TryHackMe WriteUp: Linux Challenges
This write-up goes through finding flags on a Linux Machine using different commands, services, and tools found in Linux Operating System.
The Linux Challenges room on the TryHackMe platform is great for brushing up your Linux skills. This write-up goes through finding flags on a Linux Machine using different commands, services, and tools found in Linux Operating System. We will be going through the entire room and finding flags hidden throughout the systems which will lead to the completion of each task systematically.
I recommend you folks try solving the challenges on your own and if you get stuck somewhere you can always come back here.
Objectives
- Learn to use commands such as find, locate, ls, grep, tar, etc.
- Understand Cron jobs, MOTDs, locate hidden directories and files on the system.
- Learn to SSH into different user account using private keys.
- Understand system files, paths, variables and file permissions.
- Learn to transfer files using SCP and remote desktop via GUI etc.
Task1 Linux Challenges Introduction
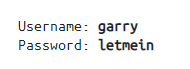
First things first, we need to connect to the TryHackMe network to access our target machine. For this, we can either connect to OpenVPN or use the in-browser machine access (Available for subscribed users). We could use the following credentials in case we need to log in via SSH manually.
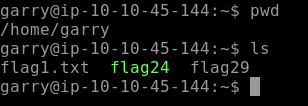
Lets ssh to the target machine using the credentials above. Use ls to list all the files of user Garry’s home directory as seen below.
[Task 2] The Basics
This section covers the basics of Linux. We are required to look for hidden flags and we might need to switch to another user account for our objectives. We need to find 10 flags to complete this section’s challenge.
Let’s find out our first flag by using the cat command as seen below.
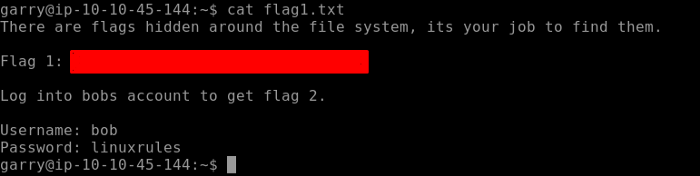
We have to log in to bobs account to find our Flag 2.
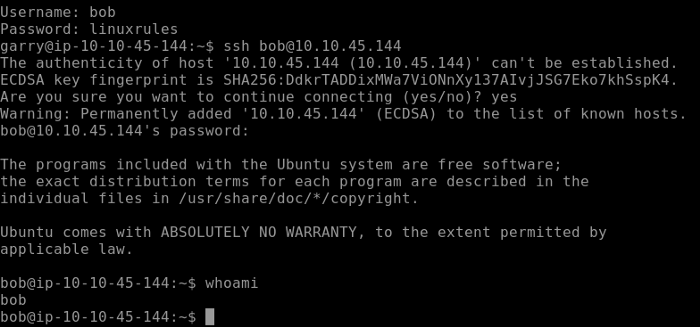
After switching to bobs account use cat to output Flag 2 as seen below.
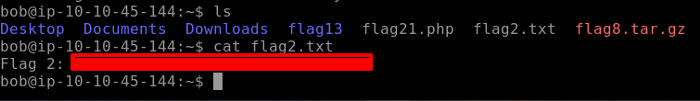
Flag 3 is hidden where the bash history of the current user is stored. We don’t know the exact location of the bash history file which is hidden so we can use the locate command and find the flag 3 as seen below.
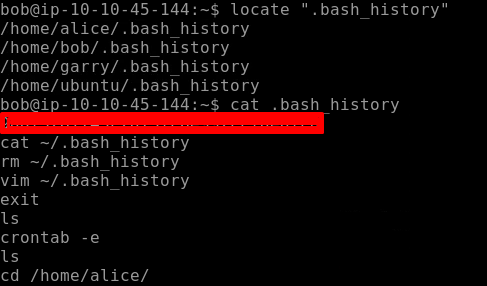
Our Flag 4 is located in crontab. Crontab is a list of commands that are used to run on a specified schedule. Crontab is related to cronjobs whose purpose is to execute specified instructions or commands at a specified schedule or time. crontab -e allows to edit the crontab entries.
