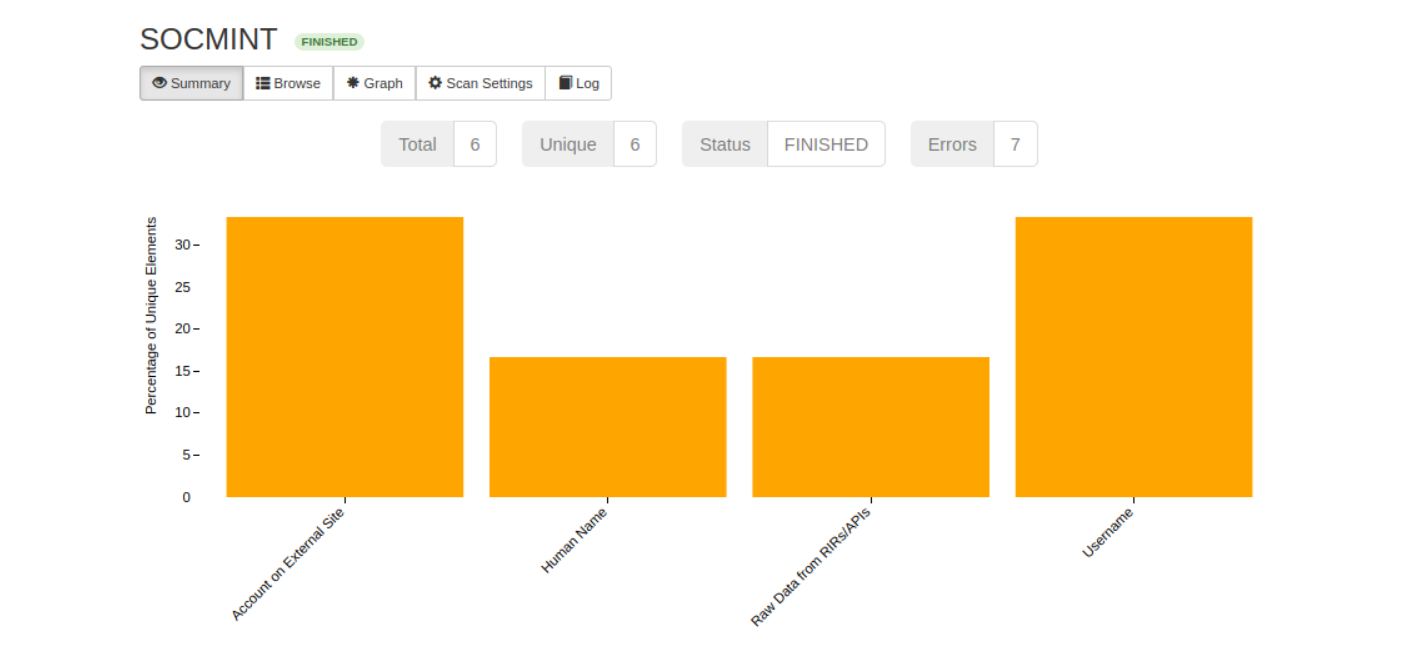
Clicking on the "Account on External Site" will display our desired results.
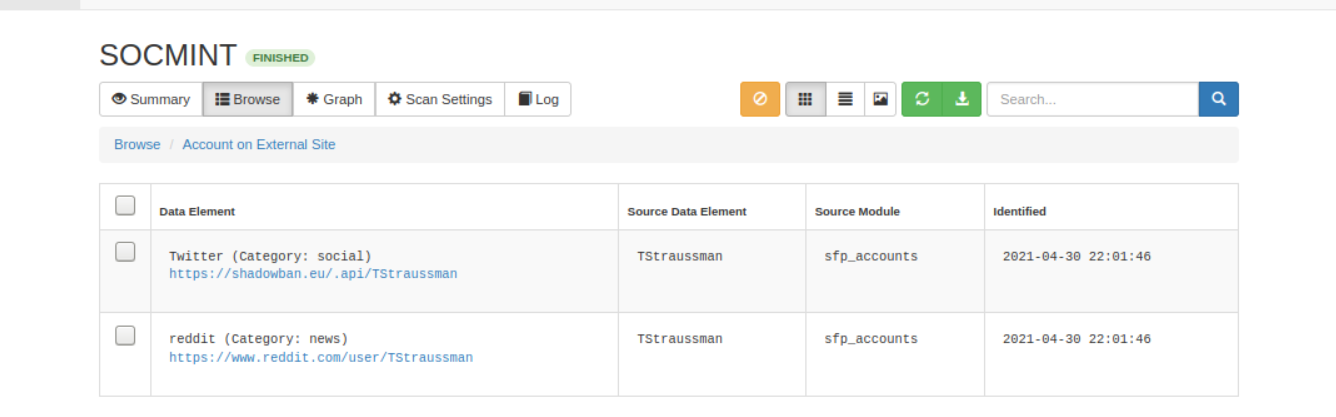
You can explore the tool on your own to know what other features this tool offer. Let’s get back to answering the questions associated with this challenge.
What was the source module used to find these accounts?
