Windows Forensics: Artifacts (2)
We continue our digital forensics journey with Windows artifacts, so let's jump right in and continue to look for artifacts in Windows!

In this article we continue our digital forensics journey with Windows artifacts, so let's jump right in and continue to look for artifacts in Windows! If you have not already read it, the first part of my guide can be found here, so do take a look before proceeding.
The Registry
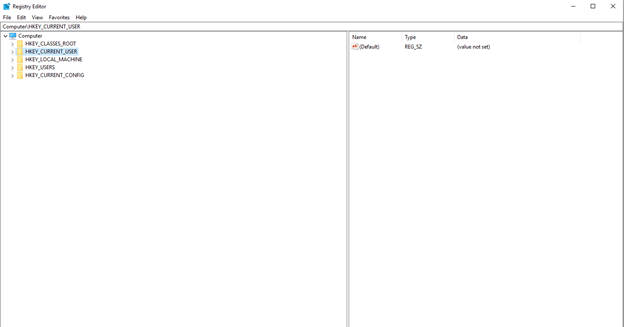
This is one of the most important artifacts in a Windows system because it functions as a database that stores various system configurations every second. The registry has a main structure called hive and you can see it in the Registry Editor:
- HKEY_USERS: Store user profiles that have logged on the system.
- HKEY_CURRENT_USER: Saves the user profile that is currently logged on the system.
- HKEY_CLASSES_ROOT: Parent of all other registries.
- HKEY_CURRENT_CONFIG: Stores information from the hardware profile that is being used on the current system.
- HKEY_LOCAL_MACHINE: Information from hardware configurations on systems such as LAN, USB, Modems and others.
In the registry there are the terms Key and Values. Key is a grouping of the registry containing Values so that each Key will have SubKey, Values contains a value in the form of binary, strings and DWORD.
When doing forensics in the registry we can use tools such as FTK Imager to extract information in the registry both physical, logical, image or that is in a particular folder. For example, to do forensics in the registry we can use the NTUSER.DAT file, which is one of the hive files in the HKEY_CURRENT_USER structure.
There are several formats which are included in a registry hive:
- HKEY_CURRENT_CONFIG - System, System.alt, System.log, System.sav
- HKEY_CURRENT_USER - Ntuser.dat, Ntuser.dat.log
- HKEY_LOCAL_MACHINE \ SAM - Sam, Sam.log, Sam.sav
- HKEY_LOCAL_MACHINE \ Security - Security, Security.log, Security.sav
- HKEY_LOCAL_MACHINE \ Software - Software, Software.log, Software.sav
- HKEY_LOCAL_MACHINE \ System - System, System.alt, System.log, System.sav
- HKEY_USER \ .DEFAULT - Default, Default.log, Default.sav
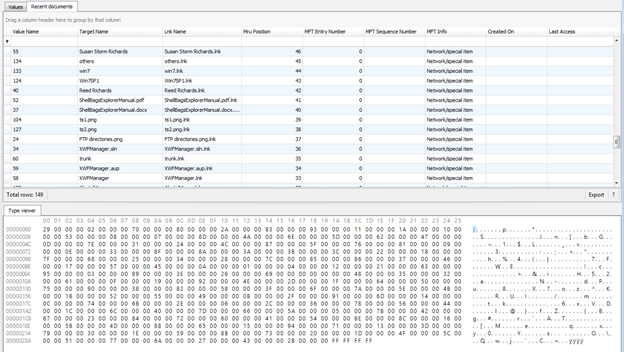
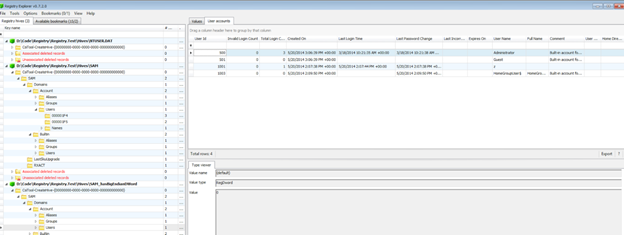
By using Registry Explorer we can use several artifact files such as the list above for use as analysis.