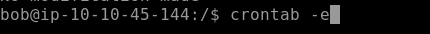
Going through the entries of crontab we find our flag 4
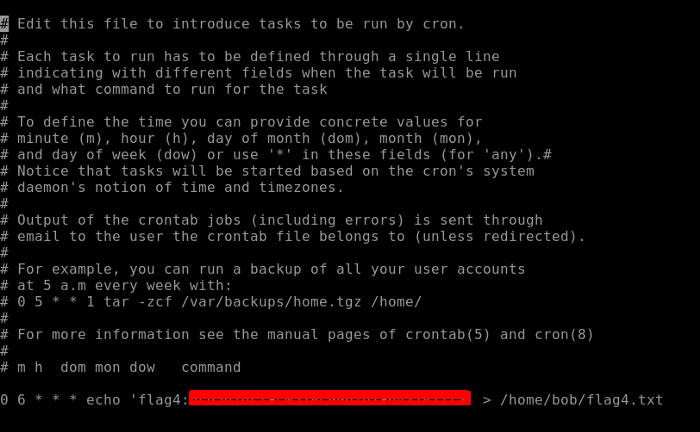
Moving to our next flag i.e. Flag 5. Let’s use the grep command which comes in handy while finding any file, directory, or content of the file. grep -r ‘flag5’ will recursively search for the content flag5. As seen below we find the path to our Flag5.
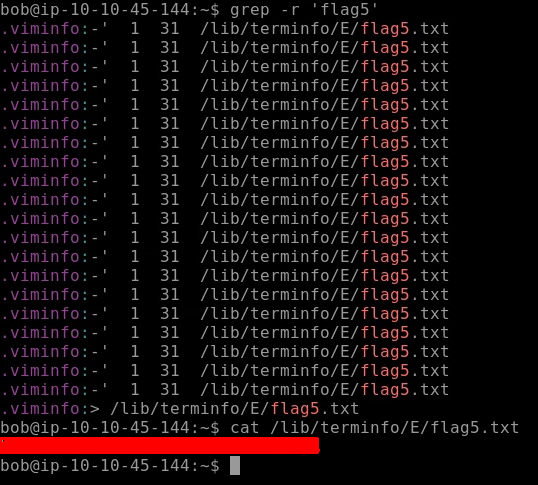
We are going to find the flag 6 similarly. The task gives us a hint that the flag contains the letters ‘c9’ in it. First, locate the Flag 6 directory using the locate command. As we output the file there is too much text so here grep comes into action.
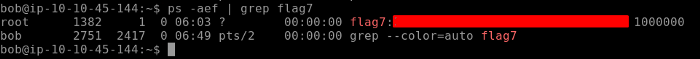
Moving on to our next flag. The challenge hints us to look into the path were processes are found. e will use the ps command which is used to list down all the active processes on the system. The flags we set with the ps commands allow us to list down active connections in a list format.
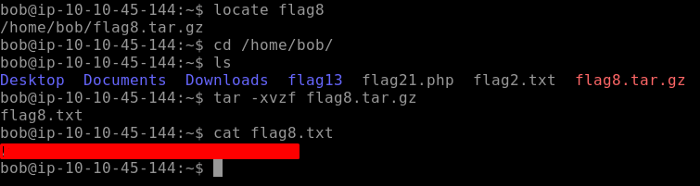
Flag 8 can be found on the home directory of the user bob. This file needs to be decompressed to output the content of Flag 8.
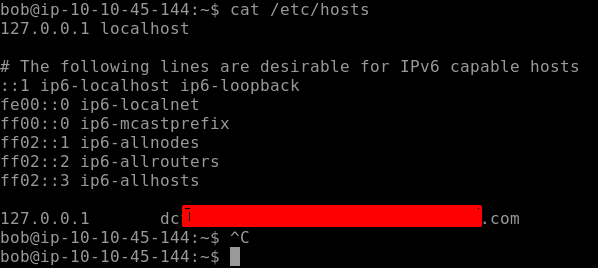
The challenge hints us to look in the hosts’ file to find our Flag 9.
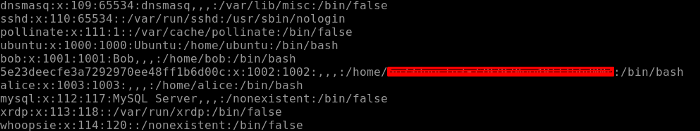
For our final flag i.e. Flag 10 we need to look into the directories where we find all the users mainly password hashes are stored in this file and if you are already familiar with the Linux files system and directories you might have guessed it until now. Yes, it is the etc/passwd file we have to look into. Analyzing the file we get our final flag 10.