From the picture displayed before we can figure out which modules were used to find the target accounts. (s**_a**on**)
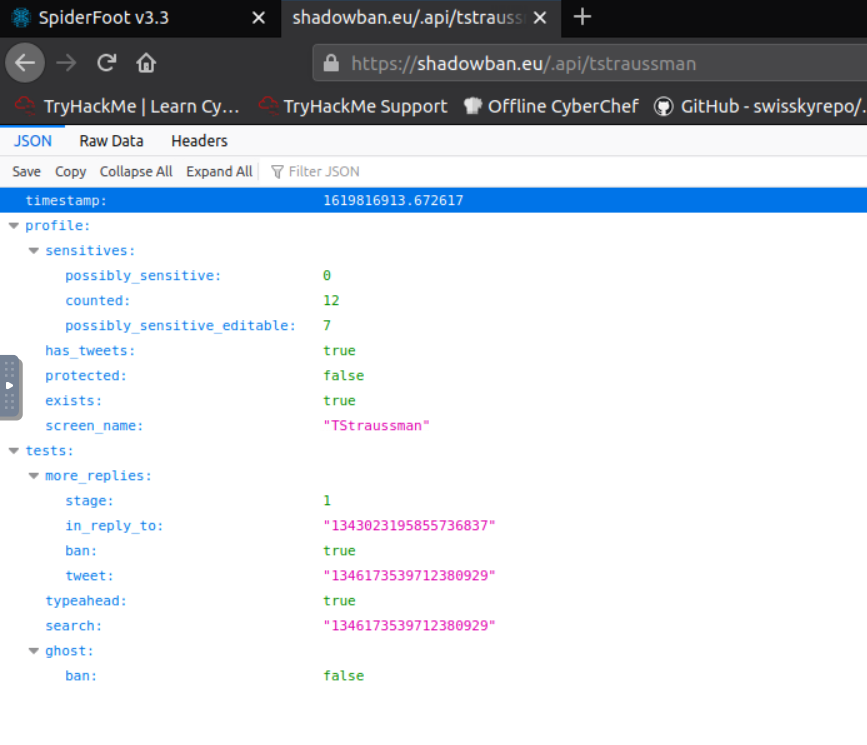
Check the shadowban API. What is the value of "search"?
Click on the first link of the Data Element i.e. https://shadowban.eu/.api/tstraussman. Explore the fields and you are going to find the value of search within. (1****17****71****929)
Challenge Task 4
As we have obtained enough information from our suspect account, it’s time that we pivot to his fiancée’s account. See what more can we find about her.
Before we dive into answering the questions associated with this challenging task, note some important and key information we could get from social accounts
- Names of places, landmarks, monuments, signs for investigation and analysis.
- Target pictures, Date of birth, the place they live, favorite sport, animal, restaurant, etc.
- Places they have visited, their whereabouts, their habits
Closely linking all the things found using social media accounts related to suspects can make an investigation very strong and impactful.
Let’s install a very useful tool known as the "RevEye" extension which is normally used for reverse image lookups across various search engines with just one click.
Where did Thomas and her fiancee vacation to? (Format is: City, Country)
Navigate to the suspect fiancée account i.e. "Francesca Hodgelink". We find a tweet as seen below
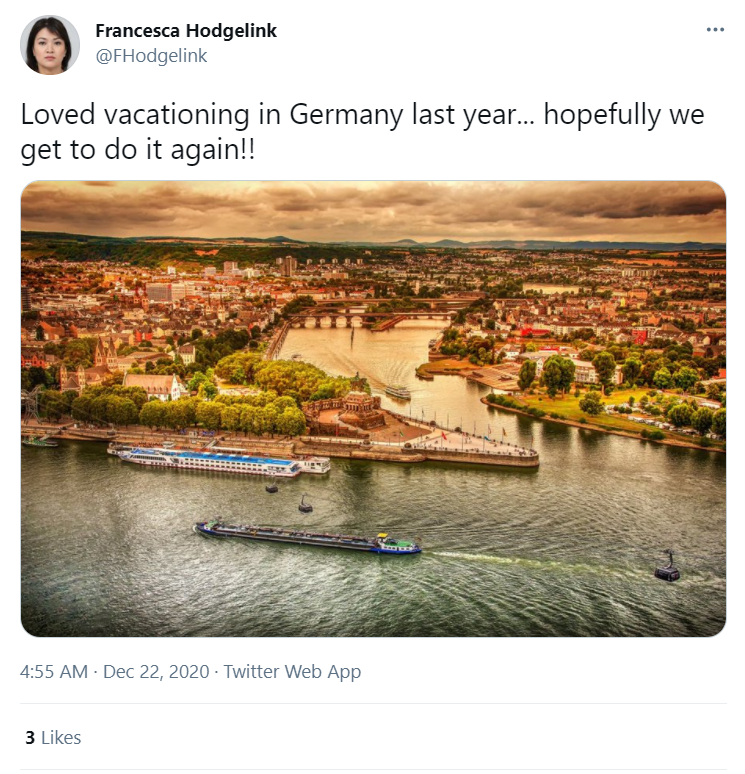
So we know the country name, but don’t know the city of the vacation yet. There are two ways to find out that. We can use the "RevEye" tool for a reverse image lookup as seen below.
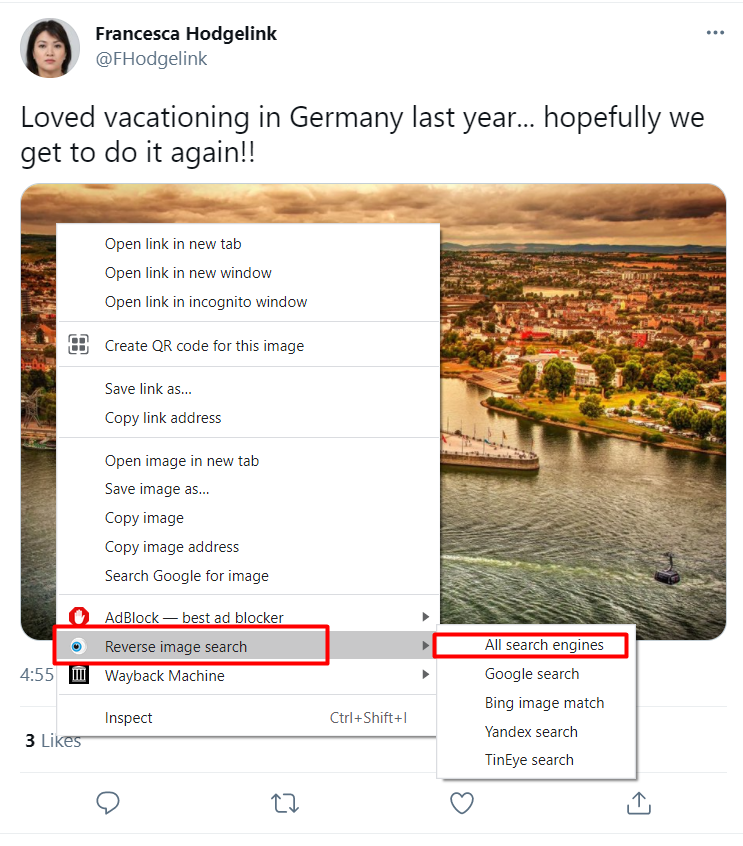
Out of many search engine options you can choose any of the listed options as seen in the previous image. There are almost 85 results against the image that we searched for.