LNK Files
Windows Shortcut / The Shell Link Binary File Format (LNK) is used by Windows as a file to link to other files such as files, network shares, or search results making it easier for users to access something that is often needed or used. Through LNK files we can get metadata information such as the location of the folder link, the date the file was created, modified and accessed last time, file size and others. Generally the location of the LNK file is in the folder: C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Recent
To read the metadata from this file we can use the Windows File Analyzer:
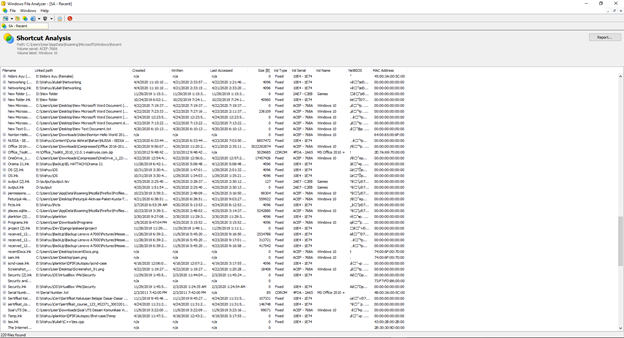
In Windows File Analyzer, we can also analyze and make a report:
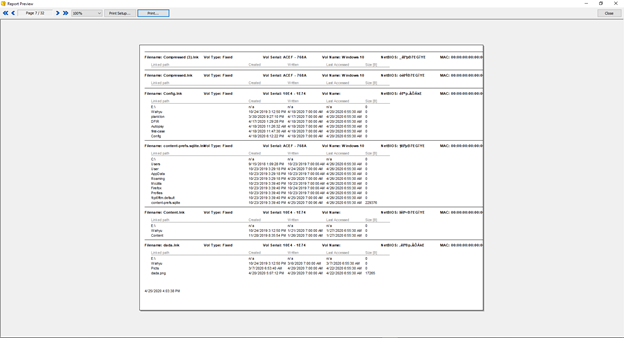
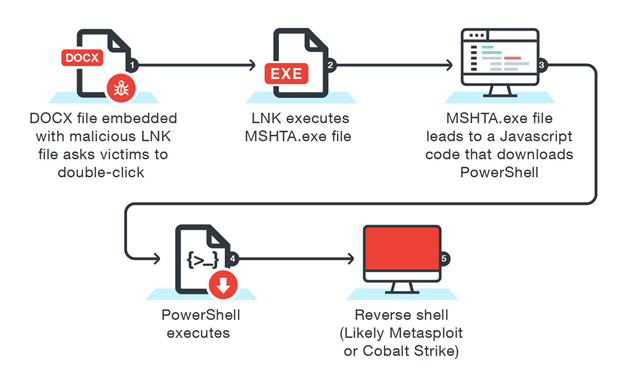
Why do we need to do forensics on this file? LNK files are also commonly used to distribute malware via e-mails as shown below which uses LNK files to execute PowerShell and run the malware. When there is malware that uses this method we can analyze the artifacts of this file to see the process of executed malware originating from what folder and at what time the malware compromised the system.
Jump List
An Object Linking and Embedding (OLE) file, used to embedding and linking documents. Before the Jump List feature was introduced in Windows, we could use Most Recently Used (MRU) and Most Frequently Used (MFU) to view history files that were previously accessed or frequently accessed. In the Jump List feature we introduced 2 types of files:
- automaticDestination-ms -
C:\Users\% USERNAME%\AppData\ Roaming\Microsoft\Windows\Recent\AutomaticDestinations
and
- customDestination-ms -
C:\Users\%USERNAME%\AppData\ Roaming\Microsoft\Windows\Recent\CustomDestinations
The two files above contain application information recently accessed on the taskbar in the form of a timestamp, path, and so on. Each Jump List file has an Application Identifier (AppID) to identify what types of files are accessed such as:
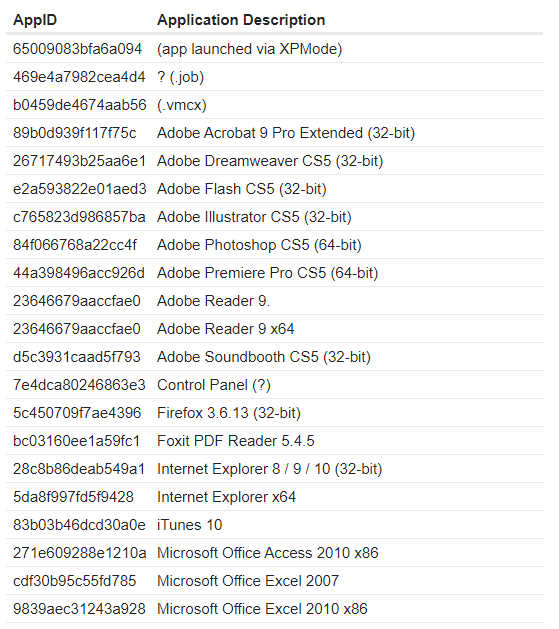
This file will definitely be an interesting artifact to be analyzed, some supporting tools can be used to obtain information from this file such as JumpList Explorer
Windows Error Reporting (WER)
Windows Error Reporting is basically a feature to help solve problems associated with programs crashing on the Windows operating system. The service analyzes the crashed application's state and builds context information surrounding the crashed program. We can find these artifacts in here: C:\ProgramData\Microsoft\Windows\WER\ReportArchive
On default configured systems, an error report (a minidump and XML file with various details, such as the DLL version numbers loaded in the process) is sent to Microsoft's online crash analysis server. Eventually, as the service is notified of a solution for a problem, it will display a tooltip to the user informing her of steps that should be taken to solve the problem.
Prefetch File Forensics
Prefetch Files are a very valuable set of artifacts for anyone doing forensics analysis. They contains a wealth of information about applications that have been run on a system such as :
- Application Name
- Application Path
- Last Execution Timestamp
- Creation Timestamp
We can find these artifacts in C:\Windows\Prefetch
To make sense of these files and the information available within. We require some tools. There are some tools that can help us parse these files.
RDP Cache Forensics
usually attackers use RDP to move laterally through the network. When using the “mstsc” client provided by windows to connect via RDP.
It automatically creates cache files containing sections of the screen of the machine we are connect to that are rarely changing. In order to improve performance.
We can find these artifacts in: C:\Users\%USERNAME%\AppData\Local\Microsoft\Terminal ServerClient\Cache
To be able to extract images stored in this cache file we can use bmc-tools.