We have our final flag fo this task which completes this challenge.
[Task 3] Linux Functionality
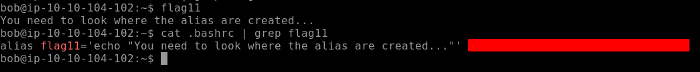
Moving on to the next challenge task, we would be using more of the Linux commands here. Let’s run the flag11 and see what it says. As the output says we have to look in where alias is created so .bashrc is the right place to look and as seen below we have our flag 11.
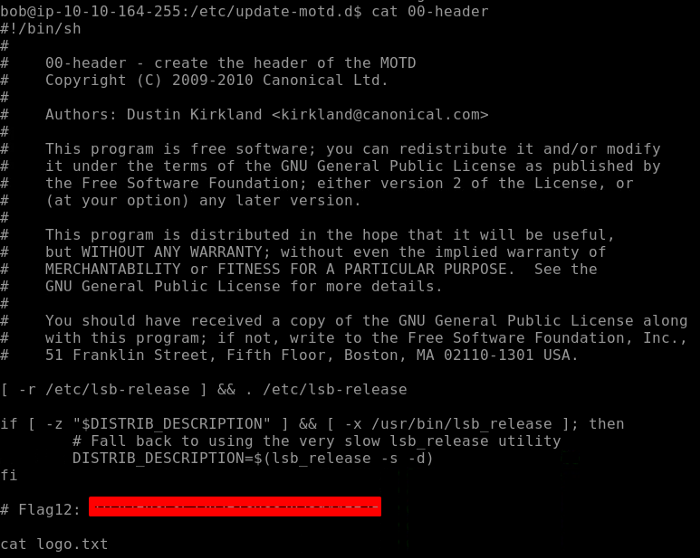
Flag 12 is found in the motd (Message of the day ) directory. So navigate to the directory as shown below. Checking the header file we have our flag12.
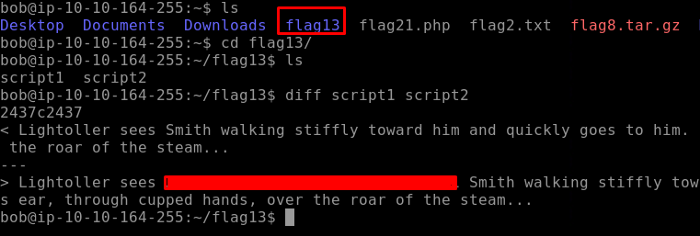
For the next flag, we navigate to the Flag13 directory. There are two scripts contained in this directory. As the challenge says to use the diff command, diff command compares the content line by line and produces the output. Doing so we get our Flag 13
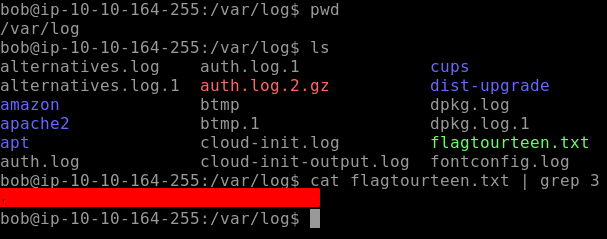
Moving on to the next flag i.e. Flag14. We can find the flag where logs are stored, navigate to the var/log directory as seen below. It can be seen that our Flag14 is named flagtourteen.txt , there is a lot of text and you will find the flag at the end. For simplicity, I use grep 3 as my flag contained the number three you can skip this command as it is not necessary
Flag15 can be found where system information is stored and that can be found in the release directory. Navigating to this directory we find our flag 15.
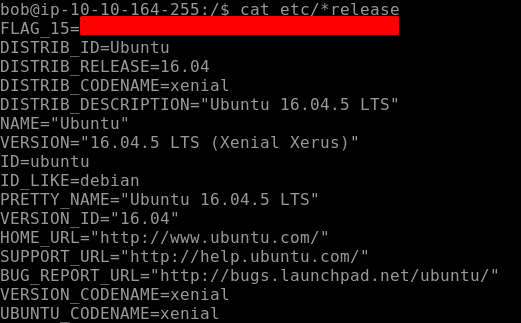
Moving on to our next flag i.e Flag 16. This is hidden on one of the mounts of the files system usually found in the directory of media. Let's navigate to this directory. Seems like there are more directories in each having a prefix of the word “Flag16is” as seen below.