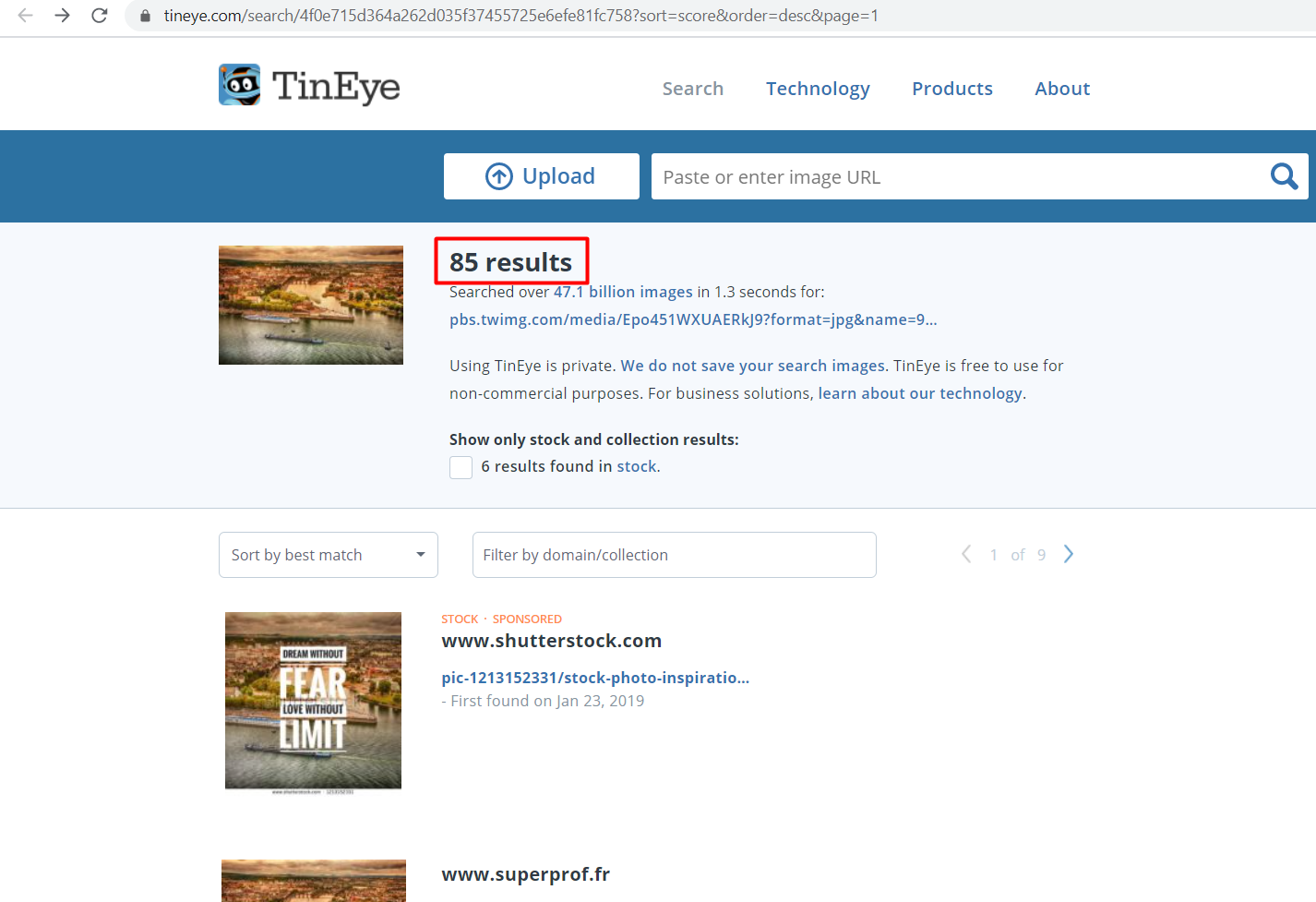
Scrolling through the results we find the exact match of our image and the city name.

There is another way through which we can obtain the required information i.e. by inspecting the source of the image in the tweet.
