WU02 TryHackMe- Basic Pentesting
A writeup of the Basic Pentesting Room on the TryHackMe Platform.

Welcome to my writeup digs into the Basic Pentesting Room on the TryHackMe Platform. I am going to explain in detail the procedure involved in solving the different challenges and tasks you find there.
Learning Outcomes
By solving the tasks/challenges associated with this room we are going to learn about scanning the host for services and open ports. In addition, we are going to look for different directories present on the webserver, in order to gain access to the host we will crack passwords and hashes. More learning outcomes would be revealed when we start to solve the tasks. So let's dive in !!!
Task 1 & 2
Connect to OpenVPN and deploy the machine. We need to find the services running on the host machine for that we will run Nmap against the host machine. From the scan, we conclude that a web service is running on port 80 and the version associated with this service is Apache httpd 2.4.18. In addition to this, there is an SMB Samba service running on port 139. These services can be our area of interest.

Task 3
We need to find the hidden directory on the webserver. Let's access the IP address of the host on the web browser. As seen below there is no information obtained

We need to find the hidden directories, for this, we will use a tool known as gobuster that will look for hidden directories and brute force directories. In the parameters, we are going to define the IP address of the server and provide a world list as seen below. Once the process completes we find a hidden directory. All other directories are not accessible and we can confirm this by looking at the status code.

Now we need to access the hidden directory to find more information

There are two text files in the hidden directory, let's have a look and see if we can find some information.


By looking at the dev.txt we find out the version of the apache webserver and service of SMB running. I tried to find exploits against the HTTP service but there was no result. Observing the j.txt we come to know that we could try cracking the hash of the users as the passwords may be weak so are their hashes.
Tasks 4 -7
Considering our Nmap scan again, let's use enum4linux in order to enumerate samba. Use the below syntax for enum4linux
enum4linux -a <machine ip>
Using the tool we get 2 users. Please note that this may take time as enumeration is done for all the UIDs on the system.
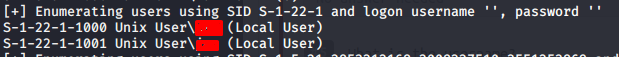
Now we need to know the password of the users found. So I am going to use hydra to brute force the user password using a dictionary. Remember the host was also running ssh, so we will try to brute force the ssh login of the user

Now lets login via ssh using the credentials

Tasks 8–11
Now we need to find any vectors to escalate our privileges. Look for files on the host. We don't find anything on the user Jan

Let's check the other user. After looking properly we find the public key of the other user. The public key contains the hash, copy the hash key with you
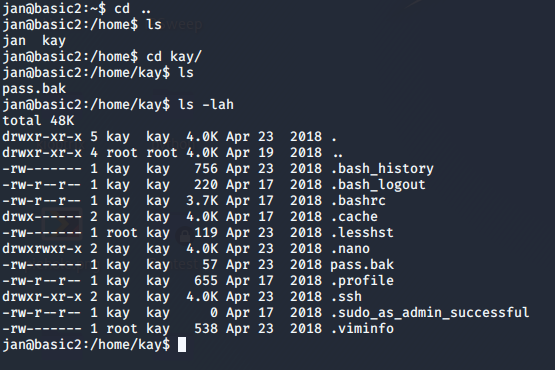
Navigate to the .ssh folder and there we find the private key of the user
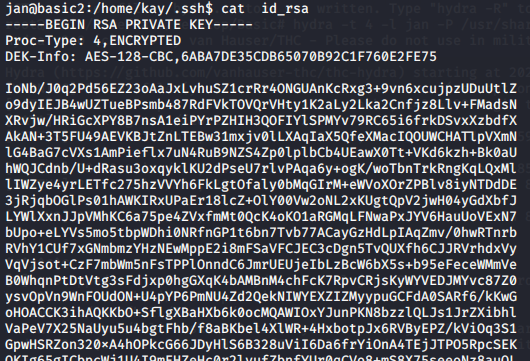
After this, we need to copy the key and use john to crack the hash. But first, we need to convert this key file into hash format as shown below

Once we are done with this, we will now use john to crack the hash using the word list rockyou.txt

Now we have the cracked hash of the user kay. Remember this is not the password for the ssh user rather its the cracked hash of the private key we found in the kay user directory which was accessed by connection to Jan via ssh. So we need to apply the cracked hash via Jan user as shown below

With that our challenges / Tasks are completed.
Conclusion
Solving this challenge enables us to get an overall idea of how we can scan our target machines and look for vulnerabilities on them. We also get to know about cracking passwords and hashes once we try to gain access or escalate our privileges. With that being said, try to complete the room first by yourself and if you get stuck feel free to consult the walkthrough. Happy Hacking :) !!
About Me
I am a cybersecurity enthusiast pursuing my Master’s in Information Security and trying to get into a full-time cybersecurity career.