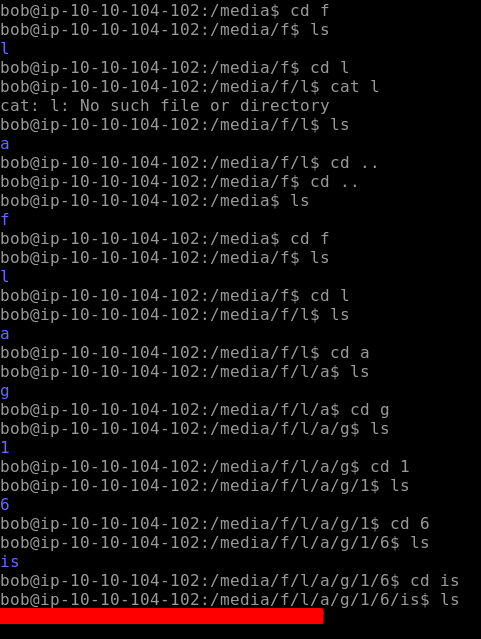
Flag17 is found on Alice Account. So lets ssh into Alice's account, her password is “TryHackMe123”. Use ls to list all the files in the directory and here we find our flag as seen below
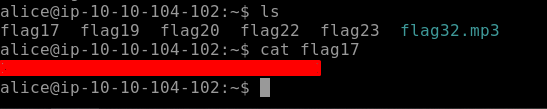
Moving on to our next hidden flag i.e. Flag18, it's hidden so we use ls -la to list down all the hidden files and directories. Use cat to output the result of the hidden flag
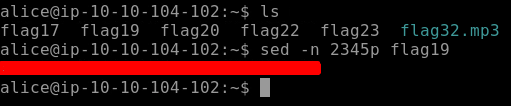
The last flag for this section is flag19. We have to find the 2435 line which will show us our flag19. We need to read a specific line of file so we would use sed. -n flag is used to suppress the unmatched text while the flag p is used to print the matched lines.
With this, we conclude our Task 3 i.e. Linux Functionality.
[Task 4] Data Representation, Strings, and Permissions
This section will focus mainly on how data is represented on the Linux System. In addition to that don’t forget to use searching skills as some of the tasks may require independent research using Google or any other reference material.
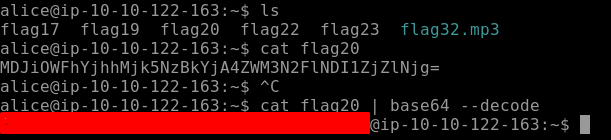
We find our Flag20 in Alice directory. When we cat the output we find that the content is encoded using base64 and we need to decode it. As seen below we can recognize if some string is encoded with base64 by looking at the character set [A-Z, a-z, 0–9, + /]. So let’s decode the string to obtain our flag. Use the following command to decode.
cat flag20 | base64 — decode
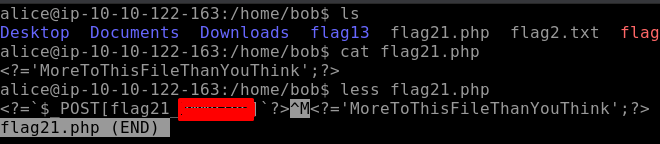
Moving on to our next flag21. This flag is a PHP file and by using less command we find our flag as seen below. Less basically outputs the content of files one page at a time, it’s similar to more but with more functionalities.
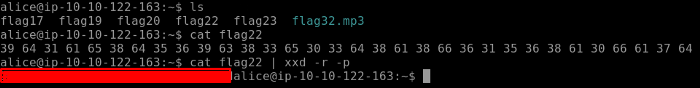
When we output the content of our Flag22, the output is in the hex format. We need to convert this is into ASCII as shown below. xxd creates the hex dump of a file and converts the hex dump back to its original binary.
Flag23 is found very easily just by reversing the order of the string found in the content of Flag23 as seen below.
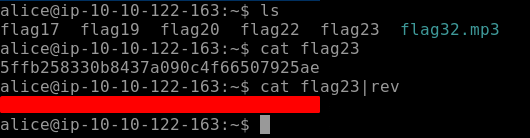
Flag24 is a c program file. We will use the commands strings so that human-readable strings are shown.