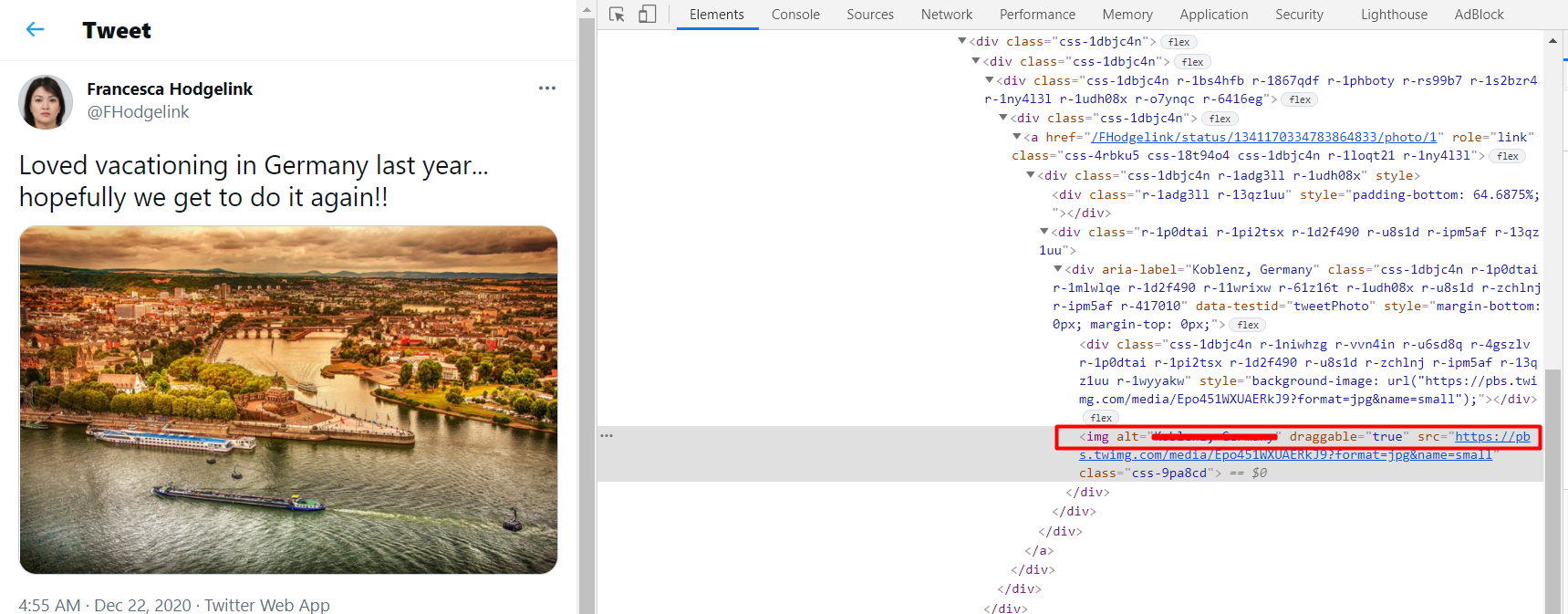
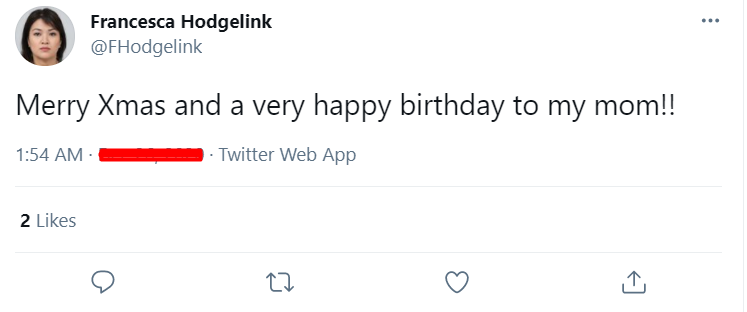
When is Francesca's Mother's birthday? (without the year)
Looking into the tweets of Francesca we find her mom's birthday.
What is the name of their cat?
Explore the tweets and you will know the name of the cat

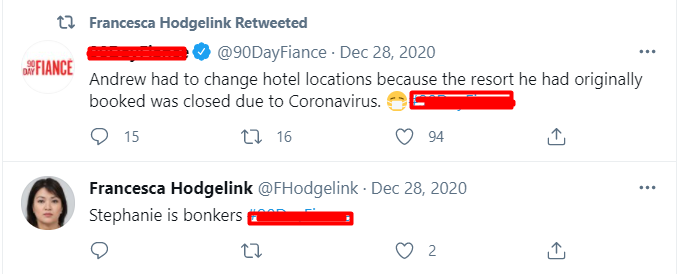
What show does Francesca like to watch?
Looking through her tweets we find two tweets regarding a popular show.
Challenge Task 5
Till now we have majorly focused on Twitter for our investigation. Let’s switch to another social media platform "Reddit". To further analyze our suspect we are going to use another tool known as "The Wayback Machine" also known as the web archive.
This tool allows us to see the web pages at different points of time since the website came online on the internet. Using this we can uncover much interesting information that once existed on the website. Install the web extension for the Wayback machine for quickly navigating to our target website web archive.
For the sake of this challenge we are going to analyze two versions of the Reddit platform i.e.
- Old version (http://old.reddit.com/)
- New version (https://www.reddit.com/)
What is the name of Thomas' coworker?
Looking at our suspect Reddit profile we don’t find any information related to a co-worker, but that does not mean the information does not exist. Let’s navigate to the old version of Reddit i.e. http://old.reddit.com/ using the Wayback machine extension.