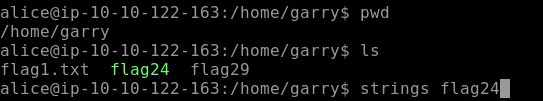
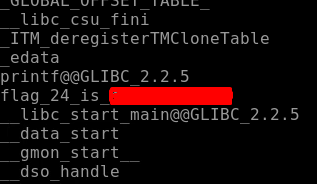
After we use the string command, we get our Flag24 as seen below.
As per the task challenges Flag25 does not exist so we are going to move to the next one i.e. Flag26.
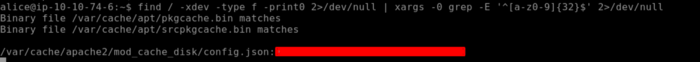
Locating flag26 is a bit tough as we need to find a string that is 32 characters long and starts with 4bceb. So here we are going to use the find command in conjunction with grep as shown below.
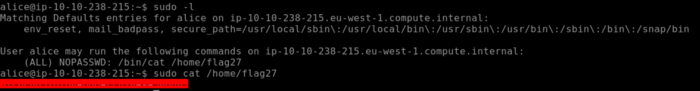
Moving on to our next Flag27. Flag27 is owned by the root user so we need to know that if Alice is allowed to execute certain commands to extract the output of Flag27. So here we use Sudo -l that will tell me which commands can be executed by the user Alice as seen below. So running the commands that are permitted by root to the user Alice we obtain our Flag27.
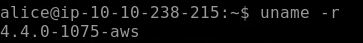
Next, we need to find the kernel version which can be obtained using the uname command as seen below. uname is used to display information about the system version, OS, etc. -r flag shows the kernel release as seen below.
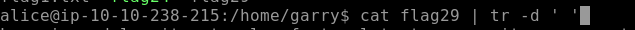
We need to remove all spaces in the file and lines, split them by a comma to get our final flag i.e. Flag29 for this section. As seen below tr is used to translate or delete characters which in our case is spaces.
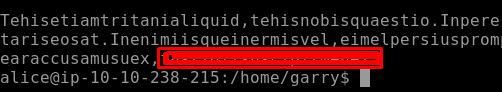
Once spaces are removed we can get our Flag29 as seen below.
[Task 5] SQL, FTP, Groups & RDP
This task challenges include playing with the databases by finding flags, downloading, and transferring files to your local systems. So let’s get started!
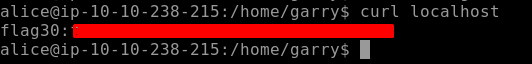
We need to find our First flag i.e. Flag30 for our current task. We need to look for any service running on the localhost. The command curl will come in handy here. curl is a tool that is used to transfer to a server or from a server using different supported protocols. Using curl in the current scenario we find our flag.
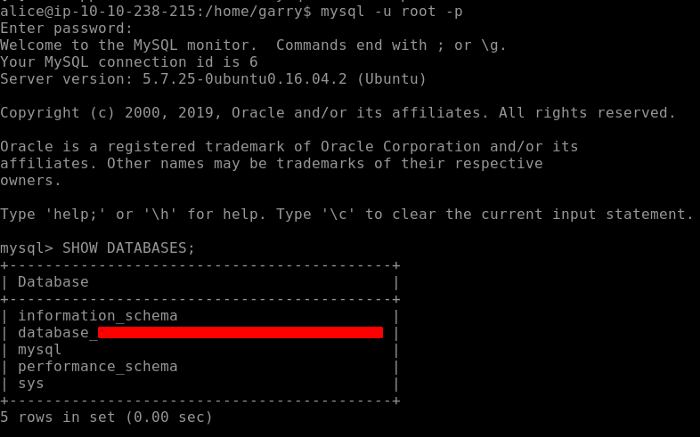
To find our Flag31 we need to login to the Database. Credentials of the database are already given. Log into the database and use the command SHOW DATABASES; which will list down the whole database and here we find out Flag31.