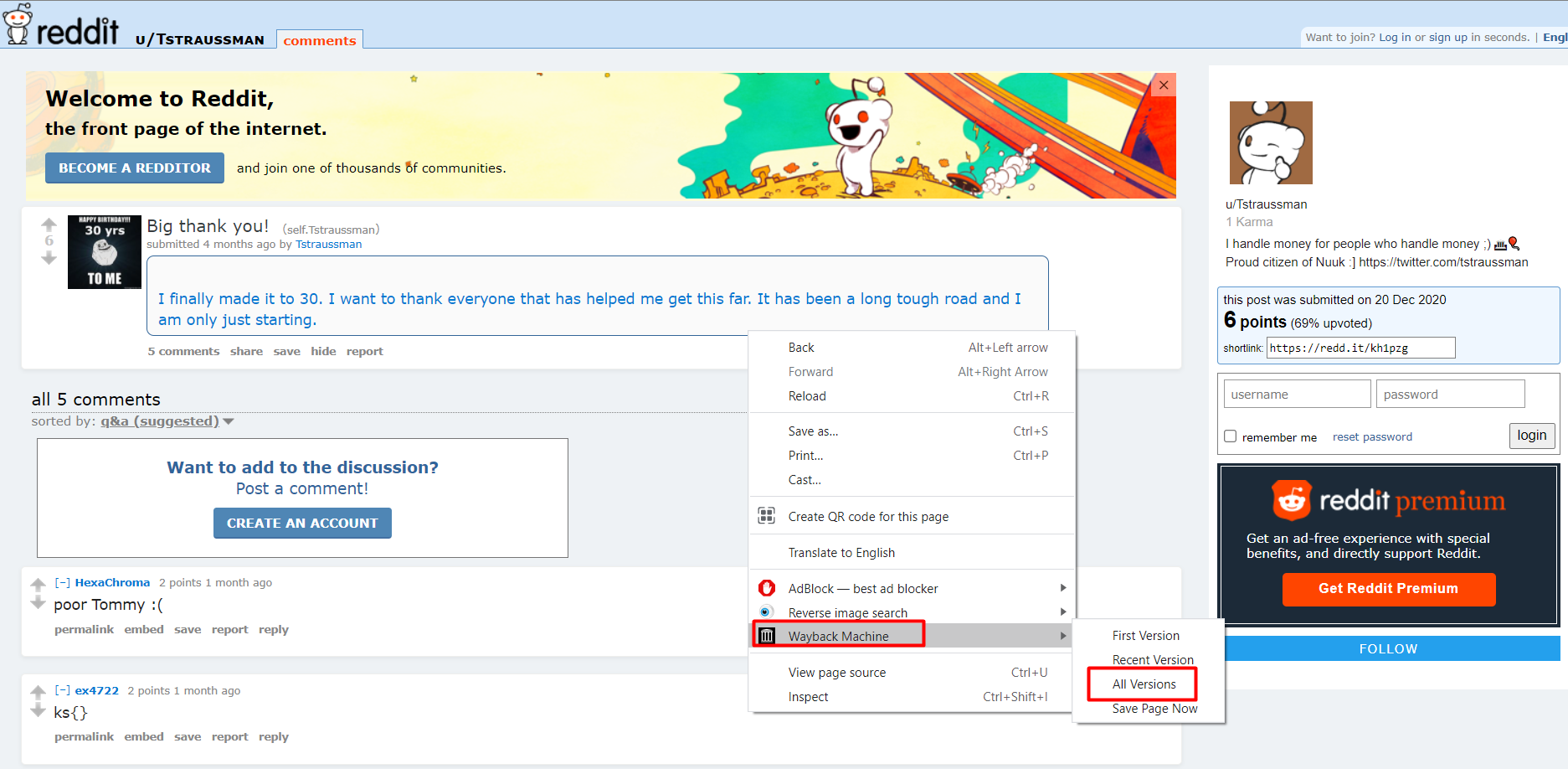
Looking at the web archive of our suspect post on an older version of Reddit we come to know that there has been activity on the post. Exploring the times at which there was an activity we uncover the name of the coworker of our suspect
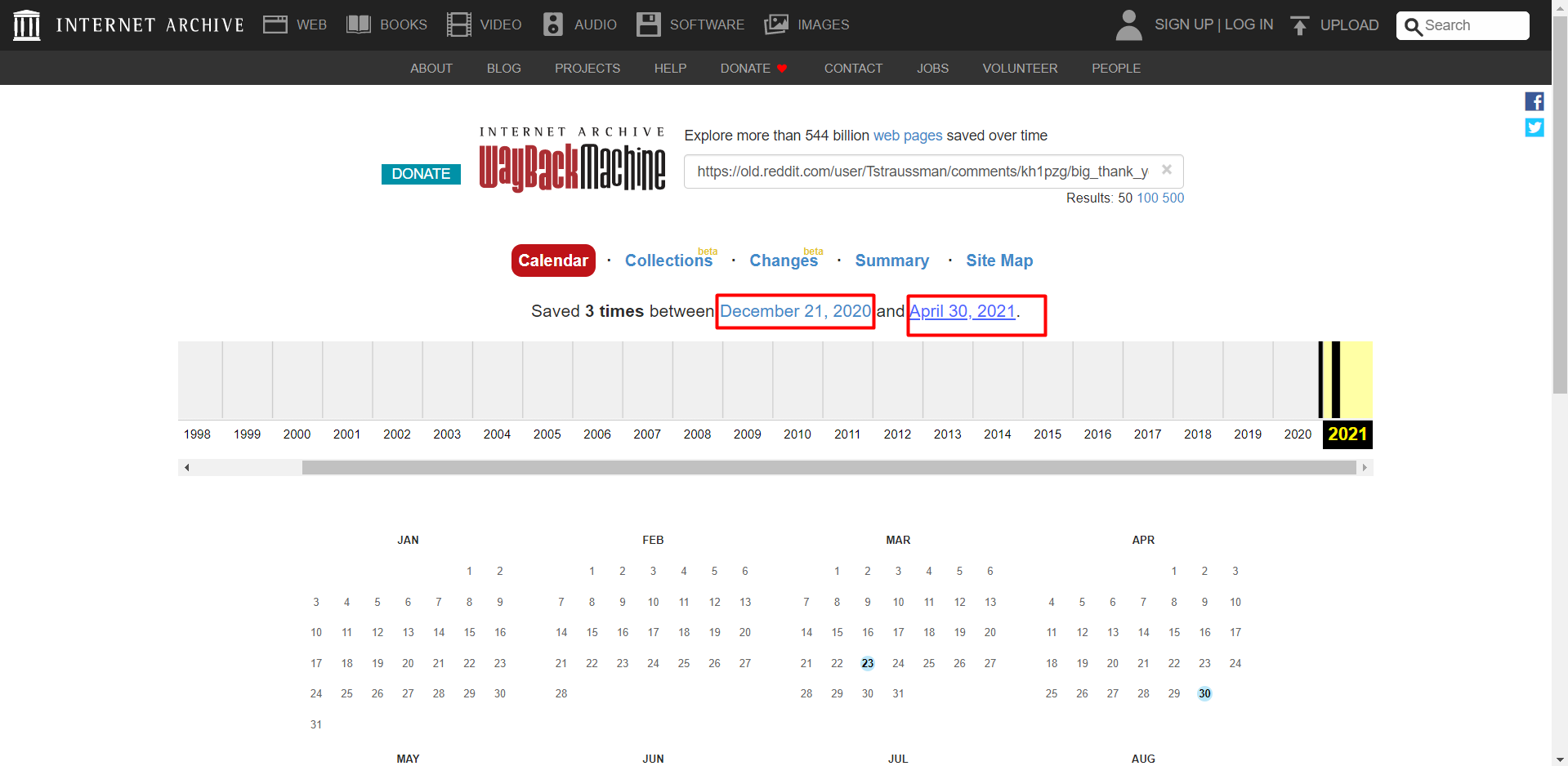
Where does his coworker live? (Format: City, Country)
Let’s dig into the coworker profile for extracting more intelligence. Looking at his profile and using some common sense we now know where he lives.