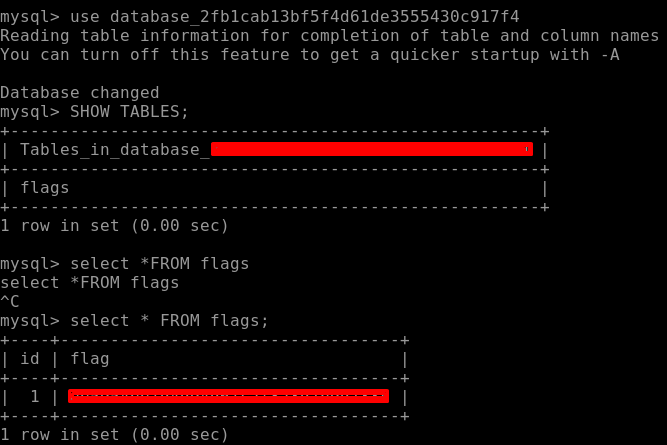
There is a bonus flag hidden in the database. For that we navigate to the database we found earlier. Under that database there is a table called flag, let’s access it to find our bonus flag as seen below.
The next flag is an mp3 file that needs to be downloaded to our local system to see what’s in it. We can either use SCP(Secure Copy) or Filezilla to download it. I prefer using SCP. You can find the syntax for SCP simply by googling.
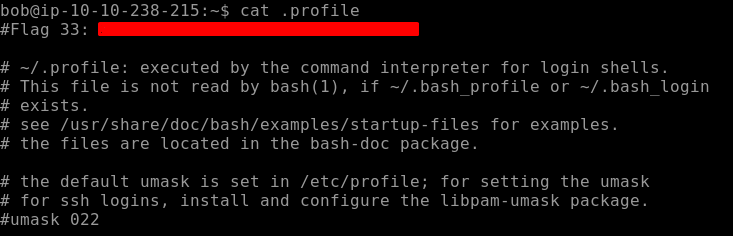
We get our Flag33 by navigating to. profile where personal paths are stored as seen below.
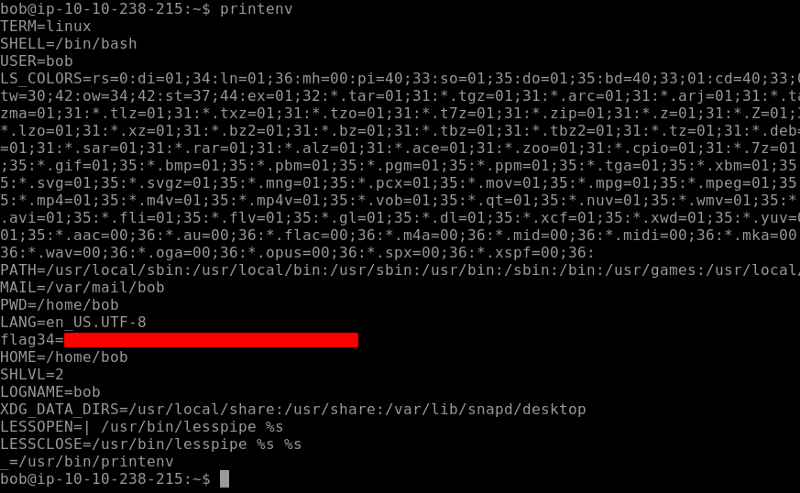
Let’s switch to Bob’s account and output the environment variable by using env or printenv which will print all the environment variables as shown below. We find our Flag34 here.
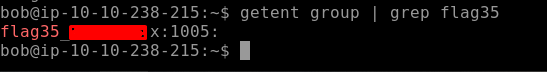
We need to look into a place where all groups are created on the system. Use the getent group command to do that, notice I have used grep in conjunction with this command so that I get specific results. We find our Flag35 as seen below.
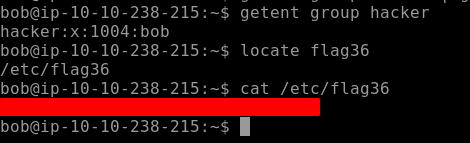
Our Final Flag for this section is related to the previous command. In this challenging task, we need to find the user that is in the hacker group. Through that, we are going to get our final flag. We use the same command which we used to display all the groups on the system and navigate to the specific user to find our Flag36 as seen below.
Closing Remarks
This concludes our CTF for Linux Challenges. This challenge contained loads of Linux commands which are used commonly used by System Admins, Ethical Hackers, Pentesters, etc. If you want to learn more about Linux commands, tools, services, and filesystem Join Learn Linux Room on TryHackMe.
About Me
I am a cybersecurity enthusiast pursuing my Master’s Degree in Information Security and trying to get into a full-time cybersecurity career.