What is the paste ID for the link we found?
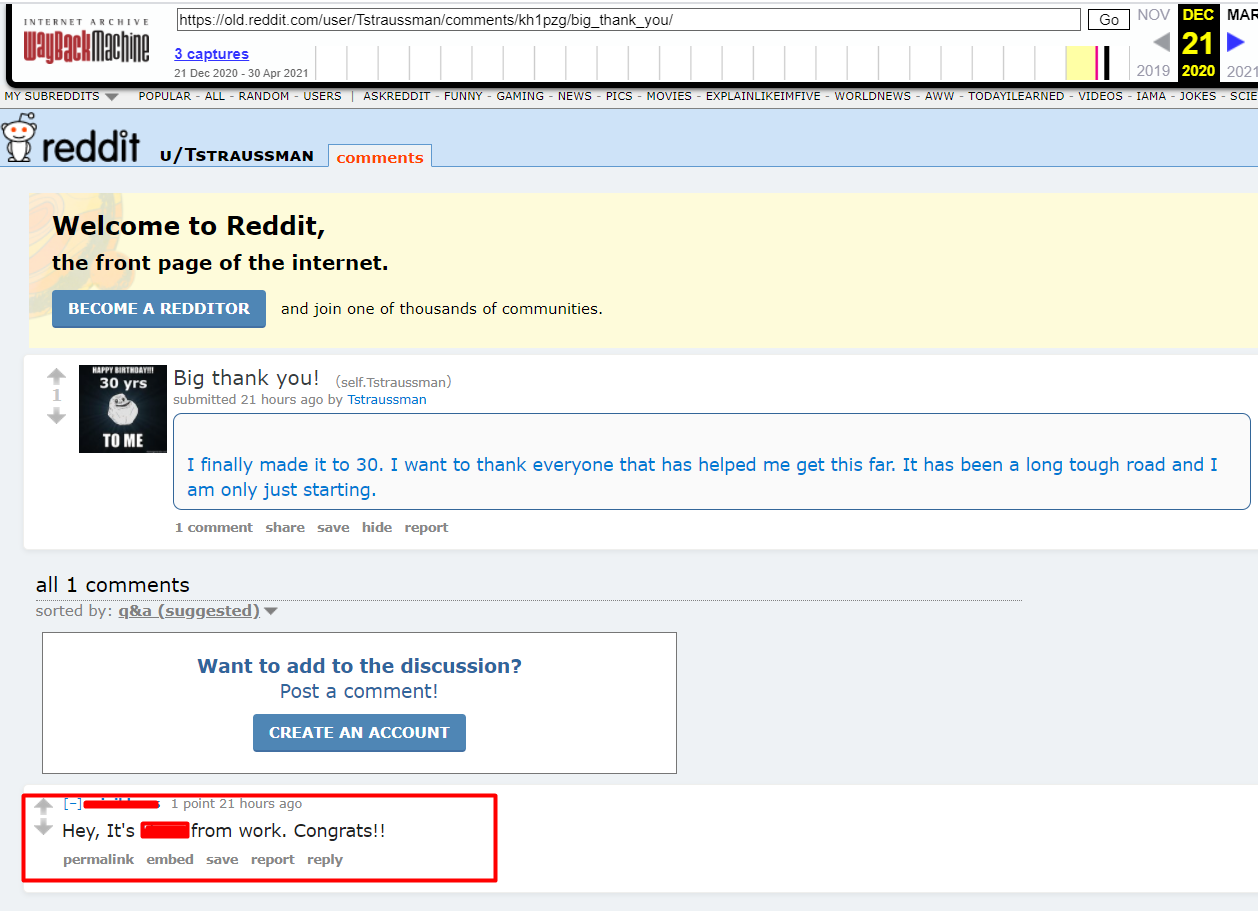
Use the Wayback machine for the coworker profile on Reddit. Looking up all the archives we found another post named "Disappointed 2 Electric Boogaloo"
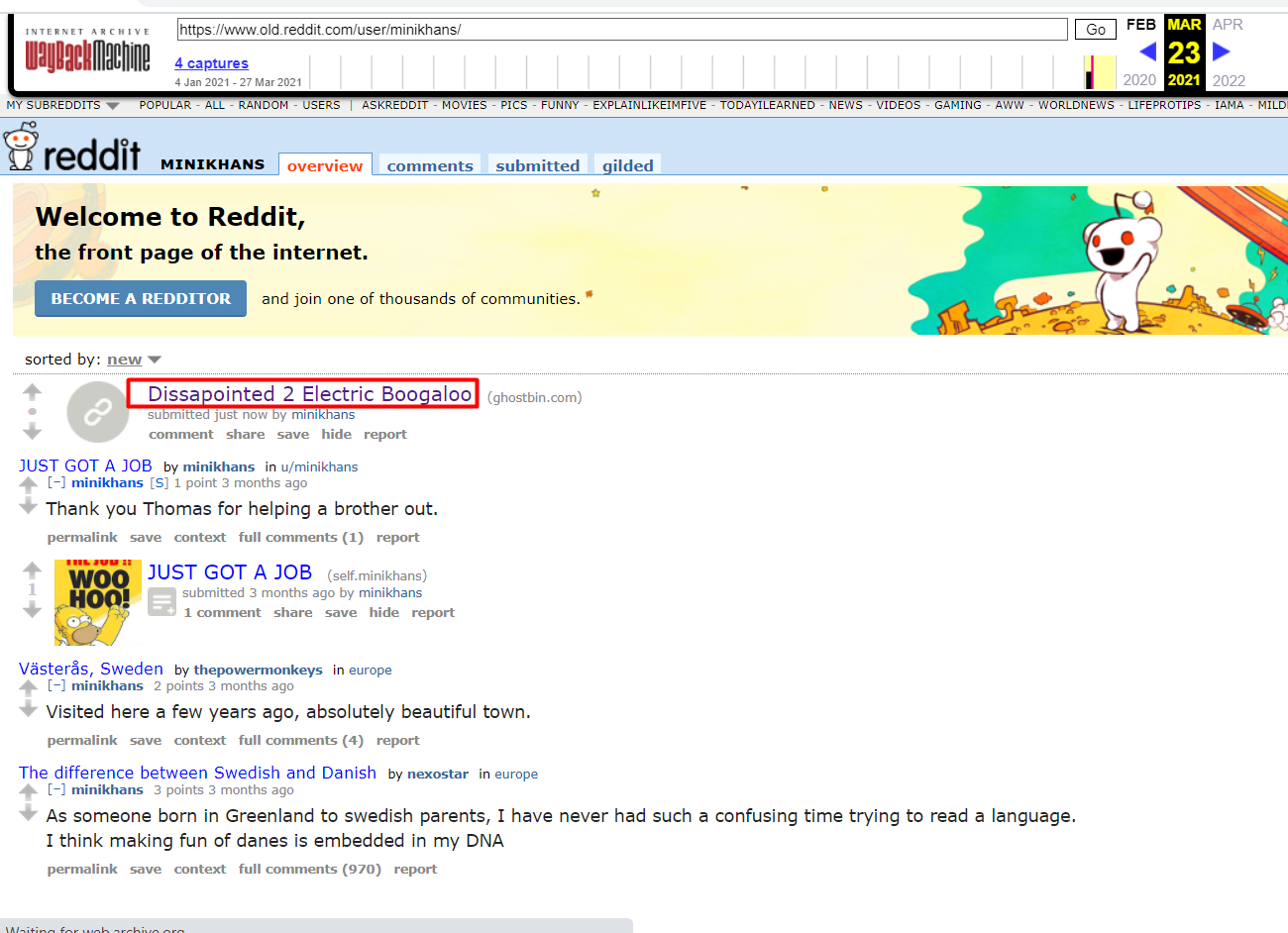
Navigating to this post we find something very interesting. Looks like the coworker has found a secret of our suspect. Well, things are getting really bad for our suspect!!
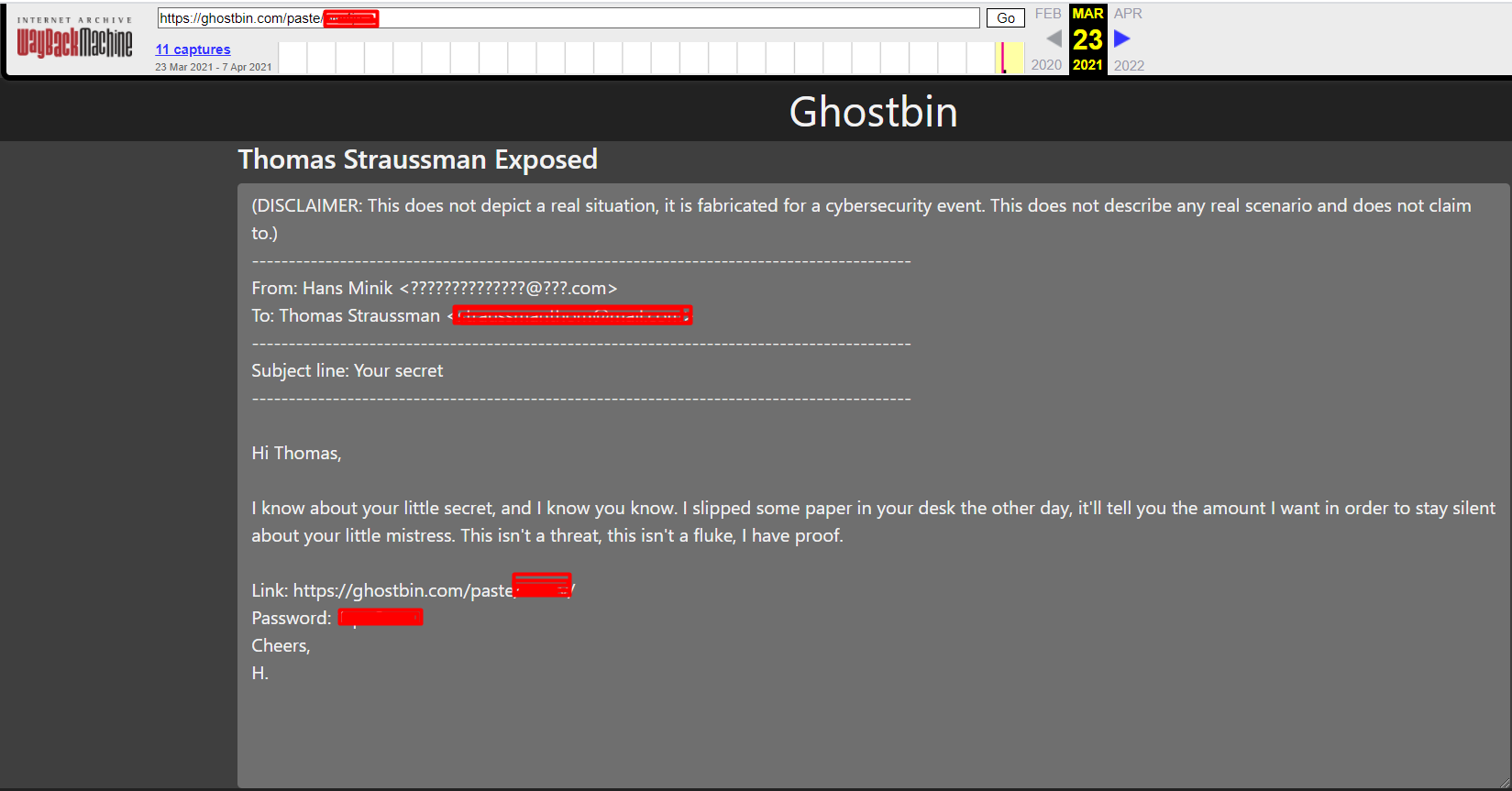
The paste bin ID can be found in the URL. While the password is in the content of the email as seen in the previous image.
The answers to the next questions lie in the ghostbin link that was provided by Hans in the email.
- What is the name of Thomas's mistress?
- What is Thomas' Email address?
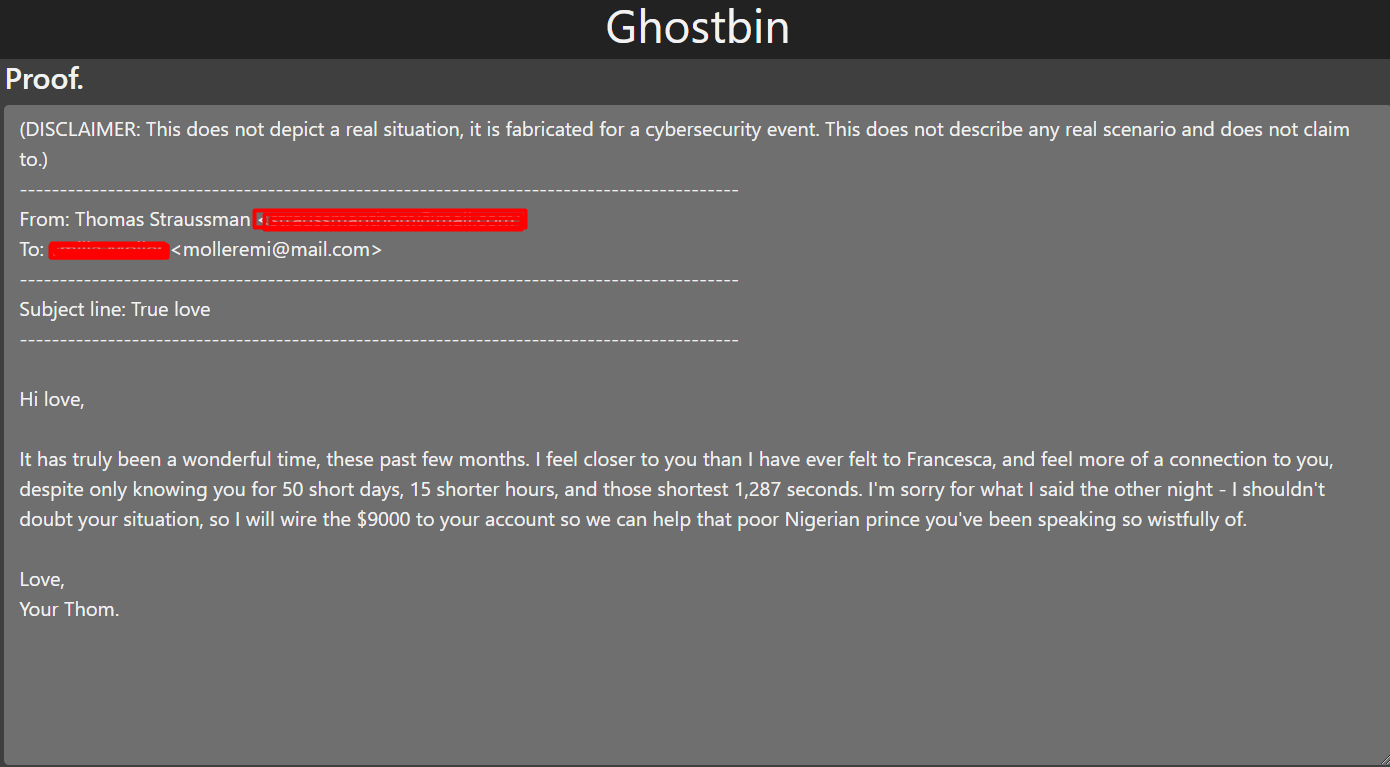
Looking at the email above, now we know why Thomas was acting suspiciously as communicated by her wife.
This concludes our challenge questions.
Secondly, we do notice that both Thomas and her mistress are both being scammed or her mistress is involved in the scam. The content of the email shows that our suspect is ready to transfer the amount to his mistress to help the Nigerian prince.
The Nigerian prince thing is a very well-known scam of impersonation where a wealthy Nigerian prince sends an email to a victim stating that a large amount of money is to be brought out of their country and your assistance is required to do that. In return, you are going to receive a sizeable share out of it once you help.
Detailed information about this scam can be found here.
Conclusion
After completing this challenge room, we now know how the SOCINT investigation is carried out. How social media can help us extract vital information which can be used for investigation and intelligence gathering purposes against a target/suspect. Extracting information from publically available resources requires an analytical approach, using the right tools and mindset you can achieve your desired results in a very effective and efficient manner.
I hope you liked the write-up, more write-ups related to OSINT can be found below


